Vulnerabilities > CVE-2017-0002 - Unspecified vulnerability in Microsoft Edge
Attack vector
NETWORK Attack complexity
LOW Privileges required
NONE Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
Microsoft Edge allows remote attackers to bypass the Same Origin Policy via vectors involving the about:blank URL and data: URLs, aka "Microsoft Edge Elevation of Privilege Vulnerability."
Vulnerable Configurations
| Part | Description | Count |
|---|---|---|
| Application | 1 |
Msbulletin
| bulletin_id | MS17-001 |
| bulletin_url | |
| date | 2017-01-10T00:00:00 |
| impact | Elevation of Privilege |
| knowledgebase_id | 3214288 |
| knowledgebase_url | |
| severity | Important |
| title | Security Update for Microsoft Edge |
Nessus
| NASL family | Windows : Microsoft Bulletins |
| NASL id | SMB_NT_MS17-001.NASL |
| description | The version of Microsoft Edge installed on the remote Windows host is missing Cumulative Security Update 3214288. It is, therefore, affected by a privilege escalation vulnerability due to improper enforcement of cross-domain policies with |
| last seen | 2020-06-01 |
| modified | 2020-06-02 |
| plugin id | 96390 |
| published | 2017-01-10 |
| reporter | This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. |
| source | https://www.tenable.com/plugins/nessus/96390 |
| title | MS17-001: Security Update for Microsoft Edge (3214288) |
| code | |
Seebug
| bulletinFamily | exploit |
| description | Original link: [UXSS on Microsoft Edge – Adventures in a Domainless World without domain big World Adventure](<https://www.brokenbrowser.com/uxss-edge-domainless-world/>) Original author: [Manuel Caballero](<https://twitter.com/magicmac2000>) Translation: **Holic (know Chong Yu 404 security lab)** Note: the associated file can be [downloaded here ](<http://paper.seebug.org/papers/Archive/EdgeUXXDomainless.zip>)in. Today, we discuss the design of problems, with these problems, we end up in a Microsoft Edge on the browser to achieve a universal cross-site scripting attacks UXSS in. If you're not a security researcher, but still want to understand this vulnerability, you can be understood: visiting a malicious webpage, the attacker can read your Cookies, change the client's web content, to obtain personal information. In addition, since the Microsoft Edge using the protected [internal resources ](<https://www.brokenbrowser.com/spoof-addressbar-malware/>)to