Vulnerabilities > CVE-2017-0263 - Use After Free vulnerability in Microsoft products
Attack vector
LOCAL Attack complexity
LOW Privileges required
LOW Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
The kernel-mode drivers in Microsoft Windows Server 2008 SP2 and R2 SP1, Windows 7 SP1, Windows 8.1, Windows Server 2012 Gold and R2, Windows RT 8.1, Windows 10 Gold, 1511, 1607, 1703, and Windows Server 2016 allow local users to gain privileges via a crafted application, aka "Win32k Elevation of Privilege Vulnerability."
Vulnerable Configurations
Common Weakness Enumeration (CWE)
Exploit-Db
| description | Microsoft Window Manager (Windows 7 x86) - Menu Management Component UAF Privilege Elevation. CVE-2017-0263. Local exploit for Windows_x86 platform |
| file | exploits/windows_x86/local/44478.cpp |
| id | EDB-ID:44478 |
| last seen | 2018-05-24 |
| modified | 2018-03-26 |
| platform | windows_x86 |
| port | |
| published | 2018-03-26 |
| reporter | Exploit-DB |
| source | https://www.exploit-db.com/download/44478/ |
| title | Microsoft Window Manager (Windows 7 x86) - Menu Management Component UAF Privilege Elevation |
| type | local |
Nessus
NASL family Windows : Microsoft Bulletins NASL id SMB_NT_MS17_MAY_4016871.NASL description The remote Windows 10 version 1703 host is missing security update KB4016871. It is, therefore, affected by multiple vulnerabilities : - A security bypass vulnerability exists in Internet Explorer due to an unspecified flaw. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to bypass mixed content warnings and load insecure content (HTTP) from secure locations (HTTPS). (CVE-2017-0064) - An elevation of privilege vulnerability exists in Windows in the Microsoft DirectX graphics kernel subsystem (dxgkrnl.sys) due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code in an elevated context. (CVE-2017-0077) - An elevation of privilege vulnerability exists in Windows Hyper-V due to improper validation of vSMB packet data. An unauthenticated, adjacent attacker can exploit this to gain elevated privileges. (CVE-2017-0212) - An elevation of privilege vulnerability exists in the Windows COM Aggregate Marshaler due to an unspecified flaw. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code with elevated privileges. (CVE-2017-0213) - An elevation of privilege vulnerability exists in Windows due to improper validation of user-supplied input when loading type libraries. A local attacker can exploit this, via a specially crafted application, to gain elevated privileges. (CVE-2017-0214) - A remote code execution vulnerability exists in Microsoft Internet Explorer due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to execute arbitrary code in the context of the current user. (CVE-2017-0222) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0224) - A remote code execution vulnerability exists in Microsoft Internet Explorer due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to execute arbitrary code in the context of the current user. (CVE-2017-0226) - A remote code execution vulnerability exists in Microsoft Edge in the scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0227) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0228) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0229) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0230) - A spoofing vulnerability exists in Microsoft browsers due to improper rendering of the SmartScreen filter. An unauthenticated, remote attacker can exploit this, via a specially crafted URL, to redirect users to a malicious website that appears to be a legitimate website. (CVE-2017-0231) - An elevation of privilege vulnerability exists in Microsoft Edge due to improper sandboxing. An unauthenticated, remote attacker can exploit this to break out of the Edge AppContainer sandbox and gain elevated privileges. (CVE-2017-0233) - A remote code execution vulnerability exists in Microsoft Edge in the Chakra JavaScript engine due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0234) - A remote code execution vulnerability exists in Microsoft Edge in the Chakra JavaScript engine due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0235) - A remote code execution vulnerability exists in Microsoft Edge in the Chakra JavaScript engine due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0236) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0238) - A remote code execution vulnerability exists in Microsoft Edge in the scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or to open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0240) - An elevation of privilege vulnerability exists in Microsoft Edge due to improper rendering of a domain-less page in the URL. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to cause the user to perform actions in the context of the Intranet Zone and access functionality that is not typically available to the browser when browsing in the context of the Internet Zone. (CVE-2017-0241) - An elevation of privilege vulnerability exists in the win32k component due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code with elevated permissions. Note that an attacker can also cause a denial of service condition on Windows 7 x64 or later systems. (CVE-2017-0246) - A security bypass vulnerability exists in the Microsoft .NET Framework and .NET Core components due to a failure to completely validate certificates. An attacker can exploit this to present a certificate that is marked invalid for a specific use, but the component uses it for that purpose, resulting in a bypass of the Enhanced Key Usage taggings. (CVE-2017-0248) - An information disclosure vulnerability exists in the Windows kernel due to improper initialization of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0258) - An information disclosure vulnerability exists in the Windows kernel due to improper initialization of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0259) - An elevation of privilege vulnerability exists in the Windows kernel-mode driver due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to run arbitrary code in kernel mode. (CVE-2017-0263) - A remote code execution vulnerability exists in the Microsoft scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a crafted web page or open a crafted Office document file, to execute arbitrary code in the context of the current user. (CVE-2017-0266) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0267) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0268) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0269) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0270) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0271) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0272) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0273) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0274) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0275) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0276) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0277) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0278) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0279) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0280) last seen 2020-06-01 modified 2020-06-02 plugin id 100055 published 2017-05-09 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100055 title KB4016871: Windows 10 Version 1703 May 2017 Cumulative Update code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(100055); script_version("1.13"); script_cvs_date("Date: 2019/11/13"); script_cve_id( "CVE-2017-0064", "CVE-2017-0077", "CVE-2017-0212", "CVE-2017-0213", "CVE-2017-0214", "CVE-2017-0222", "CVE-2017-0223", "CVE-2017-0224", "CVE-2017-0226", "CVE-2017-0227", "CVE-2017-0228", "CVE-2017-0229", "CVE-2017-0230", "CVE-2017-0231", "CVE-2017-0233", "CVE-2017-0234", "CVE-2017-0235", "CVE-2017-0236", "CVE-2017-0238", "CVE-2017-0240", "CVE-2017-0241", "CVE-2017-0246", "CVE-2017-0248", "CVE-2017-0258", "CVE-2017-0259", "CVE-2017-0263", "CVE-2017-0266", "CVE-2017-0267", "CVE-2017-0268", "CVE-2017-0269", "CVE-2017-0270", "CVE-2017-0271", "CVE-2017-0272", "CVE-2017-0273", "CVE-2017-0274", "CVE-2017-0275", "CVE-2017-0276", "CVE-2017-0277", "CVE-2017-0278", "CVE-2017-0279", "CVE-2017-0280" ); script_bugtraq_id( 98099, 98102, 98103, 98108, 98112, 98113, 98114, 98117, 98121, 98127, 98139, 98164, 98173, 98179, 98203, 98208, 98214, 98217, 98222, 98229, 98230, 98234, 98237, 98258, 98259, 98260, 98261, 98263, 98264, 98265, 98266, 98267, 98268, 98270, 98271, 98272, 98273, 98274, 98276, 98281, 98452 ); script_xref(name:"MSKB", value:"4016871"); script_xref(name:"MSFT", value:"MS17-4016871"); script_xref(name:"IAVA", value:"2017-A-0148"); script_name(english:"KB4016871: Windows 10 Version 1703 May 2017 Cumulative Update"); script_summary(english:"Checks for rollup."); script_set_attribute(attribute:"synopsis", value: "The remote Windows host is affected by multiple vulnerabilities."); script_set_attribute(attribute:"description", value: "The remote Windows 10 version 1703 host is missing security update KB4016871. It is, therefore, affected by multiple vulnerabilities : - A security bypass vulnerability exists in Internet Explorer due to an unspecified flaw. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to bypass mixed content warnings and load insecure content (HTTP) from secure locations (HTTPS). (CVE-2017-0064) - An elevation of privilege vulnerability exists in Windows in the Microsoft DirectX graphics kernel subsystem (dxgkrnl.sys) due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code in an elevated context. (CVE-2017-0077) - An elevation of privilege vulnerability exists in Windows Hyper-V due to improper validation of vSMB packet data. An unauthenticated, adjacent attacker can exploit this to gain elevated privileges. (CVE-2017-0212) - An elevation of privilege vulnerability exists in the Windows COM Aggregate Marshaler due to an unspecified flaw. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code with elevated privileges. (CVE-2017-0213) - An elevation of privilege vulnerability exists in Windows due to improper validation of user-supplied input when loading type libraries. A local attacker can exploit this, via a specially crafted application, to gain elevated privileges. (CVE-2017-0214) - A remote code execution vulnerability exists in Microsoft Internet Explorer due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to execute arbitrary code in the context of the current user. (CVE-2017-0222) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0224) - A remote code execution vulnerability exists in Microsoft Internet Explorer due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to execute arbitrary code in the context of the current user. (CVE-2017-0226) - A remote code execution vulnerability exists in Microsoft Edge in the scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0227) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0228) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0229) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0230) - A spoofing vulnerability exists in Microsoft browsers due to improper rendering of the SmartScreen filter. An unauthenticated, remote attacker can exploit this, via a specially crafted URL, to redirect users to a malicious website that appears to be a legitimate website. (CVE-2017-0231) - An elevation of privilege vulnerability exists in Microsoft Edge due to improper sandboxing. An unauthenticated, remote attacker can exploit this to break out of the Edge AppContainer sandbox and gain elevated privileges. (CVE-2017-0233) - A remote code execution vulnerability exists in Microsoft Edge in the Chakra JavaScript engine due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0234) - A remote code execution vulnerability exists in Microsoft Edge in the Chakra JavaScript engine due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0235) - A remote code execution vulnerability exists in Microsoft Edge in the Chakra JavaScript engine due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0236) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0238) - A remote code execution vulnerability exists in Microsoft Edge in the scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or to open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0240) - An elevation of privilege vulnerability exists in Microsoft Edge due to improper rendering of a domain-less page in the URL. