Security News > 2021 > December > How to visualise security and threat information in Microsoft Power BI
Want a custom security dashboard to bring together data from multiple places? Microsoft Power BI can do that and help you spot what's changing.
Obviously, you can use Microsoft Power BI to monitor Power BI usage, using the Power BI Admin APIs to track who is accessing data and visualisations and make sure it's only the people you expect to have access to what might be critical or confidential business information.
"Microsoft Cloud App Security enables organizations to monitor and control, in real time, risky Power BI sessions such as user access from unmanaged devices. Security administrators can define policies to control user actions, such as downloading reports with sensitive information. With Power BI's MCAS integration, you can set monitoring policy and anomaly detection and augment Power BI user activity with the MCAS activity log."
A security information and event management system like Azure Sentinel will pull together that kind of information for you, but the advantage of Power BI is how easy it is to create exactly the right reports and visualisations for what's important to you, along with AI-powered analytics that find and highlight anomalies and outliers in the data.
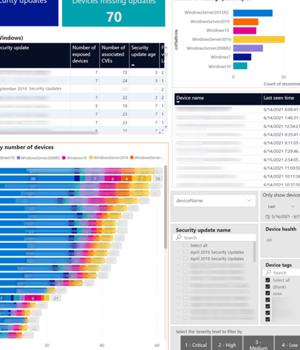
There are Power BI content packs for various security tools, and several of Microsoft's security tools have APIs so you can bring that information into Power BI. Microsoft Defender for Endpoint has APIs to access threat and vulnerability data for software inventory, software vulnerabilities and devices that have been detected as being misconfigured - which includes missing Windows security updates.
You can pull a full snapshot or just the changes since you last pulled the data, depending on whether you want to look back at security data over time to see patterns and see if security policies you've introduced are making a difference or whether you're looking for the same kind of real-time overview that Power BI can give you for IoT devices.
News URL
Related news
- AI threats and workforce shortages put pressure on security leaders (source)
- URGENT: Microsoft Patches 57 Security Flaws, Including 6 Actively Exploited Zero-Days (source)
- Patch Tuesday: Microsoft Fixes 57 Security Flaws – Including Active Zero-Days (source)
- 5 Identity Threat Detection & Response Must-Haves for Super SaaS Security (source)
- Hidden Threats: How Microsoft 365 Backups Store Risks for Future Attacks (source)
- AI agents swarm Microsoft Security Copilot (source)
- After Detecting 30B Phishing Attempts, Microsoft Adds Even More AI to Its Security Copilot (source)
- Android Malware Exploits a Microsoft-Related Security Blind Spot to Avoid Detection (source)
- Week in review: Chrome sandbox escape 0-day fixed, Microsoft adds new AI agents to Security Copilot (source)
- April 2025 Patch Tuesday forecast: More AI security introduced by Microsoft (source)