Security News > 2020 > October > Browser Bugs Exploited to Install 2 New Backdoors on Targeted Computers
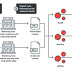
Dubbed "Operation Earth Kitsune" by Trend Micro, the campaign involves the use of SLUB malware and two new backdoors - dneSpy and agfSpy - to exfiltrate system information and gain additional control of the compromised machine.
Although previous operations involving SLUB used the GitHub repository platform to download malicious code snippets onto the Windows system and post the results of the execution to an attacker-controlled private Slack channel, the latest iteration of the malware has targeted Mattermost, a Slack-like open-source collaborative messaging system.
"In total, we found the campaign using five C&C servers, seven samples, and exploits for four N-day bugs."
The difference in the infection vector notwithstanding, the exploit chain proceeds through the same sequence of steps - initiate a connection with the C&C server, receive the dropper, which then checks for the presence of anti-malware solutions on the target system before proceeding to download the three backdoor samples and executing them.
"The central C&C server's response is actually the next-stage C&C server's domain/IP, which dneSpy has to communicate with to receive further instructions."
News URL
http://feedproxy.google.com/~r/TheHackersNews/~3/Adfwd-GBINQ/browser-exploit-backdoor.html