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to cause the user to perform actions in the context of the Intranet Zone and access functionality that is not typically available to the browser when browsing in the context of the Internet Zone. (CVE-2017-0241) - An elevation of privilege vulnerability exists in the win32k component due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code with elevated permissions. Note that an attacker can also cause a denial of service condition on Windows 7 x64 or later systems. (CVE-2017-0246) - A security bypass vulnerability exists in the Microsoft .NET Framework and .NET Core components due to a failure to completely validate certificates. An attacker can exploit this to present a certificate that is marked invalid for a specific use, but the component uses it for that purpose, resulting in a bypass of the Enhanced Key Usage taggings. (CVE-2017-0248) - An information disclosure vulnerability exists in the Windows kernel due to improper initialization of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0258) - An information disclosure vulnerability exists in the Windows kernel due to improper initialization of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0259) - An elevation of privilege vulnerability exists in the Windows kernel-mode driver due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to run arbitrary code in kernel mode. (CVE-2017-0263) - A remote code execution vulnerability exists in the Microsoft scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a crafted web page or open a crafted Office document file, to execute arbitrary code in the context of the current user. (CVE-2017-0266) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0267) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0268) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0269) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0270) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0271) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0272) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0273) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0274) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0275) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0276) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0277) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0278) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0279) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0280)"); # https://support.microsoft.com/en-us/help/4016871/windows-10-update-kb4016871 script_set_attribute(attribute:"see_also", value:"http://www.nessus.org/u?f546dcfb"); script_set_attribute(attribute:"solution", value: "Apply security update KB4016871."); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2017-0272"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"vuln_publication_date", value:"2017/05/09"); script_set_attribute(attribute:"patch_publication_date", value:"2017/05/09"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/05/09"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"cpe:/o:microsoft:windows"); script_set_attribute(attribute:"stig_severity", value:"I"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"Windows : Microsoft Bulletins"); script_copyright(english:"This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("smb_hotfixes.nasl", "ms_bulletin_checks_possible.nasl", "smb_check_rollup.nasl"); script_require_keys("SMB/MS_Bulletin_Checks/Possible"); script_require_ports(139, 445, "Host/patch_management_checks"); exit(0); } include("audit.inc"); include("smb_hotfixes_fcheck.inc"); include("smb_hotfixes.inc"); include("smb_func.inc"); include("smb_reg_query.inc"); include("misc_func.inc"); get_kb_item_or_exit('SMB/MS_Bulletin_Checks/Possible'); bulletin = 'MS17-05'; kbs = make_list( '4016871' # 10 1703 ); if (get_kb_item('Host/patch_management_checks')) hotfix_check_3rd_party(bulletin:bulletin, kbs:kbs, severity:SECURITY_HOLE); get_kb_item_or_exit("SMB/Registry/Enumerated"); get_kb_item_or_exit('SMB/WindowsVersion', exit_code:1); if (hotfix_check_sp_range(win10:'0') <= 0) audit(AUDIT_OS_SP_NOT_VULN); productname = get_kb_item_or_exit("SMB/ProductName", exit_code:1); if ("2016" >< productname) audit(AUDIT_OS_SP_NOT_VULN); if ( # 10 (1703) smb_check_rollup(os:"10", sp:0, os_build:"15063", rollup_date: "05_2017", bulletin:bulletin, rollup_kb_list:make_list(4016871)) ) { replace_kb_item(name:'SMB/Missing/'+bulletin, value:TRUE); hotfix_security_hole(); hotfix_check_fversion_end(); exit(0); } else { hotfix_check_fversion_end(); audit(AUDIT_HOST_NOT, hotfix_get_audit_report()); }NASL family Windows : Microsoft Bulletins NASL id SMB_NT_MS17_MAY_4019474.NASL description The remote Windows 10 version 1507 host is missing security update KB4019474. It is, therefore, affected by multiple vulnerabilities : - A security bypass vulnerability exists in Internet Explorer due to an unspecified flaw. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to bypass mixed content warnings and load insecure content (HTTP) from secure locations (HTTPS). (CVE-2017-0064) - An elevation of privilege vulnerability exists in Windows in the Microsoft DirectX graphics kernel subsystem (dxgkrnl.sys) due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code in an elevated context. (CVE-2017-0077) - An information disclosure vulnerability exists in the Windows Graphics Device Interface (GDI) due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0190) - An elevation of privilege vulnerability exists in Windows Hyper-V due to improper validation of vSMB packet data. An unauthenticated, adjacent attacker can exploit this to gain elevated privileges. (CVE-2017-0212) - An elevation of privilege vulnerability exists in the Windows COM Aggregate Marshaler due to an unspecified flaw. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code with elevated privileges. (CVE-2017-0213) - An elevation of privilege vulnerability exists in Windows due to improper validation of user-supplied input when loading type libraries. A local attacker can exploit this, via a specially crafted application, to gain elevated privileges. (CVE-2017-0214) - A remote code execution vulnerability exists in Microsoft Internet Explorer due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to execute arbitrary code in the context of the current user. (CVE-2017-0222) - A remote code execution vulnerability exists in Microsoft Internet Explorer due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to execute arbitrary code in the context of the current user. (CVE-2017-0226) - A remote code execution vulnerability exists in Microsoft Edge in the scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0227) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0228) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0229) - A spoofing vulnerability exists in Microsoft browsers due to improper rendering of the SmartScreen filter. An unauthenticated, remote attacker can exploit this, via a specially crafted URL, to redirect users to a malicious website that appears to be a legitimate website. (CVE-2017-0231) - An elevation of privilege vulnerability exists in Microsoft Edge due to improper sandboxing. An unauthenticated, remote attacker can exploit this to break out of the Edge AppContainer sandbox and gain elevated privileges. (CVE-2017-0233) - A remote code execution vulnerability exists in Microsoft Edge in the Chakra JavaScript engine due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0234) - A remote code execution vulnerability exists in Microsoft Edge in the Chakra JavaScript engine due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0236) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0238) - A remote code execution vulnerability exists in Microsoft Edge in the scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or to open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0240) - An elevation of privilege vulnerability exists in Microsoft Edge due to improper rendering of a domain-less page in the URL. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to cause the user to perform actions in the context of the Intranet Zone and access functionality that is not typically available to the browser when browsing in the context of the Internet Zone. (CVE-2017-0241) - An elevation of privilege vulnerability exists in the win32k component due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code with elevated permissions. Note that an attacker can also cause a denial of service condition on Windows 7 x64 or later systems. (CVE-2017-0246) - A security bypass vulnerability exists in the Microsoft .NET Framework and .NET Core components due to a failure to completely validate certificates. An attacker can exploit this to present a certificate that is marked invalid for a specific use, but the component uses it for that purpose, resulting in a bypass of the Enhanced Key Usage taggings. (CVE-2017-0248) - An information disclosure vulnerability exists in the Windows kernel due to improper initialization of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0258) - An information disclosure vulnerability exists in the Windows kernel due to improper initialization of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0259) - An elevation of privilege vulnerability exists in the Windows kernel-mode driver due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to run arbitrary code in kernel mode. (CVE-2017-0263) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0267) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0268) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0269) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0270) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0271) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0272) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0273) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0274) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0275) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0276) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0277) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0278) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0279) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0280) last seen 2020-06-01 modified 2020-06-02 plugin id 100061 published 2017-05-09 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100061 title KB4019474: Windows 10 Version 1507 May 2017 Cumulative Update code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(100061); script_version("1.12"); script_cvs_date("Date: 2019/11/13"); script_cve_id( "CVE-2017-0064", "CVE-2017-0077", "CVE-2017-0190", "CVE-2017-0212", "CVE-2017-0213", "CVE-2017-0214", "CVE-2017-0222", "CVE-2017-0226", "CVE-2017-0227", "CVE-2017-0228", "CVE-2017-0229", "CVE-2017-0231", "CVE-2017-0233", "CVE-2017-0234", "CVE-2017-0236", "CVE-2017-0238", "CVE-2017-0240", "CVE-2017-0241", "CVE-2017-0246", "CVE-2017-0248", "CVE-2017-0258", "CVE-2017-0259", "CVE-2017-0263", "CVE-2017-0267", "CVE-2017-0268", "CVE-2017-0269", "CVE-2017-0270", "CVE-2017-0271", "CVE-2017-0272", "CVE-2017-0273", "CVE-2017-0274", "CVE-2017-0275", "CVE-2017-0276", "CVE-2017-0277", "CVE-2017-0278", "CVE-2017-0279", "CVE-2017-0280" ); script_bugtraq_id( 98099, 98102, 98103, 98108, 98112, 98113, 98114, 98117, 98121, 98127, 98139, 98164, 98173, 98179, 98203, 98208, 98217, 98229, 98234, 98237, 98258, 98259, 98260, 98261, 98263, 98264, 98265, 98266, 98267, 98268, 98270, 98271, 98272, 98273, 98274, 98281, 98298 ); script_xref(name:"MSKB", value:"4019474"); script_xref(name:"MSFT", value:"MS17-4019474"); script_xref(name:"IAVA", value:"2017-A-0148"); script_name(english:"KB4019474: Windows 10 Version 1507 May 2017 Cumulative Update"); script_summary(english:"Checks for rollup."); script_set_attribute(attribute:"synopsis", value: "The remote Windows host is affected by multiple vulnerabilities."); script_set_attribute(attribute:"description", value: "The remote Windows 10 version 1507 host is missing security update KB4019474. It is, therefore, affected by multiple vulnerabilities : - A security bypass vulnerability exists in Internet Explorer due to an unspecified flaw. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to bypass mixed content warnings and load insecure content (HTTP) from secure locations (HTTPS). (CVE-2017-0064) - An elevation of privilege vulnerability exists in Windows in the Microsoft DirectX graphics kernel subsystem (dxgkrnl.sys) due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code in an elevated context. (CVE-2017-0077) - An information disclosure vulnerability exists in the Windows Graphics Device Interface (GDI) due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0190) - An elevation of privilege vulnerability exists in Windows Hyper-V due to improper validation of vSMB packet data. An unauthenticated, adjacent attacker can exploit this to gain elevated privileges. (CVE-2017-0212) - An elevation of privilege vulnerability exists in the Windows COM Aggregate Marshaler due to an unspecified flaw. