Security News > 2021 > September > New FinSpy Malware Variant Infects Windows Systems With UEFI Bootkit
Commercially developed FinFisher surveillanceware has been upgraded to infect Windows devices using a UEFI bootkit using a trojanized Windows Boot Manager, marking a shift in infection vectors that allow it to elude discovery and analysis.
While the tool was previously deployed through tampered installers of legitimate applications such as TeamViewer, VLC, and WinRAR that were backdoored with an obfuscated downloader, subsequent updates in 2014 enabled infections via Master Boot Record bootkits with the goal of injecting a malicious loader in a manner that's engineered to slip past security tools.
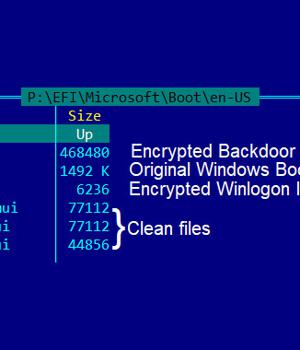
The latest feature to be added is the ability to deploy a UEFI bootkit to load FinSpy, with new samples exhibiting properties that replaced the Windows UEFI boot loader with a malicious variant as well as boasting of four layers of obfuscation and other detection-evasion methods to slow down reverse engineering and analysis.
UEFI is a firmware interface and an improvement over basic input/output system with support for Secure Boot, which ensures the integrity of the operating system to ensure no malware has interfered with the boot process.
Because UEFI facilitates the loading of the operating system itself, bootkit infections are not only resistant to OS reinstallation or replacement of the hard drive but are also inconspicuous to security solutions running within the operating system.
"While in this case the attackers did not infect the UEFI firmware itself, but its next boot stage, the attack was particularly stealthy, as the malicious module was installed on a separate partition and could control the boot process of the infected machine," the researchers added.
News URL
http://feedproxy.google.com/~r/TheHackersNews/~3/F3qIQhPCctQ/new-finspy-malware-variant-infects.html