perform a special operation, the attacker may access these resources, and may set Edge configure options, open IE, etc. We have a [video ](<http://paper.seebug.org/papers/Archive/media/uxss1.html>)show up for a bing cookie attack, [another section of the video ](<http://paper.seebug.org/papers/Archive/media/uxss2.html>)display nature.com content. But please remember, these website itself without any problems and the vulnerability from the Microsoft Edge browser. Below we'll look at how this is done. ### Domainless World about:blank is a very special URL, sometimes make people feel confused, don't know belong to where. Think about it: if we are located **www.magicmac.com/dom/index.html ** document. the domain is clearly **www.magicmac.com **but about:blank domain belong to? This is subject to availability. In theory, it should match the referrer domain, i.e., set its URL to the web page. For example, if we are in the www.magicmac.com click an about:blank link, then the about:blank will be www.magicmac.com as its domain. 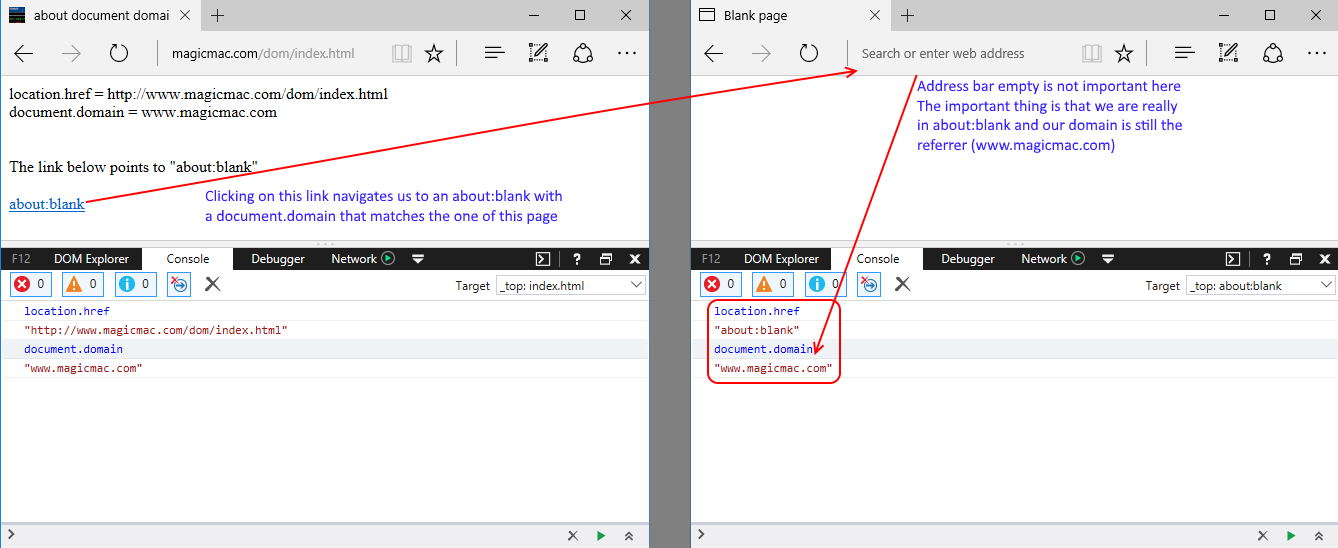 Another example is an iframe, its source is pointing to about:blank, or no source, the browser defaults to about:blank to. 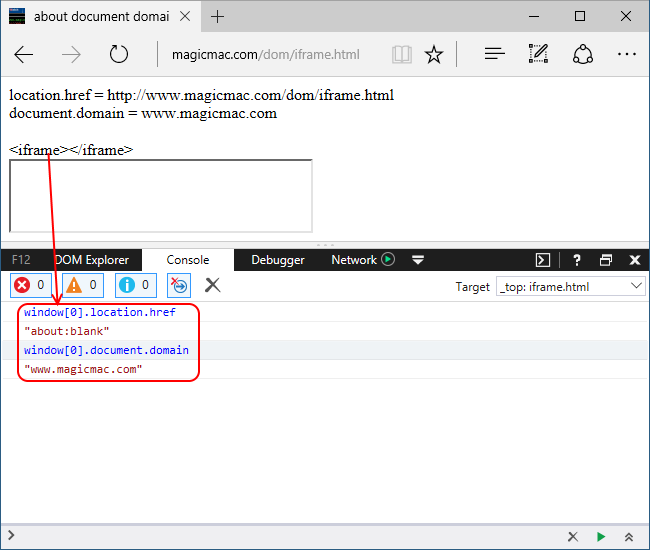 So, from goodfellas.com load the about:blank look and from evil.com loaded almost, because the two URL are the same, but they have a different document. domain, so that between them **can not access each other**。 Then the question came: we manually enter into the address bar of the about:blank domain? Want is this! The answer is so important, so I put the Devtools magnified look. 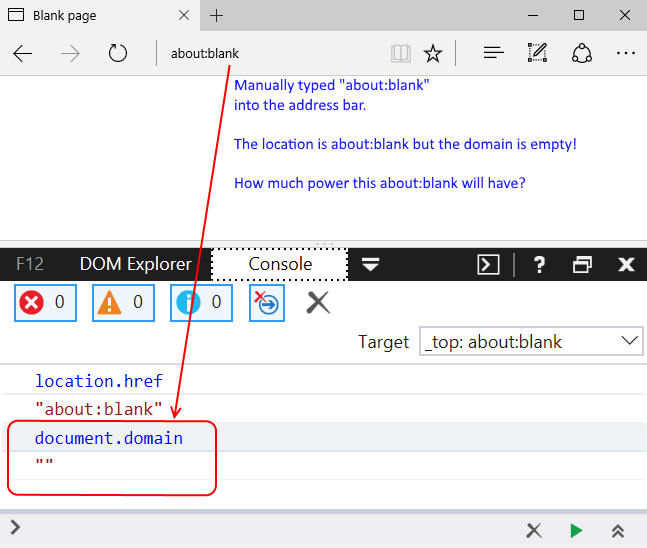 Is empty, as we have seen, it has great power, but in order to ensure that we are on the same page, we call the one without a domain“free domain name”the domainless and“domain”domained URL, a link to a document. the domain of the website. Bug hunter, the present article the following is the important stuff. ### “A domainless about:blank is capable of accessing any domained about:blank” Without a domain of about:blank to be able to access any domain of about:blank) In other words, a domain of about:blank can be unlimited access to a domain of about:blank. We are here to cut corners, directly in the Debug console operation, to quickly add a bing.com iframe to this page. `javascript document. body. innerHTML = '<iframe