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code with elevated privileges. (CVE-2017-0213) - An elevation of privilege vulnerability exists in Windows due to improper validation of user-supplied input when loading type libraries. A local attacker can exploit this, via a specially crafted application, to gain elevated privileges. (CVE-2017-0214) - A remote code execution vulnerability exists in Microsoft Internet Explorer due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to execute arbitrary code in the context of the current user. (CVE-2017-0222) - A remote code execution vulnerability exists in Microsoft Internet Explorer due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to execute arbitrary code in the context of the current user. (CVE-2017-0226) - A remote code execution vulnerability exists in Microsoft Edge in the scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0227) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0228) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0229) - A spoofing vulnerability exists in Microsoft browsers due to improper rendering of the SmartScreen filter. An unauthenticated, remote attacker can exploit this, via a specially crafted URL, to redirect users to a malicious website that appears to be a legitimate website. (CVE-2017-0231) - An elevation of privilege vulnerability exists in Microsoft Edge due to improper sandboxing. An unauthenticated, remote attacker can exploit this to break out of the Edge AppContainer sandbox and gain elevated privileges. (CVE-2017-0233) - A remote code execution vulnerability exists in Microsoft Edge in the Chakra JavaScript engine due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0234) - A remote code execution vulnerability exists in Microsoft Edge in the Chakra JavaScript engine due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0236) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0238) - A remote code execution vulnerability exists in Microsoft Edge in the scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or to open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0240) - An elevation of privilege vulnerability exists in Microsoft Edge due to improper rendering of a domain-less page in the URL. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to cause the user to perform actions in the context of the Intranet Zone and access functionality that is not typically available to the browser when browsing in the context of the Internet Zone. (CVE-2017-0241) - An elevation of privilege vulnerability exists in the win32k component due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code with elevated permissions. Note that an attacker can also cause a denial of service condition on Windows 7 x64 or later systems. (CVE-2017-0246) - A security bypass vulnerability exists in the Microsoft .NET Framework and .NET Core components due to a failure to completely validate certificates. An attacker can exploit this to present a certificate that is marked invalid for a specific use, but the component uses it for that purpose, resulting in a bypass of the Enhanced Key Usage taggings. (CVE-2017-0248) - An information disclosure vulnerability exists in the Windows kernel due to improper initialization of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0258) - An information disclosure vulnerability exists in the Windows kernel due to improper initialization of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0259) - An elevation of privilege vulnerability exists in the Windows kernel-mode driver due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to run arbitrary code in kernel mode. (CVE-2017-0263) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0267) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0268) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0269) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0270) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0271) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0272) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0273) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0274) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0275) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0276) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0277) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0278) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0279) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0280)"); # https://support.microsoft.com/en-us/help/4019474/windows-10-update-kb4019474 script_set_attribute(attribute:"see_also", value:"http://www.nessus.org/u?01ec841b"); script_set_attribute(attribute:"solution", value: "Apply security update KB4019474."); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2017-0272"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"vuln_publication_date", value:"2017/05/09"); script_set_attribute(attribute:"patch_publication_date", value:"2017/05/09"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/05/09"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"cpe:/o:microsoft:windows"); script_set_attribute(attribute:"stig_severity", value:"I"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"Windows : Microsoft Bulletins"); script_copyright(english:"This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("smb_check_rollup.nasl", "smb_hotfixes.nasl", "ms_bulletin_checks_possible.nasl"); script_require_keys("SMB/MS_Bulletin_Checks/Possible"); script_require_ports(139, 445, "Host/patch_management_checks"); exit(0); } include("audit.inc"); include("smb_hotfixes_fcheck.inc"); include("smb_hotfixes.inc"); include("smb_func.inc"); include("smb_reg_query.inc"); include("misc_func.inc"); get_kb_item_or_exit('SMB/MS_Bulletin_Checks/Possible'); bulletin = 'MS17-05'; kbs = make_list( '4019474' # 10 1507 ); if (get_kb_item('Host/patch_management_checks')) hotfix_check_3rd_party(bulletin:bulletin, kbs:kbs, severity:SECURITY_HOLE); get_kb_item_or_exit("SMB/Registry/Enumerated"); get_kb_item_or_exit('SMB/WindowsVersion', exit_code:1); if (hotfix_check_sp_range(win10:'0') <= 0) audit(AUDIT_OS_SP_NOT_VULN); productname = get_kb_item_or_exit("SMB/ProductName", exit_code:1); if ("2016" >< productname) audit(AUDIT_OS_SP_NOT_VULN); if ( # 10 (1507) smb_check_rollup(os:"10", sp:0, os_build:"10240", rollup_date: "05_2017", bulletin:bulletin, rollup_kb_list:kbs) ) { replace_kb_item(name:'SMB/Missing/'+bulletin, value:TRUE); hotfix_security_hole(); hotfix_check_fversion_end(); exit(0); } else { hotfix_check_fversion_end(); audit(AUDIT_HOST_NOT, hotfix_get_audit_report()); }NASL family Windows : Microsoft Bulletins NASL id SMB_NT_MS17_MAY_4019215.NASL description The remote Windows host is missing security update 4019213 or cumulative update 4019215. It is, therefore, affected by multiple vulnerabilities : - A security bypass vulnerability exists in Internet Explorer due to an unspecified flaw. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to bypass mixed content warnings and load insecure content (HTTP) from secure locations (HTTPS). (CVE-2017-0064) - An elevation of privilege vulnerability exists in Windows in the Microsoft DirectX graphics kernel subsystem (dxgkrnl.sys) due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code in an elevated context. (CVE-2017-0077) - A denial of service vulnerability exists in the Windows DNS server when it last seen 2020-06-01 modified 2020-06-02 plugin id 100057 published 2017-05-09 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100057 title Windows 8.1 and Windows Server 2012 R2 May 2017 Security Updates code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(100057); script_version("1.14"); script_cvs_date("Date: 2019/11/13"); script_cve_id( "CVE-2017-0064", "CVE-2017-0077", "CVE-2017-0171", "CVE-2017-0190", "CVE-2017-0213", "CVE-2017-0214", "CVE-2017-0222", "CVE-2017-0226", "CVE-2017-0228", "CVE-2017-0231", "CVE-2017-0238", "CVE-2017-0246", "CVE-2017-0248", "CVE-2017-0258", "CVE-2017-0259", "CVE-2017-0263", "CVE-2017-0267", "CVE-2017-0268", "CVE-2017-0269", "CVE-2017-0270", "CVE-2017-0271", "CVE-2017-0272", "CVE-2017-0273", "CVE-2017-0274", "CVE-2017-0275", "CVE-2017-0276", "CVE-2017-0277", "CVE-2017-0278", "CVE-2017-0279", "CVE-2017-0280" ); script_bugtraq_id( 98097, 98102, 98103, 98108, 98112, 98113, 98114, 98117, 98121, 98127, 98139, 98164, 98173, 98237, 98258, 98259, 98260, 98261, 98263, 98264, 98265, 98266, 98267, 98268, 98270, 98271, 98272, 98273, 98274, 98298 ); script_xref(name:"MSKB", value:"4019215"); script_xref(name:"MSFT", value:"MS17-4019215"); script_xref(name:"IAVA", value:"2017-A-0148"); script_xref(name:"MSKB", value:"4019213"); script_xref(name:"MSFT", value:"MS17-4019213"); script_name(english:"Windows 8.1 and Windows Server 2012 R2 May 2017 Security Updates"); script_summary(english:"Checks for rollup."); script_set_attribute(attribute:"synopsis", value: "The remote Windows host is affected by multiple vulnerabilities."); script_set_attribute(attribute:"description", value: "The remote Windows host is missing security update 4019213 or cumulative update 4019215. It is, therefore, affected by multiple vulnerabilities : - A security bypass vulnerability exists in Internet Explorer due to an unspecified flaw. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to bypass mixed content warnings and load insecure content (HTTP) from secure locations (HTTPS). (CVE-2017-0064) - An elevation of privilege vulnerability exists in Windows in the Microsoft DirectX graphics kernel subsystem (dxgkrnl.sys) due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code in an elevated context. (CVE-2017-0077) - A denial of service vulnerability exists in the Windows DNS server when it's configured to answer version queries. An unauthenticated, remote attacker can exploit this, via a malicious DNS query, to cause the DNS server to become nonresponsive. (CVE-2017-0171) - An information disclosure vulnerability exists in the Windows Graphics Device Interface (GDI) due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0190) - An elevation of privilege vulnerability exists in the Windows COM Aggregate Marshaler due to an unspecified flaw. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code with elevated privileges. (CVE-2017-0213) - An elevation of privilege vulnerability exists in Windows due to improper validation of user-supplied input when loading type libraries. A local attacker can exploit this, via a specially crafted application, to gain elevated privileges. (CVE-2017-0214) - A remote code execution vulnerability exists in Microsoft Internet Explorer due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to execute arbitrary code in the context of the current user. (CVE-2017-0222) - A remote code execution vulnerability exists in Microsoft Internet Explorer due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to execute arbitrary code in the context of the current user. (CVE-2017-0226) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0228) - A spoofing vulnerability exists in Microsoft browsers due to improper rendering of the SmartScreen filter. An unauthenticated, remote attacker can exploit this, via a specially crafted URL, to redirect users to a malicious website that appears to be a legitimate website. (CVE-2017-0231) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0238) - An elevation of privilege vulnerability exists in the win32k component due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code with elevated permissions. Note that an attacker can also cause a denial of service condition on Windows 7 x64 or later systems. (CVE-2017-0246) - A security bypass vulnerability exists in the Microsoft .NET Framework and .NET Core components due to a failure to completely validate certificates. An attacker can exploit this to present a certificate that is marked invalid for a specific use, but the component uses it for that purpose, resulting in a bypass of the Enhanced Key Usage taggings. (CVE-2017-0248) - An information disclosure vulnerability exists in the Windows kernel due to improper initialization of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0258) - An information disclosure vulnerability exists in the Windows kernel due to improper initialization of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0259) - An elevation of privilege vulnerability exists in the Windows kernel-mode driver due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to run arbitrary code in kernel