Security News > 2021 > April > Hackers Targeting professionals With 'more_eggs' Malware via LinkedIn Job Offers
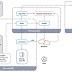
A new spear-phishing campaign is targeting professionals on LinkedIn with weaponized job offers in an attempt to infect targets with a sophisticated backdoor trojan called "More eggs."
To increase the odds of success, the phishing lures take advantage of malicious ZIP archive files that have the same name as that of the victims' job titles taken from their LinkedIn profiles.
If the LinkedIn member's job is listed as Senior Account Executive-International Freight the malicious zip file would be titled Senior Account Executive-International Freight position," cybersecurity firm eSentire's Threat Response Unit said in an analysis.
"Upon opening the fake job offer, the victim unwittingly initiates the stealthy installation of the fileless backdoor, more eggs."
Campaigns delivering more eggs using the same modus operandi have been spotted at least since 2018, with the backdoor attributed to a malware-as-a-service provider called Golden Chickens.
Once installed, more eggs maintains a stealthy profile by hijacking legitimate Windows processes while presenting the decoy "Employment application" document to distract targets from ongoing background tasks triggered by the malware.
News URL
Related news
- New Linux Malware ‘Auto-Color’ Grants Hackers Full Remote Access to Compromised Systems (source)
- Chinese FamousSparrow hackers deploy upgraded malware in attacks (source)
- North Korean Hackers Deploy BeaverTail Malware via 11 Malicious npm Packages (source)
- Chinese Hackers Target Linux Systems Using SNOWLIGHT Malware and VShell Tool (source)
- State-Sponsored Hackers Weaponize ClickFix Tactic in Targeted Malware Campaigns (source)
- Chinese hackers target Russian govt with upgraded RAT malware (source)
- Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery (source)