src="http://www.bing.com/images/search?q=microsoft+edge"></iframe>'` 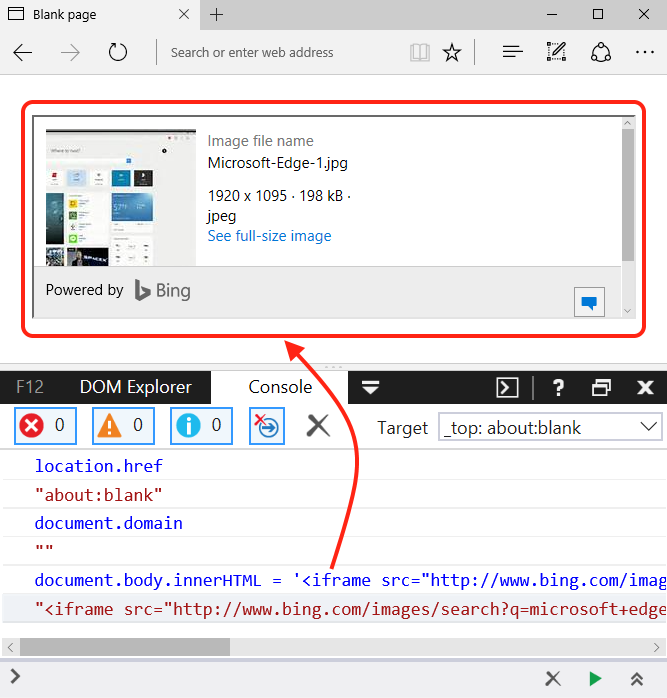 Very good! We are in the top-level free domain blank has a bing.com of the frame, but our goal is to find bing in a blank iframe, as I said, a free domain blank (main windows will be able to access any domain in the blank(bing.com in the iframe it. This case is very easy to achieve, because we use the bing.com already have a blank iframe. But let us continue to give it a try! Even from the debugger, the following this instruction is usually denied access, but due to the page top is no domain, it can be run. So let's check it out now! `javascript window[0][0]. location. href = "javascript:alert(parent. document. domain)";` 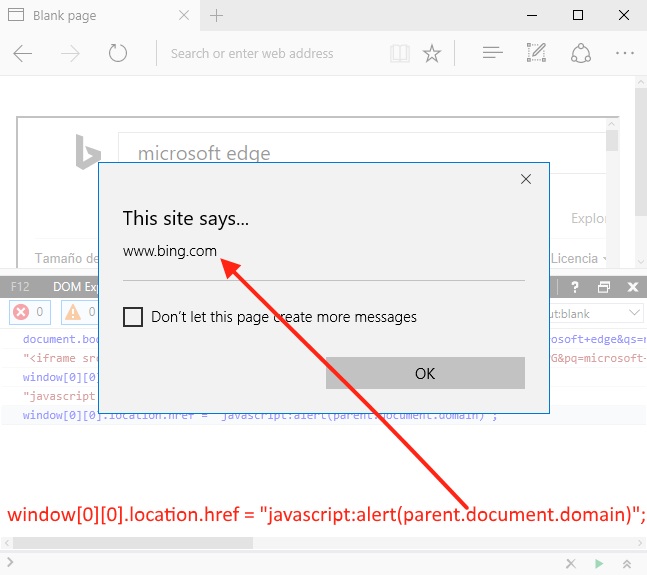 Bang on! I know it's not going deep into your mind, because we are from the DevTool to get the results, right? But for me, this is what I do the most important thing, because if we can master this one concept, the next found new UXSS will to some extent ease a lot. From now on, each find a way to access non-domain blank of the method is about:blank, but we can also use the other, we will get a UXSS in. Now is to use the DevTools, and I wanted to make sure we know exactly what the are doing, of course, we don't need DevTools to. ### Independent of PoC, without the DevTools Now to the real thing. We need to find a way to create a Can from a normal web page access to non-domain site, the faster method is to use a data: URI instead of about:blank. Similarly, at least the Protocol is different. And if we are in an iframe inside loading a data: URI, then its domain will be other references to the same domain as we are in the beginning to see the about:blank, and if you try to top load the data:uri of the data, the Edge will reject sending us to the wrong page. However, we have a few tips that can be done to get free domain Data data:uri, now let us explore the Flash version of the PoC, because it and its simple. In fact, I since 2005 have been using this Flash, it only set up the one from the query string of the URL, hurry up and use it! `<iframe src="geturl. swf? target=_top&redir=data:,[html/script goes here]"></iframe>` See? Only will you want to load the URL added to the **redir ** parameter. In this case, we use a data:uri and load it in the absence of domain of the top layer. In addition, in order to deceive the Edge of the browser, we