Vulnerabilities > CVE-2017-7234 - Open Redirect vulnerability in Djangoproject Django
Attack vector
NETWORK Attack complexity
LOW Privileges required
NONE Confidentiality impact
LOW Integrity impact
LOW Availability impact
NONE Summary
A maliciously crafted URL to a Django (1.10 before 1.10.7, 1.9 before 1.9.13, and 1.8 before 1.8.18) site using the ``django.views.static.serve()`` view could redirect to any other domain, aka an open redirect vulnerability.
Vulnerable Configurations
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Fake the Source of Data An adversary provides data under a falsified identity. The purpose of using the falsified identity may be to prevent traceability of the provided data or it might be an attempt by the adversary to assume the rights granted to another identity. One of the simplest forms of this attack would be the creation of an email message with a modified "From" field in order to appear that the message was sent from someone other than the actual sender. Results of the attack vary depending on the details of the attack, but common results include privilege escalation, obfuscation of other attacks, and data corruption/manipulation.
Nessus
NASL family FreeBSD Local Security Checks NASL id FREEBSD_PKG_DC880D6C195D11E78C630800277DCC69.NASL description Django team reports : These release addresses two security issues detailed below. We encourage all users of Django to upgrade as soon as possible. - Open redirect and possible XSS attack via user-supplied numeric redirect URLs - Open redirect vulnerability in django.views.static.serve() last seen 2020-06-01 modified 2020-06-02 plugin id 99193 published 2017-04-05 reporter This script is Copyright (C) 2017-2018 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/99193 title FreeBSD : django -- multiple vulnerabilities (dc880d6c-195d-11e7-8c63-0800277dcc69) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from the FreeBSD VuXML database : # # Copyright 2003-2018 Jacques Vidrine and contributors # # Redistribution and use in source (VuXML) and 'compiled' forms (SGML, # HTML, PDF, PostScript, RTF and so forth) with or without modification, # are permitted provided that the following conditions are met: # 1. Redistributions of source code (VuXML) must retain the above # copyright notice, this list of conditions and the following # disclaimer as the first lines of this file unmodified. # 2. Redistributions in compiled form (transformed to other DTDs, # published online in any format, converted to PDF, PostScript, # RTF and other formats) must reproduce the above copyright # notice, this list of conditions and the following disclaimer # in the documentation and/or other materials provided with the # distribution. # # THIS DOCUMENTATION IS PROVIDED BY THE AUTHOR AND CONTRIBUTORS "AS IS" # AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, # THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR # PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS # BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, # OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT # OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR # BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, # WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE # OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS DOCUMENTATION, # EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. # include("compat.inc"); if (description) { script_id(99193); script_version("3.6"); script_cvs_date("Date: 2018/11/10 11:49:46"); script_cve_id("CVE-2017-7233", "CVE-2017-7234"); script_name(english:"FreeBSD : django -- multiple vulnerabilities (dc880d6c-195d-11e7-8c63-0800277dcc69)"); script_summary(english:"Checks for updated packages in pkg_info output"); script_set_attribute( attribute:"synopsis", value: "The remote FreeBSD host is missing one or more security-related updates." ); script_set_attribute( attribute:"description", value: "Django team reports : These release addresses two security issues detailed below. We encourage all users of Django to upgrade as soon as possible. - Open redirect and possible XSS attack via user-supplied numeric redirect URLs - Open redirect vulnerability in django.views.static.serve()" ); script_set_attribute( attribute:"see_also", value:"https://www.djangoproject.com/weblog/2017/apr/04/security-releases/" ); # https://vuxml.freebsd.org/freebsd/dc880d6c-195d-11e7-8c63-0800277dcc69.html script_set_attribute( attribute:"see_also", value:"http://www.nessus.org/u?38ddf117" ); script_set_attribute(attribute:"solution", value:"Update the affected