Security News > 2022 > December > New Truebot Malware Variant Leveraging Netwrix Auditor Bug and Raspberry Robin Worm
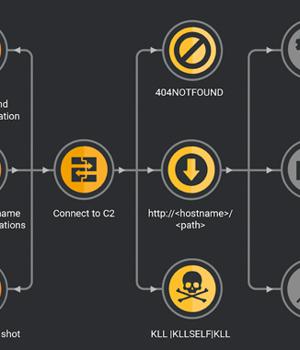
Cybersecurity researchers have reported an increase in TrueBot infections, primarily targeting Mexico, Brazil, Pakistan, and the U.S. Cisco Talos said the attackers behind the operation have moved from using malicious emails to alternative delivery methods such as the exploitation of a now-patched remote code execution flaw in Netwrix auditor as well as the Raspberry Robin worm.
TrueBot is a Windows malware downloader that's attributed to a threat actor tracked by Group-IB as Silence, a Russian-speaking crew believed to share associations with Evil Corp and TA505.
The use of Raspberry Robin - a worm mainly spread through infected USB drives - as a delivery vector for TrueBot was highlighted recently by Microsoft, which it said is part of a "Complex and interconnected malware ecosystem."
In what's a further sign of enmeshed collaboration with other malware families, Raspberry Robin has also been observed deploying FakeUpdates on compromised systems, ultimately leading to ransomware-like behavior linked to Evil Corp. Microsoft is tracking the operators of the USB-based malware as DEV-0856 and the Clop ransomware attacks that happen via Raspberry Robin and TrueBot under the emerging threat cluster DEV-0950.
The latest findings from Cisco Talos show that the Silence APT carried out a small set of attacks between mid-August and September 2022 by abusing a critical RCE vulnerability in Netwrix auditor to download and run TrueBot.
TrueBot infections in October entailed the use of a different attack vector - i.e., Raspberry Robin - underscoring Microsoft's assessment about the USB worm's central role as a malware distribution platform.
News URL
https://thehackernews.com/2022/12/new-truebot-malware-variant-leveraging.html