Security News > 2023 > May > New GobRAT Remote Access Trojan Targeting Linux Routers in Japan
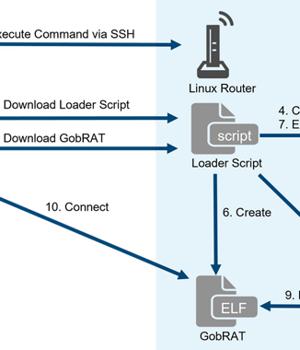
Linux routers in Japan are the target of a new Golang remote access trojan called GobRAT. "Initially, the attacker targets a router whose WEBUI is open to the public, executes scripts possibly by using vulnerabilities, and finally infects the GobRAT," the JPCERT Coordination Center said in a report published today.
The compromise of an internet-exposed router is followed by the deployment of a loader script that acts as a conduit for delivering GobRAT, which, when launched, masquerades as the Apache daemon process to evade detection.
The loader is also equipped to disable firewalls, establish persistence using the cron job scheduler, and register an SSH public key in the.
GobRAT, for its part, communicates with a remote server via the Transport Layer Security protocol to receive as many as 22 different encrypted commands for execution.
Attempt to login to sshd, Telnet, Redis, MySQL, PostgreSQL services running on another machine.
The findings come nearly three months after Lumen Black Lotus Labs revealed that business-grade routers have been victimized to spy on victims in Latin America, Europe, and North America using a malware called HiatusRAT..
News URL
https://thehackernews.com/2023/05/new-gobrat-remote-access-trojan.html