Security News > 2022 > February > Chinese Experts Uncover Details of Equation Group's Bvp47 Covert Hacking Tool
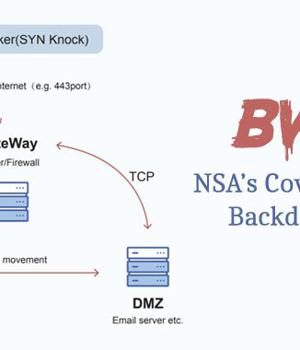
Researchers from China's Pangu Lab have disclosed details of a "Top-tier" backdoor put to use by the Equation Group, an advanced persistent threat with alleged ties to the cyber-warfare intelligence-gathering unit of the U.S. National Security Agency.
Equation Group's malware toolset became public knowledge in 2016 when a group calling itself the Shadow Brokers leaked the entire tranche of exploits used by the elite hacking team, with Kaspersky uncovering code-level similarities between the stolen files and that of samples identified as used by the threat actor.
Pangu Lab's attribution to Equation Group stems from overlaps with exploits contained in a GPG-encrypted archive file published by the Shadow Brokers - "Eqgrp-auction-file.tar.xz.gpg" - as part of a failed auction of the cyber weapons in August 2016.
"The 'tipoffs' directory contains the RSA asymmetric algorithm private key used in the Bvp47 covert channel [for] command execution and other operations. On this basis, it can be confirmed that Bvp47 is from [the] Equation group."
"Judging from the attack tools related to the organization, including Bvp47, Equation group is indeed a first-class hacking group," the researchers concluded.
"The tool is well-designed, powerful, and widely adapted. Its network attack capability equipped by 0day vulnerabilities was unstoppable, and its data acquisition under covert control was with little effort. The Equation Group is in a dominant position in national-level cyberspace confrontation."
News URL
https://thehackernews.com/2022/02/chinese-experts-uncover-details-of.html