Vulnerabilities > CVE-2017-17411 - OS Command Injection vulnerability in Linksys Wvbr0 Firmware
Attack vector
NETWORK Attack complexity
LOW Privileges required
NONE Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
This vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of Linksys WVBR0. Authentication is not required to exploit this vulnerability. The specific flaw exists within the web management portal. The issue lies in the lack of proper validation of user data before executing a system call. An attacker could leverage this vulnerability to execute code with root privileges. Was ZDI-CAN-4892.
Vulnerable Configurations
| Part | Description | Count |
|---|---|---|
| OS | 1 | |
| Hardware | 1 |
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Command Line Execution through SQL Injection An attacker uses standard SQL injection methods to inject data into the command line for execution. This could be done directly through misuse of directives such as MSSQL_xp_cmdshell or indirectly through injection of data into the database that would be interpreted as shell commands. Sometime later, an unscrupulous backend application (or could be part of the functionality of the same application) fetches the injected data stored in the database and uses this data as command line arguments without performing proper validation. The malicious data escapes that data plane by spawning new commands to be executed on the host.
- Command Delimiters An attack of this type exploits a programs' vulnerabilities that allows an attacker's commands to be concatenated onto a legitimate command with the intent of targeting other resources such as the file system or database. The system that uses a filter or a blacklist input validation, as opposed to whitelist validation is vulnerable to an attacker who predicts delimiters (or combinations of delimiters) not present in the filter or blacklist. As with other injection attacks, the attacker uses the command delimiter payload as an entry point to tunnel through the application and activate additional attacks through SQL queries, shell commands, network scanning, and so on.
- Exploiting Multiple Input Interpretation Layers An attacker supplies the target software with input data that contains sequences of special characters designed to bypass input validation logic. This exploit relies on the target making multiples passes over the input data and processing a "layer" of special characters with each pass. In this manner, the attacker can disguise input that would otherwise be rejected as invalid by concealing it with layers of special/escape characters that are stripped off by subsequent processing steps. The goal is to first discover cases where the input validation layer executes before one or more parsing layers. That is, user input may go through the following logic in an application: In such cases, the attacker will need to provide input that will pass through the input validator, but after passing through parser2, will be converted into something that the input validator was supposed to stop.
- Argument Injection An attacker changes the behavior or state of a targeted application through injecting data or command syntax through the targets use of non-validated and non-filtered arguments of exposed services or methods.
- OS Command Injection In this type of an attack, an adversary injects operating system commands into existing application functions. An application that uses untrusted input to build command strings is vulnerable. An adversary can leverage OS command injection in an application to elevate privileges, execute arbitrary commands and compromise the underlying operating system.