packages."); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:N"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:py27-django"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:py27-django110"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:py27-django18"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:py27-django19"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:py33-django"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:py33-django110"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:py33-django18"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:py33-django19"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:py34-django"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:py34-django110"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:py34-django18"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:py34-django19"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:py35-django"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:py35-django110"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:py35-django18"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:py35-django19"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:py36-django"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:py36-django110"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:py36-django18"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:freebsd:freebsd:py36-django19"); script_set_attribute(attribute:"cpe", value:"cpe:/o:freebsd:freebsd"); script_set_attribute(attribute:"vuln_publication_date", value:"2017/04/04"); script_set_attribute(attribute:"patch_publication_date", value:"2017/04/04"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/04/05"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2017-2018 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"FreeBSD Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/FreeBSD/release", "Host/FreeBSD/pkg_info"); exit(0); } include("audit.inc"); include("freebsd_package.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); if (!get_kb_item("Host/FreeBSD/release")) audit(AUDIT_OS_NOT, "FreeBSD"); if (!get_kb_item("Host/FreeBSD/pkg_info")) audit(AUDIT_PACKAGE_LIST_MISSING); flag = 0; if (pkg_test(save_report:TRUE, pkg:"py27-django<1.8.18")) flag++; if (pkg_test(save_report:TRUE, pkg:"py33-django<1.8.18")) flag++; if (pkg_test(save_report:TRUE, pkg:"py34-django<1.8.18")) flag++; if (pkg_test(save_report:TRUE, pkg:"py35-django<1.8.18")) flag++; if (pkg_test(save_report:TRUE, pkg:"py36-django<1.8.18")) flag++; if (pkg_test(save_report:TRUE, pkg:"py27-django18<1.8.18")) flag++; if (pkg_test(save_report:TRUE, pkg:"py33-django18<1.8.18")) flag++; if (pkg_test(save_report:TRUE, pkg:"py34-django18<1.8.18")) flag++; if (pkg_test(save_report:TRUE, pkg:"py35-django18<1.8.18")) flag++; if (pkg_test(save_report:TRUE, pkg:"py36-django18<1.8.18")) flag++; if (pkg_test(save_report:TRUE, pkg:"py27-django19<1.9.13")) flag++; if (pkg_test(save_report:TRUE, pkg:"py33-django19<1.9.13")) flag++; if (pkg_test(save_report:TRUE, pkg:"py34-django19<1.9.13")) flag++; if (pkg_test(save_report:TRUE, pkg:"py35-django19<1.9.13")) flag++; if (pkg_test(save_report:TRUE, pkg:"py36-django19<1.9.13")) flag++; if (pkg_test(save_report:TRUE, pkg:"py27-django110<1.10.7")) flag++; if (pkg_test(save_report:TRUE, pkg:"py33-django110<1.10.7")) flag++; if (pkg_test(save_report:TRUE, pkg:"py34-django110<1.10.7")) flag++; if (pkg_test(save_report:TRUE, pkg:"py35-django110<1.10.7")) flag++; if (pkg_test(save_report:TRUE, pkg:"py36-django110<1.10.7")) flag++; if (flag) { if (report_verbosity > 0) security_warning(port:0, extra:pkg_report_get()); else security_warning(0); exit(0); } else audit(AUDIT_HOST_NOT, "affected");NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3254-1.NASL description It was discovered that Django incorrectly handled numeric redirect URLs. A remote attacker could possibly use this issue to perform XSS attacks, and to use a Django server as an open redirect. (CVE-2017-7233) Phithon Gong discovered that Django incorrectly handled certain URLs when the jango.views.static.serve() view is being used. A remote attacker could possibly use a Django server as an open redirect. (CVE-2017-7234). Note that Tenable Network Security has extracted the preceding description block directly from the Ubuntu security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 99195 published 2017-04-05 reporter Ubuntu Security Notice (C) 2017-2019 Canonical, Inc. / NASL script (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/99195 title Ubuntu 12.04 LTS / 14.04 LTS / 16.04 LTS / 16.10 : python-django vulnerabilities (USN-3254-1) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Ubuntu Security Notice USN-3254-1. The text # itself is copyright (C) Canonical, Inc. See # <http://www.ubuntu.com/usn/>. Ubuntu(R) is a registered # trademark of Canonical, Inc. # include("compat.inc"); if (description) { script_id(99195); script_version("3.8"); script_cvs_date("Date: 2019/09/18 12:31:46"); script_cve_id("CVE-2017-7233", "CVE-2017-7234"); script_xref(name:"USN", value:"3254-1"); script_name(english:"Ubuntu 12.04 LTS / 14.04 LTS / 16.04 LTS / 16.10 : python-django vulnerabilities (USN-3254-1)"); script_summary(english:"Checks dpkg output for updated packages."); script_set_attribute( attribute:"synopsis", value: "The remote Ubuntu host is missing one or more security-related patches." ); script_set_attribute( attribute:"description", value: "It was discovered that Django incorrectly handled numeric redirect URLs. A remote attacker could possibly use this issue to perform XSS attacks, and to use a Django server as an open redirect. (CVE-2017-7233) Phithon Gong discovered that Django incorrectly handled certain URLs when the jango.views.static.serve() view is being used. A remote attacker could possibly use a Django server as an open redirect. (CVE-2017-7234). Note that Tenable Network Security has extracted the preceding description block directly from the Ubuntu security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues." ); script_set_attribute( attribute:"see_also", value:"https://usn.ubuntu.com/3254-1/" ); script_set_attribute( attribute:"solution", value:"Update the affected python-django and / or python3-django packages." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:N"); script_set_cvss_temporal_vector("CVSS2#E:U/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N"); script_set_cvss3_temporal_vector("CVSS:3.0/E:U/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"No known exploits are available"); script_set_attribute(attribute:"exploit_available", value:"false"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:canonical:ubuntu_linux:python-django"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:canonical:ubuntu_linux:python3-django"); script_set_attribute(attribute:"cpe", value:"cpe:/o:canonical:ubuntu_linux:12.04:-:lts"); script_set_attribute(attribute:"cpe", value:"cpe:/o:canonical:ubuntu_linux:14.04"); script_set_attribute(attribute:"cpe", value:"cpe:/o:canonical:ubuntu_linux:16.04"); script_set_attribute(attribute:"cpe", value:"cpe:/o:canonical:ubuntu_linux:16.10"); script_set_attribute(attribute:"vuln_publication_date", value:"2017/04/04"); script_set_attribute(attribute:"patch_publication_date", value:"2017/04/04"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/04/05"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"Ubuntu Security Notice (C) 2017-2019 Canonical, Inc. / NASL script (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Ubuntu Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/cpu", "Host/Ubuntu", "Host/Ubuntu/release", "Host/Debian/dpkg-l"); exit(0); } include("audit.inc"); include("ubuntu.inc"); include("misc_func.inc"); if ( ! get_kb_item("Host/local_checks_enabled") ) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/Ubuntu/release"); if ( isnull(release) ) audit(AUDIT_OS_NOT, "Ubuntu"); release = chomp(release); if (! preg(pattern:"^(12\.04|14\.04|16\.04|16\.10)$", string:release)) audit(AUDIT_OS_NOT, "Ubuntu 12.04 / 14.04 / 16.04 / 16.10", "Ubuntu " + release); if ( ! get_kb_item("Host/Debian/dpkg-l") ) audit(AUDIT_PACKAGE_LIST_MISSING); cpu = get_kb_item("Host/cpu"); if (isnull(cpu)) audit(AUDIT_UNKNOWN_ARCH); if ("x86_64" >!< cpu && cpu !~ "^i[3-6]86$") audit(AUDIT_LOCAL_CHECKS_NOT_IMPLEMENTED, "Ubuntu", cpu); flag = 0; if (ubuntu_check(osver:"12.04", pkgname:"python-django", pkgver:"1.3.1-4ubuntu1.23")) flag++; if (ubuntu_check(osver:"14.04", pkgname:"python-django", pkgver:"1.6.11-0ubuntu1.1")) flag++; if (ubuntu_check(osver:"16.04", pkgname:"python-django", pkgver:"1.8.7-1ubuntu5.5")) flag++; if (ubuntu_check(osver:"16.04", pkgname:"python3-django", pkgver:"1.8.7-1ubuntu5.5")) flag++; if (ubuntu_check(osver:"16.10", pkgname:"python-django", pkgver:"1.8.7-1ubuntu8.2")) flag++; if (ubuntu_check(osver:"16.10", pkgname:"python3-django", pkgver:"1.8.7-1ubuntu8.2")) flag++; if (flag) { security_report_v4( port : 0, severity : SECURITY_WARNING, extra : ubuntu_report_get() ); exit(0); } else { tested = ubuntu_pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "python-django / python3-django"); }NASL family Debian Local Security Checks NASL id DEBIAN_DLA-885.NASL description It was discovered that there were