Vulnerabilities > CVE-2017-8890 - Double Free vulnerability in multiple products
Attack vector
LOCAL Attack complexity
LOW Privileges required
LOW Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c in the Linux kernel through 4.10.15 allows attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call.
Vulnerable Configurations
Common Weakness Enumeration (CWE)
Nessus
NASL family Fedora Local Security Checks NASL id FEDORA_2017-6F06BE3FE9.NASL description Rebase to 4.11.3 Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2017-06-01 plugin id 100563 published 2017-06-01 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100563 title Fedora 25 : kernel (2017-6f06be3fe9) code #%NASL_MIN_LEVEL 80502 # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Fedora Security Advisory FEDORA-2017-6f06be3fe9. # include("compat.inc"); if (description) { script_id(100563); script_version("3.6"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/06/04"); script_cve_id("CVE-2017-8890", "CVE-2017-9074", "CVE-2017-9075", "CVE-2017-9076", "CVE-2017-9077"); script_xref(name:"FEDORA", value:"2017-6f06be3fe9"); script_name(english:"Fedora 25 : kernel (2017-6f06be3fe9)"); script_summary(english:"Checks rpm output for the updated package."); script_set_attribute( attribute:"synopsis", value:"The remote Fedora host is missing a security update." ); script_set_attribute( attribute:"description", value: "Rebase to 4.11.3 Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues." ); script_set_attribute( attribute:"see_also", value:"https://bodhi.fedoraproject.org/updates/FEDORA-2017-6f06be3fe9" ); script_set_attribute( attribute:"solution", value:"Update the affected kernel package." ); script_set_cvss_base_vector("CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fedoraproject:fedora:kernel"); script_set_attribute(attribute:"cpe", value:"cpe:/o:fedoraproject:fedora:25"); script_set_attribute(attribute:"vuln_publication_date", value:"2017/05/10"); script_set_attribute(attribute:"patch_publication_date", value:"2017/05/31"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/06/01"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Fedora Local Security Checks"); script_dependencies("ssh_get_info.nasl", "linux_alt_patch_detect.nasl"); script_require_keys("Host/local_checks_enabled", "Host/RedHat/release", "Host/RedHat/rpm-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); include("ksplice.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/RedHat/release"); if (isnull(release) || "Fedora" >!< release) audit(AUDIT_OS_NOT, "Fedora"); os_ver = pregmatch(pattern: "Fedora.*release ([0-9]+)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "Fedora"); os_ver = os_ver[1]; if (! preg(pattern:"^25([^0-9]|$)", string:os_ver)) audit(AUDIT_OS_NOT, "Fedora 25", "Fedora " + os_ver); if (!get_kb_item("Host/RedHat/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$") audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "Fedora", cpu); if (get_one_kb_item("Host/ksplice/kernel-cves")) { rm_kb_item(name:"Host/uptrack-uname-r"); cve_list = make_list("CVE-2017-8890", "CVE-2017-9074", "CVE-2017-9075", "CVE-2017-9076", "CVE-2017-9077"); if (ksplice_cves_check(cve_list)) { audit(AUDIT_PATCH_INSTALLED, "KSplice hotfix for FEDORA-2017-6f06be3fe9"); } else { __rpm_report = ksplice_reporting_text(); } } flag = 0; if (rpm_check(release:"FC25", reference:"kernel-4.11.3-200.fc25")) flag++; if (flag) { security_report_v4( port : 0, severity : SECURITY_HOLE, extra : rpm_report_get() ); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "kernel"); }NASL family Fedora Local Security Checks NASL id FEDORA_2017-85744F8AA9.NASL description The 4.10.17 stable kernel update contains a number of important fixes across the tree. Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2017-05-30 plugin id 100491 published 2017-05-30 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100491 title Fedora 24 : kernel (2017-85744f8aa9) code #%NASL_MIN_LEVEL 80502 # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Fedora Security Advisory FEDORA-2017-85744f8aa9. # include("compat.inc"); if (description) { script_id(100491); script_version("3.6"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/06/04"); script_cve_id("CVE-2017-8890", "CVE-2017-9059", "CVE-2017-9074", "CVE-2017-9075", "CVE-2017-9076", "CVE-2017-9077"); script_xref(name:"FEDORA", value:"2017-85744f8aa9"); script_name(english:"Fedora 24 : kernel (2017-85744f8aa9)"); script_summary(english:"Checks rpm output for the updated package."); script_set_attribute( attribute:"synopsis", value:"The remote Fedora host is missing a security update." ); script_set_attribute( attribute:"description", value: "The 4.10.17 stable kernel update contains a number of important fixes across the tree. Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues." ); script_set_attribute( attribute:"see_also", value:"https://bodhi.fedoraproject.org/updates/FEDORA-2017-85744f8aa9" ); script_set_attribute( attribute:"solution", value:"Update the affected kernel package." ); script_set_cvss_base_vector("CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:fedoraproject:fedora:kernel"); script_set_attribute(attribute:"cpe", value:"cpe:/o:fedoraproject:fedora:24"); script_set_attribute(attribute:"vuln_publication_date", value:"2017/05/10"); script_set_attribute(attribute:"patch_publication_date", value:"2017/05/26"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/05/30"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Fedora Local Security Checks"); script_dependencies("ssh_get_info.nasl", "linux_alt_patch_detect.nasl"); script_require_keys("Host/local_checks_enabled", "Host/RedHat/release", "Host/RedHat/rpm-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); include("ksplice.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/RedHat/release"); if (isnull(release) || "Fedora" >!< release) audit(AUDIT_OS_NOT, "Fedora"); os_ver = pregmatch(pattern: "Fedora.*release ([0-9]+)", string:release); if (isnull(os_ver)) audit(AUDIT_UNKNOWN_APP_VER, "Fedora"); os_ver = os_ver[1]; if (! preg(pattern:"^24([^0-9]|$)", string:os_ver)) audit(AUDIT_OS_NOT, "Fedora 24", "Fedora " + os_ver); if (!get_kb_item("Host/RedHat/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$") audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "Fedora", cpu); if (get_one_kb_item("Host/ksplice/kernel-cves")) { rm_kb_item(name:"Host/uptrack-uname-r"); cve_list = make_list("CVE-2017-8890", "CVE-2017-9059", "CVE-2017-9074", "CVE-2017-9075", "CVE-2017-9076", "CVE-2017-9077"); if (ksplice_cves_check(cve_list)) { audit(AUDIT_PATCH_INSTALLED, "KSplice hotfix for FEDORA-2017-85744f8aa9"); } else { __rpm_report = ksplice_reporting_text(); } } flag = 0; if (rpm_check(release:"FC24", reference:"kernel-4.10.17-100.fc24")) flag++; if (flag) { security_report_v4( port : 0, severity : SECURITY_HOLE, extra : rpm_report_get() ); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "kernel"); }NASL family Debian Local Security Checks NASL id DEBIAN_DLA-993.NASL description Several vulnerabilities have been discovered in the Linux kernel that may lead to a privilege escalation, denial of service or information leaks. CVE-2017-7487 Li Qiang reported a reference counter leak in the ipxitf_ioctl function which may result into a use-after-free vulnerability, triggerable when a IPX interface is configured. CVE-2017-7645 Tuomas Haanpaa and Matti Kamunen from Synopsys Ltd discovered that the NFSv2 and NFSv3 server implementations are vulnerable to an out-of-bounds memory access issue while processing arbitrarily long arguments sent by NFSv2/NFSv3 PRC clients, leading to a denial of service. CVE-2017-7895 Ari Kauppi from Synopsys Ltd discovered that the NFSv2 and NFSv3 server implementations do not properly handle payload bounds checking of WRITE requests. A remote attacker with write access to a NFS mount can take advantage of this flaw to read chunks of arbitrary memory from both kernel-space and user-space. CVE-2017-8890 It was discovered that the net_csk_clone_lock() function allows a remote attacker to cause a double free leading to a denial of service or potentially have other impact. CVE-2017-8924 Johan Hovold found that the io_ti USB serial driver could leak sensitive information if a malicious USB device was connected. CVE-2017-8925 Johan Hovold found a reference counter leak in the omninet USB serial driver, resulting in a use-after-free vulnerability. This can be triggered by a local user permitted to open tty devices. CVE-2017-9074 Andrey Konovalov reported that the IPv6 fragmentation implementation could read beyond the end of a packet buffer. A local user or guest VM might be able to use this to leak sensitive information or to cause a denial of service (crash). CVE-2017-9075 Andrey Konovalov reported that the SCTP/IPv6 implementation wrongly initialised address lists on connected sockets, resulting in a use-after-free vulnerability, a similar issue to CVE-2017-8890. This can be triggered by any local user. CVE-2017-9076 / CVE-2017-9077 Cong Wang found that the TCP/IPv6 and DCCP/IPv6 implementations wrongly initialised address lists on connected sockets, a similar issue to CVE-2017-9075. CVE-2017-9242 Andrey Konovalov reported a packet buffer overrun in the IPv6 implementation. A local user could use this for denial of service (memory corruption; crash) and possibly for privilege escalation. CVE-2017-1000364 The Qualys Research Labs discovered that the size of the stack guard page is not sufficiently large. The stack-pointer can jump over the guard-page and moving from the stack into another memory region without accessing the guard-page. In this case no page-fault exception is raised and the stack extends into the other memory region. An attacker can exploit this flaw for privilege escalation. The default stack gap protection is set to 256 pages and can be configured via the stack_guard_gap kernel parameter on the kernel command line. Further details can be found at https://www.qualys.com/2017/06/19/stack-clash/stack-clash.tx t For Debian 7 last seen 2020-03-17 modified 2017-06-20 plugin id 100876 published 2017-06-20 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100876 title Debian DLA-993-2 : linux regression update (Stack Clash) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3345-1.NASL description USN 3324-1 fixed a vulnerability in the Linux kernel. However, that fix introduced regressions for some Java applications. This update addresses the issue. We apologize for the inconvenience. Roee Hay discovered that the parallel port printer driver in the Linux kernel did not properly bounds check passed arguments. A local attacker with write access to the kernel command line arguments could use this to execute arbitrary code. (CVE-2017-1000363) It was discovered that a double-free vulnerability existed in the IPv4 stack of the Linux kernel. An attacker could use this to cause a denial of service (system crash). (CVE-2017-8890) Andrey Konovalov discovered an IPv6 out-of-bounds read error in the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 101156 published 2017-06-30 reporter Ubuntu Security Notice (C) 2017-2019 Canonical, Inc. / NASL script (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/101156 title Ubuntu 17.04 : linux, linux-raspi2 vulnerabilities (USN-3345-1) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2061-1.NASL description This update for the Linux Kernel 3.12.67-60_64_18 fixes several issues. The following security bugs were fixed : - CVE-2017-7533: A bug in inotify code allowed local users to escalate privilege (bsc#1050751). - CVE-2017-7645: The NFSv2/NFSv3 server in the nfsd subsystem in the Linux kernel allowed remote attackers to cause a denial of service (system crash) via a long RPC reply, related to net/sunrpc/svc.c, fs/nfsd/nfs3xdr.c, and fs/nfsd/nfsxdr.c (bsc#1046191). - CVE-2017-2636: Race condition in drivers/tty/n_hdlc.c in the Linux kernel allowed local users to gain privileges or cause a denial of service (double free) by setting the HDLC line discipline (bsc#1027575). - CVE-2017-9242: The __ip6_append_data function in net/ipv6/ip6_output.c in the Linux kernel is too late in checking whether an overwrite of an skb data structure may occur, which allowed local users to cause a denial of service (system crash) via crafted system calls (bsc#1042892). - CVE-2017-8890: The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c in the Linux kernel allowed attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call (bsc#1038564). Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 102252 published 2017-08-08 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102252 title SUSE SLES12 Security Update : kernel (SUSE-SU-2017:2061-1) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2092-1.NASL description This update for the Linux Kernel 3.12.69-60_64_32 fixes several issues. The following security bugs were fixed : - CVE-2017-7533: A bug in inotify code allowed local users to escalate privilege (bsc#1050751). - CVE-2017-7645: The NFSv2/NFSv3 server in the nfsd subsystem in the Linux kernel allowed remote attackers to cause a denial of service (system crash) via a long RPC reply, related to net/sunrpc/svc.c, fs/nfsd/nfs3xdr.c, and fs/nfsd/nfsxdr.c (bsc#1046191). - CVE-2017-2636: Race condition in drivers/tty/n_hdlc.c in the Linux kernel allowed local users to gain privileges or cause a denial of service (double free) by setting the HDLC line discipline (bsc#1027575). - CVE-2017-9242: The __ip6_append_data function in net/ipv6/ip6_output.c in the Linux kernel is too late in checking whether an overwrite of an skb data structure may occur, which allowed local users to cause a denial of service (system crash) via crafted system calls (bsc#1042892). - CVE-2017-8890: The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c in the Linux kernel allowed attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call (bsc#1038564). Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 102311 published 2017-08-09 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102311 title SUSE SLES12 Security Update : kernel (SUSE-SU-2017:2092-1) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2091-1.NASL description This update for the Linux Kernel 3.12.69-60_64_35 fixes several issues. The following security bugs were fixed : - CVE-2017-7533: A bug in inotify code allowed local users to escalate privilege (bsc#1050751). - CVE-2017-7645: The NFSv2/NFSv3 server in the nfsd subsystem in the Linux kernel allowed remote attackers to cause a denial of service (system crash) via a long RPC reply, related to net/sunrpc/svc.c, fs/nfsd/nfs3xdr.c, and fs/nfsd/nfsxdr.c (bsc#1046191). - CVE-2017-9242: The __ip6_append_data function in net/ipv6/ip6_output.c in the Linux kernel is too late in checking whether an overwrite of an skb data structure may occur, which allowed local users to cause a denial of service (system crash) via crafted system calls (bsc#1042892). - CVE-2017-8890: The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c in the Linux kernel allowed attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call (bsc#1038564). Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 102310 published 2017-08-09 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102310 title SUSE SLES12 Security Update : kernel (SUSE-SU-2017:2091-1) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2017-1842.NASL description From Red Hat Security Advisory 2017:1842 : An update for kernel is now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The kernel packages contain the Linux kernel, the core of any Linux operating system. Security Fix(es) : * An use-after-free flaw was found in the Linux kernel which enables a race condition in the L2TPv3 IP Encapsulation feature. A local user could use this flaw to escalate their privileges or crash the system. (CVE-2016-10200, Important) * A flaw was found that can be triggered in keyring_search_iterator in keyring.c if type->match is NULL. A local user could use this flaw to crash the system or, potentially, escalate their privileges. (CVE-2017-2647, Important) * It was found that the NFSv4 server in the Linux kernel did not properly validate layout type when processing NFSv4 pNFS LAYOUTGET and GETDEVICEINFO operands. A remote attacker could use this flaw to soft-lockup the system and thus cause denial of service. (CVE-2017-8797, Important) This update also fixes multiple Moderate and Low impact security issues : * CVE-2015-8839, CVE-2015-8970, CVE-2016-9576, CVE-2016-7042, CVE-2016-7097, CVE-2016-8645, CVE-2016-9576, CVE-2016-9588, CVE-2016-9806, CVE-2016-10088, CVE-2016-10147, CVE-2017-2596, CVE-2017-2671, CVE-2017-5970, CVE-2017-6001, CVE-2017-6951, CVE-2017-7187, CVE-2017-7616, CVE-2017-7889, CVE-2017-8890, CVE-2017-9074, CVE-2017-8890, CVE-2017-9075, CVE-2017-8890, CVE-2017-9076, CVE-2017-8890, CVE-2017-9077, CVE-2017-9242, CVE-2014-7970, CVE-2014-7975, CVE-2016-6213, CVE-2016-9604, CVE-2016-9685 Documentation for these issues is available from the Release Notes document linked from the References section. Red Hat would like to thank Igor Redko (Virtuozzo) and Andrey Ryabinin (Virtuozzo) for reporting CVE-2017-2647; Igor Redko (Virtuozzo) and Vasily Averin (Virtuozzo) for reporting CVE-2015-8970; Marco Grassi for reporting CVE-2016-8645; and Dmitry Vyukov (Google Inc.) for reporting CVE-2017-2596. The CVE-2016-7042 issue was discovered by Ondrej Kozina (Red Hat); the CVE-2016-7097 issue was discovered by Andreas Gruenbacher (Red Hat) and Jan Kara (SUSE); the CVE-2016-6213 and CVE-2016-9685 issues were discovered by Qian Cai (Red Hat); and the CVE-2016-9604 issue was discovered by David Howells (Red Hat). Additional Changes : For detailed information on other changes in this release, see the Red Hat Enterprise Linux 7.4 Release Notes linked from the References section. last seen 2020-06-01 modified 2020-06-02 plugin id 102281 published 2017-08-09 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102281 title Oracle Linux 7 : kernel (ELSA-2017-1842) (Stack Clash) NASL family OracleVM Local Security Checks NASL id ORACLEVM_OVMSA-2017-0174.NASL description The remote OracleVM system is missing necessary patches to address critical security updates : please see Oracle VM Security Advisory OVMSA-2017-0174 for details. last seen 2020-06-05 modified 2017-12-14 plugin id 105248 published 2017-12-14 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/105248 title OracleVM 3.4 : Unbreakable / etc (OVMSA-2017-0174) (BlueBorne) (Dirty COW) (Stack Clash) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2448-1.NASL description This update for the Linux Kernel 3.12.74-60_64_57 fixes several issues. The following security bugs were fixed : - CVE-2017-9242: The __ip6_append_data function in net/ipv6/ip6_output.c in the Linux kernel was too late in checking whether an overwrite of an skb data structure may occur, which allowed local users to cause a denial of service (system crash) via crafted system calls (bsc#1038564, bsc#1042892). - CVE-2017-8890: The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c in the Linux kernel allowed attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call (bsc#1038564). Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 103214 published 2017-09-14 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103214 title SUSE SLES12 Security Update : kernel (SUSE-SU-2017:2448-1) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2049-1.NASL description This update for the Linux Kernel 3.12.69-60_64_29 fixes several issues. The following security bugs were fixed : - CVE-2017-7533: A bug in inotify code allowed local users to escalate privilege (bsc#1050751). - CVE-2017-7645: The NFSv2/NFSv3 server in the nfsd subsystem in the Linux kernel allowed remote attackers to cause a denial of service (system crash) via a long RPC reply, related to net/sunrpc/svc.c, fs/nfsd/nfs3xdr.c, and fs/nfsd/nfsxdr.c (bsc#1046191). - CVE-2017-2636: Race condition in drivers/tty/n_hdlc.c in the Linux kernel allowed local users to gain privileges or cause a denial of service (double free) by setting the HDLC line discipline (bsc#1027575). - CVE-2017-9242: The __ip6_append_data function in net/ipv6/ip6_output.c in the Linux kernel is too late in checking whether an overwrite of an skb data structure may occur, which allowed local users to cause a denial of service (system crash) via crafted system calls (bsc#1042892). - CVE-2017-8890: The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c in the Linux kernel allowed attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call (bsc#1038564). Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 102219 published 2017-08-07 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102219 title SUSE SLES12 Security Update : kernel (SUSE-SU-2017:2049-1) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3343-1.NASL description USN 3335-1 fixed a vulnerability in the Linux kernel. However, that fix introduced regressions for some Java applications. This update addresses the issue. We apologize for the inconvenience. It was discovered that a use-after-free vulnerability in the core voltage regulator driver of the Linux kernel. A local attacker could use this to cause a denial of service or possibly execute arbitrary code. (CVE-2014-9940) Roee Hay discovered that the parallel port printer driver in the Linux kernel did not properly bounds check passed arguments. A local attacker with write access to the kernel command line arguments could use this to execute arbitrary code. (CVE-2017-1000363) Li Qiang discovered that an integer overflow vulnerability existed in the Direct Rendering Manager (DRM) driver for VMware devices in the Linux kernel. A local attacker could use this to cause a denial of service (system crash) or possibly execute arbitrary code. (CVE-2017-7294) It was discovered that a double-free vulnerability existed in the IPv4 stack of the Linux kernel. An attacker could use this to cause a denial of service (system crash). (CVE-2017-8890) Andrey Konovalov discovered an IPv6 out-of-bounds read error in the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 101152 published 2017-06-30 reporter Ubuntu Security Notice (C) 2017-2019 Canonical, Inc. / NASL script (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/101152 title Ubuntu 14.04 LTS : linux vulnerabilities (USN-3343-1) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3326-1.NASL description It was discovered that a use-after-free flaw existed in the filesystem encryption subsystem in the Linux kernel. A local attacker could use this to cause a denial of service (system crash). (CVE-2017-7374) It was discovered that the stack guard page for processes in the Linux kernel was not sufficiently large enough to prevent overlapping with the heap. An attacker could leverage this with another vulnerability to execute arbitrary code and gain administrative privileges (CVE-2017-1000364) Roee Hay discovered that the parallel port printer driver in the Linux kernel did not properly bounds check passed arguments. A local attacker with write access to the kernel command line arguments could use this to execute arbitrary code. (CVE-2017-1000363) Ingo Molnar discovered that the VideoCore DRM driver in the Linux kernel did not return an error after detecting certain overflows. A local attacker could exploit this issue to cause a denial of service (OOPS). (CVE-2017-5577) A double free bug was discovered in the IPv4 stack of the Linux kernel. An attacker could use this to cause a denial of service (system crash). (CVE-2017-8890) Andrey Konovalov discovered an IPv6 out-of-bounds read error in the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 100924 published 2017-06-20 reporter Ubuntu Security Notice (C) 2017-2019 Canonical, Inc. / NASL script (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100924 title Ubuntu 16.10 : linux, linux-meta vulnerabilities (USN-3326-1) (Stack Clash) NASL family F5 Networks Local Security Checks NASL id F5_BIGIP_SOL02236463.NASL description The sctp_v6_create_accept_sk function in net/sctp/ipv6.c in the Linux kernel through 4.11.1 mishandles inheritance, which allows local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890. (CVE-2017-9075) Impact This vulnerability allows malicious users to cause a denial of service (DoS) on the F5 product. last seen 2020-06-01 modified 2020-06-02 plugin id 118617 published 2018-11-02 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/118617 title F5 Networks BIG-IP : Linux kernel vulnerability (K02236463) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2525-1.NASL description The SUSE Linux Enterprise 11 SP3 LTSS kernel was updated receive various security and bugfixes. The following security bugs were fixed : - CVE-2016-5243: The tipc_nl_compat_link_dump function in net/tipc/netlink_compat.c in the Linux kernel did not properly copy a certain string, which allowed local users to obtain sensitive information from kernel stack memory by reading a Netlink message (bnc#983212) - CVE-2016-10200: Race condition in the L2TPv3 IP Encapsulation feature in the Linux kernel allowed local users to gain privileges or cause a denial of service (use-after-free) by making multiple bind system calls without properly ascertaining whether a socket has the SOCK_ZAPPED status, related to net/l2tp/l2tp_ip.c and net/l2tp/l2tp_ip6.c (bnc#1028415) - CVE-2017-2647: The KEYS subsystem in the Linux kernel allowed local users to gain privileges or cause a denial of service (NULL pointer dereference and system crash) via vectors involving a NULL value for a certain match field, related to the keyring_search_iterator function in keyring.c (bsc#1030593). - CVE-2017-2671: The ping_unhash function in net/ipv4/ping.c in the Linux kernel was too late in obtaining a certain lock and consequently could not ensure that disconnect function calls are safe, which allowed local users to cause a denial of service (panic) by leveraging access to the protocol value of IPPROTO_ICMP in a socket system call (bnc#1031003) - CVE-2017-5669: The do_shmat function in ipc/shm.c in the Linux kernel did not restrict the address calculated by a certain rounding operation, which allowed local users to map page zero, and consequently bypass a protection mechanism that exists for the mmap system call, by making crafted shmget and shmat system calls in a privileged context (bnc#1026914) - CVE-2017-5970: The ipv4_pktinfo_prepare function in net/ipv4/ip_sockglue.c in the Linux kernel allowed attackers to cause a denial of service (system crash) via (1) an application that made crafted system calls or possibly (2) IPv4 traffic with invalid IP options (bsc#1024938) - CVE-2017-5986: Race condition in the sctp_wait_for_sndbuf function in net/sctp/socket.c in the Linux kernel allowed local users to cause a denial of service (assertion failure and panic) via a multithreaded application that peels off an association in a certain buffer-full state (bsc#1025235) - CVE-2017-6074: The dccp_rcv_state_process function in net/dccp/input.c in the Linux kernel mishandled DCCP_PKT_REQUEST packet data structures in the LISTEN state, which allowed local users to obtain root privileges or cause a denial of service (double free) via an application that made an IPV6_RECVPKTINFO setsockopt system call (bnc#1026024) - CVE-2017-6214: The tcp_splice_read function in net/ipv4/tcp.c in the Linux kernel allowed remote attackers to cause a denial of service (infinite loop and soft lockup) via vectors involving a TCP packet with the URG flag (bnc#1026722) - CVE-2017-6348: The hashbin_delete function in net/irda/irqueue.c in the Linux kernel improperly managed lock dropping, which allowed local users to cause a denial of service (deadlock) via crafted operations on IrDA devices (bnc#1027178) - CVE-2017-6353: net/sctp/socket.c in the Linux kernel did not properly restrict association peel-off operations during certain wait states, which allowed local users to cause a denial of service (invalid unlock and double free) via a multithreaded application. NOTE: this vulnerability exists because of an incorrect fix for CVE-2017-5986 (bnc#1027066) - CVE-2017-6951: The keyring_search_aux function in security/keys/keyring.c in the Linux kernel allowed local users to cause a denial of service (NULL pointer dereference and OOPS) via a request_key system call for the last seen 2020-06-01 modified 2020-06-02 plugin id 103354 published 2017-09-20 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103354 title SUSE SLES11 Security Update : kernel (SUSE-SU-2017:2525-1) (Stack Clash) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2017-1842.NASL description An update for kernel is now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The kernel packages contain the Linux kernel, the core of any Linux operating system. Security Fix(es) : * An use-after-free flaw was found in the Linux kernel which enables a race condition in the L2TPv3 IP Encapsulation feature. A local user could use this flaw to escalate their privileges or crash the system. (CVE-2016-10200, Important) * A flaw was found that can be triggered in keyring_search_iterator in keyring.c if type->match is NULL. A local user could use this flaw to crash the system or, potentially, escalate their privileges. (CVE-2017-2647, Important) * It was found that the NFSv4 server in the Linux kernel did not properly validate layout type when processing NFSv4 pNFS LAYOUTGET and GETDEVICEINFO operands. A remote attacker could use this flaw to soft-lockup the system and thus cause denial of service. (CVE-2017-8797, Important) This update also fixes multiple Moderate and Low impact security issues : * CVE-2015-8839, CVE-2015-8970, CVE-2016-9576, CVE-2016-7042, CVE-2016-7097, CVE-2016-8645, CVE-2016-9576, CVE-2016-9588, CVE-2016-9806, CVE-2016-10088, CVE-2016-10147, CVE-2017-2596, CVE-2017-2671, CVE-2017-5970, CVE-2017-6001, CVE-2017-6951, CVE-2017-7187, CVE-2017-7616, CVE-2017-7889, CVE-2017-8890, CVE-2017-9074, CVE-2017-8890, CVE-2017-9075, CVE-2017-8890, CVE-2017-9076, CVE-2017-8890, CVE-2017-9077, CVE-2017-9242, CVE-2014-7970, CVE-2014-7975, CVE-2016-6213, CVE-2016-9604, CVE-2016-9685 Documentation for these issues is available from the Release Notes document linked from the References section. Red Hat would like to thank Igor Redko (Virtuozzo) and Andrey Ryabinin (Virtuozzo) for reporting CVE-2017-2647; Igor Redko (Virtuozzo) and Vasily Averin (Virtuozzo) for reporting CVE-2015-8970; Marco Grassi for reporting CVE-2016-8645; and Dmitry Vyukov (Google Inc.) for reporting CVE-2017-2596. The CVE-2016-7042 issue was discovered by Ondrej Kozina (Red Hat); the CVE-2016-7097 issue was discovered by Andreas Gruenbacher (Red Hat) and Jan Kara (SUSE); the CVE-2016-6213 and CVE-2016-9685 issues were discovered by Qian Cai (Red Hat); and the CVE-2016-9604 issue was discovered by David Howells (Red Hat). Additional Changes : For detailed information on other changes in this release, see the Red Hat Enterprise Linux 7.4 Release Notes linked from the References section. last seen 2020-06-01 modified 2020-06-02 plugin id 102143 published 2017-08-03 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102143 title RHEL 7 : kernel (RHSA-2017:1842) (Stack Clash) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3329-1.NASL description It was discovered that the stack guard page for processes in the Linux kernel was not sufficiently large enough to prevent overlapping with the heap. An attacker could leverage this with another vulnerability to execute arbitrary code and gain administrative privileges (CVE-2017-1000364) Roee Hay discovered that the parallel port printer driver in the Linux kernel did not properly bounds check passed arguments. A local attacker with write access to the kernel command line arguments could use this to execute arbitrary code. (CVE-2017-1000363) A reference count bug was discovered in the Linux kernel ipx protocol stack. A local attacker could exploit this flaw to cause a denial of service or possibly other unspecified problems. (CVE-2017-7487) A double free bug was discovered in the IPv4 stack of the Linux kernel. An attacker could use this to cause a denial of service (system crash). (CVE-2017-8890) Andrey Konovalov discovered an IPv6 out-of-bounds read error in the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 100927 published 2017-06-20 reporter Ubuntu Security Notice (C) 2017-2019 Canonical, Inc. / NASL script (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100927 title Ubuntu 16.04 LTS : linux-gke, linux-meta-gke vulnerabilities (USN-3329-1) (Stack Clash) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3344-2.NASL description USN-3344-1 fixed vulnerabilities in the Linux kernel for Ubuntu 16.04 LTS. This update provides the corresponding updates for the Linux Hardware Enablement (HWE) kernel from Ubuntu 16.04 LTS for Ubuntu 14.04 LTS. USN 3334-1 fixed a vulnerability in the Linux kernel. However, that fix introduced regressions for some Java applications. This update addresses the issue. We apologize for the inconvenience. Roee Hay discovered that the parallel port printer driver in the Linux kernel did not properly bounds check passed arguments. A local attacker with write access to the kernel command line arguments could use this to execute arbitrary code. (CVE-2017-1000363) A reference count bug was discovered in the Linux kernel ipx protocol stack. A local attacker could exploit this flaw to cause a denial of service or possibly other unspecified problems. (CVE-2017-7487) It was discovered that a double-free vulnerability existed in the IPv4 stack of the Linux kernel. An attacker could use this to cause a denial of service (system crash). (CVE-2017-8890) Andrey Konovalov discovered an IPv6 out-of-bounds read error in the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 101155 published 2017-06-30 reporter Ubuntu Security Notice (C) 2017-2019 Canonical, Inc. / NASL script (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/101155 title Ubuntu 14.04 LTS : linux-lts-xenial vulnerabilities (USN-3344-2) NASL family PhotonOS Local Security Checks NASL id PHOTONOS_PHSA-2017-0019.NASL description An update of [linux] packages for PhotonOS has been released. last seen 2019-02-08 modified 2019-02-07 plugin id 111868 published 2018-08-17 reporter Tenable source https://www.tenable.com/plugins/index.php?view=single&id=111868 title Photon OS 1.0: Linux PHSA-2017-0019 (deprecated) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3334-1.NASL description It was discovered that the stack guard page for processes in the Linux kernel was not sufficiently large enough to prevent overlapping with the heap. An attacker could leverage this with another vulnerability to execute arbitrary code and gain administrative privileges (CVE-2017-1000364) Roee