Vulnerabilities > CVE-2017-6926 - Information Exposure vulnerability in Drupal
Attack vector
NETWORK Attack complexity
LOW Privileges required
LOW Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
NONE Summary
In Drupal versions 8.4.x versions before 8.4.5 users with permission to post comments are able to view content and comments they do not have access to, and are also able to add comments to this content. This vulnerability is mitigated by the fact that the comment system must be enabled and the attacker must have permission to post comments.
Vulnerable Configurations
| Part | Description | Count |
|---|---|---|
| Application | 10 |
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Subverting Environment Variable Values The attacker directly or indirectly modifies environment variables used by or controlling the target software. The attacker's goal is to cause the target software to deviate from its expected operation in a manner that benefits the attacker.
- Footprinting An attacker engages in probing and exploration activity to identify constituents and properties of the target. Footprinting is a general term to describe a variety of information gathering techniques, often used by attackers in preparation for some attack. It consists of using tools to learn as much as possible about the composition, configuration, and security mechanisms of the targeted application, system or network. Information that might be collected during a footprinting effort could include open ports, applications and their versions, network topology, and similar information. While footprinting is not intended to be damaging (although certain activities, such as network scans, can sometimes cause disruptions to vulnerable applications inadvertently) it may often pave the way for more damaging attacks.