mode. (CVE-2017-0263) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0267) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0268) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0269) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0270) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0271) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0272) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0273) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0274) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0275) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0276) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0277) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0278) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0279) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0280)"); # https://support.microsoft.com/en-us/help/4019215/windows-8-update-kb4019215 script_set_attribute(attribute:"see_also", value:"http://www.nessus.org/u?09cc032f"); script_set_attribute(attribute:"solution", value: "Apply Security Only update KB4019213 or Cumulative update KB4019215."); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2017-0272"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"vuln_publication_date", value:"2017/05/09"); script_set_attribute(attribute:"patch_publication_date", value:"2017/05/09"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/05/09"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"cpe:/o:microsoft:windows"); script_set_attribute(attribute:"stig_severity", value:"I"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"Windows : Microsoft Bulletins"); script_copyright(english:"This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("smb_hotfixes.nasl", "ms_bulletin_checks_possible.nasl", "smb_check_rollup.nasl"); script_require_keys("SMB/MS_Bulletin_Checks/Possible"); script_require_ports(139, 445, "Host/patch_management_checks"); exit(0); } include("audit.inc"); include("smb_hotfixes_fcheck.inc"); include("smb_hotfixes.inc"); include("smb_func.inc"); include("smb_reg_query.inc"); include("misc_func.inc"); get_kb_item_or_exit('SMB/MS_Bulletin_Checks/Possible'); bulletin = 'MS17-05'; kbs = make_list( '4019213', # 8.1 / 2012 R2 Security Only '4019215' # 8.1 / 2012 R2 Monthly Rollup ); if (get_kb_item("Host/patch_management_checks")) hotfix_check_3rd_party(bulletin:bulletin, kbs:kbs, severity:SECURITY_HOLE); get_kb_item_or_exit("SMB/Registry/Enumerated"); get_kb_item_or_exit("SMB/WindowsVersion", exit_code:1); if (hotfix_check_sp_range(win81:'0') <= 0) audit(AUDIT_OS_SP_NOT_VULN); # Windows 8 EOL productname = get_kb_item_or_exit("SMB/ProductName", exit_code:1); if ("Windows 8" >< productname && "8.1" >!< productname) audit(AUDIT_OS_SP_NOT_VULN); share = hotfix_get_systemdrive(exit_on_fail:TRUE, as_share:TRUE); if (!is_accessible_share(share:share)) audit(AUDIT_SHARE_FAIL, share); # Windows 8.1 / Windows Server 2012 R2 if ( smb_check_rollup(os:"6.3", sp:0, rollup_date: "05_2017", bulletin:bulletin, rollup_kb_list:[4019213, 4019215]) ) { replace_kb_item(name:'SMB/Missing/'+bulletin, value:TRUE); hotfix_security_hole(); hotfix_check_fversion_end(); exit(0); } else { hotfix_check_fversion_end(); audit(AUDIT_HOST_NOT, hotfix_get_audit_report()); }NASL family Windows : Microsoft Bulletins NASL id SMB_NT_MS17_MAY_WIN2008.NASL description The remote Windows host is missing multiple security updates released on 2017/05/09. It is, therefore, affected by multiple vulnerabilities : - An elevation of privilege vulnerability exists when the Windows improperly handles objects in memory. (CVE-2017-0077) - A denial of service vulnerability exists in Windows DNS Server if the server is configured to answer version queries. An attacker who successfully exploited this vulnerability could cause the DNS Server service to become nonresponsive. (CVE-2017-0171) - An information disclosure vulnerability exists in the way that the Windows Graphics Device Interface+ (GDI+) handles objects in memory, allowing an attacker to retrieve information from a targeted system. (CVE-2017-0190) - An elevation of privilege vulnerability exists in the Windows COM Aggregate Marshaler due to an unspecified flaw. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code with elevated privileges. (CVE-2017-0213) - An elevation of privilege vulnerability exists in Windows due to improper validation of user-supplied input when loading type libraries. A local attacker can exploit this, via a specially crafted application, to gain elevated privileges. (CVE-2017-0214) - An information disclosure vulnerability exists in the Windows kernel due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0175, CVE-2017-0220) - An information disclosure vulnerability exists in the way some ActiveX objects are instantiated. An attacker who successfully exploited this vulnerability could gain access to protected memory contents. (CVE-2017-0242) - An elevation of privilege vulnerability exists in the way that the Windows Kernel handles objects in memory. An attacker who successfully exploited the vulnerability could execute code with elevated permissions. On systems with Windows 7 for x64-based Systems or later installed, this vulnerability can lead to denial of service. (CVE-2017-0244) - An information disclosure vulnerability exists when the win32k component improperly provides kernel information. An attacker who successfully exploited the vulnerability could obtain information to further compromise the users system. (CVE-2017-0245) - An elevation of privilege vulnerability exists when Windows improperly handles objects in memory. An attacker who successfully exploited this vulnerability could run processes in an elevated context. On computers with Windows 7 for x64-based systems or later installed, this vulnerability can lead to denial of service. (CVE-2017-0246) - An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. (CVE-2017-0258) - An elevation of privilege vulnerability exists in Windows when the Windows kernel-mode driver fails to properly handle objects in memory. (CVE-2017-0263) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0267) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0268) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0269) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0270) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0271) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0272) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0273) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0274) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0275) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0276) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0277) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0278) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0279) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0280) - An information disclosure vulnerability exists in the GDI component due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to open a specially crafted document or visit a specially crafted website, to disclose the contents of memory. (CVE-2017-8552) last seen 2020-06-01 modified 2020-06-02 plugin id 100063 published 2017-05-09 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100063 title Windows 2008 May 2017 Multiple Security Updates code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(100063); script_version("1.16"); script_cvs_date("Date: 2019/11/13"); script_cve_id( "CVE-2017-0077", "CVE-2017-0171", "CVE-2017-0175", "CVE-2017-0190", "CVE-2017-0213", "CVE-2017-0214", "CVE-2017-0220", "CVE-2017-0242", "CVE-2017-0244", "CVE-2017-0245", "CVE-2017-0246", "CVE-2017-0258", "CVE-2017-0263", "CVE-2017-0267", "CVE-2017-0268", "CVE-2017-0269", "CVE-2017-0270", "CVE-2017-0271", "CVE-2017-0272", "CVE-2017-0273", "CVE-2017-0274", "CVE-2017-0275", "CVE-2017-0276", "CVE-2017-0277", "CVE-2017-0278", "CVE-2017-0279", "CVE-2017-0280", "CVE-2017-8552" ); script_bugtraq_id( 98097, 98102, 98103, 98108, 98109, 98110, 98111, 98112, 98114, 98115, 98258, 98259, 98260, 98261, 98263, 98264, 98265, 98266, 98267, 98268, 98270, 98271, 98272, 98273, 98274, 98275, 98298 ); script_xref(name:"MSKB", value:"4018196"); script_xref(name:"MSFT", value:"MS17-4018196"); script_xref(name:"IAVA", value:"2017-A-0148"); script_xref(name:"MSKB", value:"4018466"); script_xref(name:"MSFT", value:"MS17-4018466"); script_xref(name:"MSKB", value:"4018556"); script_xref(name:"MSFT", value:"MS17-4018556"); script_xref(name:"MSKB", value:"4018821"); script_xref(name:"MSFT", value:"MS17-4018821"); script_xref(name:"MSKB", value:"4018885"); script_xref(name:"MSFT", value:"MS17-4018885"); script_xref(name:"MSKB", value:"4018927"); script_xref(name:"MSFT", value:"MS17-4018927"); script_xref(name:"MSKB", value:"4019149"); script_xref(name:"MSFT", value:"MS17-4019149"); script_xref(name:"MSKB", value:"4019204"); script_xref(name:"MSFT", value:"MS17-4019204"); script_xref(name:"MSKB", value:"4019206"); script_xref(name:"MSFT", value:"MS17-4019206"); script_name(english:"Windows 2008 May 2017 Multiple Security Updates"); script_summary(english:"Checks the existence of Windows Server 2008 May 2017 Patches."); script_set_attribute(attribute:"synopsis", value: "The remote Windows host is affected by multiple vulnerabilities."); script_set_attribute(attribute:"description", value: "The remote Windows host is missing multiple security updates released on 2017/05/09. It is, therefore, affected by multiple vulnerabilities : - An elevation of privilege vulnerability exists when the Windows improperly handles objects in memory. (CVE-2017-0077) - A denial of service vulnerability exists in Windows DNS Server if the server is configured to answer version queries. An attacker who successfully exploited this vulnerability could cause the DNS Server service to become nonresponsive. (CVE-2017-0171) - An information disclosure vulnerability exists in the way that the Windows Graphics Device Interface+ (GDI+) handles objects in memory, allowing an attacker to retrieve information from a targeted system. (CVE-2017-0190) - An elevation of privilege vulnerability exists in the Windows COM Aggregate Marshaler due to an unspecified flaw. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code with elevated privileges. (CVE-2017-0213) - An elevation of privilege vulnerability exists in Windows due to improper validation of user-supplied input when loading type libraries. A local attacker can exploit this, via a specially crafted application, to gain elevated privileges. (CVE-2017-0214) - An information disclosure vulnerability exists in the Windows kernel due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0175, CVE-2017-0220) - An information disclosure vulnerability exists in the way some ActiveX objects are instantiated. An attacker who successfully exploited this vulnerability could gain access to protected memory contents. (CVE-2017-0242) - An elevation of privilege vulnerability exists in the way that the Windows Kernel handles objects in memory. An attacker who successfully exploited the vulnerability could execute code with elevated permissions. On systems with Windows 7 for x64-based Systems or later installed, this vulnerability can lead to denial of service. (CVE-2017-0244) - An information disclosure vulnerability exists when the win32k component improperly provides kernel information. An attacker who successfully exploited the vulnerability could obtain information to further compromise the users system. (CVE-2017-0245) - An elevation of privilege vulnerability exists when Windows improperly handles objects in memory. An attacker who successfully exploited this vulnerability could run processes in an elevated context. On computers with Windows 7 for x64-based systems or later installed, this vulnerability can lead to denial of service. (CVE-2017-0246) - An information disclosure vulnerability exists when the Windows kernel improperly initializes objects in memory. (CVE-2017-0258) - An elevation of privilege vulnerability exists in Windows when the Windows kernel-mode driver fails to properly handle objects in memory. (CVE-2017-0263) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0267) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0268) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0269) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0270) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0271) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0272) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0273) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0274) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0275) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0276) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0277) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0278) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0279) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0280) - An