two vulnerabilities in python-django, a high-level Python web development framework. CVE-2017-7233 (#859515): Open redirect and possible XSS attack via user-supplied numeric redirect URLs. Django relies on user input in some cases (e.g. django.contrib.auth.views.login() and i18n) to redirect the user to an last seen 2020-03-17 modified 2017-04-06 plugin id 99202 published 2017-04-06 reporter This script is Copyright (C) 2017-2020 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/99202 title Debian DLA-885-1 : python-django security update code #%NASL_MIN_LEVEL 80502 # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Debian Security Advisory DLA-885-1. The text # itself is copyright (C) Software in the Public Interest, Inc. # include("compat.inc"); if (description) { script_id(99202); script_version("3.6"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/03/12"); script_cve_id("CVE-2017-7233", "CVE-2017-7234"); script_name(english:"Debian DLA-885-1 : python-django security update"); script_summary(english:"Checks dpkg output for the updated packages."); script_set_attribute( attribute:"synopsis", value:"The remote Debian host is missing a security update." ); script_set_attribute( attribute:"description", value: "It was discovered that there were two vulnerabilities in python-django, a high-level Python web development framework. CVE-2017-7233 (#859515): Open redirect and possible XSS attack via user-supplied numeric redirect URLs. Django relies on user input in some cases (e.g. django.contrib.auth.views.login() and i18n) to redirect the user to an 'on success' URL. The security check for these redirects (namely is_safe_url()) considered some numeric URLs (e.g. http:999999999) 'safe' when they shouldn't be. Also, if a developer relied on is_safe_url() to provide safe redirect targets and puts such a URL into a link, they could suffer from an XSS attack. CVE-2017-7234 (#895516): Open redirect vulnerability in django.views.static.serve; A maliciously crafted URL to a Django site using the serve() view could redirect to any other domain. The view no longer does any redirects as they don't provide any known, useful functionality. For Debian 7 'Wheezy', this issue has been fixed in python-django version 1.4.22-1+deb7u3. We recommend that you upgrade your python-django packages. NOTE: Tenable Network Security has extracted the preceding description block directly from the DLA security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues." ); script_set_attribute( attribute:"see_also", value:"https://lists.debian.org/debian-lts-announce/2017/04/msg00004.html" ); script_set_attribute( attribute:"see_also", value:"https://packages.debian.org/source/wheezy/python-django" ); script_set_attribute( attribute:"solution", value:"Upgrade the affected python-django, and python-django-doc packages." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:N"); script_set_cvss_temporal_vector("CVSS2#E:U/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N"); script_set_cvss3_temporal_vector("CVSS:3.0/E:U/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"No known exploits are available"); script_set_attribute(attribute:"exploit_available", value:"false"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:debian:debian_linux:python-django"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:debian:debian_linux:python-django-doc"); script_set_attribute(attribute:"cpe", value:"cpe:/o:debian:debian_linux:7.0"); script_set_attribute(attribute:"patch_publication_date", value:"2017/04/05"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/04/06"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2017-2020 Tenable Network Security, Inc."); script_family(english:"Debian Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/Debian/release", "Host/Debian/dpkg-l"); exit(0); } include("audit.inc"); include("debian_package.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); if (!get_kb_item("Host/Debian/release")) audit(AUDIT_OS_NOT, "Debian"); if (!get_kb_item("Host/Debian/dpkg-l")) audit(AUDIT_PACKAGE_LIST_MISSING); flag = 0; if (deb_check(release:"7.0", prefix:"python-django", reference:"1.4.22-1+deb7u3")) flag++; if (deb_check(release:"7.0", prefix:"python-django-doc", reference:"1.4.22-1+deb7u3")) flag++; if (flag) { if (report_verbosity > 0) security_warning(port:0, extra:deb_report_get()); else security_warning(0); exit(0); } else audit(AUDIT_HOST_NOT, "affected");NASL family Debian Local Security Checks NASL id DEBIAN_DSA-3835.NASL description Several vulnerabilities were discovered in Django, a high-level Python web development framework. The Common