Security News > 2021 > January > New Docker Container Escape Bug Affects Microsoft Azure Functions
Cybersecurity researcher Paul Litvak today disclosed an unpatched vulnerability in Microsoft Azure Functions that could be used by an attacker to escalate privileges and escape the Docker container used for hosting them.
Following disclosure to Microsoft, the Windows maker is said to have "Determined that the vulnerability has no security impact on Function users, since the host itself is still protected by another defense boundary against the elevated position we reached in the container host."
Azure Functions, analogous to Amazon AWS Lambda, is a serverless solution that allows users to run event-triggered code without having to provision or manage infrastructure explicitly while simultaneously making it possible to scale and allocate compute and resources based on demand.
By incorporating Docker into the mix, it makes it possible for developers to easily deploy and run Azure Functions either in the cloud or on-premises.
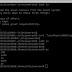
Since the trigger code is an event that is configured to call an Azure Function, the researchers first created an HTTP trigger to gain a foothold over the Function container, using it to find sockets belonging to processes with "Root" privileges.
In the final step, the extended privileges assigned to the container were abused to escape the Docker container and run an arbitrary command on the host.