Security News > 2023 > April > Iranian Hackers Using SimpleHelp Remote Support Software for Persistent Access
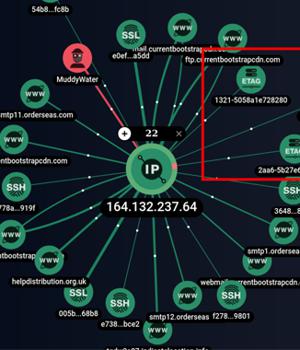
The Iranian threat actor known as MuddyWater is continuing its time-tested tradition of relying on legitimate remote administration tools to commandeer targeted systems.
While the nation-state group has previously employed ScreenConnect, RemoteUtilities, and Syncro, a new analysis from Group-IB has revealed the adversary's use of the SimpleHelp remote support software in June 2022.
"MuddyWater uses SimpleHelp, a legitimate remote device control and management tool, to ensure persistence on victim devices," Nikita Rostovtsev, senior threat analyst at Group-IB, said.
"SimpleHelp is not compromised and is used as intended. The threat actors found a way to download the tool from the official website and use it in their attacks."
The exact distribution method used to drop the SimpleHelp samples is currently unclear, although the group is known to send spear-phishing messages bearing malicious links from already compromised corporate mailboxes.
Group-IB's findings were corroborated by Slovak cybersecurity firm ESET earlier this January, detailing MuddyWater's attacks in Egypt and Saudi Arabia that entailed the use of SimpleHelp to deploy its Ligolo reverse tunneling tool and a credential harvester dubbed MKL64.
News URL
https://thehackernews.com/2023/04/iranian-hackers-using-simplehelp-remote.html
Related news
- Hackers abuse Zoom remote control feature for crypto-theft attacks (source)
- Iranian Hackers Maintain 2-Year Access to Middle East CNI via VPN Flaws and Malware (source)
- Iranian Hacker Pleads Guilty in $19 Million Robbinhood Ransomware Attack on Baltimore (source)
- OpenAI Bans ChatGPT Accounts Used by Russian, Iranian and Chinese Hacker Groups (source)