information disclosure vulnerability exists in the GDI component due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to open a specially crafted document or visit a specially crafted website, to disclose the contents of memory. (CVE-2017-8552)"); script_set_attribute(attribute:"see_also", value:"https://support.microsoft.com/en-us/help/4018196/title"); script_set_attribute(attribute:"see_also", value:"https://support.microsoft.com/en-us/help/4018466/title"); script_set_attribute(attribute:"see_also", value:"https://support.microsoft.com/en-us/help/4018556/title"); script_set_attribute(attribute:"see_also", value:"https://support.microsoft.com/en-us/help/4018821/title"); script_set_attribute(attribute:"see_also", value:"https://support.microsoft.com/en-us/help/4018885/title"); script_set_attribute(attribute:"see_also", value:"https://support.microsoft.com/en-us/help/4018927/title"); script_set_attribute(attribute:"see_also", value:"https://support.microsoft.com/en-us/help/4019149/title"); script_set_attribute(attribute:"see_also", value:"https://support.microsoft.com/en-us/help/4019204/title"); script_set_attribute(attribute:"see_also", value:"https://support.microsoft.com/en-us/help/4019206/title"); script_set_attribute(attribute:"solution", value: "Apply the following security updates : - KB4018196 - KB4018466 - KB4018556 - KB4018821 - KB4018885 - KB4018927 - KB4019149 - KB4019204 - KB4019206"); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2017-0272"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"vuln_publication_date", value:"2017/05/09"); script_set_attribute(attribute:"patch_publication_date", value:"2017/05/09"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/05/09"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"cpe:/o:microsoft:windows"); script_set_attribute(attribute:"stig_severity", value:"I"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"Windows : Microsoft Bulletins"); script_copyright(english:"This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("smb_check_rollup.nasl", "smb_hotfixes.nasl", "ms_bulletin_checks_possible.nasl"); script_require_keys("SMB/MS_Bulletin_Checks/Possible"); script_require_ports(139, 445, "Host/patch_management_checks"); exit(0); } include("audit.inc"); include("smb_func.inc"); include("smb_hotfixes.inc"); include("smb_hotfixes_fcheck.inc"); include("smb_reg_query.inc"); include("misc_func.inc"); get_kb_item_or_exit("SMB/MS_Bulletin_Checks/Possible"); bulletin = 'MS17-05'; kbs = make_list( "4018196", "4018466", "4018556", "4018821", "4018885", "4018927", "4019149", "4019204", "4019206" ); if (get_kb_item("Host/patch_management_checks")) hotfix_check_3rd_party(bulletin:bulletin, kbs:kbs, severity:SECURITY_HOLE); get_kb_item_or_exit("SMB/Registry/Enumerated"); get_kb_item_or_exit("SMB/WindowsVersion", exit_code:1); # KB4018196 Applies only to hosts having 'DNS Server' role installed registry_init(); hklm = registry_hive_connect(hive:HKEY_LOCAL_MACHINE, exit_on_fail:TRUE); dns_role_installed = get_registry_value( handle:hklm, item:"SYSTEM\CurrentControlSet\Services\DNS\DisplayName" ); RegCloseKey(handle:hklm); close_registry(close:TRUE); # KBs only apply to Windows 2008 if (hotfix_check_sp_range(vista:'2') <= 0) audit(AUDIT_OS_SP_NOT_VULN); productname = get_kb_item_or_exit("SMB/ProductName", exit_code:1); if ("Vista" >< productname) audit(AUDIT_OS_SP_NOT_VULN); systemroot = hotfix_get_systemroot(); if (!systemroot) audit(AUDIT_PATH_NOT_DETERMINED, 'system root'); port = kb_smb_transport(); login = kb_smb_login(); pass = kb_smb_password(); domain = kb_smb_domain(); if(! smb_session_init()) audit(AUDIT_FN_FAIL, 'smb_session_init'); winsxs = ereg_replace(pattern:'^[A-Za-z]:(.*)', replace:"\1\WinSxS", string:systemroot); winsxs_share = hotfix_path2share(path:systemroot); rc = NetUseAdd(login:login, password:pass, domain:domain, share:winsxs_share); if (rc != 1) { NetUseDel(); audit(AUDIT_SHARE_FAIL, winsxs_share); } the_session = make_array( 'login', login, 'password', pass, 'domain', domain, 'share', winsxs_share ); vuln = 0; # 4018196 if (!isnull(dns_role_installed)) { files = list_dir(basedir:winsxs, level:0, dir_pat:"dns-server-service_31bf3856ad364e35_", file_pat:"^dns\.exe$", max_recurse:1); vuln += hotfix_check_winsxs(os:'6.0', sp:2, files:files, versions:make_list('6.0.6002.19765','6.0.6002.24089'), max_versions:make_list('6.0.6002.20000','6.0.6002.99999'), bulletin:bulletin, kb:"4018196", session:the_session); } # 4018466 files = list_dir(basedir:winsxs, level:0, dir_pat:"smbserver-common_31bf3856ad364e35_", file_pat:"^srvnet\.sys$", max_recurse:1); vuln += hotfix_check_winsxs(os:'6.0', sp:2, files:files, versions:make_list('6.0.6002.19673','6.0.6002.24089'), max_versions:make_list('6.0.6002.20000','6.0.6002.99999'), bulletin:bulletin, kb:"4018466", session:the_session); # 4018556 files = list_dir(basedir:winsxs, level:0, dir_pat:"com-base-qfe-ole32_31bf3856ad364e35_", file_pat:"^ole32\.dll$", max_recurse:1); vuln += hotfix_check_winsxs(os:'6.0', sp:2, files:files, versions:make_list('6.0.6002.19773','6.0.6002.24089'), max_versions:make_list('6.0.6002.20000','6.0.6002.99999'), bulletin:bulletin, kb:"4018556", session:the_session); # 4018821 files = list_dir(basedir:winsxs, level:0, dir_pat:"tdi-over-tcpip_31bf3856ad364e35_", file_pat:"^tdx\.sys$", max_recurse:1); vuln += hotfix_check_winsxs(os:'6.0', sp:2, files:files, versions:make_list('6.0.6002.19762','6.0.6002.24087'), max_versions:make_list('6.0.6002.20000','6.0.6002.99999'), bulletin:bulletin, kb:"4018821", session:the_session); # 4018885 files = list_dir(basedir:winsxs, level:0, dir_pat:"tcpip-binaries_31bf3856ad364e35_", file_pat:"^tcpip\.sys$", max_recurse:1); vuln += hotfix_check_winsxs(os:'6.0', sp:2, files:files, versions:make_list('6.0.6002.19763','6.0.6002.24087'), max_versions:make_list('6.0.6002.20000','6.0.6002.99999'), bulletin:bulletin, kb:"4018885", session:the_session); # 4018927 files = list_dir(basedir:winsxs, level:0, dir_pat:"rds-datafactory-dll_31bf3856ad364e35_", file_pat:"^msadcf\.dll$", max_recurse:1); vuln += hotfix_check_winsxs(os:'6.0', sp:2, files:files, versions:make_list('6.0.6002.19770','6.0.6002.24089'), max_versions:make_list('6.0.6002.20000','6.0.6002.99999'), bulletin:bulletin, kb:"4018927", session:the_session); # 4019149 files = list_dir(basedir:winsxs, level:0, dir_pat:"lddmcore_31bf3856ad364e35_", file_pat:"^dxgkrnl\.sys$", max_recurse:1); vuln += hotfix_check_winsxs(os:'6.0', sp:2, files:files, versions:make_list('7.0.6002.19765','7.0.6002.24089'), max_versions:make_list('7.0.6002.20000','7.0.6002.99999'), bulletin:bulletin, kb:"4019149", session:the_session); # 4019204 files = list_dir(basedir:winsxs, level:0, dir_pat:"win32k_31bf3856ad364e35_", file_pat:"^win32k\.sys$", max_recurse:1); vuln += hotfix_check_winsxs(os:'6.0', sp:2, files:files, versions:make_list('6.0.6002.19778','6.0.6002.24095'), max_versions:make_list('6.0.6002.20000','6.0.6002.99999'), bulletin:bulletin, kb:"4019204", session:the_session); # 4019206 files = list_dir(basedir:winsxs, level:0, dir_pat:"gdi32_31bf3856ad364e35_", file_pat:"^gdi32\.dll$", max_recurse:1); vuln += hotfix_check_winsxs(os:'6.0', sp:2, files:files, versions:make_list('6.0.6002.19765','6.0.6002.24089'), max_versions:make_list('6.0.6002.20000','6.0.6002.99999'), bulletin:bulletin, kb:"4019206", session:the_session); if (vuln > 0) { replace_kb_item(name:'SMB/Missing/'+bulletin, value:TRUE); hotfix_security_hole(); hotfix_check_fversion_end(); exit(0); } else { hotfix_check_fversion_end(); audit(AUDIT_HOST_NOT, 'affected'); }NASL family Windows : Microsoft Bulletins NASL id SMB_NT_MS17_MAY_4019472.NASL description The remote Windows host is missing security update KB4019472. It is, therefore, affected by multiple vulnerabilities : - A security bypass vulnerability exists in Internet Explorer due to an unspecified flaw. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to bypass mixed content warnings and load insecure content (HTTP) from secure locations (HTTPS). (CVE-2017-0064) - An elevation of privilege vulnerability exists in Windows in the Microsoft DirectX graphics kernel subsystem (dxgkrnl.sys) due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code in an elevated context. (CVE-2017-0077) - A denial of service vulnerability exists in the Windows DNS server when it last seen 2020-06-01 modified 2020-06-02 plugin id 100059 published 2017-05-09 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100059 title KB4019472: Windows 10 Version 1607 and Windows Server 2016 May 2017 Cumulative Update code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(100059); script_version("1.15"); script_cvs_date("Date: 2019/11/13"); script_cve_id( "CVE-2017-0064", "CVE-2017-0077", "CVE-2017-0171", "CVE-2017-0190", "CVE-2017-0212", "CVE-2017-0213", "CVE-2017-0214", "CVE-2017-0221", "CVE-2017-0222", "CVE-2017-0226", "CVE-2017-0227", "CVE-2017-0228", "CVE-2017-0229", "CVE-2017-0230", "CVE-2017-0231", "CVE-2017-0233", "CVE-2017-0234", "CVE-2017-0236", "CVE-2017-0238", "CVE-2017-0240", "CVE-2017-0241", "CVE-2017-0246", "CVE-2017-0248", "CVE-2017-0258", "CVE-2017-0259", "CVE-2017-0263", "CVE-2017-0266", "CVE-2017-0267", "CVE-2017-0268", "CVE-2017-0269", "CVE-2017-0270", "CVE-2017-0271", "CVE-2017-0272", "CVE-2017-0273", "CVE-2017-0274", "CVE-2017-0275", "CVE-2017-0276", "CVE-2017-0277", "CVE-2017-0278", "CVE-2017-0279", "CVE-2017-0280" ); script_bugtraq_id( 98097, 98099, 98102, 98103, 98108, 98112, 98113, 98114, 98117, 98121, 98127, 98139, 98147, 98164, 98173, 98179, 98203, 98208, 98217, 98222, 98229, 98234, 98237, 98258, 98259, 98260, 98261, 98263, 98264, 98265, 98266, 98267, 98268, 98270, 98271, 98272, 98273, 98274, 98276, 98281, 98298 ); script_xref(name:"MSKB", value:"4019472"); script_xref(name:"MSFT", value:"MS17-4019472"); script_xref(name:"IAVA", value:"2017-A-0148"); script_name(english:"KB4019472: Windows 10 Version 1607 and Windows Server 2016 May 2017 Cumulative Update"); script_summary(english:"Checks for presence of the patch rollup."); script_set_attribute(attribute:"synopsis", value: "The remote Windows host is affected by multiple vulnerabilities."); script_set_attribute(attribute:"description", value: "The remote Windows host is missing security update KB4019472. It is, therefore, affected by multiple vulnerabilities : - A security bypass vulnerability exists in Internet Explorer due to an unspecified flaw. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to bypass mixed content warnings and load insecure content (HTTP) from secure locations (HTTPS). (CVE-2017-0064) - An elevation of privilege vulnerability exists in Windows in the Microsoft DirectX graphics kernel subsystem (dxgkrnl.sys) due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code in an elevated context. (CVE-2017-0077) - A denial of service vulnerability exists in the Windows DNS server when it's configured to answer version queries. An unauthenticated, remote attacker can exploit this, via a malicious DNS query, to cause the DNS server to become nonresponsive. (CVE-2017-0171) - An information disclosure vulnerability exists in the Windows Graphics Device Interface (GDI) due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0190) - An elevation of privilege vulnerability exists in Windows Hyper-V due to improper validation of vSMB packet data. An unauthenticated, adjacent attacker can exploit this to gain elevated privileges. (CVE-2017-0212) - An elevation of privilege vulnerability exists in the Windows COM Aggregate Marshaler due to an unspecified flaw. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code with elevated privileges. (CVE-2017-0213) - An elevation of privilege vulnerability exists in Windows due to improper validation of user-supplied input when loading type libraries. A local attacker can exploit this, via a specially crafted application, to gain elevated privileges. (CVE-2017-0214) - A remote code execution vulnerability exists in Microsoft Edge due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to execute arbitrary code in the context of the current user. (CVE-2017-0221) - A remote code execution vulnerability exists in Microsoft Internet Explorer due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to execute arbitrary code in the context of the current user. (CVE-2017-0222) - A remote code execution vulnerability exists in Microsoft Internet Explorer due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to execute arbitrary code in the context of the current user. (CVE-2017-0226) - A remote code execution vulnerability exists in Microsoft Edge in the scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0227) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0228) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0229) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0230) - A spoofing vulnerability exists in Microsoft browsers due to improper rendering of the SmartScreen filter. An unauthenticated, remote attacker can exploit this, via a specially crafted URL, to redirect users to a malicious website that appears to be a legitimate website. (CVE-2017-0231) - An elevation of privilege vulnerability exists in Microsoft Edge due to improper sandboxing. An unauthenticated, remote attacker can exploit this to break out of the Edge AppContainer sandbox and gain elevated privileges. (CVE-2017-0233) - A remote code execution vulnerability exists in Microsoft Edge in the Chakra JavaScript engine due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0234) - A remote code execution vulnerability exists in Microsoft Edge in the Chakra JavaScript engine due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0236) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0238) - A remote code execution vulnerability exists in Microsoft Edge in the scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or to open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0240) - An elevation of privilege vulnerability exists in Microsoft Edge due to improper rendering of a domain-less page in the URL. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to cause the user to perform actions in the context of the Intranet Zone and access functionality that is not typically available to the browser when browsing in the context of the Internet Zone. (CVE-2017-0241) - An elevation of privilege vulnerability exists in the win32k component due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code with elevated permissions. Note that an attacker can also cause a denial of service condition on Windows 7 x64 or later systems. (CVE-2017-0246) - A security bypass vulnerability exists in the Microsoft .NET Framework and .NET Core components due to a failure to completely validate certificates. An attacker can exploit this to present a certificate that is marked invalid for a specific use, but the component uses it for that purpose, resulting in a bypass of the Enhanced Key Usage taggings. (CVE-2017-0248) - An information disclosure vulnerability exists in the Windows kernel due to improper initialization of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0258) - An information disclosure vulnerability exists in the Windows kernel due to improper initialization of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0259) - An elevation of privilege vulnerability exists in the Windows kernel-mode driver due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to run arbitrary code in kernel mode. (CVE-2017-0263) - A remote code execution vulnerability exists in the Microsoft scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a crafted web page or open a crafted Office document file, to execute arbitrary code in the context of the current user. (CVE-2017-0266) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0267) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0268) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0269) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0270) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0271) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0272) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0273) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0274) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0275) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0276) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0277) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0278) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0279) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0280)"); # https://support.microsoft.com/en-us/help/4019472/windows-10-update-kb4019472 script_set_attribute(attribute:"see_also", value:"http://www.nessus.org/u?038b505a"); script_set_attribute(attribute:"solution", value: "Apply security update KB4019472."); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2017-0272"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"vuln_publication_date", value:"2017/05/09"); script_set_attribute(attribute:"patch_publication_date", value:"2017/05/09"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/05/09"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"cpe:/o:microsoft:windows"); script_set_attribute(attribute:"stig_severity", value:"I"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"Windows : Microsoft Bulletins"); script_copyright(english:"This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("smb_check_rollup.nasl", "smb_hotfixes.nasl", "ms_bulletin_checks_possible.nasl"); script_require_keys("SMB/MS_Bulletin_Checks/Possible"); script_require_ports(139, 445, "Host/patch_management_checks"); exit(0); } include("audit.inc"); include("smb_func.inc"); include("smb_hotfixes.inc"); include("smb_hotfixes_fcheck.inc"); include("misc_func.inc"); get_kb_item_or_exit("SMB/MS_Bulletin_Checks/Possible"); ## NB: Microsoft bulletin = 'MS17-05'; kbs = make_list(4019472); get_kb_item_or_exit("SMB/Registry/Enumerated"); get_kb_item_or_exit("SMB/WindowsVersion", exit_code:1); # Update only applies to Window 10 1607 / Server 2016 if (hotfix_check_sp_range(win10:'0') <= 0) audit(AUDIT_OS_SP_NOT_VULN); if (hotfix_check_server_nano() == 1) audit(AUDIT_OS_NOT, "a currently supported OS (Windows Nano Server)"); if (get_kb_item("Host/patch_management_checks")) hotfix_check_3rd_party(bulletin:bulletin, kbs:kbs, severity:SECURITY_HOLE); share = hotfix_get_systemdrive(as_share:TRUE, exit_on_fail:TRUE); if (!is_accessible_share(share:share)) audit(AUDIT_SHARE_FAIL, share); if ( # Windows 10 1607 / Server 2016 smb_check_rollup(os:"10", sp:0, os_build:"14393", rollup_date:"05_2017", bulletin:bulletin, rollup_kb_list:kbs) ) { replace_kb_item(name:"SMB/Missing/"+bulletin, value:TRUE); hotfix_security_hole(); hotfix_check_fversion_end(); exit(0); } else { hotfix_check_fversion_end(); audit(AUDIT_HOST_NOT, hotfix_get_audit_report()); }NASL family Windows : Microsoft Bulletins NASL id SMB_NT_MS17_MAY_4019473.NASL description The remote Windows 10 version 1511 host is missing security update KB4019473. It is, therefore, affected by multiple vulnerabilities : - A security bypass vulnerability exists in Internet Explorer due to an unspecified flaw. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to bypass mixed content warnings and load insecure content (HTTP) from secure locations (HTTPS). (CVE-2017-0064) - An elevation of privilege vulnerability exists in Windows in the Microsoft DirectX graphics kernel subsystem (dxgkrnl.sys) due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code in an elevated context. (CVE-2017-0077) - An information disclosure vulnerability exists in the Windows Graphics Device Interface (GDI) due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0190) - An elevation of privilege vulnerability exists in Windows Hyper-V due to improper validation of vSMB packet data. An unauthenticated, adjacent attacker can exploit this to gain elevated privileges. (CVE-2017-0212) - An elevation of privilege vulnerability exists in the Windows COM Aggregate Marshaler due to an unspecified flaw. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code with elevated privileges. (CVE-2017-0213) - An elevation of privilege vulnerability exists in Windows due to improper validation of user-supplied input when loading type libraries. A local attacker can exploit this, via a specially crafted application, to gain elevated privileges. (CVE-2017-0214) - A remote code execution vulnerability exists in Microsoft Internet Explorer due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to execute arbitrary code in the context of the current user. (CVE-2017-0222) - A remote code execution vulnerability exists in Microsoft Internet Explorer due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to execute arbitrary code in the context of the current user. (CVE-2017-0226) - A remote code execution vulnerability exists in Microsoft Edge in the scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0227) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0228) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0229) - A spoofing vulnerability exists in Microsoft browsers due to improper rendering of the SmartScreen filter. An unauthenticated, remote attacker can exploit this, via a specially crafted URL, to redirect users to a malicious website that appears to be a legitimate website. (CVE-2017-0231) - An elevation of privilege vulnerability exists in Microsoft Edge due to improper sandboxing. An unauthenticated, remote attacker can exploit this to break out of the Edge AppContainer sandbox and gain elevated privileges. (CVE-2017-0233) - A remote code execution vulnerability exists in Microsoft Edge in the Chakra JavaScript engine due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0234) - A remote code execution vulnerability exists in Microsoft Edge in the Chakra JavaScript engine due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0236) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0238) - A remote code execution vulnerability exists in Microsoft Edge in the scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or to open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0240) - An elevation of privilege vulnerability exists in Microsoft Edge due to improper rendering of a domain-less page in the URL. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to cause the user to perform actions in the context of the Intranet Zone and access functionality that is not typically available to the browser when browsing in the context of the Internet Zone. (CVE-2017-0241) - An elevation of privilege vulnerability exists in the win32k component due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code with elevated permissions. Note that an attacker can also cause a denial of service condition on Windows 7 x64 or later systems. (CVE-2017-0246) - A security bypass vulnerability exists in the Microsoft .NET Framework and .NET Core components due to a failure to completely validate certificates. An attacker can exploit this to present a certificate that is marked invalid for a specific use, but the component uses it for that purpose, resulting in a bypass of the Enhanced Key Usage taggings. (CVE-2017-0248) - An information disclosure vulnerability exists in the Windows kernel due to improper initialization of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0258) - An information disclosure vulnerability exists in the Windows kernel due to improper initialization of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0259) - An elevation of privilege vulnerability exists in the Windows kernel-mode driver due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to run arbitrary code in kernel mode. (CVE-2017-0263) - A remote code execution vulnerability exists in the Microsoft scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a crafted web page or open a crafted Office document file, to execute arbitrary code in the context of the current user. (CVE-2017-0266) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0267) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0268) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0269) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0270) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0271) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0272) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0273) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0274) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0275) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0276) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0277) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0278) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0279) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0280) last seen 2020-06-01 modified 2020-06-02 plugin id 100060 published 2017-05-09 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/100060 title KB4019473: Windows 10 Version 1511 May 2017 Cumulative Update code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(100060); script_version("1.12"); script_cvs_date("Date: 2019/11/13"); script_cve_id( "CVE-2017-0064", "CVE-2017-0077", "CVE-2017-0190", "CVE-2017-0212", "CVE-2017-0213", "CVE-2017-0214", "CVE-2017-0222", "CVE-2017-0226", "CVE-2017-0227", "CVE-2017-0228", "CVE-2017-0229", "CVE-2017-0231", "CVE-2017-0233", "CVE-2017-0234", "CVE-2017-0236", "CVE-2017-0238", "CVE-2017-0240", "CVE-2017-0241", "CVE-2017-0246", "CVE-2017-0248", "CVE-2017-0258", "CVE-2017-0259", "CVE-2017-0263", "CVE-2017-0266", "CVE-2017-0267", "CVE-2017-0268", "CVE-2017-0269", "CVE-2017-0270", "CVE-2017-0271", "CVE-2017-0272", "CVE-2017-0273", "CVE-2017-0274", "CVE-2017-0275", "CVE-2017-0276", "CVE-2017-0277", "CVE-2017-0278", "CVE-2017-0279", "CVE-2017-0280" ); script_bugtraq_id( 98099, 98102, 98103, 98108, 98112, 98113, 98114, 98117, 98121, 98127, 98139, 98164, 98173, 98179, 98203, 98208, 98217, 98229, 98234, 98237, 98258, 98259, 98260, 98261, 98263, 98264, 98265, 98266, 98267, 98268, 98270, 98271, 98272, 98273, 98274, 98276, 98281, 98298 ); script_xref(name:"MSKB", value:"4019473"); script_xref(name:"MSFT", value:"MS17-4019473"); script_xref(name:"IAVA", value:"2017-A-0148"); script_name(english:"KB4019473: Windows 10 Version 1511 May 2017 Cumulative Update"); script_summary(english:"Checks for rollup."); script_set_attribute(attribute:"synopsis", value: "The remote Windows host is affected by multiple vulnerabilities."); script_set_attribute(attribute:"description", value: "The remote Windows 10 version 1511 host is missing security update KB4019473. It is, therefore, affected by multiple vulnerabilities : - A security bypass vulnerability exists in Internet Explorer due to an unspecified flaw. