Security News > 2022 > April > Product showcase: Enclave – using zero trust network access to simplify your networks
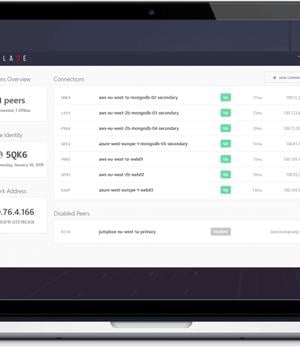
Administrators can define an Enclave policy similar to "Devs can access the test environment", and Enclave takes care of the rest, regardless of what physical network the developer is on, and whether the test environment is on-prem, in the cloud, or an IoT device.
Enclave is default-deny, so Administrators can effortlessly craft precision access across the organisation regardless of what network each system is on, without needing to install appliances or proxy servers or opening firewall ports to the Internet.
Once remote access traffic has arrived at the perimeter, the internal network can still be a complex web of tooling and configuration that tries to segment and route network traffic to its intended destination, which often then tends to cross to the east-west traffic pattern inside the organisation, and can often be several more firewall and VPN hops away from the original entry point.
By defining a Zero Trust Overlay Network using Enclave, segmented however you wish, the distinction between north-south and east-west traffic patterns, location and bearer all become completely irrelevant, transforming the network from a blocker to an agile and dynamic enabler.
Enclave creates fully audited peer-to-peer and end-to-end encrypted tunnels and so is able to always utilise the best network route and all available network capacity between two points, without any bottlenecks.
Enclave is deployed as agent-based software on user devices or servers, and adds a new network adapter to transparently create the Enclave Zero Trust Overlay Network.
News URL
https://www.helpnetsecurity.com/2022/04/13/product-showcase-enclave-using-zero-trust-network-access/