Vulnerabilities > CVE-2017-0016 - NULL Pointer Dereference vulnerability in Microsoft products
Attack vector
NETWORK Attack complexity
HIGH Privileges required
NONE Confidentiality impact
NONE Integrity impact
NONE Availability impact
HIGH Summary
Microsoft Windows 10 Gold, 1511, and 1607; Windows 8.1; Windows RT 8.1; Windows Server 2012 R2, and Windows Server 2016 do not properly handle certain requests in SMBv2 and SMBv3 packets, which allows remote attackers to execute arbitrary code via a crafted SMBv2 or SMBv3 packet to the Server service, aka "SMBv2/SMBv3 Null Dereference Denial of Service Vulnerability."
Vulnerable Configurations
| Part | Description | Count |
|---|---|---|
| OS | 7 |
Common Weakness Enumeration (CWE)
Nessus
| NASL family | Windows : Microsoft Bulletins |
| NASL id | SMB_NT_MS17-012.NASL |
| description | The remote Windows host is missing a security update. It is, therefore, affected by multiple vulnerabilities : - A security feature bypass vulnerability exists in Device Guard due to improper validation of certain elements in a signed PowerShell script. An unauthenticated, remote attacker can exploit this vulnerability to modify the contents of a PowerShell script without invalidating the signature associated with the file, allowing the execution of a malicious script. (CVE-2017-0007) - A denial of service vulnerability exists in the Microsoft Server Message Block 2.0 and 3.0 (SMBv2/SMBv3) client implementations due to improper handling of certain requests sent to the client. An unauthenticated, remote attacker can exploit this issue, via a malicious SMB server, to cause the system to stop responding until it is manually restarted. (CVE-2017-0016) - A remote code execution vulnerability exists due to using an insecure path to load certain dynamic link library (DLL) files. A local attacker can exploit this, via a specially crafted library placed in the path, to execute arbitrary code. (CVE-2017-0039) - An information disclosure vulnerability exists in Windows dnsclient due to improper handling of certain requests. An unauthenticated, remote attacker can exploit this, by convincing a user to visit a specially crafted web page, to gain access to sensitive information on a targeted workstation. If the target is a server, the attacker can also exploit this issue by tricking the server into sending a DNS query to a malicious DNS server. (CVE-2017-0057) - An elevation of privilege vulnerability exists in Helppane.exe due to a failure by an unspecified DCOM object, configured to run as the interactive user, to properly authenticate the client. An authenticated, remote attacker can exploit this, via a specially crafted application, to execute arbitrary code in another user |
| last seen | 2020-06-01 |
| modified | 2020-06-02 |
| plugin id | 97743 |
| published | 2017-03-15 |
| reporter | This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. |
| source | https://www.tenable.com/plugins/nessus/97743 |
| title | MS17-012: Security Update for Microsoft Windows (4013078) |
Seebug
| bulletinFamily | exploit |
| description | ### 1 vulnerability profile: SMB is a network file sharing Protocol that allows applications and end-user from a remote file server to access file resources. Just recently, foreign researchers published a SMB 3.0 Protocol 0day vulnerabilities, can cause the system to denial-of-service, there is no more detailed vulnerability details disclosed. ### 2 vulnerability: The attacker can convince a user to visit bogus SMB Server, thereby performing a denial of service attack, the ultimate harm to the user of the system. ### 3 effect version: Windows Server 2012 Windows Server 2016 Windows 10 other versions may also be affected. ### 4 environment to build PoC to run the server:Ubuntu 16.04 x64 Test client:Windows 10 x64 PoC as follows: https://www.exploit-db.com/exploits/41222/ ### 5 vulnerability reproduction In Ubuntu under the implementation of the PoC script to simulate the SMB of the service end and wait for the client connection: 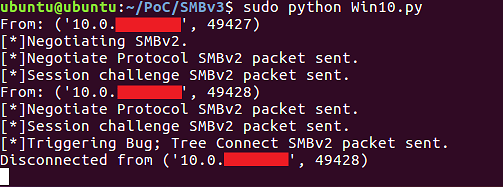 In client Windows 10 to access the SMB service end: 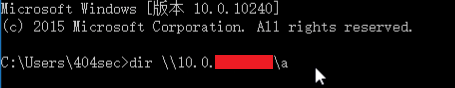 Will eventually trigger the vulnerability to cause the system to crash:  Vulnerability details and analysis: http://paper.seebug.org/215/ |
| id | SSV:92651 |
| last seen | 2017-11-19 |
| modified | 2017-02-03 |
| published | 2017-02-03 |
| reporter | Root |
| source | https://www.seebug.org/vuldb/ssvid-92651 |
| title | Microsoft Windows SMBv3 denial of service vulnerability (CVE-2017-0016) |
References
- http://www.securityfocus.com/bid/95969
- http://www.securityfocus.com/bid/95969
- http://www.securitytracker.com/id/1037767
- http://www.securitytracker.com/id/1037767
- http://www.securitytracker.com/id/1038001
- http://www.securitytracker.com/id/1038001
- https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-0016
- https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-0016