Vulnerabilities and Exposures project identifies the following problems : - CVE-2016-9013 Marti Raudsepp reported that a user with a hard-coded password is created when running tests with an Oracle database. - CVE-2016-9014 Aymeric Augustin discovered that Django does not properly validate the Host header against settings.ALLOWED_HOSTS when the debug setting is enabled. A remote attacker can take advantage of this flaw to perform DNS rebinding attacks. - CVE-2017-7233 It was discovered that is_safe_url() does not properly handle certain numeric URLs as safe. A remote attacker can take advantage of this flaw to perform XSS attacks or to use a Django server as an open redirect. - CVE-2017-7234 Phithon from Chaitin Tech discovered an open redirect vulnerability in the django.views.static.serve() view. Note that this view is not intended for production use. last seen 2020-06-01 modified 2020-06-02 plugin id 99695 published 2017-04-27 reporter This script is Copyright (C) 2017-2018 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/99695 title Debian DSA-3835-1 : python-django - security update code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from Debian Security Advisory DSA-3835. The text # itself is copyright (C) Software in the Public Interest, Inc. # include("compat.inc"); if (description) { script_id(99695); script_version("3.5"); script_cvs_date("Date: 2018/11/10 11:49:38"); script_cve_id("CVE-2016-9013", "CVE-2016-9014", "CVE-2017-7233", "CVE-2017-7234"); script_xref(name:"DSA", value:"3835"); script_name(english:"Debian DSA-3835-1 : python-django - security update"); script_summary(english:"Checks dpkg output for the updated package"); script_set_attribute( attribute:"synopsis", value:"The remote Debian host is missing a security-related update." ); script_set_attribute( attribute:"description", value: "Several vulnerabilities were discovered in Django, a high-level Python web development framework. The Common Vulnerabilities and Exposures project identifies the following problems : - CVE-2016-9013 Marti Raudsepp reported that a user with a hard-coded password is created when running tests with an Oracle database. - CVE-2016-9014 Aymeric Augustin discovered that Django does not properly validate the Host header against settings.ALLOWED_HOSTS when the debug setting is enabled. A remote attacker can take advantage of this flaw to perform DNS rebinding attacks. - CVE-2017-7233 It was discovered that is_safe_url() does not properly handle certain numeric URLs as safe. A remote attacker can take advantage of this flaw to perform XSS attacks or to use a Django server as an open redirect. - CVE-2017-7234 Phithon from Chaitin Tech discovered an open redirect vulnerability in the django.views.static.serve() view. Note that this view is not intended for production use." ); script_set_attribute( attribute:"see_also", value:"https://bugs.debian.org/cgi-bin/bugreport.cgi?bug=842856" ); script_set_attribute( attribute:"see_also", value:"https://bugs.debian.org/cgi-bin/bugreport.cgi?bug=859515" ); script_set_attribute( attribute:"see_also", value:"https://bugs.debian.org/cgi-bin/bugreport.cgi?bug=859516" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-9013" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2016-9014" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2017-7233" ); script_set_attribute( attribute:"see_also", value:"https://security-tracker.debian.org/tracker/CVE-2017-7234" ); script_set_attribute( attribute:"see_also", value:"https://packages.debian.org/source/jessie/python-django" ); script_set_attribute( attribute:"see_also", value:"https://www.debian.org/security/2017/dsa-3835" ); script_set_attribute( attribute:"solution", value: "Upgrade the python-django packages. For the stable distribution (jessie), these problems have been fixed in version 1.7.11-1+deb8u2." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P"); script_set_cvss_temporal_vector("CVSS2#E:U/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:U/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"No known exploits are available"); script_set_attribute(attribute:"exploit_available", value:"false"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:debian:debian_linux:python-django"); script_set_attribute(attribute:"cpe", value:"cpe:/o:debian:debian_linux:8.0"); script_set_attribute(attribute:"patch_publication_date", value:"2017/04/26"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/04/27"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2017-2018 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"Debian Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/Debian/release", "Host/Debian/dpkg-l"); exit(0); } include("audit.inc"); include("debian_package.