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to bypass mixed content warnings and load insecure content (HTTP) from secure locations (HTTPS). (CVE-2017-0064) - An elevation of privilege vulnerability exists in Windows in the Microsoft DirectX graphics kernel subsystem (dxgkrnl.sys) due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code in an elevated context. (CVE-2017-0077) - An information disclosure vulnerability exists in the Windows Graphics Device Interface (GDI) due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0190) - An elevation of privilege vulnerability exists in Windows Hyper-V due to improper validation of vSMB packet data. An unauthenticated, adjacent attacker can exploit this to gain elevated privileges. (CVE-2017-0212) - An elevation of privilege vulnerability exists in the Windows COM Aggregate Marshaler due to an unspecified flaw. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code with elevated privileges. (CVE-2017-0213) - An elevation of privilege vulnerability exists in Windows due to improper validation of user-supplied input when loading type libraries. A local attacker can exploit this, via a specially crafted application, to gain elevated privileges. (CVE-2017-0214) - A remote code execution vulnerability exists in Microsoft Internet Explorer due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to execute arbitrary code in the context of the current user. (CVE-2017-0222) - A remote code execution vulnerability exists in Microsoft Internet Explorer due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to execute arbitrary code in the context of the current user. (CVE-2017-0226) - A remote code execution vulnerability exists in Microsoft Edge in the scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0227) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0228) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0229) - A spoofing vulnerability exists in Microsoft browsers due to improper rendering of the SmartScreen filter. An unauthenticated, remote attacker can exploit this, via a specially crafted URL, to redirect users to a malicious website that appears to be a legitimate website. (CVE-2017-0231) - An elevation of privilege vulnerability exists in Microsoft Edge due to improper sandboxing. An unauthenticated, remote attacker can exploit this to break out of the Edge AppContainer sandbox and gain elevated privileges. (CVE-2017-0233) - A remote code execution vulnerability exists in Microsoft Edge in the Chakra JavaScript engine due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Microsoft Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0234) - A remote code execution vulnerability exists in Microsoft Edge in the Chakra JavaScript engine due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0236) - A remote code execution vulnerability exists in Microsoft browsers in the JavaScript scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0238) - A remote code execution vulnerability exists in Microsoft Edge in the scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website or to open a specially crafted Office document, to execute arbitrary code in the context of the current user. (CVE-2017-0240) - An elevation of privilege vulnerability exists in Microsoft Edge due to improper rendering of a domain-less page in the URL. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted website, to cause the user to perform actions in the context of the Intranet Zone and access functionality that is not typically available to the browser when browsing in the context of the Internet Zone. (CVE-2017-0241) - An elevation of privilege vulnerability exists in the win32k component due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to execute arbitrary code with elevated permissions. Note that an attacker can also cause a denial of service condition on Windows 7 x64 or later systems. (CVE-2017-0246) - A security bypass vulnerability exists in the Microsoft .NET Framework and .NET Core components due to a failure to completely validate certificates. An attacker can exploit this to present a certificate that is marked invalid for a specific use, but the component uses it for that purpose, resulting in a bypass of the Enhanced Key Usage taggings. (CVE-2017-0248) - An information disclosure vulnerability exists in the Windows kernel due to improper initialization of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0258) - An information disclosure vulnerability exists in the Windows kernel due to improper initialization of objects in memory. A local attacker can exploit this, via a specially crafted application, to disclose sensitive information. (CVE-2017-0259) - An elevation of privilege vulnerability exists in the Windows kernel-mode driver due to improper handling of objects in memory. A local attacker can exploit this, via a specially crafted application, to run arbitrary code in kernel mode. (CVE-2017-0263) - A remote code execution vulnerability exists in the Microsoft scripting engines due to improper handling of objects in memory. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a crafted web page or open a crafted Office document file, to execute arbitrary code in the context of the current user. (CVE-2017-0266) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0267) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0268) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0269) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0270) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0271) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0272) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0273) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0274) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0275) - An information disclosure vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to disclose sensitive information. (CVE-2017-0276) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0277) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0278) - A remote code execution vulnerability exists in the Microsoft Server Message Block 1.0 (SMBv1) server when handling certain requests. An unauthenticated, remote attacker can exploit this, via a specially crafted packet, to execute arbitrary code on a target server. (CVE-2017-0279) - A denial of service vulnerability exists in Microsoft Server Message Block (SMB) when handling a specially crafted request to the server. An unauthenticated, remote attacker can exploit this, via a crafted SMB request, to cause the system to stop responding. (CVE-2017-0280)"); # https://support.microsoft.com/en-us/help/4019473/windows-10-update-kb4019473 script_set_attribute(attribute:"see_also", value:"http://www.nessus.org/u?4763dd01"); script_set_attribute(attribute:"solution", value: "Apply security update KB4019473."); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2017-0272"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"vuln_publication_date", value:"2017/05/09"); script_set_attribute(attribute:"patch_publication_date", value:"2017/05/09"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/05/09"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"cpe:/o:microsoft:windows"); script_set_attribute(attribute:"stig_severity", value:"I"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"Windows : Microsoft Bulletins"); script_copyright(english:"This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("smb_hotfixes.nasl", "ms_bulletin_checks_possible.nasl", "smb_check_rollup.nasl"); script_require_keys("SMB/MS_Bulletin_Checks/Possible"); script_require_ports(139, 445, "Host/patch_management_checks"); exit(0); } include("audit.inc"); include("smb_hotfixes_fcheck.inc"); include("smb_hotfixes.inc"); include("smb_func.inc"); include("smb_reg_query.inc"); include("misc_func.inc"); get_kb_item_or_exit('SMB/MS_Bulletin_Checks/Possible'); bulletin = 'MS17-05'; kb = make_list( '4019473' # 10 1151 ); if (get_kb_item('Host/patch_management_checks')) hotfix_check_3rd_party(bulletin:bulletin, kbs:kb, severity:SECURITY_HOLE); get_kb_item_or_exit("SMB/Registry/Enumerated"); get_kb_item_or_exit('SMB/WindowsVersion', exit_code:1); if (hotfix_check_sp_range(win10:'0') <= 0) audit(AUDIT_OS_SP_NOT_VULN); share = hotfix_get_systemdrive(exit_on_fail:TRUE, as_share:TRUE); if (!is_accessible_share(share:share)) audit(AUDIT_SHARE_FAIL, share); if ( # 10 (1511) smb_check_rollup(os:"10", sp:0, os_build:"10586", rollup_date: "05_2017", bulletin:bulletin, rollup_kb_list:make_list(4019473)) ) { replace_kb_item(name:'SMB/Missing/'+bulletin, value:TRUE); hotfix_security_hole(); hotfix_check_fversion_end(); exit(0); } else { hotfix_check_fversion_end(); audit(AUDIT_HOST_NOT, hotfix_get_audit_report()); }
Seebug
| bulletinFamily | exploit |
| description | May has been a busy month for vulnerabilities in the world's most popular desktop operating system. Hackers have made headlines with massive infections by WannaCry ransomware, which exploits an SMB security flaw and the ETERNALBLUE tool. Shortly prior, on May 9, Microsoft fixed CVE-2017-0263, which had made it possible for attackers to gain maximum system privileges on PCs running Windows 10, Windows 8.1, Windows 7, Windows Server 2008, Windows Server 2012, and Windows Server 2016. Vulnerability CVE-2017-0263 had been used already in phishing messages. The emails contained an exploit that first entered the system by taking advantage of incorrect handling of EPS files by Microsoft Office (CVE-2017-0262) and then, once on the inside, leveraged CVE-2017-0263 to get full administrator rights. Two years ago we looked at a similar vulnerability in Windows, and here we will see how the new CVE-2017-0263 opens the way to "pwning" remote workstations and servers. In a word, this is a use-after-free vulnerability (CWE-416)—when context menu windows were closed and the memory occupied by the menu was freed up, the pointer to the freed-up memory was not zeroed out. As a result, the pointer could be reused. The below discussion covers the process of window handling in the win32k.sys driver and how this process makes it possible to exploit the vulnerability. #### Context menus Every Windows user is familiar with context menus. These are the menus that drop down when we right-click.  