Hay discovered that the parallel port printer driver in the Linux kernel did not properly bounds check passed arguments. A local attacker with write access to the kernel command line arguments could use this to execute arbitrary code. (CVE-2017-1000363) A reference count bug was discovered in the Linux kernel ipx protocol stack. A local attacker could exploit this flaw to cause a denial of service or possibly other unspecified problems. (CVE-2017-7487) A double free bug was discovered in the IPv4 stack of the Linux kernel. An attacker could use this to cause a denial of service (system crash). (CVE-2017-8890) Andrey Konovalov discovered an IPv6 out-of-bounds read error in the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 100932 published 2017-06-20 reporter Ubuntu Security Notice (C) 2017-2019 Canonical, Inc. / NASL script (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100932 title Ubuntu 14.04 LTS : linux-lts-xenial, linux-meta-lts-xenial vulnerabilities (USN-3334-1) (Stack Clash) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3343-2.NASL description USN 3343-1 fixed vulnerabilities in the Linux kernel for Ubuntu 14.04 LTS. This update provides the corresponding updates for the Linux Hardware Enablement (HWE) kernel from Ubuntu 14.04 LTS for Ubuntu 12.04 ESM. USN 3335-2 fixed a vulnerability in the Linux kernel. However, that fix introduced regressions for some Java applications. This update addresses the issue. We apologize for the inconvenience. It was discovered that a use-after-free vulnerability in the core voltage regulator driver of the Linux kernel. A local attacker could use this to cause a denial of service or possibly execute arbitrary code. (CVE-2014-9940) Roee Hay discovered that the parallel port printer driver in the Linux kernel did not properly bounds check passed arguments. A local attacker with write access to the kernel command line arguments could use this to execute arbitrary code. (CVE-2017-1000363) Li Qiang discovered that an integer overflow vulnerability existed in the Direct Rendering Manager (DRM) driver for VMware devices in the Linux kernel. A local attacker could use this to cause a denial of service (system crash) or possibly execute arbitrary code. (CVE-2017-7294) It was discovered that a double-free vulnerability existed in the IPv4 stack of the Linux kernel. An attacker could use this to cause a denial of service (system crash). (CVE-2017-8890) Andrey Konovalov discovered an IPv6 out-of-bounds read error in the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 101153 published 2017-06-30 reporter This script is Copyright (C) 2017-2018 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/101153 title Ubuntu 12.04 LTS : linux-lts-trusty vulnerabilities (USN-3343-2) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2017-3575.NASL description Description of changes: kernel-uek [3.8.13-118.18.3.el7uek] - dccp/tcp: do not inherit mc_list from parent (Eric Dumazet) [Orabug: 26108571] {CVE-2017-8890} last seen 2020-06-01 modified 2020-06-02 plugin id 100450 published 2017-05-26 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100450 title Oracle Linux 6 / 7 : Unbreakable Enterprise kernel (ELSA-2017-3575) NASL family OracleVM Local Security Checks NASL id ORACLEVM_OVMSA-2017-0126.NASL description The remote OracleVM system is missing necessary patches to address critical security updates : please see Oracle VM Security Advisory OVMSA-2017-0126 for details. last seen 2020-06-01 modified 2020-06-02 plugin id 102064 published 2017-07-31 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102064 title OracleVM 3.4 : Unbreakable / etc (OVMSA-2017-0126) (Stack Clash) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2017-1842-1.NASL description The remote Oracle Linux host is missing a security update for the kernel package(s). last seen 2020-06-01 modified 2020-06-02 plugin id 102511 published 2017-08-16 reporter This script is Copyright (C) 2017-2018 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/102511 title Oracle Linux 7 : kernel (ELSA-2017-1842-1) (Stack Clash) NASL family F5 Networks Local Security Checks NASL id F5_BIGIP_SOL61429540.NASL description The tcp_v6_syn_recv_sock function in net/ipv6/tcp_ipv6.c in the Linux kernel through 4.11.1 mishandles inheritance, which allows local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890. (CVE-2017-9077) Impact This vulnerability allows a disruption of service and possibly an unauthorized disclosure of information. last seen 2020-06-01 modified 2020-06-02 plugin id 118685 published 2018-11-02 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/118685 title F5 Networks BIG-IP : Linux kernel vulnerability (K61429540) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2017-3576.NASL description Description of changes: [2.6.39-400.296.2.el6uek] - dccp/tcp: do not inherit mc_list from parent (Eric Dumazet) [Orabug: 26108573] {CVE-2017-8890} [2.6.39-400.296.1.el6uek] - cifs: adjust sequence number downward after signing NT_CANCEL request (Albert Barbe) - nfsd: stricter decoding of write-like NFSv2/v3 ops (J. Bruce Fields) [Orabug: 25986995] {CVE-2017-7895} last seen 2020-06-01 modified 2020-06-02 plugin id 100451 published 2017-05-26 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100451 title Oracle Linux 6 : Unbreakable Enterprise kernel (ELSA-2017-3576) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2017-3595.NASL description The remote Oracle Linux host is missing a security update for the Unbreakable Enterprise kernel package(s). last seen 2020-06-01 modified 2020-06-02 plugin id 102059 published 2017-07-31 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102059 title Oracle Linux 6 / 7 : Unbreakable Enterprise kernel (ELSA-2017-3595) (Stack Clash) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2447-1.NASL description This update for the Linux Kernel 3.12.74-60_64_51 fixes several issues. The following security bugs were fixed : - CVE-2017-1000112: Prevent a race condition in net-packet code that could have been exploited by unprivileged users to gain root access (bsc#1052368). - CVE-2017-9242: The __ip6_append_data function in net/ipv6/ip6_output.c in the Linux kernel was too late in checking whether an overwrite of an skb data structure may occur, which allowed local users to cause a denial of service (system crash) via crafted system calls (bsc#1038564, bsc#1042892). - CVE-2017-8890: The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c in the Linux kernel allowed attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call (bsc#1038564). Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 103213 published 2017-09-14 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103213 title SUSE SLES12 Security Update : kernel (SUSE-SU-2017:2447-1) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3344-1.NASL description USN 3328-1 fixed a vulnerability in the Linux kernel. However, that fix introduced regressions for some Java applications. This update addresses the issue. We apologize for the inconvenience. Roee Hay discovered that the parallel port printer driver in the Linux kernel did not properly bounds check passed arguments. A local attacker with write access to the kernel command line arguments could use this to execute arbitrary code. (CVE-2017-1000363) A reference count bug was discovered in the Linux kernel ipx protocol stack. A local attacker could exploit this flaw to cause a denial of service or possibly other unspecified problems. (CVE-2017-7487) It was discovered that a double-free vulnerability existed in the IPv4 stack of the Linux kernel. An attacker could use this to cause a denial of service (system crash). (CVE-2017-8890) Andrey Konovalov discovered an IPv6 out-of-bounds read error in the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 101154 published 2017-06-30 reporter Ubuntu Security Notice (C) 2017-2019 Canonical, Inc. / NASL script (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/101154 title Ubuntu 16.04 LTS : linux, linux-aws, linux-gke, linux-raspi2, linux-snapdragon vulnerabilities (USN-3344-1) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2090-1.NASL description This update for the Linux Kernel 3.12.74-60_64_45 fixes several issues. The following security bugs were fixed : - CVE-2017-7533: A bug in inotify code allowed local users to escalate privilege (bsc#1050751). - CVE-2017-9242: The __ip6_append_data function in net/ipv6/ip6_output.c in the Linux kernel is too late in checking whether an overwrite of an skb data structure may occur, which allowed local users to cause a denial of service (system crash) via crafted system calls (bsc#1042892). - CVE-2017-8890: The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c in the Linux kernel allowed attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call (bsc#1038564). Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 102309 published 2017-08-09 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102309 title SUSE SLES12 Security Update : kernel (SUSE-SU-2017:2090-1) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2791-1.NASL description This update for the Linux Kernel 3.12.74-60_64_60 fixes several issues. The following security bugs were fixed : - CVE-2017-15274: security/keys/keyctl.c in the Linux kernel did not consider the case of a NULL payload in conjunction with a nonzero length value, which allowed local users to cause a denial of service (NULL pointer dereference and OOPS) via a crafted add_key or keyctl system call (bsc#1045327). - CVE-2017-1000112: Updated patch for this issue to be in sync with the other livepatches. Description of the issue: Prevent race condition in net-packet code that could have been exploited by unprivileged users to gain root access (bsc#1052368, bsc#1052311). - CVE-2017-9242: The __ip6_append_data function in net/ipv6/ip6_output.c was too late in checking whether an overwrite of an skb data structure may occur, which allowed local users to cause a denial of service (system crash) via crafted system calls (bsc#1042892). - CVE-2017-8890: The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c allowed attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call (bsc#1038564). Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 104030 published 2017-10-20 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104030 title SUSE SLES12 Security Update : kernel (SUSE-SU-2017:2791-1) NASL family OracleVM Local Security Checks NASL id ORACLEVM_OVMSA-2017-0111.NASL description The remote OracleVM system is missing necessary patches to address critical security updates : - net/packet: fix overflow in check for tp_reserve (Andrey Konovalov) [Orabug: 26143545] (CVE-2017-7308) - net/packet: fix overflow in check for tp_frame_nr (Andrey Konovalov) [Orabug: 26143545] (CVE-2017-7308) - net/packet: fix overflow in check for priv area size (Andrey Konovalov) [Orabug: 26143545] (CVE-2017-7308) - dccp/tcp: do not inherit mc_list from parent (Eric Dumazet) [Orabug: 26132091] (CVE-2017-8890) last seen 2020-06-01 modified 2020-06-02 plugin id 100585 published 2017-06-02 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100585 title OracleVM 3.4 : Unbreakable / etc (OVMSA-2017-0111) NASL family OracleVM Local Security Checks NASL id ORACLEVM_OVMSA-2017-0121.NASL description The remote OracleVM system is missing necessary patches to address critical security updates : - nfsd: check for oversized NFSv2/v3 arguments (J. Bruce Fields) [Orabug: 26366024] (CVE-2017-7645) - dm mpath: allow ioctls to trigger pg init (Mikulas Patocka) [Orabug: 25645229] - xen/manage: Always freeze/thaw processes when suspend/resuming (Ross Lagerwall) [Orabug: 25795530] - lpfc cannot establish connection with targets that send PRLI under P2P mode (Joe Jin) [Orabug: 25955028] - nvme: Handle PM1725 HIL reset (Martin K. Petersen) [Orabug: 26277602] - dccp/tcp: do not inherit mc_list from parent (Eric Dumazet) [Orabug: 26108573] (CVE-2017-8890) - cifs: adjust sequence number downward after signing NT_CANCEL request (Albert Barbe) - nfsd: stricter decoding of write-like NFSv2/v3 ops (J. Bruce Fields) [Orabug: 25986995] (CVE-2017-7895) last seen 2020-06-01 modified 2020-06-02 plugin id 101200 published 2017-07-03 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/101200 title OracleVM 3.2 : Unbreakable / etc (OVMSA-2017-0121) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-1853-1.NASL description The SUSE Linux Enterprise 12 SP2 kernel was updated to 4.4.74 to receive various security and bugfixes. The following security bugs were fixed : - CVE-2017-1000365: The Linux Kernel imposes a size restriction on the arguments and environmental strings passed through RLIMIT_STACK/RLIM_INFINITY (1/4 of the size), but did not take the argument and environment pointers into account, which allowed attackers to bypass this limitation. (bnc#1039354). - CVE-2017-1000380: sound/core/timer.c in the Linux kernel is vulnerable to a data race in the ALSA /dev/snd/timer driver resulting in local users being able to read information belonging to other users, i.e., uninitialized memory contents may be disclosed when a read and an ioctl happen at the same time (bnc#1044125). - CVE-2017-7346: The vmw_gb_surface_define_ioctl function in drivers/gpu/drm/vmwgfx/vmwgfx_surface.c in the Linux kernel did not validate certain levels data, which allowed local users to cause a denial of service (system hang) via a crafted ioctl call for a /dev/dri/renderD* device (bnc#1031796). - CVE-2017-9242: The __ip6_append_data function in net/ipv6/ip6_output.c in the Linux kernel is too late in checking whether an overwrite of an skb data structure may occur, which allowed local users to cause a denial of service (system crash) via crafted system calls (bnc#1041431). - CVE-2017-9076: The dccp_v6_request_recv_sock function in net/dccp/ipv6.c in the Linux kernel mishandled inheritance, which allowed local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890 (bnc#1039885). - CVE-2017-9077: The tcp_v6_syn_recv_sock function in net/ipv6/tcp_ipv6.c in the Linux kernel mishandled inheritance, which allowed local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890 (bnc#1040069). - CVE-2017-9075: The sctp_v6_create_accept_sk function in net/sctp/ipv6.c in the Linux kernel mishandled inheritance, which allowed local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890 (bnc#1039883). - CVE-2017-9074: The IPv6 fragmentation implementation in the Linux kernel did not consider that the nexthdr field may be associated with an invalid option, which allowed local users to cause a denial of service (out-of-bounds read and BUG) or possibly have unspecified other impact via crafted socket and send system calls (bnc#1039882). - CVE-2017-8924: The edge_bulk_in_callback function in drivers/usb/serial/io_ti.c in the Linux kernel allowed local users to obtain sensitive information (in the dmesg ringbuffer and syslog) from uninitialized kernel memory by using a crafted USB device (posing as an io_ti USB serial device) to trigger an integer underflow. (bsc#1038982) - CVE-2017-8925: The omninet_open function in drivers/usb/serial/omninet.c in the Linux kernel allowed local users to cause a denial of service (tty exhaustion) by leveraging reference count mishandling. (bsc#1038981) - CVE-2017-7487: The ipxitf_ioctl function in net/ipx/af_ipx.c in the Linux kernel mishandled reference counts, which allowed local users to cause a denial of service (use-after-free) or possibly have unspecified other impact via a failed SIOCGIFADDR ioctl call for an IPX interface (bnc#1038879). - CVE-2017-8890: The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c in the Linux kernel allowed attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call (bnc#1038544). - CVE-2017-9150: The do_check function in kernel/bpf/verifier.c in the Linux kernel did not make the allow_ptr_leaks value available for restricting the output of the print_bpf_insn function, which allowed local users to obtain sensitive address information via crafted bpf system calls (bnc#1040279). - CVE-2017-7618: crypto/ahash.c in the Linux kernel allowed attackers to cause a denial of service (API operation calling its own callback, and infinite recursion) by triggering EBUSY on a full queue (bnc#1033340). - CVE-2017-7616: Incorrect error handling in the set_mempolicy and mbind compat syscalls in mm/mempolicy.c in the Linux kernel allowed local users to obtain sensitive information from uninitialized stack data by triggering failure of a certain bitmap operation (bnc#1033336). Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 101762 published 2017-07-17 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/101762 title SUSE SLED12 / SLES12 Security Update : kernel (SUSE-SU-2017:1853-1) (Stack Clash) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2017-2669.NASL description An update for kernel-rt is now available for Red Hat Enterprise MRG 2. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The kernel-rt packages provide the Real Time Linux Kernel, which enables fine-tuning for systems with extremely high determinism requirements. Security Fix(es) : * A race condition was found in the Linux kernel, present since v3.14-rc1 through v4.12. The race happens between threads of inotify_handle_event() and vfs_rename() while running the rename operation against the same file. As a result of the race the next slab data or the slab last seen 2020-06-01 modified 2020-06-02 plugin id 103046 published 2017-09-08 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103046 title RHEL 6 : MRG (RHSA-2017:2669) NASL family Huawei Local Security Checks NASL id EULEROS_SA-2019-1500.NASL description According to the versions of the kernel packages installed, the EulerOS Virtualization for ARM 64 installation on the remote host is affected by the following vulnerabilities : - The IPv6 DCCP implementation in the Linux kernel mishandles inheritance, which allows local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely.(CVE-2017-9076i1/4%0 - It was found that the driver_override implementation in base/platform.c in the Linux kernel is susceptible to race condition when different threads are reading vs storing a different driver override.(CVE-2017-12146i1/4%0 - The Linux Kernel imposes a size restriction on the arguments and environmental strings passed through RLIMIT_STACK/RLIMIT_INFINITY, but does not take the argument and environment pointers into account, which allows attackers to bypass this limitation.(CVE-2017-1000365i1/4%0 - A buffer overflow flaw was found in the way the Linux kernel last seen 2020-03-19 modified 2019-05-13 plugin id 124823 published 2019-05-13 reporter This script is Copyright (C) 2019-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/124823 title EulerOS Virtualization for ARM 64 3.0.1.0 : kernel (EulerOS-SA-2019-1500) NASL family OracleVM Local Security Checks NASL id ORACLEVM_OVMSA-2017-0145.NASL description The remote OracleVM system is missing necessary patches to address critical security updates : please see Oracle VM Security Advisory OVMSA-2017-0145 for details. last seen 2020-06-01 modified 2020-06-02 plugin id 102774 published 2017-08-25 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102774 title OracleVM 3.4 : Unbreakable / etc (OVMSA-2017-0145) (Stack Clash) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2073-1.NASL description This update for the Linux Kernel 3.12.67-60_64_24 fixes several issues. The following security bugs were fixed : - CVE-2017-7533: A bug in inotify code allowed local users to escalate privilege (bsc#1050751). - CVE-2017-7645: The NFSv2/NFSv3 server in the nfsd subsystem in the Linux kernel allowed remote attackers to cause a denial of service (system crash) via a long RPC reply, related to net/sunrpc/svc.c, fs/nfsd/nfs3xdr.c, and fs/nfsd/nfsxdr.c (bsc#1046191). - CVE-2017-2636: Race condition in drivers/tty/n_hdlc.c in the Linux kernel allowed local users to gain privileges or cause a denial of service (double free) by setting the HDLC line discipline (bsc#1027575). - CVE-2017-9242: The __ip6_append_data function in net/ipv6/ip6_output.c in the Linux kernel is too late in checking whether an overwrite of an skb data structure may occur, which allowed local users to cause a denial of service (system crash) via crafted system calls (bsc#1042892). - CVE-2017-8890: The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c in the Linux kernel allowed attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call (bsc#1038564). Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 102254 published 2017-08-08 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102254 title SUSE SLES12 Security Update : kernel (SUSE-SU-2017:2073-1) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2446-1.NASL description This update for the Linux Kernel 3.12.74-60_64_54 fixes several issues. The following security bugs were fixed : - CVE-2017-9242: The __ip6_append_data function in net/ipv6/ip6_output.c in the Linux kernel was too late in checking whether an overwrite of an skb data structure may occur, which allowed local users to cause a denial of service (system crash) via crafted system calls (bsc#1038564, bsc#1042892). - CVE-2017-8890: The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c in the Linux kernel allowed attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call (bsc#1038564). Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 103212 published 2017-09-14 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103212 title SUSE SLES12 Security Update : kernel (SUSE-SU-2017:2446-1) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3330-1.NASL description It was discovered that the stack guard page for processes in the Linux kernel was not sufficiently large enough to prevent overlapping with the heap. An attacker could leverage this with another vulnerability to execute arbitrary code and gain administrative privileges (CVE-2017-1000364) Roee Hay discovered that the parallel port printer driver in the Linux kernel did not properly bounds check passed arguments. A local attacker with write access to the kernel command line arguments could use this to execute arbitrary code. (CVE-2017-1000363) A reference count bug was discovered in the Linux kernel ipx protocol stack. A local attacker could exploit this flaw to cause a denial of service or possibly other unspecified problems. (CVE-2017-7487) A double free bug was discovered in the IPv4 stack of the Linux kernel. An attacker could use this to cause a denial of service (system crash). (CVE-2017-8890) Andrey Konovalov discovered an IPv6 out-of-bounds read error in the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 100928 published 2017-06-20 reporter Ubuntu Security Notice (C) 2017-2019 Canonical, Inc. / NASL script (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100928 title Ubuntu 16.04 LTS : linux-meta-snapdragon, linux-snapdragon vulnerabilities (USN-3330-1) (Stack Clash) NASL family Fedora Local Security Checks NASL id FEDORA_2017-6554692044.NASL description The 4.11.4 update contains a number of important fixes across the tree ---- This is a rebase to the 4.11 series of kernels. It includes all fixes Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2017-06-15 plugin id 100798 published 2017-06-15 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100798 title Fedora 24 : kernel (2017-6554692044) NASL family OracleVM Local Security Checks NASL id ORACLEVM_OVMSA-2018-0015.NASL description The remote OracleVM system is missing necessary patches to address critical security updates : please see Oracle VM Security Advisory OVMSA-2018-0015 for details. last seen 2020-06-01 modified 2020-06-02 plugin id 106469 published 2018-01-30 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/106469 title OracleVM 3.4 : Unbreakable / etc (OVMSA-2018-0015) (BlueBorne) (Meltdown) (Spectre) (Stack Clash) NASL family CentOS Local Security Checks NASL id CENTOS_RHSA-2017-1842.NASL description An update for kernel is now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The kernel packages contain the Linux kernel, the core of any Linux operating system. Security Fix(es) : * An use-after-free flaw was found in the Linux kernel which enables a race condition in the L2TPv3 IP Encapsulation feature. A local user could use this flaw to escalate their privileges or crash the system. (CVE-2016-10200, Important) * A flaw was found that can be triggered in keyring_search_iterator in keyring.c if type->match is NULL. A local user could use this flaw to crash the system or, potentially, escalate their privileges. (CVE-2017-2647, Important) * It was found that the NFSv4 server in the Linux kernel did not properly validate layout type when processing NFSv4 pNFS LAYOUTGET and GETDEVICEINFO operands. A remote attacker could use this flaw to soft-lockup the system and thus cause denial of service. (CVE-2017-8797, Important) This update also fixes multiple Moderate and Low impact security issues : * CVE-2015-8839, CVE-2015-8970, CVE-2016-9576, CVE-2016-7042, CVE-2016-7097, CVE-2016-8645, CVE-2016-9576, CVE-2016-9588, CVE-2016-9806, CVE-2016-10088, CVE-2016-10147, CVE-2017-2596, CVE-2017-2671, CVE-2017-5970, CVE-2017-6001, CVE-2017-6951, CVE-2017-7187, CVE-2017-7616, CVE-2017-7889, CVE-2017-8890, CVE-2017-9074, CVE-2017-8890, CVE-2017-9075, CVE-2017-8890, CVE-2017-9076, CVE-2017-8890, CVE-2017-9077, CVE-2017-9242, CVE-2014-7970, CVE-2014-7975, CVE-2016-6213, CVE-2016-9604, CVE-2016-9685 Documentation for these issues is available from the Release Notes document linked from the References section. Red Hat would like to thank Igor Redko (Virtuozzo) and Andrey Ryabinin (Virtuozzo) for reporting CVE-2017-2647; Igor Redko (Virtuozzo) and Vasily Averin (Virtuozzo) for reporting CVE-2015-8970; Marco Grassi for reporting CVE-2016-8645; and Dmitry Vyukov (Google Inc.) for reporting CVE-2017-2596. The CVE-2016-7042 issue was discovered by Ondrej Kozina (Red Hat); the CVE-2016-7097 issue was discovered by Andreas Gruenbacher (Red Hat) and Jan Kara (SUSE); the CVE-2016-6213 and CVE-2016-9685 issues were discovered by Qian Cai (Red Hat); and the CVE-2016-9604 issue was discovered by David Howells (Red Hat). Additional Changes : For detailed information on other changes in this release, see the Red Hat Enterprise Linux 7.4 Release Notes linked from the References section. last seen 2020-06-01 modified 2020-06-02 plugin id 102734 published 2017-08-25 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102734 title CentOS 7 : kernel (CESA-2017:1842) (Stack Clash) NASL family Virtuozzo Local Security Checks NASL id VIRTUOZZO_VZA-2017-047.NASL description According to the versions of the parallels-server-bm-release / vzkernel / etc packages installed, the Virtuozzo installation on the remote host is affected by the following vulnerabilities : - The tcp_v6_syn_recv_sock function in net/ipv6/tcp_ipv6.c in the Linux kernel mishandles inheritance, which allows local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. - The IPv6 DCCP implementation in the Linux kernel mishandles inheritance, which allows local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. - The sctp_v6_create_accept_sk function in net/sctp/ipv6.c in the Linux kernel mishandles inheritance, which allows local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. - The IPv6 fragmentation implementation in the Linux kernel through 4.11.1 does not consider that the nexthdr field may be associated with an invalid option, which allows local users to cause a denial of service (out-of-bounds read and BUG) or possibly have unspecified other impact via crafted socket and send system calls. - The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c in the Linux kernel allows attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. - Improved isolation for neighbor table settings. (The fix added to the 042stab120.19 kernel was incomplete.) Note that Tenable Network Security has extracted the preceding description block directly from the Virtuozzo security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 100769 published 2017-06-14 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100769 title Virtuozzo 6 : parallels-server-bm-release / vzkernel / etc (VZA-2017-047) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3325-1.NASL description It was discovered that the stack guard page for processes in the Linux kernel was not sufficiently large enough to prevent overlapping with the heap. An attacker could leverage this with another vulnerability to execute arbitrary code and gain administrative privileges (CVE-2017-1000364) Roee Hay discovered that the parallel port printer driver in the Linux kernel did not properly bounds check passed arguments. A local attacker with write access to the kernel command line arguments could use this to execute arbitrary code. (CVE-2017-1000363) A double free bug was discovered in the IPv4 stack of the Linux kernel. An attacker could use this to cause a denial of service (system crash). (CVE-2017-8890) Andrey Konovalov discovered an IPv6 out-of-bounds read error in the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 100923 published 2017-06-20 reporter Ubuntu Security Notice (C) 2017-2019 Canonical, Inc. / NASL script (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100923 title Ubuntu 17.04 : linux-meta-raspi2, linux-raspi2 vulnerabilities (USN-3325-1) (Stack Clash) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3332-1.NASL description It was discovered that the stack guard page for processes in the Linux kernel was not sufficiently large enough to prevent overlapping with the heap. An attacker could leverage this with another vulnerability to execute arbitrary code and gain administrative privileges (CVE-2017-1000364) Roee Hay discovered that the parallel port printer driver in the Linux kernel did not properly bounds check passed arguments. A local attacker with write access to the kernel command line arguments could use this to execute arbitrary code. (CVE-2017-1000363) A reference count bug was discovered in the Linux kernel ipx protocol stack. A local attacker could exploit this flaw to cause a denial of service or possibly other unspecified problems. (CVE-2017-7487) A double free bug was discovered in the IPv4 stack of the Linux kernel. An attacker could use this to cause a denial of service (system crash). (CVE-2017-8890) Andrey Konovalov discovered an IPv6 out-of-bounds read error in the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 100930 published 2017-06-20 reporter Ubuntu Security Notice (C) 2017-2019 Canonical, Inc. / NASL script (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100930 title Ubuntu 16.04 LTS : linux-meta-raspi2, linux-raspi2 vulnerabilities (USN-3332-1) (Stack Clash) NASL family PhotonOS Local Security Checks NASL id PHOTONOS_PHSA-2017-0019_LINUX.NASL description An update of the linux package has been released. last seen 2020-03-17 modified 2019-02-07 plugin id 121698 published 2019-02-07 reporter This script is Copyright (C) 2019-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/121698 title Photon OS 1.0: Linux PHSA-2017-0019 NASL family Amazon Linux Local Security Checks NASL id ALA_ALAS-2017-846.NASL description Module reference leak due to improper shut down of callback channel on umount : The NFSv4 implementation in the Linux kernel through 4.11.1 allows local users to cause a denial of service (resource consumption) by leveraging improper channel callback shutdown when unmounting an NFSv4 filesystem, aka a last seen 2020-06-01 modified 2020-06-02 plugin id 100999 published 2017-06-23 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100999 title Amazon Linux AMI : kernel (ALAS-2017-846) NASL family Virtuozzo Local Security Checks NASL id VIRTUOZZO_VZA-2017-043.NASL description According to the version of the vzkernel package and the readykernel-patch installed, the Virtuozzo installation on the remote host is affected by the following vulnerabilities : - The tcp_v6_syn_recv_sock function in net/ipv6/tcp_ipv6.c in the Linux kernel mishandles inheritance, which allows local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. - The IPv6 DCCP implementation in the Linux kernel mishandles inheritance, which allows local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. - The sctp_v6_create_accept_sk function in net/sctp/ipv6.c in the Linux kernel mishandles inheritance, which allows local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. - The IPv6 fragmentation implementation in the Linux kernel through 4.11.1 does not consider that the nexthdr field may be associated with an invalid option, which allows local users to cause a denial of service (out-of-bounds read and BUG) or possibly have unspecified other impact via crafted socket and send system calls. - The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c in the Linux kernel allows attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. - A vulnerability was found in the Linux kernel. An unprivileged local user could trigger oops in shash_async_export() by attempting to force the in-kernel hashing algorithms into decrypting an empty data set. Note that Tenable Network Security has extracted the preceding description block directly from the Virtuozzo security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 100599 published 2017-06-05 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100599 title Virtuozzo 7 : readykernel-patch (VZA-2017-043) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3342-2.NASL description USN-3342-1 fixed vulnerabilities in the Linux kernel for Ubuntu 16.10. This update provides the corresponding updates for the Linux Hardware Enablement (HWE) kernel from Ubuntu 16.10 for Ubuntu 16.04 LTS. USN-3333-1 fixed a vulnerability in the Linux kernel. However, that fix introduced regressions for some Java applications. This update addresses the issue. We apologize for the inconvenience. It was discovered that a use-after-free flaw existed in the filesystem encryption subsystem in the Linux kernel. A local attacker could use this to cause a denial of service (system crash). (CVE-2017-7374) Roee Hay discovered that the parallel port printer driver in the Linux kernel did not properly bounds check passed arguments. A local attacker with write access to the kernel command line arguments could use this to execute arbitrary code. (CVE-2017-1000363) Ingo Molnar discovered that the VideoCore DRM driver in the Linux kernel did not return an error after detecting certain overflows. A local attacker could exploit this issue to cause a denial of service (OOPS). (CVE-2017-5577) Li Qiang discovered that an integer overflow vulnerability existed in the Direct Rendering Manager (DRM) driver for VMware devices in the Linux kernel. A local