Security News > 2023 > March > Trojanized TOR Browser Installers Spreading Crypto-Stealing Clipper Malware
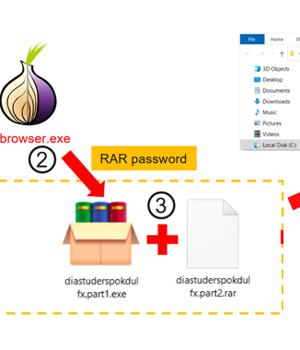
Trojanized installers for the TOR anonymity browser are being used to target users in Russia and Eastern Europe with clipper malware designed to siphon cryptocurrencies since September 2022.
"Clipboard injectors can be silent for years, show no network activity or any other signs of presence until the disastrous day when they replace a crypto wallet address," Vitaly Kamluk, director of global research and analysis team for APAC at Kaspersky, said.
Another notable aspect of clipper malware is that its nefarious functions are not triggered unless the clipboard data meet specific criteria, making it more evasive.
It's not immediately clear how the installers are distributed, but evidence points to the use of torrent downloads or some unknown third-party source since the Tor Project's website has been subjected to blockades in Russia in recent years.
Regardless of the method used, the installer launches the legitimate executable, while also simultaneously launching the clipper payload that's designed to monitor the clipboard content.
"If the clipboard contains text, it scans the contents with a set of embedded regular expressions," Kamluk noted.
News URL
https://thehackernews.com/2023/03/trojanized-tor-browser-installers.html
Related news
- Crypto Developers Targeted by Python Malware Disguised as Coding Challenges (source)
- Node.js Malware Campaign Targets Crypto Users with Fake Binance and TradingView Installers (source)
- Lotus Panda Hacks SE Asian Governments With Browser Stealers and Sideloaded Malware (source)
- Docker Malware Exploits Teneo Web3 Node to Earn Crypto via Fake Heartbeat Signals (source)
- North Korean Hackers Spread Malware via Fake Crypto Firms and Job Interview Lures (source)
- Golden Chickens Deploy TerraStealerV2 to Steal Browser Credentials and Crypto Wallet Data (source)
- Hackers Use Fake VPN and Browser NSIS Installers to Deliver Winos 4.0 Malware (source)