The appearance of this menu and how it is displayed are completely up to the developer of each application. WinAPI provides developers with the TrackPopupMenuEx function, which causes a context menu to appear with the specified parameters at the specified location on the screen. The state of the context menu is stored in the kernel in the variable win32k!gMenuState, which is a win32k!tagMENUSTATE structure: ``` 0: kd> dt win32k!tagMenuState +0x000 pGlobalPopupMenu : Ptr32 tagPOPUPMENU +0x004 flags : Int4B +0x008 ptMouseLast : tagPOINT +0x010 mnFocus : Int4B +0x014 cmdLast : Int4B +0x018 ptiMenuStateOwner : Ptr32 tagTHREADINFO +0x01c dwLockCount : Uint4B +0x020 pmnsPrev : Ptr32 tagMENUSTATE +0x024 ptButtonDown : tagPOINT +0x02c uButtonDownHitArea: Uint4B +0x030 uButtonDownIndex : Uint4B +0x034 vkButtonDown : Int4B +0x038 uDraggingHitArea : Uint4B +0x03c uDraggingIndex : Uint4B +0x040 uDraggingFlags : Uint4B +0x044 hdcWndAni : Ptr32 HDC__ +0x048 dwAniStartTime : Uint4B +0x04c ixAni : Int4B +0x050 iyAni : Int4B +0x054 cxAni : Int4B +0x058 cyAni : Int4B +0x05c hbmAni : Ptr32 HBITMAP__ +0x060 hdcAni : Ptr32 HDC__ ``` Note that all of the call stacks and structures presented here are taken from Windows 7 x86. The 32-bit OS version is used for convenience: arguments for most functions are stored on the stack and there is no WoW64 layer, which during system calls switches to a 64-bit stack due to which 32-bit stack frames are lost when the call stack is printed. A full list of vulnerable operating systems is given on the Microsoft website. The win32k!tagMENUSTATE structure stores, for example, such information as: the clicked region of the screen, number of the most recent menu command, and pointers to the windows that were clicked or selected for drag-and-drop. The list of context menu windows is stored in the first field, pGlobalPopupMenu, which is of the type win32k!tagPOPUPMENU: ``` 0: kd> dt win32k!tagPopupMenu +0x000 flags : Int4B +0x004 spwndNotify : Ptr32 tagWND +0x008 spwndPopupMenu : Ptr32 tagWND +0x00c spwndNextPopup : Ptr32 tagWND +0x010 spwndPrevPopup : Ptr32 tagWND +0x014 spmenu : Ptr32 tagMENU +0x018 spmenuAlternate : Ptr32 tagMENU +0x01c spwndActivePopup : Ptr32 tagWND +0x020 ppopupmenuRoot : Ptr32 tagPOPUPMENU +0x024 ppmDelayedFree : Ptr32 tagPOPUPMENU +0x028 posSelectedItem : Uint4B +0x02c posDropped : Uint4B +0x030 ppmlockFree : Ptr32 tagPOPUPMENU ``` In both structures we have highlighted the fields of interest, which will be used below to describe the exploitation process. The variable win32k!gMenuState is initialized when a context menu is created, during the previously mentioned TrackPopupMenuEx function. Initialization occurs when win32k!xxxMNAllocMenuState is called: ``` 1: kd> k # ChildEBP RetAddr 00 95f29b38 81fe3ca6 win32k!xxxMNAllocMenuState+0x7c 01 95f29ba0 81fe410f win32k!xxxTrackPopupMenuEx+0x27f 02 95f29c14 82892db6 win32k!NtUserTrackPopupMenuEx+0xc3 03 95f29c14 77666c74 nt!KiSystemServicePostCall 04 0131fd58 7758480e ntdll!KiFastSystemCallRet 05 0131fd5c 100015b3 user32!NtUserTrackPopupMenuEx+0xc 06 0131fd84 7756c4b7 q_Main_Window_Class_wndproc (call TrackPopupMenuEx) ``` And when the context menu is no longer needed—for example, the user selected a menu item or clicked outside of the menu—the function win32k!xxxMNEndMenuState is called and frees up the state of the menu: ``` 1: kd> k # ChildEBP RetAddr 00 a0fb7ab0 82014f68 win32k!xxxMNEndMenuState 01 a0fb7b20 81fe39f5 win32k!xxxRealMenuWindowProc+0xd46 02 a0fb7b54 81f5c134 win32k!xxxMenuWindowProc+0xfd 03 a0fb7b94 81f1bb74 win32k!xxxSendMessageTimeout+0x1ac 04 a0fb7bbc 81f289c8 win32k!xxxWrapSendMessage+0x1c 05 a0fb7bd8 81f5e149 win32k!NtUserfnNCDESTROY+0x27 06 a0fb7c10 82892db6 win32k!NtUserMessageCall+0xcf 07 a0fb7c10 77666c74 nt!KiSystemServicePostCall 08 013cfd90 77564f21 ntdll!KiFastSystemCallRet 09 013cfd94 77560908 user32!NtUserMessageCall+0xc 0a 013cfdd0 77565552 user32!SendMessageWorker+0x546 0b 013cfdf0 100014e4 user32!SendMessageW+0x7c 0c 013cfe08 775630bc q_win_event_hook (call SendMessageW(MN_DODRAGDROP)) ``` Important here is that the gMenuState.pGlobalPopupMenu field is updated only during initialization in the xxxMNAllocMenuState function—it is not zeroed out when the structure is destroyed. #### xxxMNEndMenuState function This function is the star of our story. Its handful of lines harbor the vulnerability. 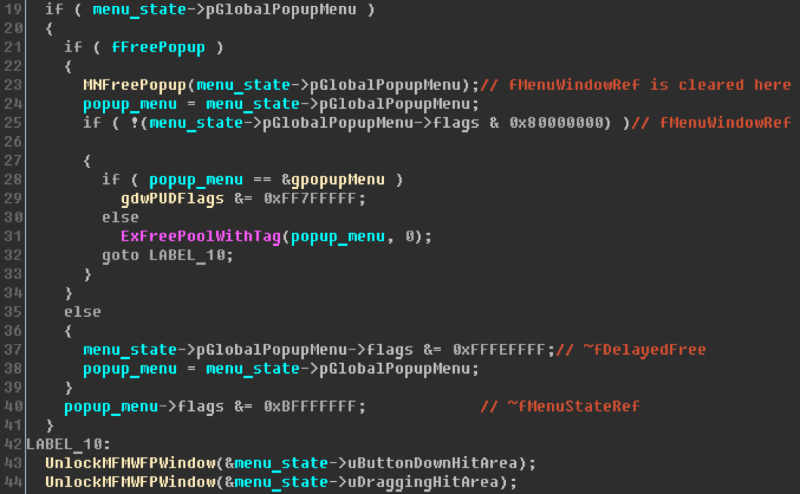 xxxMNEndMenuState starts with deinitialization and freeing of information related to the context menu. The MNFreePopup function—to which we will return in the following section—is called. The main task of MNFreePopup is to decrement reference counters for windows related to the particular context menu. When the reference count falls to zero, this decrementing can cause the window to be destroyed. Then the xxxMNEndMenuState function checks the fMenuWindowRef flag of the pGlobalPopupMenu field to see if any references remain to the main window of the context menu. This flag is cleared upon destruction of the window contained in the spwndPopupMenu field of the context menu: ``` 3: kd> k # ChildEBP RetAddr 00 95fffa5c 81f287da win32k!xxxFreeWindow+0x847 01 95fffab0 81f71252 win32k!xxxDestroyWindow+0x532 02 95fffabc 81f7122c win32k!HMDestroyUnlockedObject+0x1b 03 95fffac8 81f70c4a win32k!HMUnlockObjectInternal+0x30 04 95fffad4 81f6e1fc win32k!HMUnlockObject+0x13 05 95fffadc 81fea664 win32k!HMAssignmentUnlock+0xf 06 95fffaec 81fea885 win32k!MNFreePopup+0x7d 07 95fffb14 8202c3d6 win32k!xxxMNEndMenuState+0x40 xxxFreeWindow+83f disasm: .text:BF89082E loc_BF89082E: .text:BF89082E and ecx, 7FFFFFFFh ; ~fMenuWindowRef .text:BF890834 mov [eax+tagPOPUPMENU.flags], ecx ``` As seen above, the flag is discarded and therefore the memory occupied by the pGlobalPopupMenu field is freed up, but the pointer itself is not zeroed out. This causes a dangling pointer, which under certain circumstances can be reused. Immediately after the context menu memory is freed up, the execution flow deletes the references stored in the context menu state structure that relate to clicked windows (uButtonDownHitArea field) when the menu was active or were selected for drag-and-drop (uDraggingHitArea field). #### Exploitation method A window object in the kernel is described by a tagWND structure. There we describe the concept of kernel callbacks, which will be needed here as well. The number of active references to a window is stored in the cLockObj field of the tagWND structure. Deleting references to a window, as shown in the previous section, can cause the window itself to be destroyed. Before the window is destroyed, a WM_NCDESTROY change-of-window-state message is sent to the window. This means that while xxxMNEndMenuState is running, control can be transferred to user application code—specifically, to the window procedure of the window being destroyed. This happens when no references remain to a window whose pointer is stored in the gMenuState.uButtonDownHitArea field. ``` 2: kd> k # ChildEBP RetAddr 0138fc34 7756c4b7 q_new_SysShadow_window_proc 0138fc60 77565f6f USER32!InternalCallWinProc+0x23 0138fcd8 77564ede USER32!UserCallWinProcCheckWow+0xe0 0138fd34 7755b28f USER32!DispatchClientMessage+0xcf 0138fd64 77666bae USER32!__fnNCDESTROY+0x26 0138fd90 77564f21 ntdll!KiUserCallbackDispatcher+0x2e 95fe38f8 81f56d86 nt!KeUserModeCallback 95fe3940 81f5c157 win32k!xxxSendMessageToClient+0x175 95fe398c 81f5c206 win32k!xxxSendMessageTimeout+0x1cf 95fe39b4 81f2839c win32k!xxxSendMessage+0x28 95fe3a10 81f2fb00 win32k!xxxDestroyWindow+0xf4 95fe3a24 81f302ee win32k!xxxRemoveShadow+0x3e 95fe3a64 81f287da win32k!xxxFreeWindow+0x2ff 95fe3ab8 81f71252 win32k!xxxDestroyWindow+0x532 95fe3ac4 81f7122c win32k!HMDestroyUnlockedObject+0x1b 95fe3ad0 81f70c4a win32k!HMUnlockObjectInternal+0x30 95fe3adc 81f6e1fc win32k!HMUnlockObject+0x13 95fe3ae4 81fe4162 win32k!HMAssignmentUnlock+0xf 95fe3aec 81fea8c3 win32k!UnlockMFMWFPWindow+0x18 95fe3b14 8202c3d6 win32k!xxxMNEndMenuState+0x7e ``` For example, in the call stack shown above, the WM_NCDESTROY message is handled by the window procedure for the SysShadow window class. Windows of this class are designed to provide shadowing and are usually destroyed together with the windows for which they are shadowing. Now let's see the most interesting part of how this window message is handled, in the form that was found in the malware sample taken from a .docx phishing attachment: 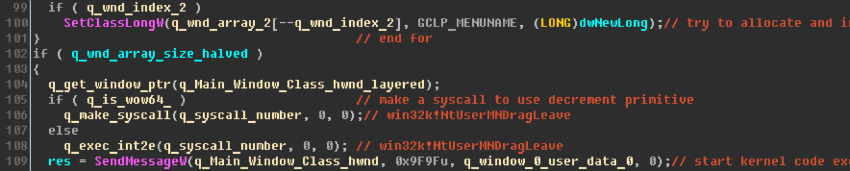 When the attacker takes control, the first matter of business is to occupy the now-free memory that was just occupied by gMenuState.pGlobalPopupMenu, in order to reuse this pointer later. Attempting to allocate the indicated memory block, the exploit performs a large number of SetClassLongW calls, thus setting a specially formed menu name for window classes that have been specially created for this purpose: ``` 2: kd> k # ChildEBP RetAddr 00 9f74bafc 81f240d2 win32k!memcpy+0x33 01 9f74bb3c 81edadb1 win32k!AllocateUnicodeString+0x6b 02 9f74bb9c 81edb146 win32k!xxxSetClassData+0x1d1 03 9f74bbb8 81edb088 win32k!xxxSetClassLong+0x39 04 9f74bc1c 82892db6 win32k!NtUserSetClassLong+0xc8 05 9f74bc1c 77666c74 nt!KiSystemServicePostCall 06 0136fac0 7755658b ntdll!KiFastSystemCallRet 07 0136fac4 775565bf user32!NtUserSetClassLong+0xc 08 0136fafc 10001a52 user32!SetClassLongW+0x5e 09 0136fc34 7756c4b7 q_new_SysShadow_window_proc (call SetClassLongW) ``` After the memory is occupied, the next stage begins. The exploit accesses the NtUserMNDragLeave system procedure, which performs a nested call of the xxxMNEndMenuState function. Clearing of the gMenuState structure starts again: ``` 2: kd> k # ChildEBP RetAddr 00 9f74bbf0 8202c3d6 win32k!xxxMNEndMenuState 01 9f74bc04 8202c40e win32k!xxxUnlockMenuStateInternal+0x2e 02 9f74bc14 82015672 win32k!xxxUnlockAndEndMenuState+0xf 03 9f74bc24 82001728 win32k!xxxMNDragLeave+0x45 04 9f74bc2c 82892db6 win32k!NtUserMNDragLeave+0xd 05 9f74bc2c 100010a9 nt!KiSystemServicePostCall 06 0136fafc 10001a84 q_exec_int2e (int 2Eh) 07 0136fc34 7756c4b7 q_new_SysShadow_window_proc (call q_exec_int2e) ``` As described in the previous section, the procedure starts by deinitializing the pGlobalPopupMenu field; this process is performed by the MNFreePopup call, which decrements the reference counters for windows contained in various fields of tagPOPUPMENU. After the prior step, the content of this structure is now controlled by the attacker. So when the described chain of actions is performed, the attacker gets a decrement primitive to an arbitrary kernel address. In this exploit, an address is inserted in the tagPOPUPMENU.spwndPrevPopup field and the primitive is used to decrement the field for flags of one of the windows, causing that window to be marked with the flag bServerSideProc, which means that its window procedure is run in the kernel. As the code shows, immediately after returning from NtUserMNDragLeave, a message is sent to the window by a SendMessage call, causing arbitrary kernel code execution. At this stage, the attacker usually steals a system process token to obtain system privileges. Indeed, this is what happened in the exploit here. #### In conclusion What are the salient points of the exploit? The most common cause of vulnerabilities in the win32k.sys library is access to callbacks in user space when any kernel structures are in an intermediate stage when a transaction is changing them. Setting the bServerSideProc flag for a window is also a popular method for kernel code execution. In addition, the most convenient method to leverage kernel code execution for privilege escalation is to copy a reference to a system token. In that sense, the exploit looks rather mundane. At the same time many of the nuances have been simplified or purposefully omitted from this discussion. For example, we did not dwell on the exact appearance of the context menu or menu-related actions that cause the necessary state of the flags and fields of the win32k!gMenuState variable during execution of the xxxMNEndMenuState procedure. Left unmentioned was the fact that the menu names set during SetClassLong calls should, on the one hand, be a Unicode string with no null characters but, on the other hand, be a legitimate tagPOPUPMENU structure. This also means that the address of the window in the kernel (to which the decrement field will refer) must not contain any wchar_t null characters. These are just a few examples from a rather long list. As for the update that fixes the vulnerability, a quick glance shows that the buffer addressed by the gMenuState.pGlobalPopupMenu field is now freed closer to the end of the xxxMNEndMenuState function, much later after the MNFreePopup and UnlockMFMWPWindow calls, and is accompanied by zeroing-out of the pointer. Thus the patch addresses two causes whose simultaneous presence caused the vulnerability to occur. |
| id | SSV:93116 |
| last seen | 2017-11-19 |
| modified | 2017-05-19 |
| published | 2017-05-19 |
| reporter | Root |
| title | Win32k Elevation of Privilege Vulnerability(CVE-2017-0263) |
The Hacker News
| id | THN:35CDED923C2A70050CA53879EA860398 |
| last seen | 2018-01-27 |
| modified | 2017-05-10 |
| published | 2017-05-09 |
| reporter | Swati Khandelwal |
| source | https://thehackernews.com/2017/05/patch-windows-zero-days.html |
| title | Microsoft Issues Patches for Another Four Zero-Day Vulnerabilities |
References
- http://www.securityfocus.com/bid/98258
- http://www.securityfocus.com/bid/98258
- http://www.securitytracker.com/id/1038449
- http://www.securitytracker.com/id/1038449
- https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-0263
- https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-0263
- https://www.exploit-db.com/exploits/44478/
- https://www.exploit-db.com/exploits/44478/
- https://xiaodaozhi.com/exploit/117.html
- https://xiaodaozhi.com/exploit/117.html