attacker could use this to cause a denial of service (system crash) or possibly execute arbitrary code. (CVE-2017-7294) It was discovered that a double-free vulnerability existed in the IPv4 stack of the Linux kernel. An attacker could use this to cause a denial of service (system crash). (CVE-2017-8890) Andrey Konovalov discovered an IPv6 out-of-bounds read error in the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 101151 published 2017-06-30 reporter Ubuntu Security Notice (C) 2017-2019 Canonical, Inc. / NASL script (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/101151 title Ubuntu 16.04 LTS : linux-hwe vulnerabilities (USN-3342-2) NASL family Virtuozzo Local Security Checks NASL id VIRTUOZZO_VZA-2017-042.NASL description According to the version of the vzkernel package and the readykernel-patch installed, the Virtuozzo installation on the remote host is affected by the following vulnerabilities : - The NFS2/3 RPC client could send long arguments to nfsd server. These encoded arguments are stored in an array of memory pages, and accessed via various pointer variables. Arbitrarily long arguments could make these pointers point outside the array, thus causing out-of-bounds memory access. A remote user/program could use this flaw to crash the kernel resulting in DoS. - The NFSv2 and NFSv3 server implementations in the Linux kernel through 4.10.13 lack certain checks for the end of a buffer. A remote attacker could trigger a pointer-arithmetic error or possibly have unspecified other impact via crafted requests related to fs/nfsd/nfs3xdr.c and fs/nfsd/nfsxdr.c. - The tcp_v6_syn_recv_sock function in net/ipv6/tcp_ipv6.c in the Linux kernel mishandles inheritance, which allows local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. - The IPv6 DCCP implementation in the Linux kernel mishandles inheritance, which allows local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. - The sctp_v6_create_accept_sk function in net/sctp/ipv6.c in the Linux kernel mishandles inheritance, which allows local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. - The IPv6 fragmentation implementation in the Linux kernel through 4.11.1 does not consider that the nexthdr field may be associated with an invalid option, which allows local users to cause a denial of service (out-of-bounds read and BUG) or possibly have unspecified other impact via crafted socket and send system calls. - The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c in the Linux kernel allows attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. - A vulnerability was found in the Linux kernel. An unprivileged local user could trigger oops in shash_async_export() by attempting to force the in-kernel hashing algorithms into decrypting an empty data set. - If the sctp module was loaded on the host, a privileged user inside a container could cause a kernel crash by triggering a NULL pointer dererefence in the sctp_endpoint_destroy() function with a specially crafted sequence of system calls. - A privileged user inside a container could cause a kernel crash by triggering a BUG_ON in the unregister_netdevice_many() function with a specially crafted sequence of system calls. Note that Tenable Network Security has extracted the preceding description block directly from the Virtuozzo security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 100598 published 2017-06-05 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100598 title Virtuozzo 7 : readykernel-patch (VZA-2017-042) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3327-1.NASL description It was discovered that a use-after-free flaw existed in the filesystem encryption subsystem in the Linux kernel. A local attacker could use this to cause a denial of service (system crash). (CVE-2017-7374) It was discovered that the stack guard page for processes in the Linux kernel was not sufficiently large enough to prevent overlapping with the heap. An attacker could leverage this with another vulnerability to execute arbitrary code and gain administrative privileges (CVE-2017-1000364) Roee Hay discovered that the parallel port printer driver in the Linux kernel did not properly bounds check passed arguments. A local attacker with write access to the kernel command line arguments could use this to execute arbitrary code. (CVE-2017-1000363) Ingo Molnar discovered that the VideoCore DRM driver in the Linux kernel did not return an error after detecting certain overflows. A local attacker could exploit this issue to cause a denial of service (OOPS). (CVE-2017-5577) A double free bug was discovered in the IPv4 stack of the Linux kernel. An attacker could use this to cause a denial of service (system crash). (CVE-2017-8890) Andrey Konovalov discovered an IPv6 out-of-bounds read error in the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 100925 published 2017-06-20 reporter Ubuntu Security Notice (C) 2017-2019 Canonical, Inc. / NASL script (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100925 title Ubuntu 16.10 : linux-meta-raspi2, linux-raspi2 vulnerabilities (USN-3327-1) (Stack Clash) NASL family F5 Networks Local Security Checks NASL id F5_BIGIP_SOL02613439.NASL description The dccp_v6_request_recv_sock function in net/dccp/ipv6.c in the Linux kernel through 4.11.1 mishandles inheritance, which allows local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890. (CVE-2017-9076) Impact This vulnerability allows an unprivileged local user to cause a denial of service (DoS) or disruption of service through crafted system calls. last seen 2020-06-01 modified 2020-06-02 plugin id 118618 published 2018-11-02 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/118618 title F5 Networks BIG-IP : Linux kernel vulnerability (K02613439) NASL family Huawei Local Security Checks NASL id EULEROS_SA-2019-1504.NASL description According to the versions of the kernel packages installed, the EulerOS Virtualization installation on the remote host is affected by the following vulnerabilities : - A vulnerability was found in the Linux kernel where the keyctl_set_reqkey_keyring() function leaks the thread keyring. This allows an unprivileged local user to exhaust kernel memory and thus cause a DoS.(CVE-2017-7472) - A reference counter leak in Linux kernel in ipxitf_ioctl function was found which results in a use after free vulnerability that last seen 2020-06-01 modified 2020-06-02 plugin id 124827 published 2019-05-13 reporter This script is Copyright (C) 2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/124827 title EulerOS Virtualization 3.0.1.0 : kernel (EulerOS-SA-2019-1504) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3335-1.NASL description It was discovered that the stack guard page for processes in the Linux kernel was not sufficiently large enough to prevent overlapping with the heap. An attacker could leverage this with another vulnerability to execute arbitrary code and gain administrative privileges (CVE-2017-1000364) It was discovered that a use-after-free vulnerability in the core voltage regulator driver of the Linux kernel. A local attacker could use this to cause a denial of service or possibly execute arbitrary code. (CVE-2014-9940) Roee Hay discovered that the parallel port printer driver in the Linux kernel did not properly bounds check passed arguments. A local attacker with write access to the kernel command line arguments could use this to execute arbitrary code. (CVE-2017-1000363) Li Qiang discovered that an integer overflow vulnerability existed in the Direct Rendering Manager (DRM) driver for VMware devices in the Linux kernel. A local attacker could use this to cause a denial of service (system crash) or possibly execute arbitrary code. (CVE-2017-7294) A double free bug was discovered in the IPv4 stack of the Linux kernel. An attacker could use this to cause a denial of service (system crash). (CVE-2017-8890) Andrey Konovalov discovered an IPv6 out-of-bounds read error in the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 100933 published 2017-06-20 reporter Ubuntu Security Notice (C) 2017-2019 Canonical, Inc. / NASL script (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100933 title Ubuntu 14.04 LTS : linux, linux-meta vulnerabilities (USN-3335-1) (Stack Clash) NASL family Huawei Local Security Checks NASL id EULEROS_SA-2019-1531.NASL description According to the versions of the kernel packages installed, the EulerOS Virtualization for ARM 64 installation on the remote host is affected by the following vulnerabilities : - Use-after-free vulnerability in drivers/net/tun.c in the Linux kernel through 3.11.1 allows local users to gain privileges by leveraging the CAP_NET_ADMIN capability and providing an invalid tuntap interface name in a TUNSETIFF ioctl call.(CVE-2013-4343i1/4%0 - It was found that when the gcc stack protector was enabled, reading the /proc/keys file could cause a panic in the Linux kernel due to stack corruption. This happened because an incorrect buffer size was used to hold a 64-bit timeout value rendered as weeks.(CVE-2016-7042i1/4%0 - A flaw was found in the Linux kernel that fs/ocfs2/aops.c omits use of a semaphore and consequently has a race condition for access to the extent tree during read operations in DIRECT mode. This allows local users to cause a denial of service by modifying a certain e_cpos field.(CVE-2017-18224i1/4%0 - The sctp_v6_create_accept_sk function in net/sctp/ipv6.c in the Linux kernel mishandles inheritance, which allows local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely.(CVE-2017-9075i1/4%0 - In the function sbusfb_ioctl_helper() in drivers/video/fbdev/sbuslib.c in the Linux kernel, up to and including 4.15, an integer signedness error allows arbitrary information leakage for the FBIOPUTCMAP_SPARC and FBIOGETCMAP_SPARC commands.(CVE-2018-6412i1/4%0 - A race condition flaw was found in the way the Linux kernel last seen 2020-03-19 modified 2019-05-14 plugin id 124984 published 2019-05-14 reporter This script is Copyright (C) 2019-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/124984 title EulerOS Virtualization for ARM 64 3.0.1.0 : kernel (EulerOS-SA-2019-1531) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3331-1.NASL description It was discovered that the stack guard page for processes in the Linux kernel was not sufficiently large enough to prevent overlapping with the heap. An attacker could leverage this with another vulnerability to execute arbitrary code and gain administrative privileges (CVE-2017-1000364) Roee Hay discovered that the parallel port printer driver in the Linux kernel did not properly bounds check passed arguments. A local attacker with write access to the kernel command line arguments could use this to execute arbitrary code. (CVE-2017-1000363) A reference count bug was discovered in the Linux kernel ipx protocol stack. A local attacker could exploit this flaw to cause a denial of service or possibly other unspecified problems. (CVE-2017-7487) A double free bug was discovered in the IPv4 stack of the Linux kernel. An attacker could use this to cause a denial of service (system crash). (CVE-2017-8890) Andrey Konovalov discovered an IPv6 out-of-bounds read error in the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 100929 published 2017-06-20 reporter Ubuntu Security Notice (C) 2017-2019 Canonical, Inc. / NASL script (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100929 title Ubuntu 16.04 LTS : linux-aws, linux-meta-aws vulnerabilities (USN-3331-1) (Stack Clash) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3328-1.NASL description It was discovered that the stack guard page for processes in the Linux kernel was not sufficiently large enough to prevent overlapping with the heap. An attacker could leverage this with another vulnerability to execute arbitrary code and gain administrative privileges (CVE-2017-1000364) Roee Hay discovered that the parallel port printer driver in the Linux kernel did not properly bounds check passed arguments. A local attacker with write access to the kernel command line arguments could use this to execute arbitrary code. (CVE-2017-1000363) A reference count bug was discovered in the Linux kernel ipx protocol stack. A local attacker could exploit this flaw to cause a denial of service or possibly other unspecified problems. (CVE-2017-7487) A double free bug was discovered in the IPv4 stack of the Linux kernel. An attacker could use this to cause a denial of service (system crash). (CVE-2017-8890) Andrey Konovalov discovered an IPv6 out-of-bounds read error in the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 100926 published 2017-06-20 reporter Ubuntu Security Notice (C) 2017-2019 Canonical, Inc. / NASL script (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100926 title Ubuntu 16.04 LTS : linux, linux-meta vulnerabilities (USN-3328-1) (Stack Clash) NASL family Virtuozzo Local Security Checks NASL id VIRTUOZZO_VZA-2017-044.NASL description According to the version of the vzkernel package and the readykernel-patch installed, the Virtuozzo installation on the remote host is affected by the following vulnerabilities : - The tcp_v6_syn_recv_sock function in net/ipv6/tcp_ipv6.c in the Linux kernel mishandles inheritance, which allows local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. - The IPv6 DCCP implementation in the Linux kernel mishandles inheritance, which allows local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. - The sctp_v6_create_accept_sk function in net/sctp/ipv6.c in the Linux kernel mishandles inheritance, which allows local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. - The IPv6 fragmentation implementation in the Linux kernel through 4.11.1 does not consider that the nexthdr field may be associated with an invalid option, which allows local users to cause a denial of service (out-of-bounds read and BUG) or possibly have unspecified other impact via crafted socket and send system calls. - The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c in the Linux kernel allows attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. Note that Tenable Network Security has extracted the preceding description block directly from the Virtuozzo security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 100600 published 2017-06-05 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100600 title Virtuozzo 7 : readykernel-patch (VZA-2017-044) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2017-3574.NASL description Description of changes: kernel-uek [4.1.12-94.3.5.el7uek] - dccp/tcp: do not inherit mc_list from parent (Eric Dumazet) [Orabug: 26132091] {CVE-2017-8890} last seen 2020-06-01 modified 2020-06-02 plugin id 100449 published 2017-05-26 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100449 title Oracle Linux 6 / 7 : Unbreakable Enterprise kernel (ELSA-2017-3574) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2018-1854.NASL description From Red Hat Security Advisory 2018:1854 : An update for kernel is now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The kernel packages contain the Linux kernel, the core of any Linux operating system. Security Fix(es) : * An industry-wide issue was found in the way many modern microprocessor designs have implemented speculative execution of Load & Store instructions (a commonly used performance optimization). It relies on the presence of a precisely-defined instruction sequence in the privileged code as well as the fact that memory read from address to which a recent memory write has occurred may see an older value and subsequently cause an update into the microprocessor last seen 2020-06-01 modified 2020-06-02 plugin id 110701 published 2018-06-27 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/110701 title Oracle Linux 6 : kernel (ELSA-2018-1854) (Spectre) NASL family OracleVM Local Security Checks NASL id ORACLEVM_OVMSA-2017-0112.NASL description The remote OracleVM system is missing necessary patches to address critical security updates : - net/packet: fix overflow in check for tp_reserve (Andrey Konovalov) [Orabug: 26143552] (CVE-2017-7308) - net/packet: fix overflow in check for tp_frame_nr (Andrey Konovalov) [Orabug: 26143552] (CVE-2017-7308) - net/packet: fix overflow in check for priv area size (Andrey Konovalov) [Orabug: 26143552] (CVE-2017-7308) - dccp/tcp: do not inherit mc_list from parent (Eric Dumazet) [Orabug: 26108571] (CVE-2017-8890) last seen 2020-06-01 modified 2020-06-02 plugin id 100586 published 2017-06-02 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100586 title OracleVM 3.3 : Unbreakable / etc (OVMSA-2017-0112) NASL family Scientific Linux Local Security Checks NASL id SL_20180619_KERNEL_ON_SL6_X.NASL description Security Fix(es) : - An industry-wide issue was found in the way many modern microprocessor designs have implemented speculative execution of Load & Store instructions (a commonly used performance optimization). It relies on the presence of a precisely-defined instruction sequence in the privileged code as well as the fact that memory read from address to which a recent memory write has occurred may see an older value and subsequently cause an update into the microprocessor last seen 2020-03-18 modified 2018-07-03 plugin id 110887 published 2018-07-03 reporter This script is Copyright (C) 2018-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/110887 title Scientific Linux Security Update : kernel on