- Exploiting Trust in Client (aka Make the Client Invisible) An attack of this type exploits a programs' vulnerabilities in client/server communication channel authentication and data integrity. It leverages the implicit trust a server places in the client, or more importantly, that which the server believes is the client. An attacker executes this type of attack by placing themselves in the communication channel between client and server such that communication directly to the server is possible where the server believes it is communicating only with a valid client. There are numerous variations of this type of attack.
- Browser Fingerprinting An attacker carefully crafts small snippets of Java Script to efficiently detect the type of browser the potential victim is using. Many web-based attacks need prior knowledge of the web browser including the version of browser to ensure successful exploitation of a vulnerability. Having this knowledge allows an attacker to target the victim with attacks that specifically exploit known or zero day weaknesses in the type and version of the browser used by the victim. Automating this process via Java Script as a part of the same delivery system used to exploit the browser is considered more efficient as the attacker can supply a browser fingerprinting method and integrate it with exploit code, all contained in Java Script and in response to the same web page request by the browser.
- Session Credential Falsification through Prediction This attack targets predictable session ID in order to gain privileges. The attacker can predict the session ID used during a transaction to perform spoofing and session hijacking.
Nessus
NASL family CGI abuses NASL id DRUPAL_8_4_5.NASL description According to its self-reported version, the instance of Drupal running on the remote web server is 8.x prior to 8.4.5. It is, therefore, affected by multiple vulnerabilities : - A flaw exists with the Comment Reply Form. An authenticated remote attacker could add or view comments that they do not have access to. (CVE-2017-6926) - A flaw exists with the Drupal.checkPlain() function due to improper handling of HTML injection. A remote attacker, with a specially crafted request, could potentially execute arbitrary script code within the trust relationship between the browser and server. (CVE-2017-6927) - A flaw exists with node access controls with a multilingual site due to defaulting to the untranslated version as a fallback. A remote attacker could potentially bypass access restrictions. (CVE-2017-6930) - A flaw exists with the Settings Tray module. A remote attacker could update data the do not have permission for. (CVE-2017-6931) Note that Nessus has not tested for these issues but has instead relied only on the application last seen 2020-06-01 modified 2020-06-02 plugin id 107089 published 2018-03-01 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/107089 title Drupal 8.x < 8.4.5 Multiple Vulnerabilities (SA-CORE-2018-001) NASL family Fedora Local Security Checks NASL id FEDORA_2018-D8269E4262.NASL description - https://www.drupal.org/SA-CORE-2018-002 - https://www.drupal.org/SA-CORE-2018-001 Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2018-04-11 plugin id 108978 published 2018-04-11 reporter This script is Copyright (C) 2018-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/108978 title Fedora 26 : drupal7 (2018-d8269e4262) NASL family Fedora Local Security Checks NASL id