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); if (!get_kb_item("Host/Debian/release")) audit(AUDIT_OS_NOT, "Debian"); if (!get_kb_item("Host/Debian/dpkg-l")) audit(AUDIT_PACKAGE_LIST_MISSING); flag = 0; if (deb_check(release:"8.0", prefix:"python-django", reference:"1.7.11-1+deb8u2")) flag++; if (deb_check(release:"8.0", prefix:"python-django-common", reference:"1.7.11-1+deb8u2")) flag++; if (deb_check(release:"8.0", prefix:"python-django-doc", reference:"1.7.11-1+deb8u2")) flag++; if (deb_check(release:"8.0", prefix:"python3-django", reference:"1.7.11-1+deb8u2")) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:deb_report_get()); else security_hole(0); exit(0); } else audit(AUDIT_HOST_NOT, "affected");NASL family SuSE Local Security Checks NASL id OPENSUSE-2018-318.NASL description This update for python3-Django to version 1.18.18 fixes multiple issues. Security issues fixed : - CVE-2018-7537: Fixed catastrophic backtracking in django.utils.text.Truncator. (bsc#1083305) - CVE-2018-7536: Fixed catastrophic backtracking in urlize and urlizetrunc template filters (bsc#1083304). - CVE-2016-7401: CSRF protection bypass on a site with Google Analytics (bsc#1001374). - CVE-2016-2513: User enumeration through timing difference on password hasher work factor upgrade (bsc#968000). - CVE-2016-2512: Fixed malicious redirect and possible XSS attack via user-supplied redirect URLs containing basic auth (bsc#967999). - CVE-2016-9013: User with hardcoded password created when running tests on Oracle (bsc#1008050). - CVE-2016-9014: DNS rebinding vulnerability when DEBUG=True (bsc#1008047). - CVE-2017-7234: Open redirect vulnerability in django.views.static.serve() (bsc#1031451). - CVE-2017-7233: Open redirect and possible XSS attack via user-supplied numeric redirect URLs (bsc#1031450). - CVE-2017-12794: Fixed XSS possibility in traceback section of technical 500 debug page (bsc#1056284) last seen 2020-06-05 modified 2018-03-27 plugin id 108641 published 2018-03-27 reporter This script is Copyright (C) 2018-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/108641 title openSUSE Security Update : python3-Django (openSUSE-2018-318) code #%NASL_MIN_LEVEL 80502 # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from openSUSE Security Update openSUSE-2018-318. # # The text description of this plugin is (C) SUSE LLC. # include("compat.inc"); if (description) { script_id(108641); script_version("1.3"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/06/04"); script_cve_id("CVE-2016-2048", "CVE-2016-2512", "CVE-2016-2513", "CVE-2016-6186", "CVE-2016-7401", "CVE-2016-9013", "CVE-2016-9014", "CVE-2017-12794", "CVE-2017-7233", "CVE-2017-7234", "CVE-2018-7536", "CVE-2018-7537"); script_name(english:"openSUSE Security Update : python3-Django (openSUSE-2018-318)"); script_summary(english:"Check for the openSUSE-2018-318 patch"); script_set_attribute( attribute:"synopsis", value:"The remote openSUSE host is missing a security update." ); script_set_attribute( attribute:"description", value: "This update for python3-Django to version 1.18.18 fixes multiple issues. Security issues fixed : - CVE-2018-7537: Fixed catastrophic backtracking in django.utils.text.Truncator. (bsc#1083305) - CVE-2018-7536: Fixed catastrophic backtracking in urlize and urlizetrunc template filters (bsc#1083304). - CVE-2016-7401: CSRF protection bypass on a site with Google Analytics (bsc#1001374). - CVE-2016-2513: User enumeration through timing difference on password hasher work factor upgrade (bsc#968000). - CVE-2016-2512: Fixed malicious redirect and possible XSS attack via user-supplied redirect URLs containing basic auth (bsc#967999). - CVE-2016-9013: User with hardcoded password created when running tests on Oracle (bsc#1008050). - CVE-2016-9014: DNS rebinding vulnerability when DEBUG=True (bsc#1008047). - CVE-2017-7234: Open redirect vulnerability in django.views.static.serve() (bsc#1031451). - CVE-2017-7233: Open redirect and possible XSS attack via user-supplied numeric redirect URLs (bsc#1031450). - CVE-2017-12794: Fixed XSS possibility in traceback section of technical 500 debug page (bsc#1056284)" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=1001374" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=1008047" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=1008050" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=1031450" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=1031451" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=1056284" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=1083304" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=1083305" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=967999" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=968000" ); script_set_attribute( attribute:"solution", value:"Update the affected python3-Django package." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P"); script_set_cvss_temporal_vector("CVSS2#E:POC/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:P/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:python3-Django"); script_set_attribute(attribute:"cpe", value:"cpe:/o:novell:opensuse:42.3"); script_set_attribute(attribute:"patch_publication_date", value:"2018/03/27"); script_set_attribute(attribute:"plugin_publication_date", value:"2018/03/27"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2018-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"SuSE Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/SuSE/release", "Host/SuSE/rpm-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/SuSE/release"); if (isnull(release) || release =~ "^(SLED|SLES)") audit(AUDIT_OS_NOT, "openSUSE"); if (release !~ "^(SUSE42\.3)$") audit(AUDIT_OS_RELEASE_NOT, "openSUSE", "42.3", release); if (!get_kb_item("Host/SuSE/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); flag = 0; if ( rpm_check(release:"SUSE42.3", reference:"python3-Django-1.8.19-5.3.1") ) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:rpm_report_get()); else security_hole(0); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "python3-Django"); }NASL family SuSE Local Security Checks NASL id OPENSUSE-2018-317.NASL description This update for python-Django to version 1.18.18 fixes multiple issues. Security issues fixed : - CVE-2018-7537: Fixed catastrophic backtracking in django.utils.text.Truncator. (bsc#1083305) - CVE-2018-7536: Fixed catastrophic backtracking in urlize and urlizetrunc template filters (bsc#1083304). - CVE-2016-7401: CSRF protection bypass on a site with Google Analytics (bsc#1001374). - CVE-2016-2513: User enumeration through timing difference on password hasher work factor upgrade (bsc#968000). - CVE-2016-2512: Fixed malicious redirect and possible XSS attack via user-supplied redirect URLs containing basic auth (bsc#967999). - CVE-2016-9013: User with hardcoded password created when running tests on Oracle (bsc#1008050). - CVE-2016-9014: DNS rebinding vulnerability when DEBUG=True (bsc#1008047). - CVE-2017-7234: Open redirect vulnerability in django.views.static.serve() (bsc#1031451). - CVE-2017-7233: Open redirect and possible XSS attack via user-supplied numeric redirect URLs (bsc#1031450). - CVE-2017-12794: Fixed XSS possibility in traceback section of technical 500 debug page (bsc#1056284) last seen 2020-06-05 modified 2018-03-27 plugin id 108640 published 2018-03-27 reporter This script is Copyright (C) 2018-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/108640 title openSUSE Security Update : python-Django (openSUSE-2018-317) code #%NASL_MIN_LEVEL 80502 # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from openSUSE Security Update openSUSE-2018-317. # # The text description of this plugin is (C) SUSE LLC. # include("compat.inc"); if (description) { script_id(108640); script_version("1.3"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/06/04"); script_cve_id("CVE-2016-2048", "CVE-2016-2512", "CVE-2016-2513", "CVE-2016-6186", "CVE-2016-7401", "CVE-2016-9013", "CVE-2016-9014", "CVE-2017-12794", "CVE-2017-7233", "CVE-2017-7234", "CVE-2018-7536", "CVE-2018-7537"); script_name(english:"openSUSE Security Update : python-Django (openSUSE-2018-317)"); script_summary(english:"Check for the openSUSE-2018-317 patch"); script_set_attribute( attribute:"synopsis", value:"The remote openSUSE host is missing a security update." ); script_set_attribute( attribute:"description", value: "This update for python-Django to version 1.18.18 fixes multiple issues. Security issues fixed : - CVE-2018-7537: Fixed catastrophic backtracking in django.utils.text.Truncator. (bsc#1083305) - CVE-2018-7536: Fixed catastrophic backtracking in urlize and urlizetrunc template filters (bsc#1083304). - CVE-2016-7401: CSRF protection bypass on a site with Google Analytics (bsc#1001374). - CVE-2016-2513: User enumeration through timing difference on password hasher work factor upgrade (bsc#968000). - CVE-2016-2512: Fixed malicious redirect and possible XSS attack via user-supplied redirect URLs containing basic auth (bsc#967999). - CVE-2016-9013: User with hardcoded password created when running tests on Oracle (bsc#1008050). - CVE-2016-9014: DNS