Security News > 2022 > December > New Malvertising Campaign via Google Ads Targets Users Searching for Popular Software
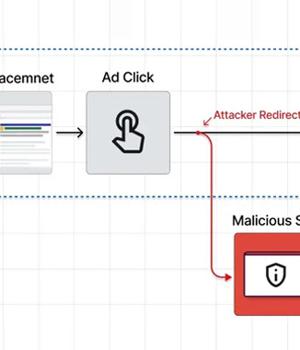
Users searching for popular software are being targeted by a new malvertising campaign that abuses Google Ads to serve trojanized variants that deploy malware, such as Raccoon Stealer and Vidar.
The activity makes use of seemingly credible websites with typosquatted domain names that are surfaced on top of Google search results in the form of malicious ads by hijacking searches for specific keywords.
In one campaign disclosed by Guardio Labs, threat actors have been observed creating a network of benign sites that are promoted on the search engine, which when clicked, redirect the visitors to a phishing page containing a trojanized ZIP archive hosted on Dropbox or OneDrive.
The Vermux operation has mainly singled out users in Canada and the U.S., employing masquerAds sites tailored to searches for AnyDesk and MSI Afterburner to proliferate cryptocurrency miners and Vidar information stealer.
The development marks the continued use of typosquatted domains that mimic legitimate software to lure users into installing rogue Android and Windows apps.
BATLOADER aside, malicious actors have also used malvertising techniques to distribute the IcedID malware via cloned web pages of well-known applications such as Adobe, Brave, Discord, LibreOffice, Mozilla Thunderbird, and TeamViewer.
News URL
https://thehackernews.com/2022/12/new-malvertising-campaign-via-google.html