FEDORA_2018-143886FDBD.NASL description - https://www.drupal.org/SA-CORE-2018-002 - https://www.drupal.org/SA-CORE-2018-001 Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2018-04-11 plugin id 108977 published 2018-04-11 reporter This script is Copyright (C) 2018-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/108977 title Fedora 27 : drupal7 (2018-143886fdbd) NASL family Fedora Local Security Checks NASL id FEDORA_2018-906BA26B4D.NASL description - [8.4.6](https://www.drupal.org/project/drupal/releases/8 .4.6) - [SA-CORE-2018-002 (CVE-2018-7600)](https://www.drupal.org/SA-CORE-2018-002 ) - [8.4.5](https://www.drupal.org/project/drupal/releases/8 .4.5) - [SA-CORE-2018-001 (CVE-2017-6926 / CVE-2017-6927 / CVE-2017-6930 / CVE-2017-6931)](https://www.drupal.org/SA-CORE-2018-001) - [8.4.4](https://www.drupal.org/project/drupal/releases/8 .4.4) - [8.4.3](https://www.drupal.org/project/drupal/releases/8 .4.3) - [8.4.2](https://www.drupal.org/project/drupal/releases/8 .4.2) - [8.4.1](https://www.drupal.org/project/drupal/releases/8 .4.1) - [8.4.0](https://www.drupal.org/project/drupal/releases/8 .4.0) - [8.4.0-rc2](https://www.drupal.org/project/drupal/releas es/8.4.0-rc2) - [8.4.0-rc1](https://www.drupal.org/project/drupal/releas es/8.4.0-rc1) - [8.4.0-beta1](https://www.drupal.org/project/drupal/rele ases/8.4.0-beta1) - [8.4.0-alpha1](https://www.drupal.org/project/drupal/rel eases/8.4.0-alpha1) Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2019-01-03 plugin id 120615 published 2019-01-03 reporter This script is Copyright (C) 2019-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/120615 title Fedora 28 : drupal8 (2018-906ba26b4d) (Drupalgeddon 2) NASL family FreeBSD Local Security Checks NASL id FREEBSD_PKG_57580FCC1A6111E897E000E04C1EA73D.NASL