SL6.x i386/x86_64 (20180619) (Spectre) NASL family NewStart CGSL Local Security Checks NASL id NEWSTART_CGSL_NS-SA-2019-0098_KERNEL.NASL description The remote NewStart CGSL host, running version MAIN 4.05, has kernel packages installed that are affected by multiple vulnerabilities: - The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c in the Linux kernel allows attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. (CVE-2017-8890) - The sctp_v6_create_accept_sk function in net/sctp/ipv6.c in the Linux kernel mishandles inheritance, which allows local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. (CVE-2017-9075) - The IPv6 DCCP implementation in the Linux kernel mishandles inheritance, which allows local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. (CVE-2017-9076) - The tcp_v6_syn_recv_sock function in net/ipv6/tcp_ipv6.c in the Linux kernel mishandles inheritance, which allows local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. (CVE-2017-9077) Note that Nessus has not tested for this issue but has instead relied only on the application last seen 2020-06-01 modified 2020-06-02 plugin id 127323 published 2019-08-12 reporter This script is Copyright (C) 2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/127323 title NewStart CGSL MAIN 4.05 : kernel Multiple Vulnerabilities (NS-SA-2019-0098) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3333-1.NASL description It was discovered that a use-after-free flaw existed in the filesystem encryption subsystem in the Linux kernel. A local attacker could use this to cause a denial of service (system crash). (CVE-2017-7374) It was discovered that the stack guard page for processes in the Linux kernel was not sufficiently large enough to prevent overlapping with the heap. An attacker could leverage this with another vulnerability to execute arbitrary code and gain administrative privileges (CVE-2017-1000364) Roee Hay discovered that the parallel port printer driver in the Linux kernel did not properly bounds check passed arguments. A local attacker with write access to the kernel command line arguments could use this to execute arbitrary code. (CVE-2017-1000363) Ingo Molnar discovered that the VideoCore DRM driver in the Linux kernel did not return an error after detecting certain overflows. A local attacker could exploit this issue to cause a denial of service (OOPS). (CVE-2017-5577) A double free bug was discovered in the IPv4 stack of the Linux kernel. An attacker could use this to cause a denial of service (system crash). (CVE-2017-8890) Andrey Konovalov discovered an IPv6 out-of-bounds read error in the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 100931 published 2017-06-20 reporter Ubuntu Security Notice (C) 2017-2019 Canonical, Inc. / NASL script (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100931 title Ubuntu 16.04 LTS : linux-hwe, linux-meta-hwe vulnerabilities (USN-3333-1) (Stack Clash) NASL family NewStart CGSL Local Security Checks NASL id NEWSTART_CGSL_NS-SA-2019-0028_KERNEL-RT.NASL description The remote NewStart CGSL host, running version CORE 5.04 / MAIN 5.04, has kernel-rt packages installed that are affected by multiple vulnerabilities: - net/llc/sysctl_net_llc.c in the Linux kernel before 3.19 uses an incorrect data type in a sysctl table, which allows local users to obtain potentially sensitive information from kernel memory or possibly have unspecified other impact by accessing a sysctl entry. (CVE-2015-2041) - net/rds/sysctl.c in the Linux kernel before 3.19 uses an incorrect data type in a sysctl table, which allows local users to obtain potentially sensitive information from kernel memory or possibly have unspecified other impact by accessing a sysctl entry. (CVE-2015-2042) - The xfrm_migrate() function in the net/xfrm/xfrm_policy.c file in the Linux kernel built with CONFIG_XFRM_MIGRATE does not verify if the dir parameter is less than XFRM_POLICY_MAX. This allows a local attacker to cause a denial of service (out-of- bounds access) or possibly have unspecified other impact by sending a XFRM_MSG_MIGRATE netlink message. This flaw is present in the Linux kernel since an introduction of XFRM_MSG_MIGRATE in 2.6.21-rc1, up to 4.13-rc3. (CVE-2017-11600) - A flaw was found in the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 127192 published 2019-08-12 reporter This script is Copyright (C) 2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/127192 title NewStart CGSL CORE 5.04 / MAIN 5.04 : kernel-rt Multiple Vulnerabilities (NS-SA-2019-0028) NASL family CentOS Local Security Checks NASL id CENTOS_RHSA-2018-1854.NASL description An update for kernel is now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The kernel packages contain the Linux kernel, the core of any Linux operating system. Security Fix(es) : * An industry-wide issue was found in the way many modern microprocessor designs have implemented speculative execution of Load & Store instructions (a commonly used performance optimization). It relies on the presence of a precisely-defined instruction sequence in the privileged code as well as the fact that memory read from address to which a recent memory write has occurred may see an older value and subsequently cause an update into the microprocessor last seen 2020-06-01 modified 2020-06-02 plugin id 110645 published 2018-06-22 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/110645 title CentOS 6 : kernel (CESA-2018:1854) (Spectre) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2089-1.NASL description This update for the Linux Kernel 3.12.74-60_64_48 fixes several issues. The following security bugs were fixed : - CVE-2017-7533: A bug in inotify code allowed local users to escalate privilege (bsc#1050751). - CVE-2017-9242: The __ip6_append_data function in net/ipv6/ip6_output.c in the Linux kernel is too late in checking whether an overwrite of an skb data structure may occur, which allowed local users to cause a denial of service (system crash) via crafted system calls (bsc#1042892). - CVE-2017-8890: The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c in the Linux kernel allowed attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call (bsc#1038564). Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 102308 published 2017-08-09 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102308 title SUSE SLES12 Security Update : kernel (SUSE-SU-2017:2089-1) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2072-1.NASL description This update for the Linux Kernel 3.12.67-60_64_21 fixes several issues. The following security bugs were fixed : - CVE-2017-7533: A bug in inotify code allowed local users to escalate privilege (bsc#1050751). - CVE-2017-7645: The NFSv2/NFSv3 server in the nfsd subsystem in the Linux kernel allowed remote attackers to cause a denial of service (system crash) via a long RPC reply, related to net/sunrpc/svc.c, fs/nfsd/nfs3xdr.c, and fs/nfsd/nfsxdr.c (bsc#1046191). - CVE-2017-2636: Race condition in drivers/tty/n_hdlc.c in the Linux kernel allowed local users to gain privileges or cause a denial of service (double free) by setting the HDLC line discipline (bsc#1027575). - CVE-2017-9242: The __ip6_append_data function in net/ipv6/ip6_output.c in the Linux kernel is too late in checking whether an overwrite of an skb data structure may occur, which allowed local users to cause a denial of service (system crash) via crafted system calls (bsc#1042892). - CVE-2017-8890: The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c in the Linux kernel allowed attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call (bsc#1038564). Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 102253 published 2017-08-08 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102253 title SUSE SLES12 Security Update : kernel (SUSE-SU-2017:2072-1) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2389-1.NASL description The SUSE Linux Enterprise 11 SP4 kernel was updated to receive various security and bugfixes. The following security bugs were fixed : - CVE-2017-7482: Several missing length checks ticket decode allowing for information leak or potentially code execution (bsc#1046107). - CVE-2016-10277: Potential privilege escalation due to a missing bounds check in the lp driver. A kernel command-line adversary can overflow the parport_nr array to execute code (bsc#1039456). - CVE-2017-7542: The ip6_find_1stfragopt function in net/ipv6/output_core.c in the Linux kernel allowed local users to cause a denial of service (integer overflow and infinite loop) by leveraging the ability to open a raw socket (bsc#1049882). - CVE-2017-7533: Bug in inotify code allowing privilege escalation (bsc#1049483). - CVE-2017-11176: The mq_notify function in the Linux kernel did not set the sock pointer to NULL upon entry into the retry logic. During a user-space close of a Netlink socket, it allowed attackers to cause a denial of service (use-after-free) or possibly have unspecified other impact (bsc#1048275). - CVE-2017-11473: Buffer overflow in the mp_override_legacy_irq() function in arch/x86/kernel/acpi/boot.c in the Linux kernel allowed local users to gain privileges via a crafted ACPI table (bnc#1049603). - CVE-2017-1000365: The Linux Kernel imposed a size restriction on the arguments and environmental strings passed through RLIMIT_STACK/RLIM_INFINITY (1/4 of the size), but did not take the argument and environment pointers into account, which allowed attackers to bypass this limitation. (bnc#1039354) - CVE-2014-9922: The eCryptfs subsystem in the Linux kernel allowed local users to gain privileges via a large filesystem stack that includes an overlayfs layer, related to fs/ecryptfs/main.c and fs/overlayfs/super.c (bnc#1032340) - CVE-2017-8924: The edge_bulk_in_callback function in drivers/usb/serial/io_ti.c in the Linux kernel allowed local users to obtain sensitive information (in the dmesg ringbuffer and syslog) from uninitialized kernel memory by using a crafted USB device (posing as an io_ti USB serial device) to trigger an integer underflow (bnc#1038982). - CVE-2017-8925: The omninet_open function in drivers/usb/serial/omninet.c in the Linux kernel allowed local users to cause a denial of service (tty exhaustion) by leveraging reference count mishandling (bnc#1038981). - CVE-2017-1000380: sound/core/timer.c was vulnerable to a data race in the ALSA /dev/snd/timer driver resulting in local users being able to read information belonging to other users, i.e., uninitialized memory contents could have bene disclosed when a read and an ioctl happen at the same time (bnc#1044125) - CVE-2017-9242: The __ip6_append_data function in net/ipv6/ip6_output.c was too late in checking whether an overwrite of an skb data structure may occur, which allowed local users to cause a denial of service (system crash) via crafted system calls (bnc#1041431) - CVE-2017-1000363: A buffer overflow in kernel commandline handling of the last seen 2020-06-01 modified 2020-06-02 plugin id 103110 published 2017-09-11 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103110 title SUSE SLES11 Security Update : kernel (SUSE-SU-2017:2389-1) (Stack Clash) NASL family Huawei Local Security Checks NASL id EULEROS_SA-2019-1519.NASL description According to the versions of the kernel packages installed, the EulerOS Virtualization for ARM 64 installation on the remote host is affected by the following vulnerabilities : - The IPv6 SCTP implementation in net/sctp/ipv6.c in the Linux kernel through 3.11.1 uses data structures and function calls that do not trigger an intended configuration of IPsec encryption, which allows remote attackers to obtain sensitive information by sniffing the network.(CVE-2013-4350i1/4%0 - The sg_ioctl function in drivers/scsi/sg.c in the Linux kernel allows local users to cause a denial of service (stack-based buffer overflow) or possibly have unspecified other impacts via a large command size in an SG_NEXT_CMD_LEN ioctl call, leading to out-of-bounds write access in the sg_write function.(CVE-2017-7187i1/4%0 - An issue was discovered in can_can_gw_rcv in net/can/gw.c in the Linux kernel through 4.19.13. The CAN frame modification rules allow bitwise logical operations that can be also applied to the can_dlc field. Because of a missing check, the CAN drivers may write arbitrary content beyond the data registers in the CAN controller last seen 2020-03-19 modified 2019-05-14 plugin id 124972 published 2019-05-14 reporter This script is Copyright (C) 2019-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/124972 title EulerOS Virtualization for ARM 64 3.0.1.0 : kernel (EulerOS-SA-2019-1519) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2018-1854.NASL description An update for kernel is now available for Red Hat Enterprise Linux 6. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The kernel packages contain the Linux kernel, the core of any Linux operating system. Security Fix(es) : * An industry-wide issue was found in the way many modern microprocessor designs have implemented speculative execution of Load & Store instructions (a commonly used performance optimization). It relies on the presence of a precisely-defined instruction sequence in the privileged code as well as the fact that memory read from address to which a recent memory write has occurred may see an older value and subsequently cause an update into the microprocessor last seen 2020-06-01 modified 2020-06-02 plugin id 110600 published 2018-06-19 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/110600 title RHEL 6 : kernel (RHSA-2018:1854) (Spectre) NASL family Huawei Local Security Checks NASL id EULEROS_SA-2017-1123.NASL description According to the versions of the kernel packages installed, the EulerOS installation on the remote host is affected by the following vulnerabilities : - The regulator_ena_gpio_free function in drivers/regulator/core.c in the Linux kernel allows local users to gain privileges or cause a denial of service (use-after-free) via a crafted application.i1/4^CVE-2014-9940i1/4%0 - Race condition in the sctp_wait_for_sndbuf function in net/sctp/socket.c in the Linux kernel before 4.9.11 allows local users to cause a denial of service (assertion failure and panic) via a multithreaded application that peels off an association in a certain buffer-full state.i1/4^CVE-2017-5986i1/4%0 - net/sctp/socket.c in the Linux kernel through 4.10.1 does not properly restrict association peel-off operations during certain wait states, which allows local users to cause a denial of service (invalid unlock and double free) via a multithreaded application. NOTE: this vulnerability exists because of an incorrect fix for CVE-2017-5986.i1/4^CVE-2017-6353i1/4%0 - The ipxitf_ioctl function in net/ipx/af_ipx.c in the Linux kernel through 4.11.1 mishandles reference counts, which allows local users to cause a denial of service (use-after-free) or possibly have unspecified other impact via a failed SIOCGIFADDR ioctl call for an IPX interface.i1/4^CVE-2017-7487i1/4%0 - fs/ext4/inode.c in the Linux kernel before 4.6.2, when ext4 data=ordered mode is used, mishandles a needs-flushing-before-commit list, which allows local users to obtain sensitive information from other users last seen 2020-05-06 modified 2017-07-21 plugin id 101853 published 2017-07-21 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/101853 title EulerOS 2.0 SP2 : kernel (EulerOS-SA-2017-1123) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3324-1.NASL description It was discovered that the stack guard page for processes in the Linux kernel was not sufficiently large enough to prevent overlapping with the heap. An attacker could leverage this with another vulnerability to execute arbitrary code and gain administrative privileges (CVE-2017-1000364) Roee Hay discovered that the parallel port printer driver in the Linux kernel did not properly bounds check passed arguments. A local attacker with write access to the kernel command line arguments could use this to execute arbitrary code. (CVE-2017-1000363) A double free bug was discovered in the IPv4 stack of the Linux kernel. An attacker could use this to cause a denial of service (system crash). (CVE-2017-8890) Andrey Konovalov discovered an IPv6 out-of-bounds read error in the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 100922 published 2017-06-20 reporter Ubuntu Security Notice (C) 2017-2019 Canonical, Inc. / NASL script (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100922 title Ubuntu 17.04 : linux, linux-meta vulnerabilities (USN-3324-1) (Stack Clash) NASL family SuSE Local Security Checks NASL id OPENSUSE-2017-666.NASL description The openSUSE Leap 42.2 kernel was updated to 4.4.70 to receive various security and bugfixes. The following security bugs were fixed : - CVE-2017-9076: The dccp_v6_request_recv_sock function in net/dccp/ipv6.c in the Linux kernel mishandled inheritance, which allowed local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890 (bnc#1039885). - CVE-2017-9077: The tcp_v6_syn_recv_sock function in net/ipv6/tcp_ipv6.c in the Linux kernel mishandled inheritance, which allowed local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890 (bnc#1040069). - CVE-2017-9075: The sctp_v6_create_accept_sk function in net/sctp/ipv6.c in the Linux kernel mishandled inheritance, which allowed local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890 (bnc#1039883). - CVE-2017-9074: The IPv6 