Security News > 2022 > August > Breaching airgap security: using your phone’s gyroscope as a microphone
At around the same time that the Rhythm Nation story broke, a researcher at Ben-Gurion university of the Negev in Israel published a research paper about resonance problems in mobile phone gyroscopes, as used by popular but apparently innocent programs such as your Compass app.
At the same time, a typical mobile phone microphone can pick up ultrasonic sounds at the other side of the airgap.
As you've figured from the title of Guri's paper it turns out that the gyroscope chip in most modern mobile phones - the chip that detects when you've turned the screen sideways or picked the device up, or that acts as a compass to show your direction - can be used as a very rudimentary microphone.
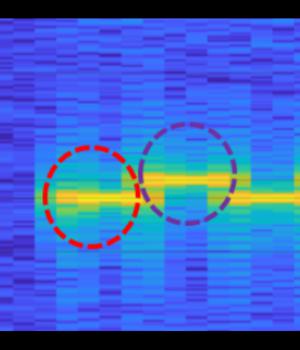
Greatly simplified, the GAIROSCOPE data exfiltration system involves exposing a mobile phone to a range of ultrasonic frequencies and finding out a precise frequency that provoke detectably abnormal resonance in the gyroscope chip, thus creating a detectable signalling medium!
The reason for using the gyroscope is that most mobile phones treat the gyroscope signal as uncontroversial, and allow apps to read out the gyroscope X, Y and Z position values without any special permissions.
In less-secure areas where airgaps are nevertheless used, and where mobile phones are allowed subject to specific settings, the invention of GAIROSCOPE means you will want to verify that users have turned off their "Motion detection" system settings, in addition to blocking access to the microphone.