description Drupal Security Team reports : CVE-2017-6926: Comment reply form allows access to restricted content CVE-2017-6927: JavaScript cross-site scripting prevention is incomplete CVE-2017-6928: Private file access bypass - Moderately Critical CVE-2017-6929: jQuery vulnerability with untrusted domains - Moderately Critical CVE-2017-6930: Language fallback can be incorrect on multilingual sites with node access restrictions CVE-2017-6931: Settings Tray access bypass CVE-2017-6932: External link injection on 404 pages when linking to the current page last seen 2020-06-01 modified 2020-06-02 plugin id 106994 published 2018-02-26 reporter This script is Copyright (C) 2018 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/106994 title FreeBSD : drupal -- Drupal Core - Multiple Vulnerabilities (57580fcc-1a61-11e8-97e0-00e04c1ea73d) NASL family Fedora Local Security Checks NASL id FEDORA_2018-922CC2FBAA.NASL description - [8.3.9](https://www.drupal.org/project/drupal/releases/8 .3.9) - [SA-CORE-2018-002 (CVE-2018-7600)](https://www.drupal.org/SA-CORE-2018-002 ) - [8.3.8](https://www.drupal.org/project/drupal/releases/8 .3.8) - [SA-CORE-2018-001 (CVE-2017-6926 / CVE-2017-6927 / CVE-2017-6930 / CVE-2017-6931)](https://www.drupal.org/SA-CORE-2018-001) Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2018-04-24 plugin id 109288 published 2018-04-24 reporter This script is Copyright (C) 2018-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/109288 title Fedora 26 : drupal8 (2018-922cc2fbaa) (Drupalgeddon 2) NASL family Fedora Local Security Checks NASL id FEDORA_2018-75BCA4C5A0.NASL description - https://www.drupal.org/SA-CORE-2018-002 - https://www.drupal.org/SA-CORE-2018-001 Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2019-01-03 plugin id 120534 published 2019-01-03 reporter This script is Copyright (C) 2019-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/120534 title Fedora 28 : drupal7 (2018-75bca4c5a0)
