Security News > 2023 > March > Lookalike Telegram and WhatsApp Websites Distributing Cryptocurrency Stealing Malware
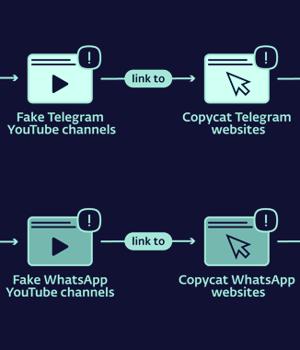
Copycat websites for instant messaging apps like Telegram and WhatApp are being used to distribute trojanized versions and infect Android and Windows users with cryptocurrency clipper malware.
"All of them are after victims' cryptocurrency funds, with several targeting cryptocurrency wallets," ESET researchers Lukáš Štefanko and Peter Strý?ek said in a new analysis.
While the first instance of clipper malware on the Google Play Store dates back to 2019, the development marks the first time Android-based clipper malware has been built into instant messaging apps.
The attack chain begins with unsuspecting users clicking on fraudulent ads on Google search results that lead to hundreds of sketchy YouTube channels, which then direct them to lookalike Telegram and WhatsApp websites.
What's novel about the latest batch of clipper malware is that it's capable of intercepting a victim's chats and replacing any sent and received cryptocurrency wallet addresses with addresses controlled by the threat actors.
Another cluster of clipper malware makes use of OCR to find and steal seed phrases by leveraging a legitimate machine learning plugin called ML Kit on Android, thereby making it possible to empty the wallets.
News URL
https://thehackernews.com/2023/03/lookalike-telegram-and-whatsapp.html