Security News > 2023 > July > PicassoLoader Malware Used in Ongoing Attacks on Ukraine and Poland
Government entities, military organizations, and civilian users in Ukraine and Poland have been targeted as part of a series of campaigns designed to steal sensitive data and gain persistent remote access to the infected systems.
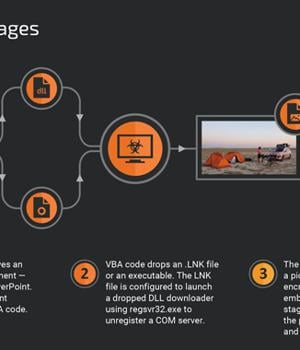
The intrusion set, which stretches from April 2022 to July 2023, leverages phishing lures and decoy documents to deploy a downloader malware called PicassoLoader, which acts as a conduit to launch Cobalt Strike Beacon and njRAT. "The attacks used a multistage infection chain initiated with malicious Microsoft Office documents, most commonly using Microsoft Excel and PowerPoint file formats," Cisco Talos researcher Vanja Svajcer said in a new report.
It's worth noting that a subset of these attacks has already been documented over the past year by Ukraine's Computer Emergency Response Team and Fortinet FortiGuard Labs, one of which employed macro-laden PowerPoint documents to deliver Agent Tesla malware in July 2022.
The infection chains aim to convince victims to enable macros, with the VBA macro engineered to drop a DLL downloader known as PicassoLoader that subsequently reaches out to an attacker-controlled site to fetch the next-stage payload, a legitimate image file that embeds the final malware.
The disclosure comes as CERT-UA detailed a number of phishing operations distributing the SmokeLoader malware as well as a smishing attack designed to gain unauthorized control of targets' Telegram accounts.
Last month, CERT-UA disclosed a cyber espionage campaign aimed at state organizations and media representatives in Ukraine that makes use of email and instant messengers to distribute files, which, when launched, results in the execution of a PowerShell script called LONEPAGE to fetch next-stage browser stealer and keylogger payloads.
News URL
https://thehackernews.com/2023/07/picassoloader-malware-used-in-ongoing.html
Related news
- Multi-Stage Malware Attack Uses .JSE and PowerShell to Deploy Agent Tesla and XLoader (source)
- New Android malware steals your credit cards for NFC relay attacks (source)
- Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery (source)
- SuperCard X Android Malware Enables Contactless ATM and PoS Fraud via NFC Relay Attacks (source)
- SK Telecom warns customer USIM data exposed in malware attack (source)
- DslogdRAT Malware Deployed via Ivanti ICS Zero-Day CVE-2025-0282 in Japan Attacks (source)
- Malware Attack Targets World Uyghur Congress Leaders via Trojanized UyghurEdit++ Tool (source)
- Nebulous Mantis Targets NATO-Linked Entities with Multi-Stage Malware Attacks (source)
- DarkWatchman, Sheriff Malware Hit Russia and Ukraine with Stealth and Nation-Grade Tactics (source)
- Disney Slack attack wasn't Russian protesters, just a Cali dude with malware (source)