Security News > 2023 > May > Chinese Hacker Group Earth Longzhi Resurfaces with Advanced Malware Tactics
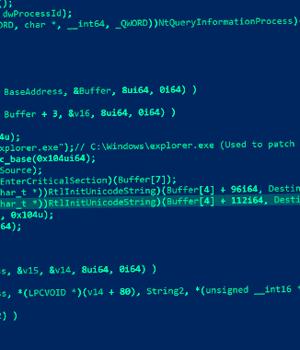
Trend Micro attributed the intrusion set to a cyber espionage group it tracks under the name Earth Longzhi, which is a subgroup within APT41 and shares overlaps with various other clusters known as Earth Baku, SparklingGoblin, and GroupCC. Earth Longzhi was first documented by the cybersecurity firm in November 2022, detailing its attacks against various organizations located in East and Southeast Asia as well as Ukraine.
Attack chains mounted by the threat actor leverage vulnerable public-facing applications as entry points to deploy the BEHINDER web shell, and then leverage that access to drop additional payloads, including a new variant of a Cobalt Strike loader called CroxLoader.
"This recent campaign abuses a Windows Defender executable to perform DLL sideloading while also exploiting a vulnerable driver, zamguard.sys, to disable security products installed on the hosts via a bring your own vulnerable driver attack," Trend Micro said.
It's by no means the first time Earth Longzhi has leveraged the BYOVD technique, what with previous campaigns utilizing the vulnerable RTCore64.
Deep Instinct, last month, detailed a new code injection technique christened Dirty Vanity that exploits the remote forking mechanism in Windows to blindside endpoint detection systems.
"Earth Longzhi remains active and continues to improve its tactics, techniques, and procedures," security researchers Ted Lee and Hara Hiroaki noted.
News URL
https://thehackernews.com/2023/05/chinese-hacker-group-earth-longzhi.html
Related news
- Chinese Hackers Target Linux Systems Using SNOWLIGHT Malware and VShell Tool (source)
- Chinese hackers target Russian govt with upgraded RAT malware (source)
- State-Sponsored Hackers Weaponize ClickFix Tactic in Targeted Malware Campaigns (source)
- Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery (source)
- Iran-Linked Hackers Target Israel with MURKYTOUR Malware via Fake Job Campaign (source)
- North Korean Hackers Spread Malware via Fake Crypto Firms and Job Interview Lures (source)
- Chinese Hackers Abuse IPv6 SLAAC for AitM Attacks via Spellbinder Lateral Movement Tool (source)
- Iranian Hackers Maintain 2-Year Access to Middle East CNI via VPN Flaws and Malware (source)
- Russian Hackers Using ClickFix Fake CAPTCHA to Deploy New LOSTKEYS Malware (source)
- Chinese Hackers Exploit SAP RCE Flaw CVE-2025-31324, Deploy Golang-Based SuperShell (source)