Exploit-Db
description Linksys WVBR0-25 - User-Agent Command Execution (Metasploit). CVE-2017-17411. Remote exploit for Hardware platform. Tags: Metasploit Framework (MSF) file exploits/hardware/remote/43429.rb id EDB-ID:43429 last seen 2018-01-24 modified 2018-01-04 platform hardware port published 2018-01-04 reporter Exploit-DB source https://www.exploit-db.com/download/43429/ title Linksys WVBR0-25 - User-Agent Command Execution (Metasploit) type remote description Linksys WVBR0 - 'User-Agent' Remote Command Injection. CVE-2017-17411. Webapps exploit for Hardware platform file exploits/hardware/webapps/43363.py id EDB-ID:43363 last seen 2017-12-19 modified 2017-12-14 platform hardware port published 2017-12-14 reporter Exploit-DB source https://www.exploit-db.com/download/43363/ title Linksys WVBR0 - 'User-Agent' Remote Command Injection type webapps
Metasploit
| description | The Linksys WVBR0-25 Wireless Video Bridge, used by DirecTV to connect wireless Genie cable boxes to the Genie DVR, is vulnerable to OS command injection in version < 1.0.41 of the web management portal via the User-Agent header. Authentication is not required to exploit this vulnerability. |
| id | MSF:EXPLOIT/LINUX/HTTP/LINKSYS_WVBR0_USER_AGENT_EXEC_NOAUTH |
| last seen | 2020-06-13 |
| modified | 2019-08-15 |
| published | 2017-12-21 |
| references | |
| reporter | Rapid7 |
| source | https://github.com/rapid7/metasploit-framework/blob/master//modules/exploits/linux/http/linksys_wvbr0_user_agent_exec_noauth.rb |
| title | Linksys WVBR0-25 User-Agent Command Execution |
Packetstorm
| data source | https://packetstormsecurity.com/files/download/145640/linksys_wvbr0_user_agent_exec_noauth.rb.txt |
| id | PACKETSTORM:145640 |
| last seen | 2018-01-05 |
| published | 2018-01-04 |
| reporter | HeadlessZeke |
| source | https://packetstormsecurity.com/files/145640/Linksys-WVBR0-25-User-Agent-Command-Execution.html |
| title | Linksys WVBR0-25 User-Agent Command Execution |
Seebug
| bulletinFamily | exploit |
| description | In this guest blog, Trend Micro DVLabs researcher Ricky Lawshae discusses the recently disclosed CVE-2017-17411. He discovered and reported this bug through the ZDI program. Earlier this year, I learned that AT&T was starting to move customers away from its U-Verse service in favor of its DirecTV offerings. As a U-Verse customer, I saw a chance to try out a new service while saving some money at the same time, so I decided to give it a shot. After the installation was over, I found myself with a slew of new devices on my network, all begging for me to come and play with them. Today, the ZDI published an [advisory](http://www.zerodayinitiative.com/advisories/ZDI-17-973/) about a zero-day vulnerability in of those devices. Gather round, my friends, as I relate to you the story of what I found during my investigation. First, a quick demonstration that results in a root shell on the device in question: https://youtu.be/3gUjBnNGLKM ### Getting to Know the Linksys WVBR0-25 As was the case with U-Verse, DirecTV also has wireless cable box options for making installation easier. The [Wireless Genie Mini (C41W)](http://insider.directv.com/2014/04/10/directvs-new-wireless-genie-mini-now-available-nationwide/) cable box pairs with a wireless video bridge to communicate with the main Genie DVR. The wireless video bridge in this case was a Linksys WVBR0-25. I had a bad experience with a wireless video bridge like this in the past, so it seemed like a good place to start looking for problems. I started out by trying to browse to the web server on the device. I expected to find a login page of some sort. What I found instead was a wall of text streaming before my eyes. 