Security News > 2021 > September > Microsoft Warns of FoggyWeb Malware Targeting Active Directory FS Servers
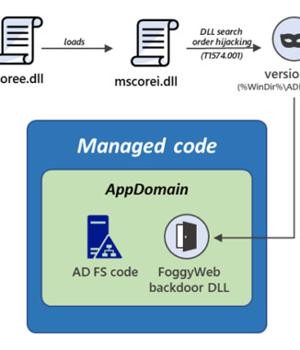
Microsoft on Monday revealed new malware deployed by the hacking group behind the SolarWinds supply chain attack last December to deliver additional payloads and steal sensitive information from Active Directory Federation Services servers.
"Once Nobelium obtains credentials and successfully compromises a server, the actor relies on that access to maintain persistence and deepen its infiltration using sophisticated malware and tools," MSTIC researchers said.
"Nobelium uses FoggyWeb to remotely exfiltrate the configuration database of compromised AD FS servers, decrypted token-signing certificate, and token-decryption certificate, as well as to download and execute additional components."
FoggyWeb, installed using a loader by exploiting a technique called DLL search order hijacking, is capable of transmitting sensitive information from a compromised AD FS server as well as receive and execute additional malicious payloads retrieved from a remote attacker-controlled server.
"Protecting AD FS servers is key to mitigating Nobelium attacks," the researchers said.
"Detecting and blocking malware, attacker activity, and other malicious artifacts on AD FS servers can break critical steps in known Nobelium attack chains. Customers should review their AD FS Server configuration and implement changes to secure these systems from attacks."
News URL
Related news
- Microsoft Teams tactics, malware connect Black Basta, Cactus ransomware (source)
- Microsoft admits GitHub hosted malware that infected almost a million devices (source)
- Microsoft: New RAT malware used for crypto theft, reconnaissance (source)
- Microsoft Trust Signing service abused to code-sign malware (source)
- Microsoft Trusted Signing service abused to code-sign malware (source)
- New Android malware uses Microsoft’s .NET MAUI to evade detection (source)
- Android Malware Exploits a Microsoft-Related Security Blind Spot to Avoid Detection (source)
- Hijacked Microsoft web domain injects spam into SharePoint servers (source)
- Outlaw Group Uses SSH Brute-Force to Deploy Cryptojacking Malware on Linux Servers (source)
- Microsoft Warns of Tax-Themed Email Attacks Using PDFs and QR Codes to Deliver Malware (source)