Seebug
| bulletinFamily | exploit |
| description | 作者:绿盟科技 来源:<http://blog.nsfocus.net/drupal8-cve-2017-6926/> 近期,著名的Drupal CMS网站爆出7个漏洞,其中1个严重漏洞CVE-2017-6926,具有发表评论权限的用户可以查看他们无权访问的内容和评论,并且还可以为该内容添加评论。绿盟科技于上周发布了[《Drupal下周将发布重要安全补丁威胁预警通告》](http://blog.nsfocus.net/drupal-vulnerability/ "《Drupal下周将发布重要安全补丁威胁预警通告》")。 本篇文章对Drupal 8 – CVE-2017-6926漏洞进行了详细分析。 #### CVE-2017-6926 漏洞详情 先看下drupal官网的通告: <https://www.drupal.org/sa-core-2018-001></https://www.drupal.org/sa-core-2018-001> 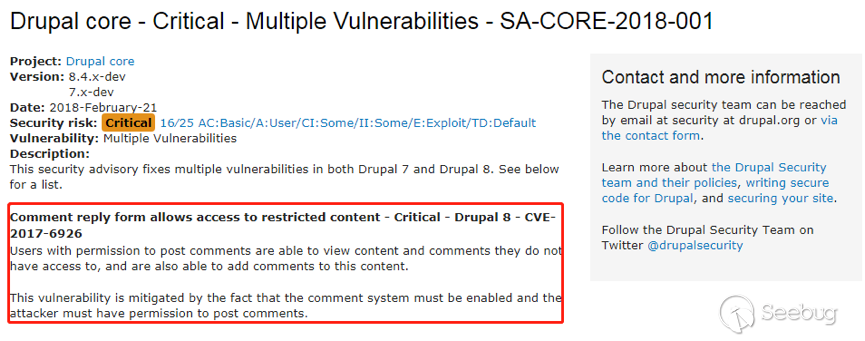 有发布评论权限的用户,可以查看他们无权访问的内容和评论。 并且还可以为此内容添加评论。 想要触发这个漏洞,必须启用评论系统,并且攻击者必须有权发布评论。 从漏洞描述来看,问题可能出在评论的权限控制上了。 但是这里有一个坑,笔者当时就掉进去了:这里的权限,指的是文章的权限?还是评论的权限呢?是攻击者可以访问他们不公开的评论呢?还是攻击者可以访问不公开的文章的公开评论呢?下面我会详细的分析这个漏洞,并给出上面问题的答案。 漏洞是在8.4.5上解决的,看一下8.4.5修改的内容: 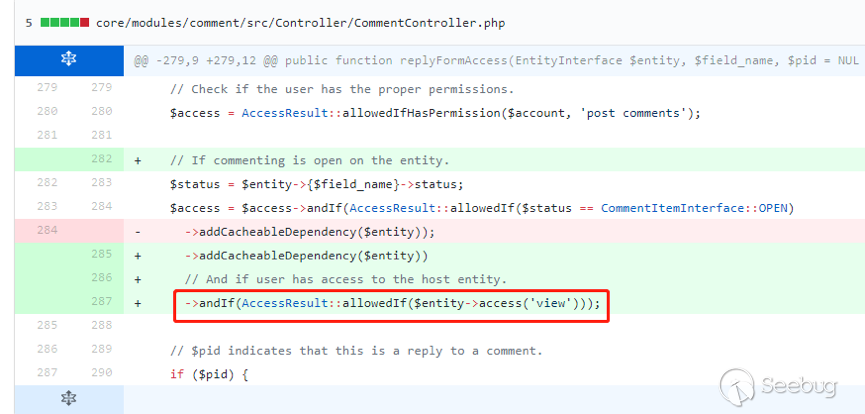 这里在CommentController.php(评论控制器)里加上了一个对entity实体是否有view权限的判断。 这个好理解,之前没有对entity的权限进行判断,导致不可view的entity也通过了权限检查,从而导致了越权。 我们看下关于entity的介绍:  我们再看下漏洞存在的函数 `\core\modules\comment\src\Controller\CommentController.php` ``` public function replyFormAccess(EntityInterface $entity, $field_name, $pid = NULL) { // Check if entity and field exists. $fields = $this->commentManager->getFields($entity->getEntityTypeId()); if (empty($fields[$field_name])) { throw new NotFoundHttpException(); } $account = $this->currentUser(); // Check if the user has the proper permissions. $access = AccessResult::allowedIfHasPermission($account, 'post comments'); $status = $entity->{$field_name}->status; $access = $access->andIf(AccessResult::allowedIf($status == CommentItemInterface::OPEN) ->addCacheableDependency($entity)); ``` 再来看下这个方法的路由 `\core\modules\comment\comment.routing.yml` ``` comment.reply: path: '/comment/reply/{entity_type}/{entity}/{field_name}/{pid}' defaults: _controller: '\Drupal\comment\Controller\CommentController::getReplyForm' _title: 'Add new comment' pid: ~ requirements: _custom_access: '\Drupal\comment\Controller\CommentController::replyFormAccess' options: parameters: entity: type: entity:{entity_type} ``` 可见replyFormAccess其实是getReplyForm方法的权限检查模块,传入replyFormAccess方法的参数将会是`{entity_type}/{entity}/{field_name}/{pid}` 我们实际测一下,访问这个模块,看看发送的参数是什么样子的: 对kingsguard test评论进行评论: 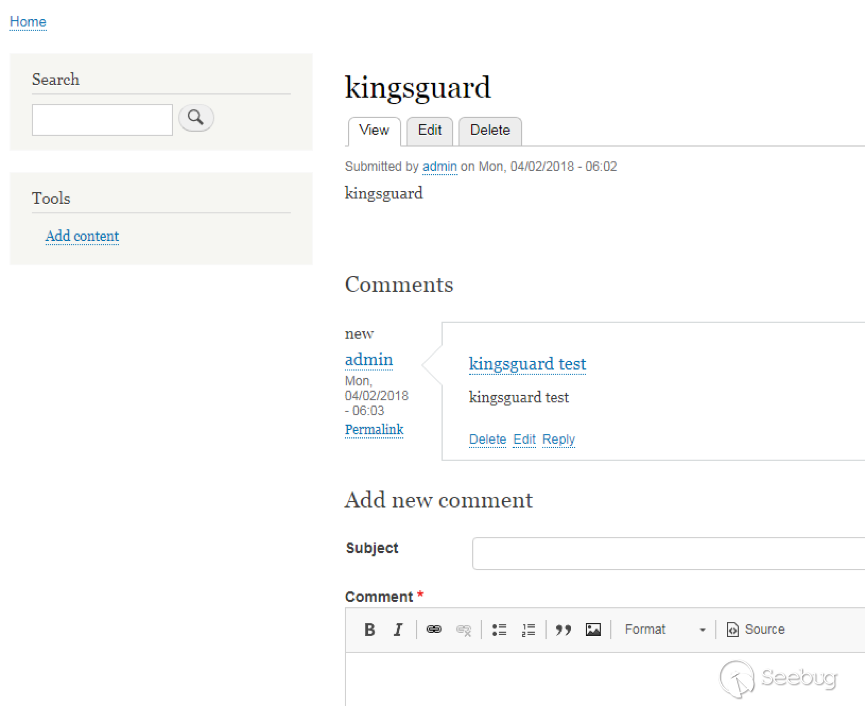 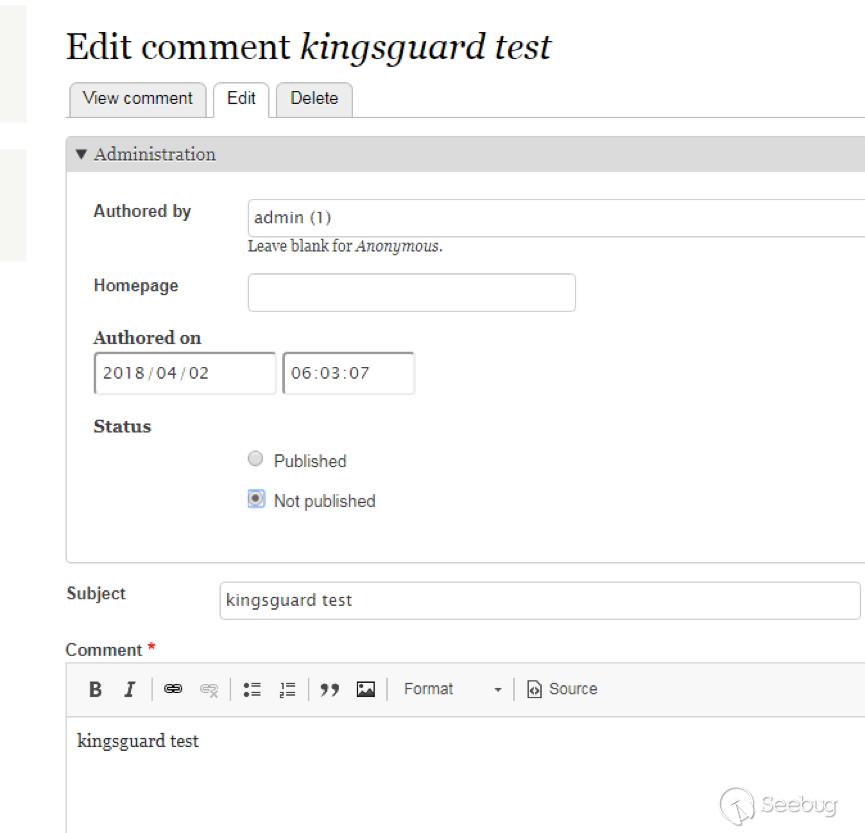 注意看url:<http://127.0.0.1/d/drupal4/comment/reply/node/1/comment/1></http://127.0.0.1/d/drupal4/comment/reply/node/1/comment/1> {entity_type}:node {entity}:1 {field_name}:comment {pid}:1 现在可以明确了,传入replyFormAccess里的entity类型是node节点类型,接着下断看下entity的数据 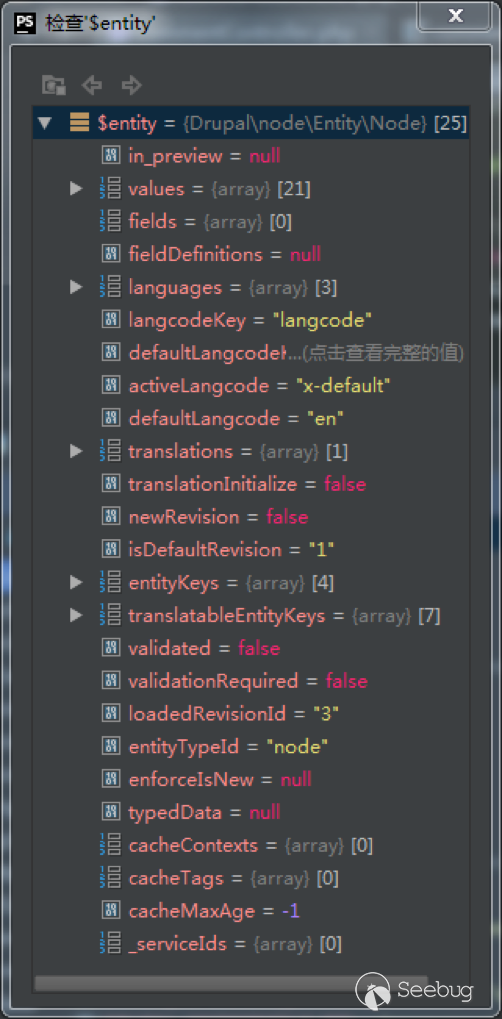 在大概知道$entity是什么之后,我们再来看下补丁代码: 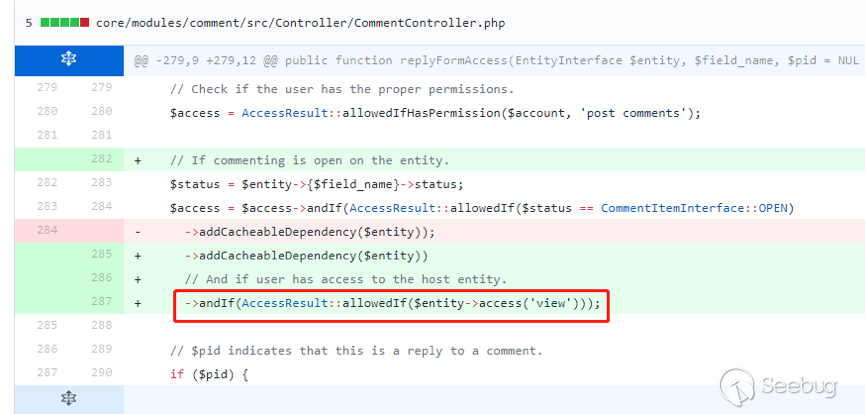 可见补丁加了一个判断 ``` andIf(AccessResult::allowedIf($entity->access('view'))); ``` 看下allowedIf方法是怎么实现的: ``` public static function allowedIf($condition) { return $condition ? static::allowed() : static::neutral(); } ``` 可见allowedIf通过传入的参数的True/False来判断是否有权限进行操作。 这样看来,$entity->access(‘view’)只有True/False两种可能出现的值。 我们在后台下断,并且构造一个$test方法值等于$entity->access(‘view’),下断看看$test何时能为False: 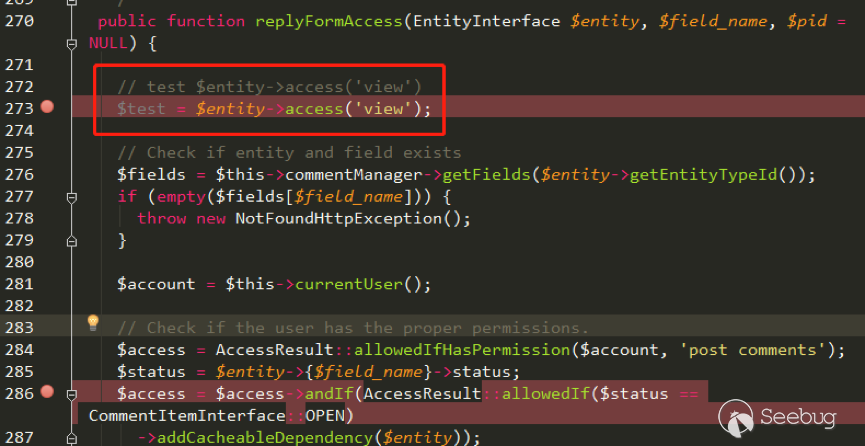 首先来找找,关于回复评论处的权限设置: 我们在admin账号下,发表一片名为kingsguard的文章,此文章有一个kingsguard test的评论: 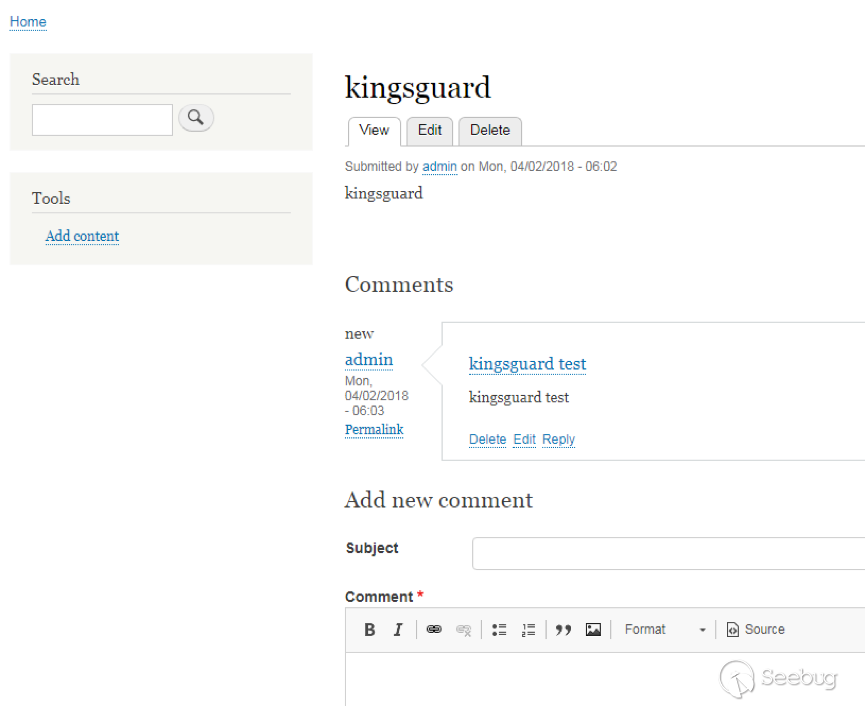 我们将kingsguard test 这条评论的权限编辑成不公开 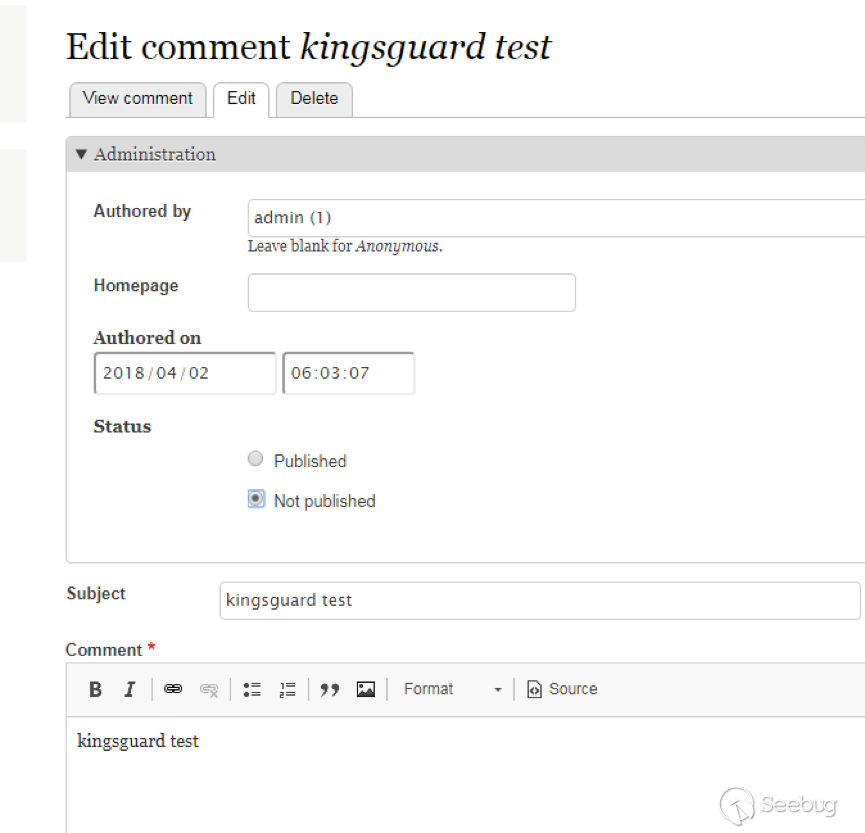 我们用admin账号回复一下这个评论,后台看下$$test = $entity->access(‘view’);的值: 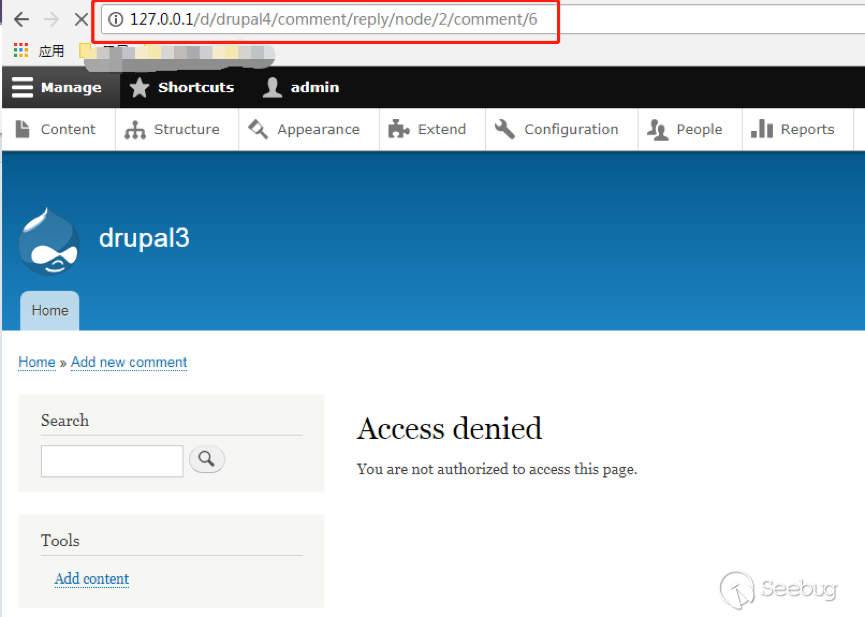 