Security News > 2023 > June > Evasive QBot Malware Leverages Short-lived Residential IPs for Dynamic Attacks
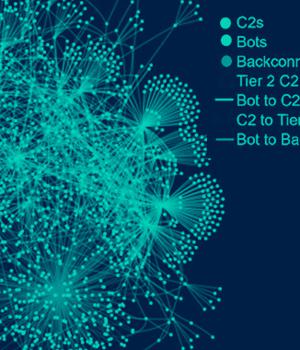
An analysis of the "Evasive and tenacious" malware known as QBot has revealed that 25% of its command-and-control servers are merely active for a single day.
What's more, 50% of the servers don't remain active for more than a week, indicating the use of an adaptable and dynamic C2 infrastructure, Lumen Black Lotus Labs said in a report shared with The Hacker News.
"This botnet has adapted techniques to conceal its infrastructure in residential IP space and infected web servers, as opposed to hiding in a network of hosted virtual private servers," security researchers Chris Formosa and Steve Rudd said.
While phishing waves bearing QBot at the start of 2023 leveraged Microsoft OneNote as an intrusion vector, recent attacks have employed protected PDF files to install the malware on victim machines.
QakBot's reliance on compromised web servers and hosts existing in the residential IP space for C2 translates to a brief lifespan, leading to a scenario where 70 to 90 new servers emerge over a seven-day period on average.
According to data released by Team Cymru last month, a majority of Qakbot bot C2 servers are suspected to be compromised hosts that were purchased from a third-party broker, with most of them located in India as of March 2023.
News URL
https://thehackernews.com/2023/06/evasive-qbot-malware-leverages-short.html
Related news
- ⚡ THN Weekly Recap: GitHub Supply Chain Attack, AI Malware, BYOVD Tactics, and More (source)
- Chinese FamousSparrow hackers deploy upgraded malware in attacks (source)
- Open-source malware doubles, data exfiltration attacks dominate (source)
- Microsoft Warns of Tax-Themed Email Attacks Using PDFs and QR Codes to Deliver Malware (source)
- New TCESB Malware Found in Active Attacks Exploiting ESET Security Scanner (source)
- Multi-Stage Malware Attack Uses .JSE and PowerShell to Deploy Agent Tesla and XLoader (source)
- New Android malware steals your credit cards for NFC relay attacks (source)
- Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery (source)
- SuperCard X Android Malware Enables Contactless ATM and PoS Fraud via NFC Relay Attacks (source)
- SK Telecom warns customer USIM data exposed in malware attack (source)