Security News > 2022 > August > New IoT RapperBot Malware Targeting Linux Servers via SSH Brute-Forcing Attack
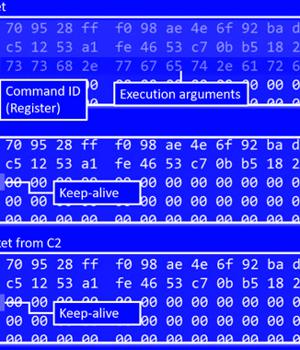
"This family borrows heavily from the original Mirai source code, but what separates it from other IoT malware families is its built-in capability to brute force credentials and gain access to SSH servers instead of Telnet as implemented in Mirai," Fortinet FortiGuard Labs said in a report.
The malware, which gets its name from an embedded URL to a YouTube rap music video in an earlier version, is said to have amassed a growing collection of compromised SSH servers, with over 3,500 unique IP addresses used to scan and brute-force their way into the servers.
"Since mid-July, RapperBot has switched from self-propagation to maintaining remote access into the brute-forced SSH servers," the researchers said.
"This presents a threat to compromised SSH servers as threat actors can access them even after SSH credentials have been changed or SSH password authentication is disabled," the researchers explained.
"Moreover, since the file is replaced, all existing authorized keys are deleted, which prevents legitimate users from accessing the SSH server via public key authentication."
What's clear is that SSH servers with default or guessable credentials are being corralled into a botnet for some unspecified future purpose.
News URL
https://thehackernews.com/2022/08/new-iot-rapperbot-malware-targeting.html
Related news
- New BPFDoor Controller Enables Stealthy Lateral Movement in Linux Server Attacks (source)
- Experts Uncover New XorDDoS Controller, Infrastructure as Malware Expands to Docker, Linux, IoT (source)
- Malicious Go Modules Deliver Disk-Wiping Linux Malware in Advanced Supply Chain Attack (source)
- New PumaBot Botnet Targets Linux IoT Devices to Steal SSH Credentials and Mine Crypto (source)
- New TCESB Malware Found in Active Attacks Exploiting ESET Security Scanner (source)
- Police detains Smokeloader malware customers, seizes servers (source)
- Chinese Hackers Target Linux Systems Using SNOWLIGHT Malware and VShell Tool (source)
- Multi-Stage Malware Attack Uses .JSE and PowerShell to Deploy Agent Tesla and XLoader (source)
- Rogue npm Packages Mimic Telegram Bot API to Plant SSH Backdoors on Linux Systems (source)
- New Android malware steals your credit cards for NFC relay attacks (source)