Security News > 2021 > January > Here's How SolarWinds Hackers Stayed Undetected for Long Enough
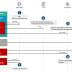
Microsoft on Wednesday shared more specifics about the tactics, techniques, and procedures adopted by the attackers behind the SolarWinds hack to stay under the radar and avoid detection, as cybersecurity companies work towards getting a "Clearer picture" of one of the most sophisticated attacks in recent history.
"The attackers behind Solorigate are skilled campaign operators who carefully planned and executed the attack, remaining elusive while maintaining persistence," researchers from Microsoft 365 Defender Research Team, Microsoft Threat Intelligence Center, and Microsoft Cyber Defense Operations Center said.
Microsoft's timeline of the attacks shows that the fully-functional Sunburst DLL backdoor was compiled and deployed onto SolarWinds' Orion platform on February 20, following which it was distributed in the form of tampered updates sometime in late March.
Answers as to how and when the transition from Sunburst to Raindrop occurs has yielded little definitive clues, even if it appears that the attackers deliberately separated the Cobalt Strike loader's execution from the SolarWinds process as an OpSec measure.
The idea is that in the event the Cobalt Strike implants were discovered on target networks, it wouldn't reveal the compromised SolarWinds binary and the supply chain attack that led to its deployment in the first place.
"With Solorigate, the attackers took advantage of broad role assignments, permissions that exceeded role requirements, and in some cases abandoned accounts and applications which should have had no permissions at all," Alex Weinert, Microsoft's director of identity security, said.