Security News > 2022 > February > Iranian State Broadcaster IRIB Hit by Destructive Wiper Malware
An investigation into the cyberattack targeting Iranian national media corporation, Islamic Republic of Iran Broadcasting, in late January 2022 resulted in the deployment of a wiper malware and other custom implants, as the country's national infrastructure continues to face a wave of attacks aimed at inflicting serious damage.
The 10-second attack, which took place on January 27, involved the breach of state broadcaster IRIB to air pictures of Mujahedin-e-Khalq Organization leaders Maryam and Massoud Rajavi alongside a call for the assassination of the Supreme Leader Ayatollah Ali Khamenei.
"This is an extremely complex attack and only the owners of this technology could exploit and damage the backdoors and features that are installed on the systems," Deputy IRIB chief Ali Dadi was quoted as saying to state TV channel IRINN. Also deployed during the course of the hack were custom-made malware capable of taking screenshots of the victims' screens as well as backdoors, batch scripts, and configuration files used to install and configure the malicious executables.
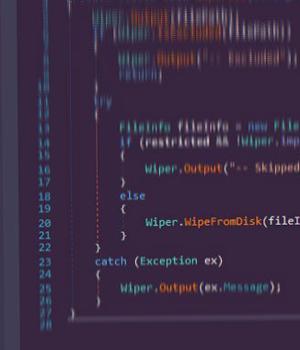
Installing the wiper malware in an attempt to disrupt operations in the hacked networks.
Behind the scenes, the attack involved interrupting the video stream using a batch script to delete the executable associated with TFI Arista Playout Server, a broadcasting software used by IRIB, and play the video file in a loop.
"On one hand, the attackers managed to pull off a complicated operation to bypass security systems and network segmentation, penetrate the broadcaster's networks, produce and run the malicious tools that heavily rely on internal knowledge of the broadcasting software used by victims, all while staying under the radar during the reconnaissance and initial intrusion stages," the researchers said.
News URL
https://thehackernews.com/2022/02/iranian-state-broadcaster-irib-hits-by_21.html