need the iframe inside the loaded swf, otherwise it will not achieve the effect of the error page. You can yourself try it. By the way, don't forget we can find to achieve the same effects of the alternatives. I just use it because it is the first to be found, Adobe people may be the data:uri blacklisted in order to help my @Edge friends to get rid of this bug. However, there are many ways to achieve the same thing without the need of flash file. Submit your own ideas, find your own way! OK, now we are in the free domain of the window, we can inject a pointer to the bing.com the iframe, but the Edge is not properly rendering the page elements of the state. If we try to use the createElement/insertAdjacentHtml/etc it will not take effect. I mean, Edge would draw a“death”of the iframe, just like there is no engine in the car is the same: it simply can not run properly. In order to solve this problem, we use the document. write write itself, force the browser to be rendered again. And because we are in the free domain of the URL, document. write will make us completely on the same address/domain. `JavaScript document. write('<iframe src="http://www.bing.com/images"></iframe>');` Perfect! Now we can access bing blank iframe, but remember we are relatively lucky, because not all of the sites inside will have “free blank iframes”in. `javascript window[0][0]. location. href = "javascript:alert(parent. document. cookie)";` 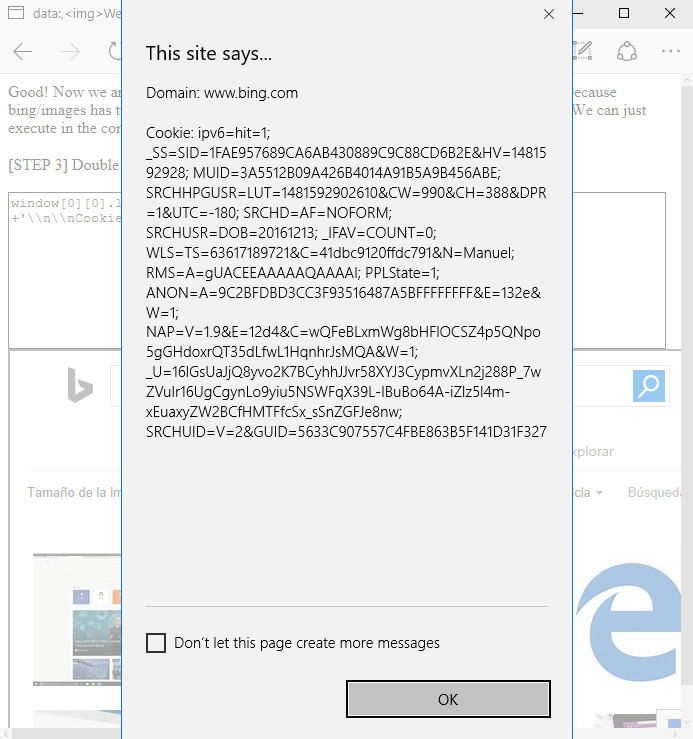 **[MS Edge line of the PoC in this](<http://unsafe.cracking.com.ar/demos/edge-domainless-uxss/bing/index.html>)** I'm very excited, this time in the absence of the DevTools case of the use of force. Oh, no, I know what you're thinking, suspicious of the bug hunter:Bing in vain gives us a pair of empty iframe, which is too simple! Yes, but I'm just a little celebration! From now on I will call you killjoy! No longer is a “bug hunter”in. We continue, killjoy is. I know the site does not like giving us an empty iframe idea, so we need to find their own way. ### Owning non-cooperative sites Take down non-cooperative site Think about it, we in a second step, the top layer is no domain of the data: while our iframe to render correctly, but the point nature.com instead bing.com because nature has a non-iframe one. If we try to change the iframe address, the Edge will refuse to open a new window. In other words, this thing is