rebinding vulnerability when DEBUG=True (bsc#1008047). - CVE-2017-7234: Open redirect vulnerability in django.views.static.serve() (bsc#1031451). - CVE-2017-7233: Open redirect and possible XSS attack via user-supplied numeric redirect URLs (bsc#1031450). - CVE-2017-12794: Fixed XSS possibility in traceback section of technical 500 debug page (bsc#1056284)" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=1001374" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=1008047" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=1008050" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=1031450" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=1031451" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=1056284" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=1083304" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=1083305" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=967999" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=968000" ); script_set_attribute( attribute:"solution", value:"Update the affected python-Django package." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P"); script_set_cvss_temporal_vector("CVSS2#E:POC/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:P/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:python-Django"); script_set_attribute(attribute:"cpe", value:"cpe:/o:novell:opensuse:42.3"); script_set_attribute(attribute:"patch_publication_date", value:"2018/03/27"); script_set_attribute(attribute:"plugin_publication_date", value:"2018/03/27"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2018-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"SuSE Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/SuSE/release", "Host/SuSE/rpm-list"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/SuSE/release"); if (isnull(release) || release =~ "^(SLED|SLES)") audit(AUDIT_OS_NOT, "openSUSE"); if (release !~ "^(SUSE42\.3)$") audit(AUDIT_OS_RELEASE_NOT, "openSUSE", "42.3", release); if (!get_kb_item("Host/SuSE/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); flag = 0; if ( rpm_check(release:"SUSE42.3", reference:"python-Django-1.8.19-6.4.1") ) flag++; if (flag) { if (report_verbosity > 0) security_hole(port:0, extra:rpm_report_get()); else security_hole(0); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "python-Django"); }
Seebug
| bulletinFamily | exploit |
| description | 来源:[同程安全应急响应中心](https://mp.weixin.qq.com/s?__biz=MzI4MzI4MDg1NA==&mid=2247483817&idx=1&sn=5a1fd58b65edf4b88d2f455a486b97bd) 作者:**Nearg1e@YSRC** 来自 @Phithon 的一个漏洞。 问题出现在:`django.views.static.serve()`函数上。该函数可以用来指定web站点的静态文件目录。如: ```python urlpatterns = [ url(r'^admin/', admin.site.urls), url(r'^staticp/(?P<path>.*)$', serve, {'document_root': os.path.join(settings.BASE_DIR, 'staticpath')}) ] ``` 这样django项目根目录下staticpath中的所有文件,就可以在staticp/目录中访问。e.g. `http://127.0.0.1:8000/staticp/test.css` 这种方法是不被django官方推荐在生成环境使用的,对安全性和性能都有一定影响。 问题代码如下 (django/views/static.py): ```python path = posixpath.normpath(unquote(path)) path = path.lstrip('/') newpath = '' for part in path.split('/'): if not part: ### Strip empty path components. continue drive, part = os.path.splitdrive(part) head, part = os.path.split(part) if part in (os.curdir, os.pardir): ### Strip '.' and '..' in path. continue newpath = os.path.join(newpath, part).replace('\\', '/') if newpath and path != newpath: return HttpResponseRedirect(newpath) ``` path既我们传入的路径,如果传入的路径为 `staticp/path.css` ,则`path=path.css` 。跟踪代码可知,path经过了unquote进行url解码,后来又 `replace('\\', '/')`,进入HttpResponseRedirect,很诡异的逻辑看起来很有问题。一般遇到这类型的函数我们会先试着找看看,任意文件读漏洞,但是这个对’.’和’..’进行了过滤,所以这边这个HttpResponseRedirect函数就成了帅的人的目标。 我们的最终目的是 `HttpResponseRedirect('//evil.neargle.com')` 或者 `HttpResponseRedirect('http://evil.neargle.com')`,那么就要使 `path != newpath`,那么path里面就必须带有’\‘,好的现在的我们传入 `’/staticp/%5C%5Cblog.neargle.com’` ,则`path=’\\blog.neargle.com’,newpath=’//blog.neargle.com’,HttpResponseRedirect` 就会跳转到 ’blog.neargle.com’ 造成跳转漏洞。 #### 修复 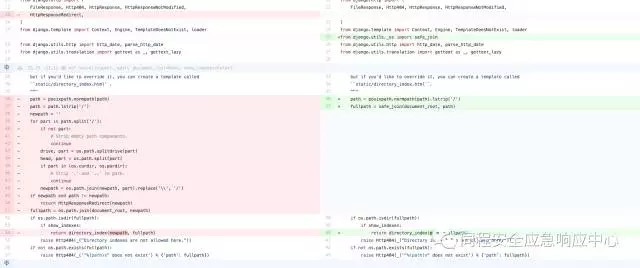 嗯,官方表示自己也不知道为什么要写这串代码,删了这一串代码然后用safe_url函数代替。 |
| id | SSV:92944 |
| last seen | 2017-11-19 |
| modified | 2017-04-13 |
| published | 2017-04-13 |
| reporter | Root |
| title | Django.views.static.serve url跳转漏洞(CVE-2017-7234) |
References
- http://www.debian.org/security/2017/dsa-3835
- http://www.debian.org/security/2017/dsa-3835
- http://www.securityfocus.com/bid/97401
- http://www.securityfocus.com/bid/97401
- http://www.securitytracker.com/id/1038177
- http://www.securitytracker.com/id/1038177
- https://www.djangoproject.com/weblog/2017/apr/04/security-releases/
- https://www.djangoproject.com/weblog/2017/apr/04/security-releases/