Security News > 2023 > May > State-Sponsored Sidewinder Hacker Group's Covert Attack Infrastructure Uncovered
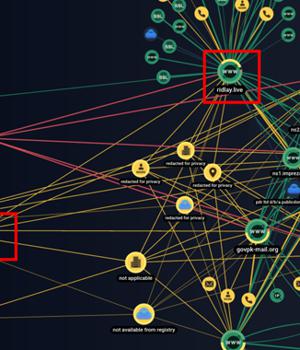
Cybersecurity researchers have unearthed previously undocumented attack infrastructure used by the prolific state-sponsored group SideWinder to strike entities located in Pakistan and China.
SideWinder has been known to be active since at least 2012, with attack chains primarily leveraging spear-phishing as an intrusion mechanism to obtain a foothold into targeted environments.
More recently, the nation-state group was observed leveraging a technique known as server-based polymorphism in evasive attacks targeting Pakistani government organizations.
Another LNK file that was uploaded to VirusTotal around the same time from Kathmandu employs a similar method to fetch an HTA file from a domain masquerading as a Nepalese government website.
Further investigation into SideWinder's infrastructure has led to the discovery of a malicious Android APK file that was uploaded to VirusTotal from Sri Lanka in March 2023.
In all, the domains point to SideWinder setting its sights on financial, government, and law enforcement organizations, as well as companies specializing in e-commerce and mass media in Pakistan and China.
News URL
https://thehackernews.com/2023/05/state-sponsored-sidewinder-hacker.html
Related news
- Russian hackers attack Western military mission using malicious drive (source)
- State-Sponsored Hackers Weaponize ClickFix Tactic in Targeted Malware Campaigns (source)
- State-sponsored hackers embrace ClickFix social engineering tactic (source)
- Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery (source)
- Hackers abuse Zoom remote control feature for crypto-theft attacks (source)
- DPRK Hackers Steal $137M from TRON Users in Single-Day Phishing Attack (source)
- Lazarus hackers breach six companies in watering hole attacks (source)
- Chinese Hackers Abuse IPv6 SLAAC for AitM Attacks via Spellbinder Lateral Movement Tool (source)
- CISA warns of hackers targeting critical oil infrastructure (source)
- Chinese hackers behind attacks targeting SAP NetWeaver servers (source)