Security News > 2022 > June > New Syslogk Linux Rootkit Lets Attackers Remotely Command It Using "Magic Packets"
A new covert Linux kernel rootkit named Syslogk has been spotted under development in the wild and cloaking a malicious payload that can be remotely commandeered by an adversary using a magic network traffic packet.
"The Syslogk rootkit is heavily based on Adore-Ng but incorporates new functionalities making the user-mode application and the kernel rootkit hard to detect," Avast security researchers David Álvarez and Jan Neduchal said in a report published Monday.
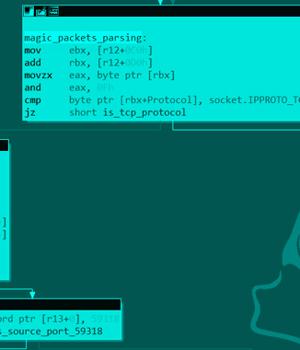
Besides its capabilities to hide network traffic from utilities like netstat, housed within the rootkit is a payload named "PgSD93ql" that's nothing but a C-based compiled backdoor trojan named Rekoobe and gets triggered upon receiving a magic packet.
Specifically, Syslogk is engineered to inspect TCP packets containing the source port number 59318 to launch the Rekoobe malware.
Contains a key that is hardcoded in the rootkit and located in a variable offset of the magic packet.
Syslogk adds to a growing list of newly discovered evasive Linux malware such as BPFDoor and Symbiote, highlighting how cyber criminals are increasingly targeting Linux servers and cloud infrastructure to launch ransomware campaigns, cryptojacking attacks, and other illicit activity.
News URL
https://thehackernews.com/2022/06/new-syslogk-linux-rootkit-lets.html