Security News > 2023 > February > North Korea's APT37 Targeting Southern Counterpart with New M2RAT Malware
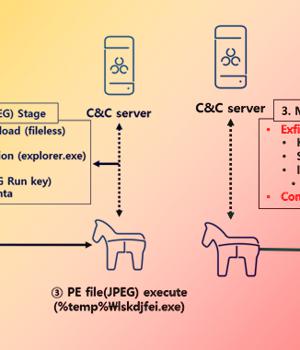
The North Korea-linked threat actor tracked as APT37 has been linked to a piece of new malware dubbed M2RAT in attacks targeting its southern counterpart, suggesting continued evolution of the group's features and tactics.
APT37, also tracked under the monikers Reaper, RedEyes, Ricochet Chollima, and ScarCruft, is linked to North Korea's Ministry of State Security unlike the Lazarus and Kimsuky threat clusters that are part of the Reconnaissance General Bureau.
"APT37's assessed primary mission is covert intelligence gathering in support of DPRK's strategic military, political, and economic interests," the threat intelligence firm said.
The threat actor is known to rely on customized tools such as Chinotto, RokRat, BLUELIGHT, GOLDBACKDOOR, and Dolphin to harvest sensitive information from compromised hosts.
This is not the first time CVE-2017-8291 has been weaponized by North Korean threat actors.
In late 2017, the Lazarus Group was observed targeting South Korean cryptocurrency exchanges and users to deploy Destover malware, according to Recorded Future.
News URL
https://thehackernews.com/2023/02/north-koreas-apt37-targeting-southern.html
Related Vulnerability
| DATE | CVE | VULNERABILITY TITLE | RISK |
|---|---|---|---|
| 2017-04-27 | CVE-2017-8291 | Type Confusion vulnerability in multiple products Artifex Ghostscript through 2017-04-26 allows -dSAFER bypass and remote command execution via .rsdparams type confusion with a "/OutputFile (%pipe%" substring in a crafted .eps document that is an input to the gs program, as exploited in the wild in April 2017. | 7.8 |