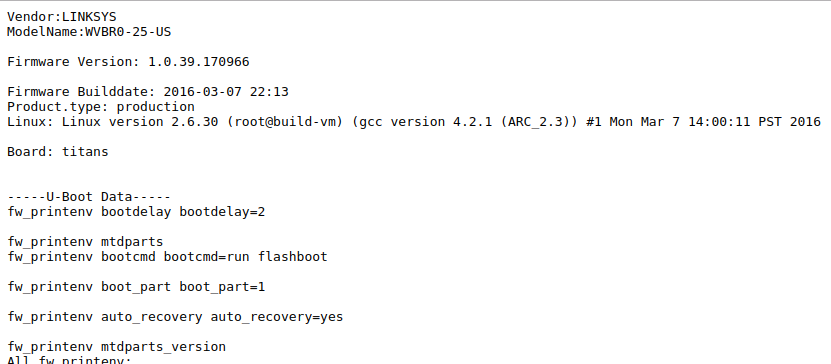 Instead of a login prompt or an index page of any kind, I was presented with the output of several diagnostic scripts containing just about everything you could want to know about the bridge, including the WPS pin, connected clients, running processes, and much more. This by itself is pretty bad as far as information disclosure goes, considering there was no authentication needed to get to this information, but I continued looking through it anyway. About halfway down the page, it started spitting out the contents of log files, and while scanning through those I saw something that made me stop dead in my tracks. With teeth clenching and knuckles turning white, I managed to get out a strained "WHAT...IS...THAT??" before attempting to confirm my suspicion. 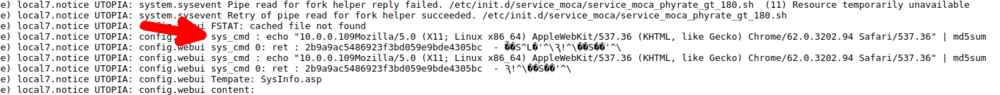 ### The Easiest Command Injection Ever A few lines in this log file, prepended with sys_cmd, seemed to indicate that they were using my IP address and user-agent in a system command to create an MD5 hash. Ostensibly, this is used as some form of access logging or tracking functionality. The logs showed the exact command that was being run and the subsequent output of that command. The problem here, however, is that users have complete control over what they want to send as a user-agent header. I surmised that if the device isn't properly sanitizing the user-agent it is given, it would be sending untrusted data directly to the system for execution. There’s no way that could be the case though, right? 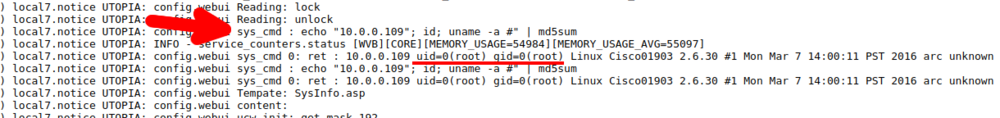 Thanks to the verbose logging on this page I could see that changing my user-agent to "; id; uname -a #" had indeed changed the syntax of the command to be executed. The return value also showed the device had happily executed my new commands and executed them as the root user, too! No login prompt. No input sanitization. Very helpful, verbose output. It literally took 30 seconds of looking at this device to find and verify an unauthenticated remote root command injection vulnerability. It was at this point that I became pretty frustrated. The vendors involved here should have had some form of secure development to prevent bugs like this from shipping. More than that, we as security practitioners have failed to affect the changes needed in the industry to prevent these simple yet impactful bugs from reaching unsuspecting consumers. So, once I finally managed to regain my composure, I decided to buy one of these off eBay to tear apart and figure out exactly what was going on. ### Examining the Firmware The device has an Entropic [ARC](https://en.wikipedia.org/wiki/ARC_(processor)) processor and an [MXIC MX25L12845E](http://www.macronix.com/en-us/products/NOR-Flash/Serial-NOR-Flash/Pages/spec.aspx?p=MX25L12845E) 128Mb serial flash chip for firmware storage. I pulled the flash chip off the board and dumped its contents over the SPI bus by connecting it to my [Bus Pirate](http://dangerousprototypes.com/docs/Bus_Pirate) and running the very useful flashrom program against it. Using binwalk to examine the resulting binary file showed, among other things, a [squashfs](http://www.tldp.org/HOWTO/SquashFS-HOWTO/whatis.html) filesystem that contained all the files I needed to root-cause this vulnerability. 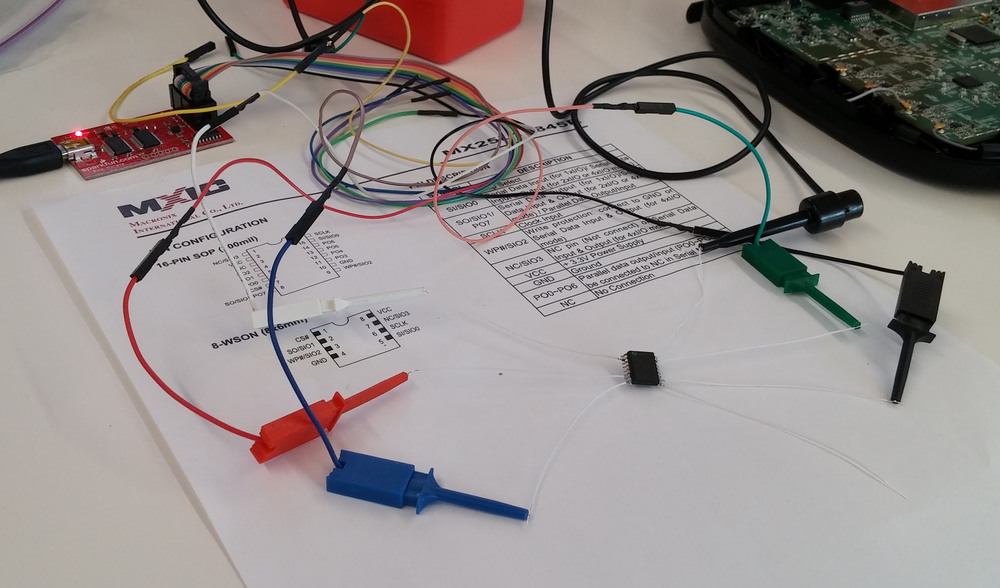 The device was running a lighttpd web server, and as defined in its configuration file, browsing to the root of the web site would result in /dispatcher.cgi?template=SysInfo.asp being rendered. The SysInfo.asp file was the page responsible for displaying all the diagnostic output I was seeing. It also showed dispatcher.cgi was actually a symbolic link to apply.cgi, which itself is a compiled ARC executable file used as kind of a “do everything” agent for the web server. It was in apply.cgi that I found the actual root cause. 