Security News > 2023 > February > PlugX Trojan Disguised as Legitimate Windows Debugger Tool in Latest Attacks
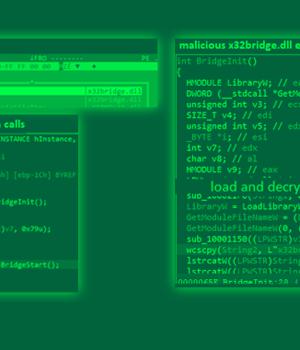
The PlugX remote access trojan has been observed masquerading as an open source Windows debugger tool called x64dbg in an attempt to circumvent security protections and gain control of a target system.
"This file is a legitimate open-source debugger tool for Windows that is generally used to examine kernel-mode and user-mode code, crash dumps, or CPU registers," Trend Micro researchers Buddy Tancio, Jed Valderama, and Catherine Loveria said in a report published last week.
One of the key methods the malware employs is a technique DLL side-loading to load a malicious DLL from a digitally signed software application, in this case the x64dbg debugging tool.
It's worth noting here that DLL side-loading attacks leverage the DLL search order mechanism in Windows to plant and then invoke a legitimate application that executes a rogue payload. "Being a legitimate application, x32dbg.exe's valid digital signature can confuse some security tools, enabling threat actors to fly under the radar, maintain persistence, escalate privileges, and bypass file execution restrictions," the researchers said.
The hijacking of x64dbg to load PlugX was disclosed last month by Palo Alto Networks Unit 42, which discovered a new variant of the malware that hides malicious files on removable USB devices to propagate the infection to other Windows hosts.
"Despite advances in security technology, attackers continue to use since it exploits a fundamental trust in legitimate applications," the researchers said.
News URL
https://thehackernews.com/2023/02/plugx-trojan-disguised-as-legitimate.html
Related news
- PipeMagic Trojan Exploits Windows Zero-Day Vulnerability to Deploy Ransomware (source)
- Windows NTLM vulnerability exploited in multiple attack campaigns (CVE-2025-24054) (source)
- Windows NTLM hash leak flaw exploited in phishing attacks on governments (source)
- Play ransomware exploited Windows logging flaw in zero-day attacks (source)