Security News > 2023 > May > CERT-UA Warns of SmokeLoader and RoarBAT Malware Attacks Against Ukraine
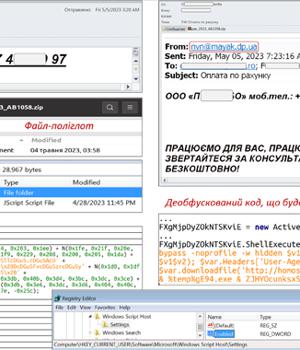
An ongoing phishing campaign with invoice-themed lures is being used to distribute the SmokeLoader malware in the form of a polyglot file, according to the Computer Emergency Response Team of Ukraine.
In a related advisory, Ukraine's cybersecurity authority also revealed details of destructive attacks orchestrated by a group known as UAC-0165 against public sector organizations.
The attack, which targeted an unnamed state organization, entailed the use of a new batch script-based wiper malware called RoarBAT that performs a recursive search for files with a specific list of extensions and irrevocably deletes them using the legitimate WinRAR utility.
"Access to the ICS target of the attack is allegedly obtained by connecting to a VPN using compromised authentication data. The successful implementation of the attack was facilitated by the lack of multi-factor authentication when making remote connections to VPN.".
The agency further attributed UAC-0165 with moderate confidence to the notorious Sandworm group, which has a history of unleashing wiper attacks since the start of the Russo-Ukrainian war last year.
The alerts come a week after CERT-UA cautioned of phishing attacks carried out by the Russian state-sponsored group APT28 targeting government entities in the country with fake Window update notifications.
News URL
https://thehackernews.com/2023/05/cert-ua-warns-of-smokeloader-and.html
Related news
- Multi-Stage Malware Attack Uses .JSE and PowerShell to Deploy Agent Tesla and XLoader (source)
- New Android malware steals your credit cards for NFC relay attacks (source)
- Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery (source)
- SuperCard X Android Malware Enables Contactless ATM and PoS Fraud via NFC Relay Attacks (source)
- SK Telecom warns customer USIM data exposed in malware attack (source)
- DslogdRAT Malware Deployed via Ivanti ICS Zero-Day CVE-2025-0282 in Japan Attacks (source)
- Malware Attack Targets World Uyghur Congress Leaders via Trojanized UyghurEdit++ Tool (source)
- Nebulous Mantis Targets NATO-Linked Entities with Multi-Stage Malware Attacks (source)
- DarkWatchman, Sheriff Malware Hit Russia and Ukraine with Stealth and Nation-Grade Tactics (source)
- Disney Slack attack wasn't Russian protesters, just a Cali dude with malware (source)