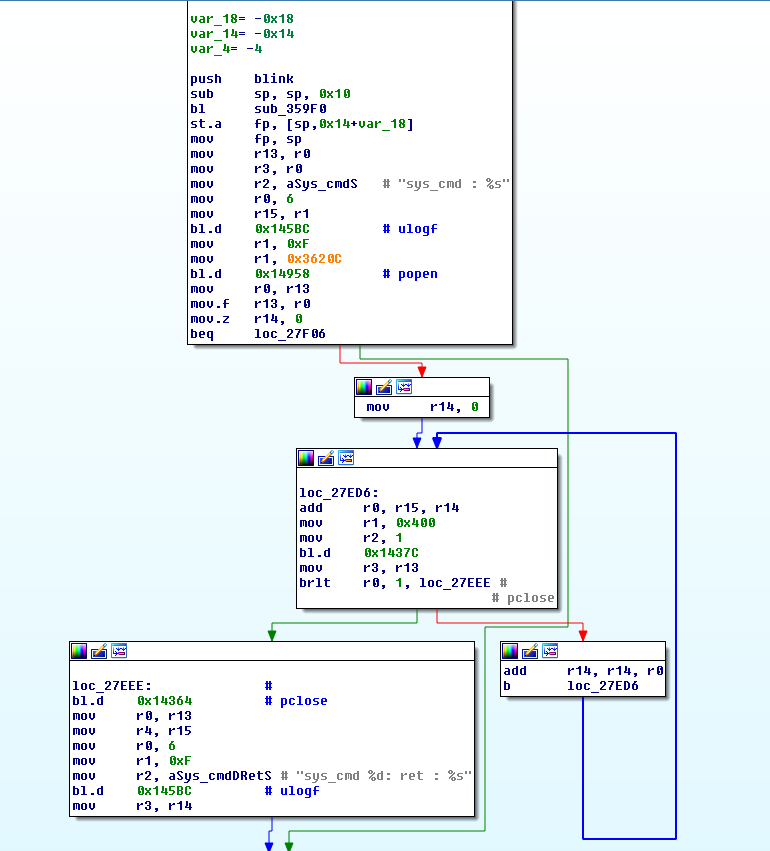 As you can see in the screenshot above, the sys_cmd message is output to the log with the supplied command string using a function called ulogf(). After that, the command is passed without any input sanitization to popen() to execute. Since the lighttpd process is run with root privileges, any commands executed by the popen() call will be run with root privileges as well. A bit later, you can see the exit status and output of the command get logged as well after a subsequent call to pclose(). Using system() or popen() to execute commands from untrusted input is about as textbook as it gets with regard to command injection. The logging just made it that much easier to find and exploit. ### Vulnerability Disclosure After verifying and root-causing the vulnerability, I submitted a bug report to the ZDI program. They attempted to work with Linksys to get it fixed, but unfortunately the vendor ceased being responsive, all deadlines have long since expired, and this bug is now being publicly [disclosed](http://www.zerodayinitiative.com/advisories/ZDI-17-973/). * 06/14/17 - ZDI disclosed the report to the vendor ([email protected]) * 09/14/17 - ZDI sent a follow-up to the vendor requesting a status update * 10/10/17 - ZDI sent a follow-up to the vendor requesting a status update * 11/20/17 - ZDI notified the vendor of the intent to release the 0-day report on 12/12 We have never received any reply. Needless to say, due to the ease of exploitation and the potentially vast install base, disclosure in this manner is less than ideal. However, we have seen devices like this one [used in botnets](https://arstechnica.com/information-technology/2017/12/100000-strong-botnet-built-on-router-0-day-could-strike-at-any-time/) in the past. Consumers and enterprises alike should be made aware of the risks of having these devices on their networks. There’s also the non-zero possibility of someone else finding this vulnerability and incorporating it into exploit kits or malware. In the absence of an actual patch from the vendor, users should protect themselves by limiting the devices that can interact with the WVBR0-25 to those that actually need to reach it. It should also be noted that the DVLabs filter team wrote and shipped filter 29060 back on July 6, 2017, which protects Trend Micro customers from this attack. I hope you enjoyed sharing in my pain as I went on this little adventure! You can find me on Twitter at [HeadlessZeke](https://twitter.com/HeadlessZeke), and follow the [ZDI team](https://twitter.com/thezdi) for the latest in exploit techniques and security patches. |
| id | SSV:96992 |
| last seen | 2018-06-26 |
| modified | 2017-12-15 |
| published | 2017-12-15 |
| reporter | My Seebug |
| source | https://www.seebug.org/vuldb/ssvid-96992 |
| title | Linksys WVBR0 25 Command Injection(CVE-2017-17411) |
References
- http://www.securityfocus.com/bid/102212
- http://www.securityfocus.com/bid/102212
- https://github.com/rapid7/metasploit-framework/pull/9336
- https://github.com/rapid7/metasploit-framework/pull/9336
- https://www.exploit-db.com/exploits/43363/
- https://www.exploit-db.com/exploits/43363/
- https://www.exploit-db.com/exploits/43429/
- https://www.exploit-db.com/exploits/43429/
- https://zerodayinitiative.com/advisories/ZDI-17-973
- https://zerodayinitiative.com/advisories/ZDI-17-973