Security News > 2022 > February > CISA Alerts on Actively Exploited Flaws in Zabbix Network Monitoring Platform
The U.S. Cybersecurity and Infrastructure Security Agency has warned of active exploitation of two security flaws impacting Zabbix open-source enterprise monitoring platform, adding them to its Known Exploited Vulnerabilities Catalog.
On top of that, CISA is also recommending that Federal Civilian Executive Branch agencies patch all systems against the vulnerabilities by March 8, 2022 to reduce their exposure to potential cyberattacks.
Tracked as CVE-2022-23131 and CVE-2022-23134, the shortcomings could lead to the compromise of complete networks, enabling a malicious unauthenticated actor to escalate privileges and gain admin access to the Zabbix Frontend as well as make configuration changes.
Thomas Chauchefoin from SonarSource has been credited with discovering and reporting the two flaws, which affect Zabbix Web Frontend versions up to and including 5.4.8, 5.0.18 and 4.0.36.
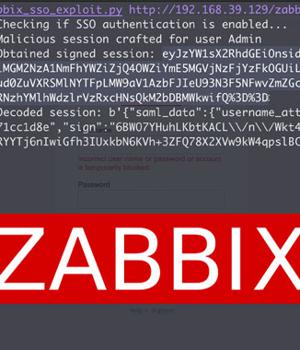
Both the flaws are the result of what the company calls "Unsafe session storage," allowing attackers to bypass authentication and execute arbitrary code.
It's worth pointing out that the flaws only impact instances where Security Assertion Markup Language Single sign-on authentication is enabled.
News URL
https://thehackernews.com/2022/02/cisa-alerts-on-actively-exploited-flaws.html
Related Vulnerability
| DATE | CVE | VULNERABILITY TITLE | RISK |
|---|---|---|---|
| 2022-01-13 | CVE-2022-23134 | Improper Authentication vulnerability in multiple products After the initial setup process, some steps of setup.php file are reachable not only by super-administrators, but by unauthenticated users as well. | 5.3 |
| 2022-01-13 | CVE-2022-23131 | Authentication Bypass by Spoofing vulnerability in Zabbix In the case of instances where the SAML SSO authentication is enabled (non-default), session data can be modified by a malicious actor, because a user login stored in the session was not verified. | 9.8 |