Security News > 2021 > October > New Study Links Seemingly Disparate Malware Attacks to Chinese Hackers
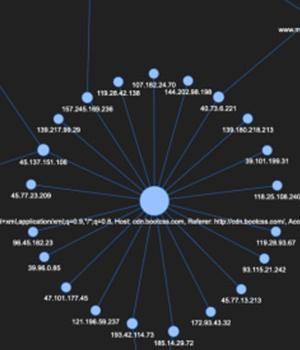
Chinese cyber espionage group APT41 has been linked to seemingly disparate malware campaigns, according to fresh research that has mapped together additional parts of the group's network infrastructure to hit upon a state-sponsored campaign that takes advantage of COVID-themed phishing lures to target victims in India.
APT41 is a moniker assigned to a prolific Chinese cyber threat group that carries out state-sponsored espionage activity in conjunction with financially motivated operations for personal gain as far back as 2012.
The group is known for staging cybercrime intrusions that are aimed at stealing source code and digital certificates, virtual currency manipulation, and deploying ransomware, as well as executing software supply chain compromises by injecting malicious code into legitimate files prior to distribution of software updates.
BlackBerry, which found a similar C2 profile uploaded to GitHub on March 29 by a Chinese security researcher with the pseudonym "1135," used the metadata configuration data to identify a fresh cluster of domains related to APT41 that attempt to masquerade Beacon traffic look like legitimate traffic from Microsoft sites, with IP address and domain name overlaps found in campaigns linked to the Higaisa APT group, and that of Winnti disclosed over the past year.
Although a set of intrusions using similar phishing lures and uncovered in September 2020 were pinned on the Evilnum group, BlackBerry said the compromise indicators point to an APT41-affiliated campaign.
"With the resources of a nation-state level threat group, it's possible to create a truly staggering level of diversity in their infrastructure," the researchers said, adding by piecing together the malicious activities of the threat actor via public sharing of information, it's possible to "Uncover the tracks that the cybercriminals involved worked so hard to hide."
News URL
Related news
- Chinese Hackers Exploit MAVInject.exe to Evade Detection in Targeted Cyber Attacks (source)
- Chinese hackers use custom malware to spy on US telecom networks (source)
- Ivanti zero-day attacks infected devices with custom malware (source)
- US Treasury hack linked to Silk Typhoon Chinese state hackers (source)
- Hackers exploit critical Aviatrix Controller RCE flaw in attacks (source)
- Russia-Linked Hackers Target Kazakhstan in Espionage Campaign with HATVIBE Malware (source)
- Hackers use FastHTTP in new high-speed Microsoft 365 password attacks (source)
- FBI wipes Chinese PlugX malware from over 4,000 US computers (source)
- FBI deletes Chinese PlugX malware from thousands of US computers (source)
- FBI wipes Chinese PlugX malware from thousands of Windows PCs in America (source)