Security News > 2023 > March > Tick APT Targeted High-Value Customers of East Asian Data-Loss Prevention Company
A cyberespionage actor known as Tick has been attributed with high confidence to a compromise of an East Asian data-loss prevention company that caters to government and military entities.
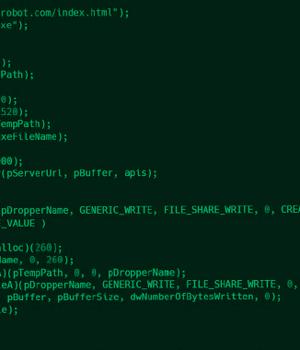
"The attackers compromised the DLP company's internal update servers to deliver malware inside the software developer's network, and trojanized installers of legitimate tools used by the company, which eventually resulted in the execution of malware on the computers of the company's customers," ESET researcher Facundo Muñoz said.
In late February 2021, Tick emerged as one of the threat actors to capitalize on the ProxyLogon flaws in Microsoft Exchange Server as a zero-day to drop a Delphi-based backdoor in a South Korean IT company.
Around the same time, the adversarial collective is believed to have gained access to the network of an East Asian software developer company through unknown means.
Subsequently, in February and June 2022, the trojanized Q-Dir installers were transferred via remote support tools like helpU and ANYSUPPORT to two of the company's customers, an engineering and a manufacturing firm located in East Asia.
The Slovak cybersecurity company said the goal here was not to perform a supply chain attack against its downstream customers, but rather that the rogue installer was "Unknowingly" used as part of technical support activities.
News URL
https://thehackernews.com/2023/03/tick-apt-targeted-high-value-customers.html