Security News > 2021 > November > Mekotio Banking Trojan Resurfaces with New Attacking and Stealth Techniques
The operators behind the Mekotio banking trojan have resurfaced with a shift in its infection flow so as to stay under the radar and evade security software, while staging nearly 100 attacks over the last three months.
The development comes after Spanish law enforcement agencies in July 2021 arrested 16 individuals belonging to a criminal network in connection with operating Mekotio and another banking malware called Grandoreiro as part of a social engineering campaign targeting financial institutions in Europe.
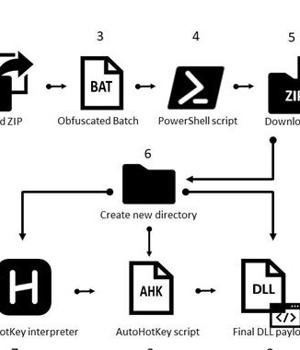
The evolved version of the Mekotio malware strain is designed for compromising Windows systems with an attack chain that commences with phishing emails masquerading as pending tax receipts and containing a link to a ZIP file or a ZIP file as an attachment.
Clicking open the ZIP archive triggers the execution of a batch script that, in turn, runs a PowerShell script to download a second-stage ZIP file.
This secondary ZIP file houses three different files - an AutoHotkey interpreter, an AHK script, and the Mekotio DLL payload. The aforementioned PowerShell script then calls the AHK interpreter to execute the AHK script, which runs the DLL payload to steal passwords from online banking portals and exfiltrate the results back to a remote server.
"There's a very real danger in the Mekotio banker stealing usernames and passwords, in order to gain entry into financial institutions," Check Point's Kobi Eisenkraft said.
News URL
https://thehackernews.com/2021/11/mekotio-banking-trojan-resurfaces-with.html