fragmentation implementation in the Linux kernel did not consider that the nexthdr field may be associated with an invalid option, which allowed local users to cause a denial of service (out-of-bounds read and BUG) or possibly have unspecified other impact via crafted socket and send system calls (bnc#1039882). - CVE-2017-7487: The ipxitf_ioctl function in net/ipx/af_ipx.c in the Linux kernel mishandled reference counts, which allowed local users to cause a denial of service (use-after-free) or possibly have unspecified other impact via a failed SIOCGIFADDR ioctl call for an IPX interface (bnc#1038879). - CVE-2017-8890: The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c in the Linux kernel allowed attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call (bnc#1038544). - CVE-2017-9150: The do_check function in kernel/bpf/verifier.c in the Linux kernel did not make the allow_ptr_leaks value available for restricting the output of the print_bpf_insn function, which allowed local users to obtain sensitive address information via crafted bpf system calls (bnc#1040279). - CVE-2017-7645: The NFSv2/NFSv3 server in the nfsd subsystem in the Linux kernel allowed remote attackers to cause a denial of service (system crash) via a long RPC reply, related to net/sunrpc/svc.c, fs/nfsd/nfs3xdr.c, and fs/nfsd/nfsxdr.c. (bsc#1034670) The following non-security bugs were fixed : - 9p: fix a potential acl leak (4.4.68 stable queue). - acpi / APEI: Add missing synchronize_rcu() on NOTIFY_SCI removal (bsc#1031717). - acpi / scan: Drop support for force_remove (bnc#1029607). - ahci: disable correct irq for dummy ports (bsc#1040125). - alsa: hda - Fix deadlock of controller device lock at unbinding (4.4.68 stable queue). - arm: 8452/3: PJ4: make coprocessor access sequences buildable in Thumb2 mode (4.4.68 stable queue). - arm: OMAP5 / DRA7: Fix HYP mode boot for thumb2 build (4.4.68 stable queue). - asoc: rt5640: use msleep() for long delays (bsc#1031717). - asoc: sti: Fix error handling if of_clk_get() fails (bsc#1031717). - blacklist 61e8a0d5a027 powerpc/pci: Fix endian bug in fixed PHB numbering (bsc#989311) - block: get rid of blk_integrity_revalidate() (4.4.68 stable queue). - bna: avoid writing uninitialized data into hw registers (bsc#966321 FATE#320156). - bnxt_en: allocate enough space for ->ntp_fltr_bmap (bsc#1020412 FATE#321671). - bpf, arm64: fix jit branch offset related to ldimm64 (4.4.68 stable queue). - brcmfmac: Ensure pointer correctly set if skb data location changes (4.4.68 stable queue). - brcmfmac: Make skb header writable before use (4.4.68 stable queue). - brcmfmac: restore stopping netdev queue when bus clogs up (bsc#1031717). - btrfs: add a flags field to btrfs_fs_info (bsc#1012452). - btrfs: add ASSERT for block group last seen 2020-06-05 modified 2017-06-09 plugin id 100711 published 2017-06-09 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100711 title openSUSE Security Update : the Linux Kernel (openSUSE-2017-666) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2017-3659.NASL description The remote Oracle Linux host is missing a security update for the Unbreakable Enterprise kernel package(s). last seen 2020-06-05 modified 2017-12-14 plugin id 105247 published 2017-12-14 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/105247 title Oracle Linux 6 / 7 : Unbreakable Enterprise kernel (ELSA-2017-3659) (BlueBorne) (Dirty COW) (Stack Clash) NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2017-2077.NASL description An update for kernel-rt is now available for Red Hat Enterprise Linux 7. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. The kernel-rt packages provide the Real Time Linux Kernel, which enables fine-tuning for systems with extremely high determinism requirements. Security Fix(es) : * An use-after-free flaw was found in the Linux kernel which enables a race condition in the L2TPv3 IP Encapsulation feature. A local user could use this flaw to escalate their privileges or crash the system. (CVE-2016-10200, Important) * A flaw was found that can be triggered in keyring_search_iterator in keyring.c if type->match is NULL. A local user could use this flaw to crash the system or, potentially, escalate their privileges. (CVE-2017-2647, Important) * It was found that the NFSv4 server in the Linux kernel did not properly validate layout type when processing NFSv4 pNFS LAYOUTGET and GETDEVICEINFO operands. A remote attacker could use this flaw to soft-lockup the system and thus cause denial of service. (CVE-2017-8797, Important) This update also fixes multiple Moderate and Low impact security issues : * CVE-2015-8839, CVE-2015-8970, CVE-2016-9576, CVE-2016-7042, CVE-2016-7097, CVE-2016-8645, CVE-2016-9576, CVE-2016-9588, CVE-2016-9806, CVE-2016-10088, CVE-2016-10147, CVE-2017-2596, CVE-2017-2671, CVE-2017-5970, CVE-2017-6001, CVE-2017-6951, CVE-2017-7187, CVE-2017-7616, CVE-2017-7889, CVE-2017-8890, CVE-2017-9074, CVE-2017-8890, CVE-2017-9075, CVE-2017-8890, CVE-2017-9076, CVE-2017-8890, CVE-2017-9077, CVE-2017-9242, CVE-2014-7970, CVE-2014-7975, CVE-2016-6213, CVE-2016-9604, CVE-2016-9685 Documentation for these issues is available from the Release Notes document linked from the References section. Red Hat would like to thank Igor Redko (Virtuozzo) and Andrey Ryabinin (Virtuozzo) for reporting CVE-2017-2647; Igor Redko (Virtuozzo) and Vasily Averin (Virtuozzo) for reporting CVE-2015-8970; Marco Grassi for reporting CVE-2016-8645; and Dmitry Vyukov (Google Inc.) for reporting CVE-2017-2596. The CVE-2016-7042 issue was discovered by Ondrej Kozina (Red Hat); the CVE-2016-7097 issue was discovered by Andreas Gruenbacher (Red Hat) and Jan Kara (SUSE); the CVE-2016-6213 and CVE-2016-9685 issues were discovered by Qian Cai (Red Hat); and the CVE-2016-9604 issue was discovered by David Howells (Red Hat). Additional Changes : For detailed information on other changes in this release, see the Red Hat Enterprise Linux 7.4 Release Notes linked from the References section. last seen 2020-06-01 modified 2020-06-02 plugin id 102151 published 2017-08-03 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102151 title RHEL 7 : kernel-rt (RHSA-2017:2077) NASL family Huawei Local Security Checks NASL id EULEROS_SA-2017-1122.NASL description According to the versions of the kernel packages installed, the EulerOS installation on the remote host is affected by the following vulnerabilities : - The regulator_ena_gpio_free function in drivers/regulator/core.c in the Linux kernel allows local users to gain privileges or cause a denial of service (use-after-free) via a crafted application.i1/4^CVE-2014-9940i1/4%0 - Race condition in the sctp_wait_for_sndbuf function in net/sctp/socket.c in the Linux kernel before 4.9.11 allows local users to cause a denial of service (assertion failure and panic) via a multithreaded application that peels off an association in a certain buffer-full state.i1/4^CVE-2017-5986i1/4%0 - net/sctp/socket.c in the Linux kernel through 4.10.1 does not properly restrict association peel-off operations during certain wait states, which allows local users to cause a denial of service (invalid unlock and double free) via a multithreaded application. NOTE: this vulnerability exists because of an incorrect fix for CVE-2017-5986.i1/4^CVE-2017-6353i1/4%0 - The ipxitf_ioctl function in net/ipx/af_ipx.c in the Linux kernel through 4.11.1 mishandles reference counts, which allows local users to cause a denial of service (use-after-free) or possibly have unspecified other impact via a failed SIOCGIFADDR ioctl call for an IPX interface.i1/4^CVE-2017-7487i1/4%0 - fs/ext4/inode.c in the Linux kernel before 4.6.2, when ext4 data=ordered mode is used, mishandles a needs-flushing-before-commit list, which allows local users to obtain sensitive information from other users last seen 2020-05-06 modified 2017-07-21 plugin id 101852 published 2017-07-21 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/101852 title EulerOS 2.0 SP1 : kernel (EulerOS-SA-2017-1122) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2060-1.NASL description This update for the Linux Kernel 3.12.62-60_62 fixes several issues. The following security bugs were fixed : - CVE-2017-7533: A bug in inotify code allowed local users to escalate privilege (bsc#1050751). - CVE-2017-7645: The NFSv2/NFSv3 server in the nfsd subsystem in the Linux kernel allowed remote attackers to cause a denial of service (system crash) via a long RPC reply, related to net/sunrpc/svc.c, fs/nfsd/nfs3xdr.c, and fs/nfsd/nfsxdr.c (bsc#1046191). - CVE-2017-2636: Race condition in drivers/tty/n_hdlc.c in the Linux kernel allowed local users to gain privileges or cause a denial of service (double free) by setting the HDLC line discipline (bsc#1027575). - CVE-2017-9242: The __ip6_append_data function in net/ipv6/ip6_output.c in the Linux kernel is too late in checking whether an overwrite of an skb data structure may occur, which allowed local users to cause a denial of service (system crash) via crafted system calls (bsc#1042892). - CVE-2017-8890: The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c in the Linux kernel allowed attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call (bsc#1038564). Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 102251 published 2017-08-08 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102251 title SUSE SLES12 Security Update : kernel (SUSE-SU-2017:2060-1) NASL family Fedora Local Security Checks NASL id FEDORA_2017-273B67D5EE.NASL description The 4.10.17 stable kernel update contains a number of important fixes across the tree. Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2017-05-26 plugin id 100435 published 2017-05-26 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100435 title Fedora 25 : kernel (2017-273b67d5ee) NASL family Debian Local Security Checks NASL id DEBIAN_DSA-3886.NASL description Several vulnerabilities have been discovered in the Linux kernel that may lead to a privilege escalation, denial of service or information leaks. - CVE-2017-7487 Li Qiang reported a reference counter leak in the ipxitf_ioctl function which may result into a use-after-free vulnerability, triggerable when a IPX interface is configured. - CVE-2017-7645 Tuomas Haanpaa and Matti Kamunen from Synopsys Ltd discovered that the NFSv2 and NFSv3 server implementations are vulnerable to an out-of-bounds memory access issue while processing arbitrarily long arguments sent by NFSv2/NFSv3 PRC clients, leading to a denial of service. - CVE-2017-7895 Ari Kauppi from Synopsys Ltd discovered that the NFSv2 and NFSv3 server implementations do not properly handle payload bounds checking of WRITE requests. A remote attacker with write access to a NFS mount can take advantage of this flaw to read chunks of arbitrary memory from both kernel-space and user-space. - CVE-2017-8064 Arnd Bergmann found that the DVB-USB core misused the device logging system, resulting in a use-after-free vulnerability, with unknown security impact. - CVE-2017-8890 It was discovered that the net_csk_clone_lock() function allows a remote attacker to cause a double free leading to a denial of service or potentially have other impact. - CVE-2017-8924 Johan Hovold found that the io_ti USB serial driver could leak sensitive information if a malicious USB device was connected. - CVE-2017-8925 Johan Hovold found a reference counter leak in the omninet USB serial driver, resulting in a use-after-free vulnerability. This can be triggered by a local user permitted to open tty devices. - CVE-2017-9074 Andrey Konovalov reported that the IPv6 fragmentation implementation could read beyond the end of a packet buffer. A local user or guest VM might be able to use this to leak sensitive information or to cause a denial of service (crash). - CVE-2017-9075 Andrey Konovalov reported that the SCTP/IPv6 implementation wrongly initialised address lists on connected sockets, resulting in a use-after-free vulnerability, a similar issue to CVE-2017-8890. This can be triggered by any local user. - CVE-2017-9076 / CVE-2017-9077 Cong Wang found that the TCP/IPv6 and DCCP/IPv6 implementations wrongly initialised address lists on connected sockets, a similar issue to CVE-2017-9075. - CVE-2017-9242 Andrey Konovalov reported a packet buffer overrun in the IPv6 implementation. A local user could use this for denial of service (memory corruption; crash) and possibly for privilege escalation. - CVE-2017-1000364 The Qualys Research Labs discovered that the size of the stack guard page is not sufficiently large. The stack-pointer can jump over the guard-page and moving from the stack into another memory region without accessing the guard-page. In this case no page-fault exception is raised and the stack extends into the other memory region. An attacker can exploit this flaw for privilege escalation. The default stack gap protection is set to 256 pages and can be configured via the stack_guard_gap kernel parameter on the kernel command line. Further details can be found at https://www.qualys.com/2017/06/19/stack-clash/stack-clash.txt last seen 2020-06-01 modified 2020-06-02 plugin id 100877 published 2017-06-20 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100877 title Debian DSA-3886-1 : linux - security update (Stack Clash) NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3342-1.NASL description USN 3326-1 fixed a vulnerability in the Linux kernel. However, that fix introduced regressions for some Java applications. This update addresses the issue. We apologize for the inconvenience. It was discovered that a use-after-free flaw existed in the filesystem encryption subsystem in the Linux kernel. A local attacker could use this to cause a denial of service (system crash). (CVE-2017-7374) Roee Hay discovered that the parallel port printer driver in the Linux kernel did not properly bounds check passed arguments. A local attacker with write access to the kernel command line arguments could use this to execute arbitrary code. (CVE-2017-1000363) Ingo Molnar discovered that the VideoCore DRM driver in the Linux kernel did not return an error after detecting certain overflows. A local attacker could exploit this issue to cause a denial of service (OOPS). (CVE-2017-5577) Li Qiang discovered that an integer overflow vulnerability existed in the Direct Rendering Manager (DRM) driver for VMware devices in the Linux kernel. A local attacker could use this to cause a denial of service (system crash) or possibly execute arbitrary code. (CVE-2017-7294) It was discovered that a double-free vulnerability existed in the IPv4 stack of the Linux kernel. An attacker could use this to cause a denial of service (system crash). (CVE-2017-8890) Andrey Konovalov discovered an IPv6 out-of-bounds read error in the Linux kernel last seen 2020-06-01 modified 2020-06-02 plugin id 101150 published 2017-06-30 reporter Ubuntu Security Notice (C) 2017-2019 Canonical, Inc. / NASL script (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/101150 title Ubuntu 16.10 : linux, linux-raspi2 vulnerabilities (USN-3342-1) NASL family Huawei Local Security Checks NASL id EULEROS_SA-2019-1525.NASL description According to the versions of the kernel packages installed, the EulerOS Virtualization for ARM 64 installation on the remote host is affected by the following vulnerabilities : - Mounting a crafted EXT4 image read-only leads to an attacker controlled memory corruption and SLAB-Out-of-Bounds reads.(CVE-2016-10208i1/4%0 - An issue was discovered in the hwpoison implementation in mm/memory-failure.c in the Linux kernel before 5.0.4. When soft_offline_in_use_page() runs on a thp tail page after pmd is split, an attacker can cause a denial of service (BUG).(CVE-2019-10124i1/4%0 - A stack-based buffer overflow flaw was found in the Linux kernel last seen 2020-03-19 modified 2019-05-14 plugin id 124978 published 2019-05-14 reporter This script is Copyright (C) 2019-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/124978 title EulerOS Virtualization for ARM 64 3.0.1.0 : kernel (EulerOS-SA-2019-1525) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2094-1.NASL description This update for the Linux Kernel 3.12.74-60_64_40 fixes several issues. The following security bugs were fixed : - CVE-2017-7533: A bug in inotify code allowed local users to escalate privilege (bsc#1050751). - CVE-2017-9242: The __ip6_append_data function in net/ipv6/ip6_output.c in the Linux kernel is too late in checking whether an overwrite of an skb data structure may occur, which allowed local users to cause a denial of service (system crash) via crafted system calls (bsc#1042892). - CVE-2017-8890: The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c in the Linux kernel allowed attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call (bsc#1038564). The update package also includes non-security fixes. See advisory for details. Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 102313 published 2017-08-09 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102313 title SUSE SLES12 Security Update : kernel (SUSE-SU-2017:2094-1) NASL family Oracle Linux Local Security Checks NASL id ORACLELINUX_ELSA-2017-3609.NASL description The remote Oracle Linux host is missing a security update for the Unbreakable Enterprise kernel package(s). last seen 2020-06-01 modified 2020-06-02 plugin id 102773 published 2017-08-25 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102773 title Oracle Linux 6 / 7 : Unbreakable Enterprise kernel (ELSA-2017-3609) (Stack Clash) NASL family Virtuozzo Local Security Checks NASL id VIRTUOZZO_VZA-2017-045.NASL description According to the version of the vzkernel package and the readykernel-patch installed, the Virtuozzo installation on the remote host is affected by the following vulnerabilities : - The tcp_v6_syn_recv_sock function in net/ipv6/tcp_ipv6.c in the Linux kernel mishandles inheritance, which allows local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. - The IPv6 DCCP implementation in the Linux kernel mishandles inheritance, which allows local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. - The sctp_v6_create_accept_sk function in net/sctp/ipv6.c in the Linux kernel mishandles inheritance, which allows local users to cause a denial of service or possibly have unspecified other impact via crafted system calls, a related issue to CVE-2017-8890. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. - The IPv6 fragmentation implementation in the Linux kernel through 4.11.1 does not consider that the nexthdr field may be associated with an invalid option, which allows local users to cause a denial of service (out-of-bounds read and BUG) or possibly have unspecified other impact via crafted socket and send system calls. - The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c in the Linux kernel allows attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call. An unprivileged local user could use this flaw to induce kernel memory corruption on the system, leading to a crash. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is unlikely. Note that Tenable Network Security has extracted the preceding description block directly from the Virtuozzo security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 100601 published 2017-06-05 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100601 title Virtuozzo 7 : readykernel-patch (VZA-2017-045) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2920-1.NASL description The SUSE Linux Enterprise 12 GA LTS kernel was updated to receive various security and bugfixes. The following security bugs were fixed : - CVE-2017-15649: net/packet/af_packet.c in the Linux kernel allowed local users to gain privileges via crafted system calls that trigger mishandling of packet_fanout data structures, because of a race condition (involving fanout_add and packet_do_bind) that leads to a use-after-free, a different vulnerability than CVE-2017-6346 (bnc#1064388). - CVE-2015-9004: kernel/events/core.c in the Linux kernel mishandled counter grouping, which allowed local users to gain privileges via a crafted application, related to the perf_pmu_register and perf_event_open functions (bnc#1037306). - CVE-2016-10229: udp.c in the Linux kernel allowed remote attackers to execute arbitrary code via UDP traffic that triggers an unsafe second checksum calculation during execution of a recv system call with the MSG_PEEK flag (bnc#1032268). - CVE-2016-9604: The handling of keyrings starting with last seen 2020-06-01 modified 2020-06-02 plugin id 104374 published 2017-11-03 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104374 title SUSE SLES12 Security Update : kernel (SUSE-SU-2017:2920-1) (KRACK) (Stack Clash) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2908-1.NASL description The SUSE Linux Enterprise 12 SP1 LTS kernel was updated to receive various security and bugfixes. The following security bugs were fixed : - CVE-2017-15649: net/packet/af_packet.c in the Linux kernel allowed local users to gain privileges via crafted system calls that trigger mishandling of packet_fanout data structures, because of a race condition (involving fanout_add and packet_do_bind) that leads to a use-after-free, a different vulnerability than CVE-2017-6346 (bnc#1064388). - CVE-2017-13080: Wi-Fi Protected Access (WPA and WPA2) allowed reinstallation of the Group Temporal Key (GTK) during the group key handshake, allowing an attacker within radio range to replay frames from access points to clients (bnc#1063667). - CVE-2017-15274: security/keys/keyctl.c in the Linux kernel did not consider the case of a NULL payload in conjunction with a nonzero length value, which allowed local users to cause a denial of service (NULL pointer dereference and OOPS) via a crafted add_key or keyctl system call, a different vulnerability than CVE-2017-12192 (bnc#1045327). - CVE-2017-15265: Use-after-free vulnerability in the Linux kernel allowed local users to have unspecified impact via vectors related to /dev/snd/seq (bnc#1062520). - CVE-2017-1000365: The Linux Kernel imposes a size restriction on the arguments and environmental strings passed through RLIMIT_STACK/RLIM_INFINITY (1/4 of the size), but did not take the argument and environment pointers into account, which allowed attackers to bypass this limitation. (bnc#1039354). - CVE-2017-12153: A security flaw was discovered in the nl80211_set_rekey_data() function in net/wireless/nl80211.c in the Linux kernel This function did not check whether the required attributes are present in a Netlink request. This request can be issued by a user with the CAP_NET_ADMIN capability and may result in a NULL pointer dereference and system crash (bnc#1058410). - CVE-2017-12154: The prepare_vmcs02 function in arch/x86/kvm/vmx.c in the Linux kernel did not ensure that the last seen 2020-06-01 modified 2020-06-02 plugin id 104271 published 2017-10-31 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104271 title SUSE SLES12 Security Update : kernel (SUSE-SU-2017:2908-1) (KRACK) (Stack Clash) NASL family Scientific Linux Local Security Checks NASL id SL_20170801_KERNEL_ON_SL7_X.NASL description Security Fix(es) : - An use-after-free flaw was found in the Linux kernel which enables a race condition in the L2TPv3 IP Encapsulation feature. A local user could use this flaw to escalate their privileges or crash the system. (CVE-2016-10200, Important) - A flaw was found that can be triggered in keyring_search_iterator in keyring.c if type->match is NULL. A local user could use this flaw to crash the system or, potentially, escalate their privileges. (CVE-2017-2647, Important) - It was found that the NFSv4 server in the Linux kernel did not properly validate layout type when processing NFSv4 pNFS LAYOUTGET and GETDEVICEINFO operands. A remote attacker could use this flaw to soft- lockup the system and thus cause denial of service. (CVE-2017-8797, Important) This update also fixes multiple Moderate and Low impact security issues : - CVE-2015-8839, CVE-2015-8970, CVE-2016-9576, CVE-2016-7042, CVE-2016-7097, CVE-2016-8645, CVE-2016-9576, CVE-2016-9588, CVE-2016-9806, CVE-2016-10088, CVE-2016-10147, CVE-2017-2596, CVE-2017-2671, CVE-2017-5970, CVE-2017-6001, CVE-2017-6951, CVE-2017-7187, CVE-2017-7616, CVE-2017-7889, CVE-2017-8890, CVE-2017-9074, CVE-2017-8890, CVE-2017-9075, CVE-2017-8890, CVE-2017-9076, CVE-2017-8890, CVE-2017-9077, CVE-2017-9242, CVE-2014-7970, CVE-2014-7975, CVE-2016-6213, CVE-2016-9604, CVE-2016-9685 last seen 2020-03-18 modified 2017-08-22 plugin id 102645 published 2017-08-22 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102645 title Scientific Linux Security Update : kernel on SL7.x x86_64 (20170801) NASL family SuSE Local Security Checks NASL id SUSE_SU-2017-2088-1.NASL description This update for the Linux Kernel 3.12.62-60_64_8 fixes several issues. The following security bugs were fixed : - CVE-2017-7533: A bug in inotify code allowed local users to escalate privilege (bsc#1050751). - CVE-2017-7645: The NFSv2/NFSv3 server in the nfsd subsystem in the Linux kernel allowed remote attackers to cause a denial of service (system crash) via a long RPC reply, related to net/sunrpc/svc.c, fs/nfsd/nfs3xdr.c, and fs/nfsd/nfsxdr.c (bsc#1046191). - CVE-2017-2636: Race condition in drivers/tty/n_hdlc.c in the Linux kernel allowed local users to gain privileges or cause a denial of service (double free) by setting the HDLC line discipline (bsc#1027575). - CVE-2017-9242: The __ip6_append_data function in net/ipv6/ip6_output.c in the Linux kernel is too late in checking whether an overwrite of an skb data structure may occur, which allowed local users to cause a denial of service (system crash) via crafted system calls (bsc#1042892). - CVE-2017-8890: The inet_csk_clone_lock function in net/ipv4/inet_connection_sock.c in the Linux kernel allowed attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging use of the accept system call (bsc#1038564). Note that Tenable Network Security has extracted the preceding description block directly from the SUSE security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 102307 published 2017-08-09 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/102307 title SUSE SLES12 Security Update : kernel (SUSE-SU-2017:2088-1)
Redhat
| advisories |
| ||||||||||||||||
| rpms |
|
Seebug
| bulletinFamily | exploit |
| description | ### About “Phoenix Talon” 2017 5 November 9, qimingxing e ADLab found that the Linux kernel there is a remote vulnerability“Phoenix Talon”the Phoenix claw fourth toe of Italy, and relates to CVE-2017-8890, CVE-2017-9075, CVE-2017-9076, CVE-2017-9077, can affect almost all Linux kernel 2.5.69 ~Linux kernel 4.11 kernel version, corresponding to the release version as well as the relevant domestic system. Can lead to a remote DOS, and in compliance with certain Use Conditions can lead to the RCE, including the transport layer of the TCP, DCCP, SCTP, and network layer IPv4 and IPv6 protocols are affected. In fact, the vulnerability in the Linux 4.11-rc8 version has been qimingxing e ADLab discovered, and later of the Linux 4.11 stable version also have this problem. The study of these vulnerabilities in the Linux kernel at least has been lurking for 11 years, the impact is extremely far-reaching. Qimingxing e ADLab has been the first time the“Phoenix Talon”vulnerability feedback to the Linux kernel community, the vulnerabilities reported after the Linux community in the Linux 4.12-rc1 merge the fix the issue the patch. These vulnerabilities to CVE-2017-8890 is the most serious to the Linux kernel vulnerability two scoring history the highest score, the CVSS V2 score achieved out of 10. 0, the CVSS V3 scoring history the highest score of 9. 8, The NVD on the search history involves Linux kernel vulnerabilities this rate the vulnerability of not more than 20, the following analysis to the vulnerability, for example, a reference to the official DESCRIPTION is as follows: “The inet_csk_clone_lock function in net/ipv4/inet_connection_sock. c in the Linux kernel through 4.10.15 allows attackers to cause a denial of service (double free) or possibly have unspecified other impact by leveraging the use of the accept system call.” ### The Vulnerability CVE-2017-8890 itself is a double free problem, using the setsockopt()function in the MCAST_JOIN_GROUP option, and call the accept()function to trigger the vulnerability. Then first take a look at a couple of multicast-related data structures: 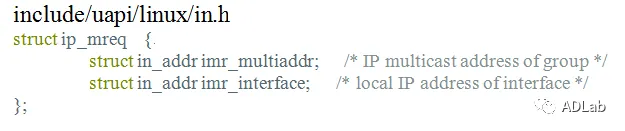 The structure of the two members are respectively used to specify the multicast group IP address and have to join a group of local interface IP address. ip_setsockopt()to achieve this function, by calling the ip_mc_join_group()the socket is added to the multicast group. 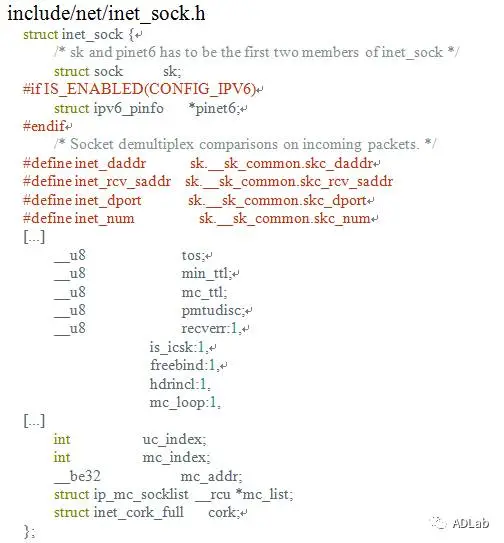 Where sk.__ sk_common. skc_rcv_saddr for multicast, receive only the address is sent to the multicast data, the unicast is concerned, only from the address represented the network card receiving data; mc_ttl for the multicast ttl; the mc_loop represents the multicast are sent to the loop; mc_index indicates multicast use the local device interface index; mc_addr represents a multicast source address; mc_list is a multicast list.  next_rcu points to the list of next nodes; multi indicates that the group information, i.e. in which one on the local interface, joined to which multicast group; sfmode is the filtering mode, the value of the MCAST_INCLUDE or MCAST_EXCLUDE, respectively, to receive only the sflist those listed the source of the multicast data packet and does not receive sflist those listed the source of multicast datagram; sflist is the source list. The following are from the vulnerability of memory assigned to the key code and the second release of the key code analysis. #### 1, The Allocate Memory allocation call chain: 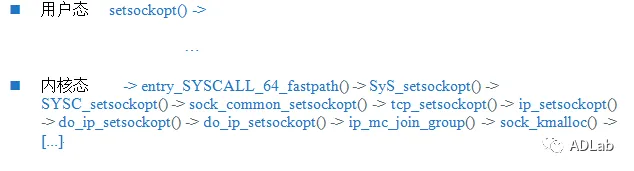 Use the setsockopt()function in the MCAST_JOIN_GROUP option. net/socket. c  Entering the kernel calls SyS_setsockopt()function, the level set is not SOL_SOCKET, General settings for the SOL_IP, in 1798 at line is called. Immediately call sock_common_setsockopt()function. net/ipv4/ip_sockglue. c 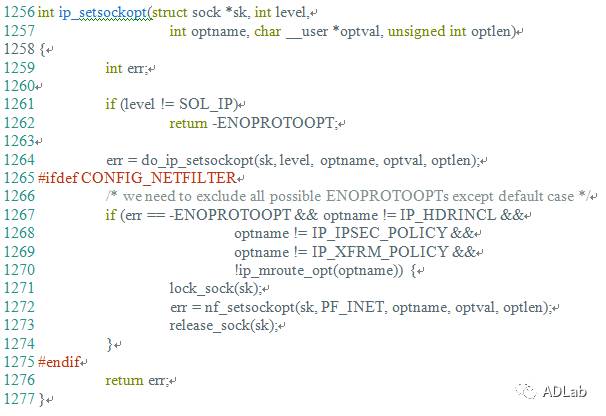 Then enter the ip_setsockopt()function, call the do_ip_setsockopt()function 1264 lines of code. net/ipv4/ip_sockglue. c 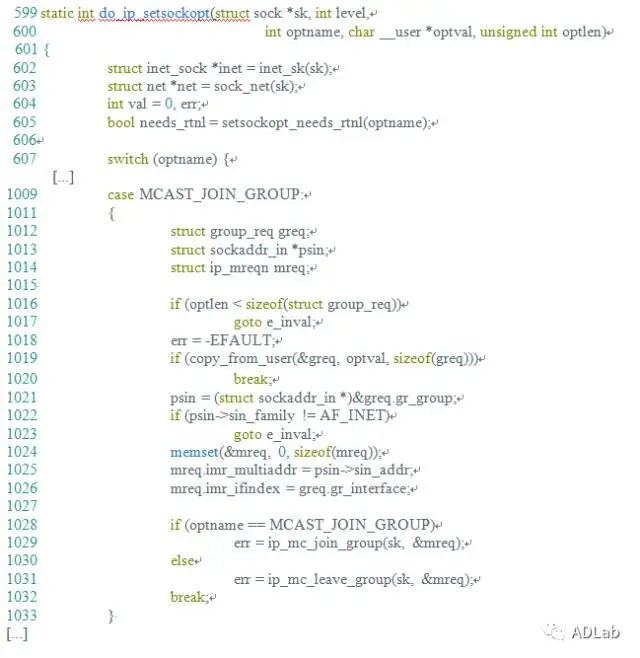 Code 1019 to 1021 call copy_from_user()to the user state data is copied to the kernel state. Before you have the option set to MCAST_JOIN_GROUP, followed by calls ip_mc_join_group()function: net/ipv4/igmp. c  Code 2128 line sock_kmalloc()for memory allocation. #### 2, The first free The kernel inside all the time produce a soft interrupt, and the vulnerability relates to a soft interrupt is generated by the accept()system call caused due to the function itself acting on the process context, and will not produce a soft interrupt. But to call accept (), it will be in the kernel induced some kind of software interrupt generate the software interrupt will invoke rcu_process_callbacks()function: kernel/rcu/tree. c 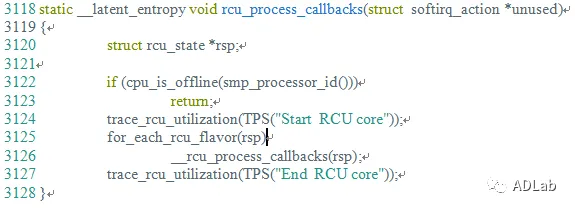 __rcu_process_callbacks call rcu_do_batch()function, as follows: kernel/rcu/tree. c 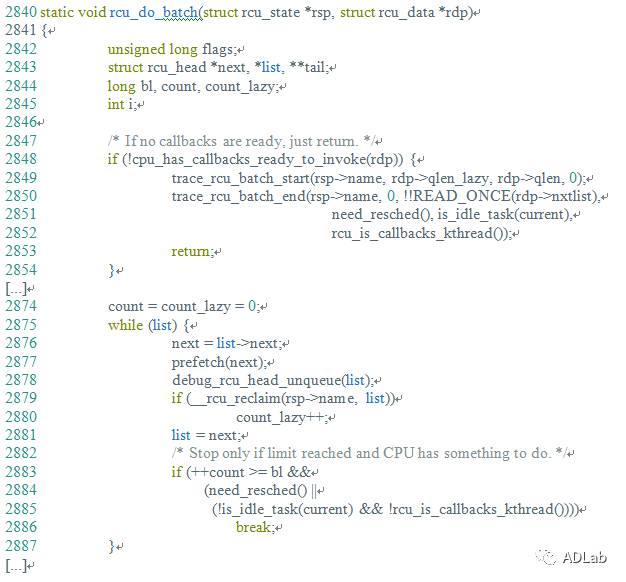 Note that the code in the first 2879 rows, function to__rcu_reclaim()to achieve the following: kernel/rcu/rcu. h 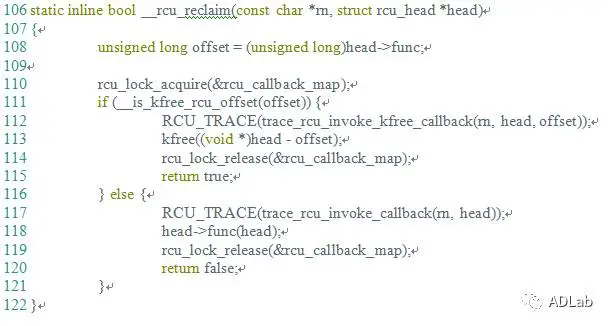 In 113 row call kfree()for the first release. #### 3, The second free When disconnecting the TCP connection, the kernel through the sock_close()function directly calls sock_release()to achieve the disconnect function, the function will empty the ops, update the global socket number, update the inode reference count. Then proceeds to inet_release()function call tcp_close()function to the end off the sock on. net/ipv4/af_inet. c 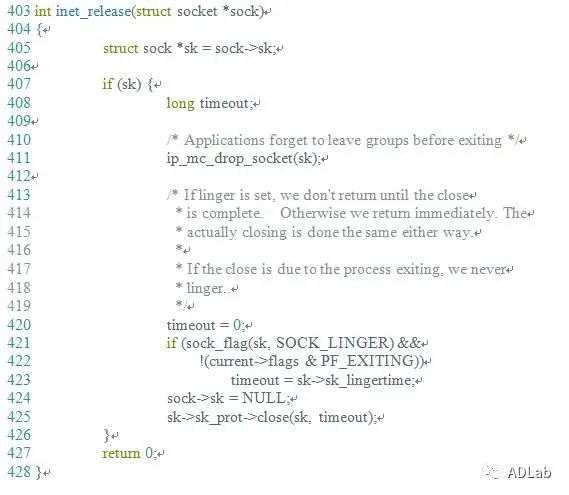 The user application disconnect the TCP connection, the kernel in use ip_mc_drop_socket()function is recovered. net/ipv4/igmp. c 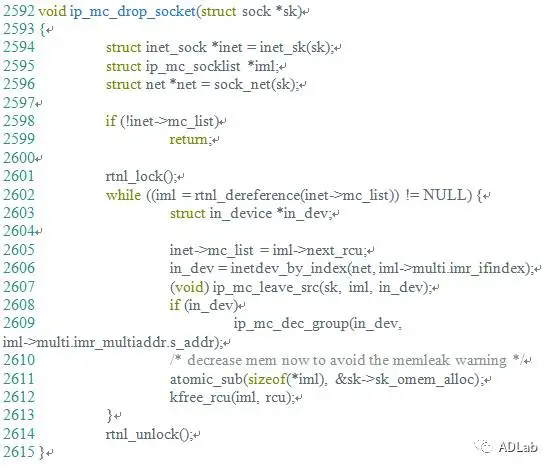 Code 2612 line calls kfree_rcu()for the second release. ### Affected #### 1, The affected kernel version The study, in theory, the Linux kernel 2.5.69 ~ Linux kernel 4.11 all versions are affected by the“Phoenix Talon”effect, and the open source community verification“Phoenix Talon”vulnerability affects the Linux kernel version part of the list is as follows:  By qimingxing e ADLab test the Linux kernel 4.11 also affected. #### 2, The affected release version The open source community verification section affected the release version is not the complete list as follows: _ Red Hat Enterprise MRG 2 _ Red Hat Enterprise Linux 7 _ Red Hat Enterprise Linux 6 _ Red Hat Enterprise Linux 5 _ SUSE Linux Enterprise Desktop 12 SP1 _ SUSE Linux Enterprise Desktop 12 SP2 _ SUSE Linux Enterprise Server 11 SP3 LTSS _ SUSE Linux Enterprise Server 11 SP4 _ SUSE Linux Enterprise Server 12 GA _ SUSE Linux Enterprise Server 12 SP1 _ SUSE Linux Enterprise Server 12 SP2 _ SUSE Linux Enterprise Server for SAP 11 SP3 _ SUSE Linux Enterprise Server for SAP 11 SP4 _ SUSE Linux Enterprise Server for SAP 12 GA _ SUSE Linux Enterprise Server for SAP 12 SP1 _ SUSE Linux Enterprise Server for SAP 12 SP2 In addition, qimingxing e ADLab on the following part of the release version to do the test, confirm that are subject to the“Phoenix Talon”vulnerability impact: _ Ubuntu 14.04 LTS (Trusty Tahr) _ Ubuntu 16.04 LTS (Xenial Xerus) _ Ubuntu 16.10(Yakkety Yak) _ Ubuntu 17.04(Zesty Zapus) * Ubuntu 17.10(Artful Aardvark) |
| id | SSV:93207 |
| last seen | 2017-11-19 |
| modified | 2017-06-16 |
| published | 2017-06-16 |
| reporter | Root |
| title | "Phoenix Talon" in Linux Kernel (Phoenix Talon) |
References
- http://git.kernel.org/cgit/linux/kernel/git/torvalds/linux.git/commit/?id=657831ffc38e30092a2d5f03d385d710eb88b09a
- http://git.kernel.org/cgit/linux/kernel/git/torvalds/linux.git/commit/?id=657831ffc38e30092a2d5f03d385d710eb88b09a
- http://www.debian.org/security/2017/dsa-3886
- http://www.debian.org/security/2017/dsa-3886
- http://www.securityfocus.com/bid/98562
- http://www.securityfocus.com/bid/98562
- https://access.redhat.com/errata/RHSA-2017:1842
- https://access.redhat.com/errata/RHSA-2017:1842
- https://access.redhat.com/errata/RHSA-2017:2077
- https://access.redhat.com/errata/RHSA-2017:2077
- https://access.redhat.com/errata/RHSA-2017:2669
- https://access.redhat.com/errata/RHSA-2017:2669
- https://access.redhat.com/errata/RHSA-2018:1854
- https://access.redhat.com/errata/RHSA-2018:1854
- https://github.com/torvalds/linux/commit/657831ffc38e30092a2d5f03d385d710eb88b09a
- https://github.com/torvalds/linux/commit/657831ffc38e30092a2d5f03d385d710eb88b09a
- https://source.android.com/security/bulletin/2017-09-01
- https://source.android.com/security/bulletin/2017-09-01