Security News > 2023 > July > TeamTNT's Silentbob Botnet Infecting 196 Hosts in Cloud Attack Campaign
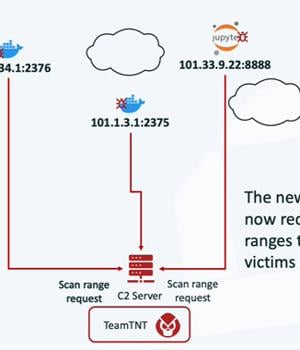
As many as 196 hosts have been infected as part of an aggressive cloud campaign mounted by the TeamTNT group called Silentbob.
"The botnet run by TeamTNT has set its sights on Docker and Kubernetes environments, Redis servers, Postgres databases, Hadoop clusters, Tomcat and Nginx servers, Weave Scope, SSH, and Jupyter applications," Aqua security researchers Ofek Itach and Assaf Morag said in a report shared with The Hacker News.
The development arrives a week after the cloud security company detailed an intrusion set linked to the TeamTNT group that targets exposed JupyterLab and Docker APIs to deploy the Tsunami malware and hijack system resources to run a cryptocurrency miner.
The latest findings suggest a broader campaign and the use of a larger attack infrastructure than previously thought, including various shell scripts to steal credentials, deploy SSH backdoors, download additional payloads, and drop legitimate tools like kubectl, Pacu, and Peirates to conduct reconnaissance of the cloud environment.
"TeamTNT is scanning for credentials across multiple cloud environments, including AWS, Azure, and GCP," the researchers said.
"The SCARLETEEL IP address, 45.9.148[.]221, was used just days ago in TeamTNT's IRC channel C2 server. The scripts are very similar and the TTPs are the same. It looks like TeamTNT never stopped attacking. If they ever retired, it was only for a brief moment."
News URL
https://thehackernews.com/2023/07/teamtnts-silentbob-botnet-infecting-196.html
Related news
- New Eleven11bot botnet infects 86,000 devices for DDoS attacks (source)
- Unpatched Edimax IP camera flaw actively exploited in botnet attacks (source)
- SANS Institute Warns of Novel Cloud-Native Ransomware Attacks (source)
- Unpatched Edimax Camera Flaw Exploited for Mirai Botnet Attacks Since Last Year (source)