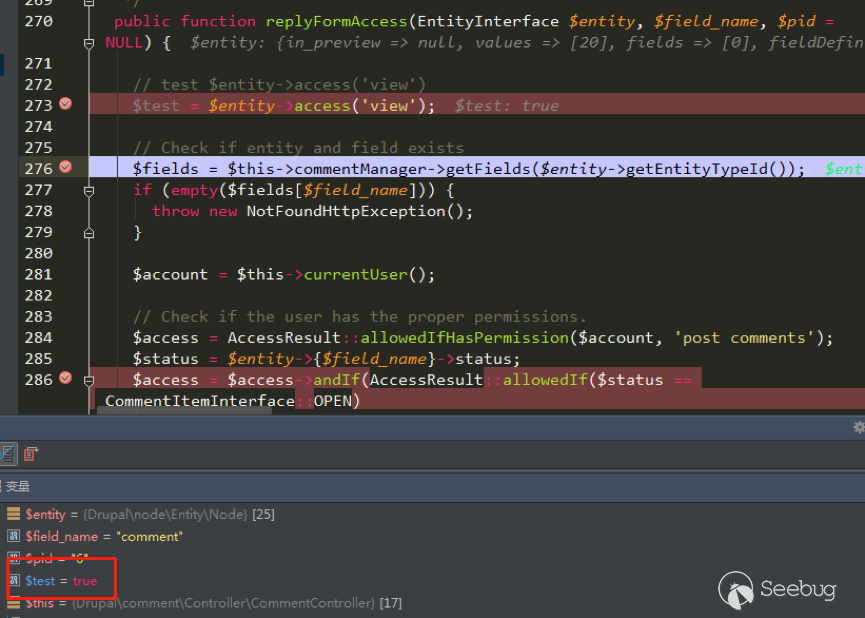 毫无疑问,$test的值是true 现在用另一个账号登录,也访问<http://127.0.0.1/d/drupal4/comment/reply/node/2/comment/6></http://127.0.0.1/d/drupal4/comment/reply/node/2/comment/6>这个连接试试: 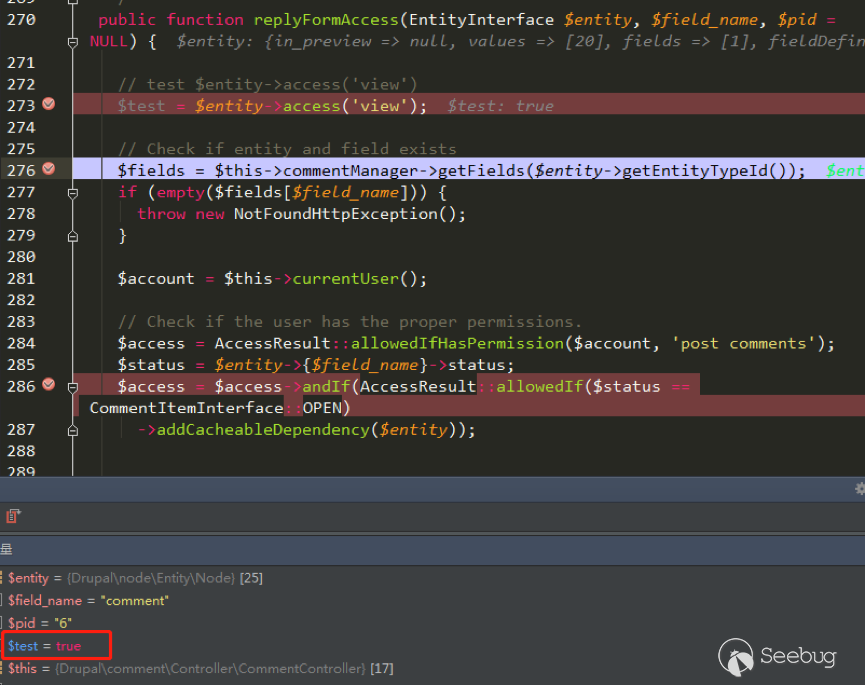 $test仍然为true。 当时笔者就是掉到这个坑里了,明明这条评论设置为不公开,为什么不同用户访问,$entity->access(‘view’)都是true呢? 后来证明了,其实这里的$entity,指的不是评论,而是这篇文章,$entity->access(‘view’)也同样不是单条评论的是否有view权限,而是这篇文章是否有view权限。 其实观察url就可以发现这个问题了: <http://127.0.0.1/d/drupal4/comment/reply/node/1/comment/6></http://127.0.0.1/d/drupal4/comment/reply/node/1/comment/6>(回复第一篇文章的第六个评论) <http://127.0.0.1/d/drupal4/comment/reply/node/2/comment/6></http://127.0.0.1/d/drupal4/comment/reply/node/2/comment/6>(回复第二篇文章的第六个评论) 显然这里的1和2,指的是文章的编号,同时也是entity的编号,那显然entity指的是文章而不是评论。 我们用admin账号编辑kingsguard这篇文章,把published选项的勾去掉: 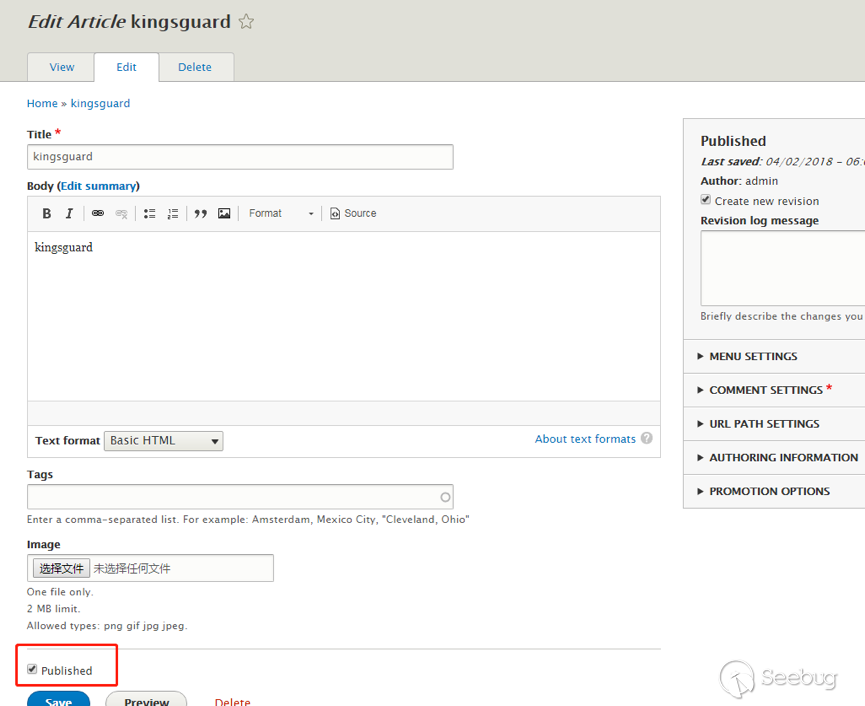 这时候用admin账号回复kingsguard test这条评论: 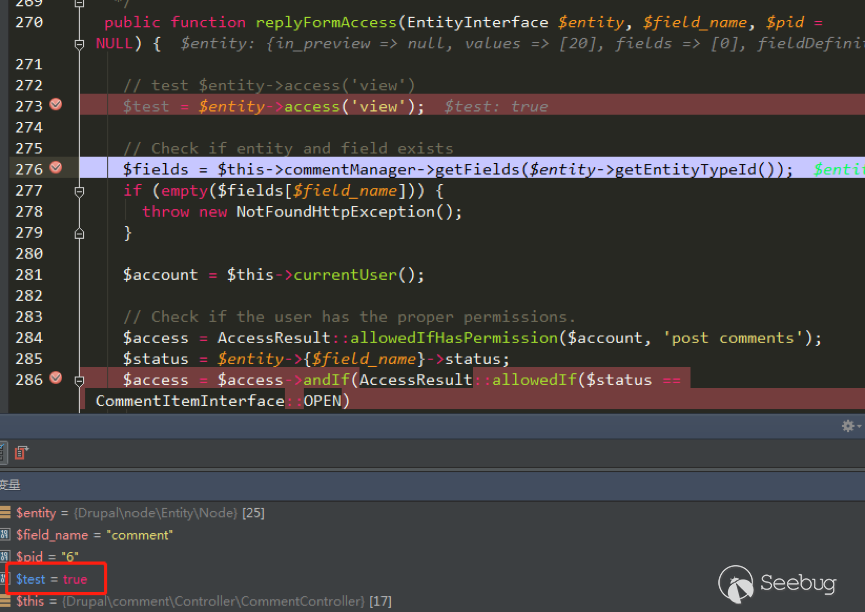 对于admin账号来说,$entity->access(‘view’);仍为true 再用其他账号登录: 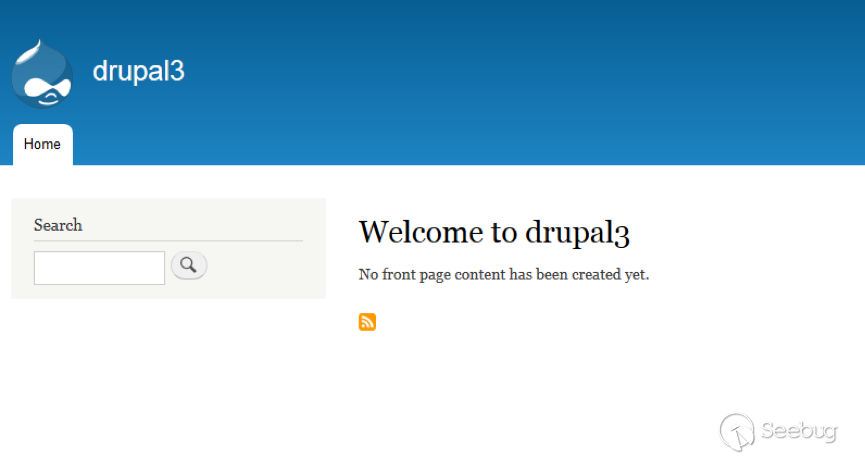 因为admin账号发布的文章都被admin账号设置为不公开了,所以这里看不到任何文章。 继续用这个账号访问: <http://127.0.0.1/d/drupal4/comment/reply/node/2/comment/6></http://127.0.0.1/d/drupal4/comment/reply/node/2/comment/6> 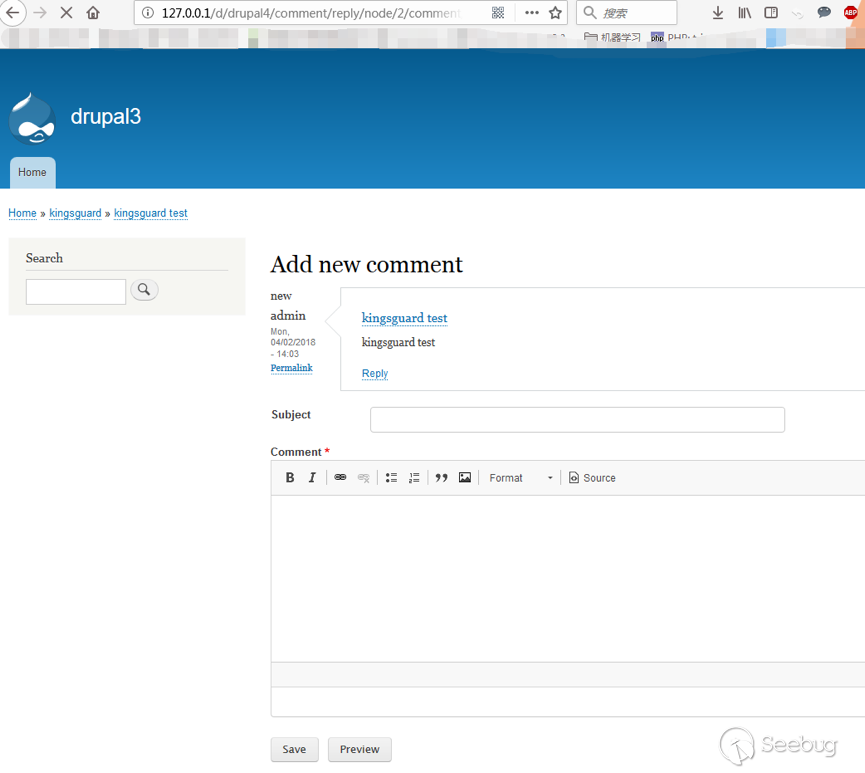 可以看到,虽然文章不公开,仍然可以看到不公开文章的评论,并且还能对评论进行回复。 再看下后台下的断点: 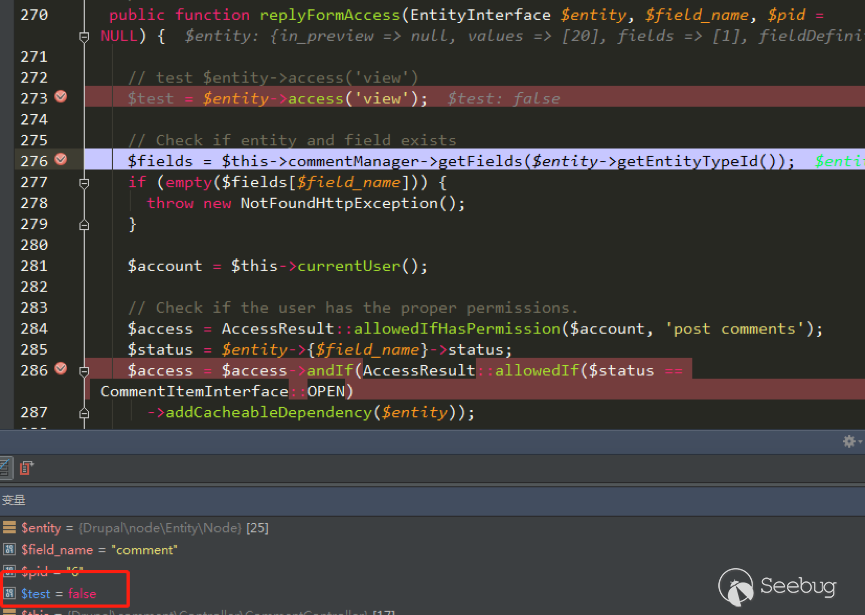 此时的$entity->access(‘view’)变成了false #### 利用验证 假设id为{node_id}的文章被作者设置为不公开,想查看/回复此文章的id为{comment_id}的评论。 访问<http://x.x.x.x/comment/reply/node/{node_id}/comment/{comment_id}></http://x.x.x.x/comment/reply/node/{node_id}/comment/{comment_id}> #### 漏洞修复 升级Drupal至最新版本 |
| id | SSV:97211 |
| last seen | 2018-04-04 |
| modified | 2018-04-03 |
| published | 2018-04-03 |
| reporter | Root |
| title | Drupal 8 – CVE-2017-6926漏洞详解 |