invalid. `javascript // We are inside a domainless data: so Edge will open a new // window instead of changing nature-iframe's location window[0][0]. location. href = "about:blank";` This will not take effect. Also it can be bypassed, but I have enough to try. This is in no domain of problems that occur, so we can open the one with the real URL of the new window, and then from there and then processed. This is exactly what we will do: 1. Open a nature.com the iframe in the new window. [Now we in the new window inside with a conventional URL] 2. The nature inside the iframe address is changed to about:blank, so we can give it a name. Yes, we want the iframe has a name. 3. The name is set to about:blank, then we non-domain opener on the CAN by the window. open access to it. Don't forget we are now within the window there is a regular URL, it is our strong opener is. We will show this iframe named, like this: window. name = "DAVID_COPPERFIELD" to commemorate the continue with a passion to learn the magician. 4. Now we should be about:blank that are part of our domain, the address is set to the nature of the address. To this end, we will use the meta-refresh will change the address to about:blank. Breeze. This technique to ensure that about:blank is restored to its parent domain of the domain. 5. Let the opener know when you are ready, so it can be accessed, like so: `window. open(“javascript:alert(document. domain)”, “DAVID_COPPERFIELD”);` 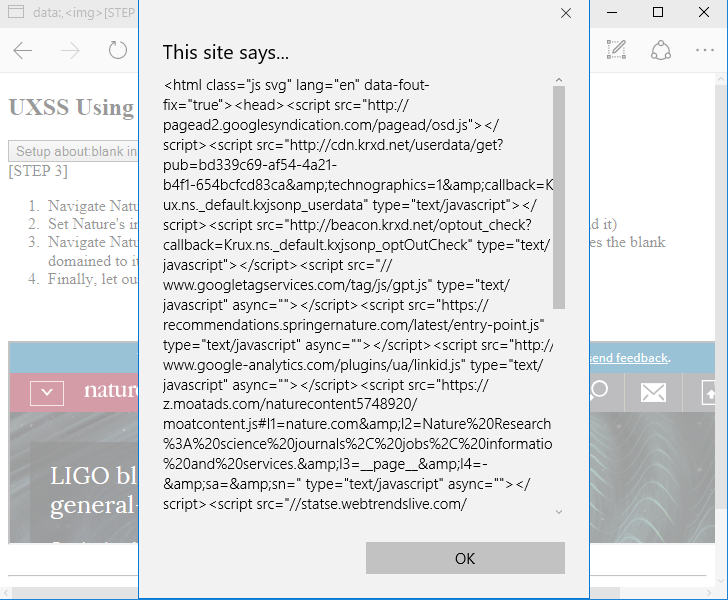 **[MS Edge line of the PoC in this](<http://unsafe.cracking.com.ar/demos/edge-domainless-uxss/nature/index.html>)** To enjoy again, but this time in the house cheered. Yes! Opsss, my wife asked what I found. She understood those screams mean something. killjoy, Sir, we did. PoC is interactive, so we can know in real time what we're doing, but please read the Code of the specific details, I'm sure there is room for improvement. If you presented these ideas, then you will probably be found to be able to achieve something similar to the workaround. Study, learn, learn! Very interesting. In no Flash situations, you can find your own method of setting the non-domain URL? Yes, you can. In addition, as long as we're here to discuss code, we can create a variety of UXSS scene, such as in the iframe to access its top. That possible? Suppose that I is by the Facebook presentation of the banner ads. Can visit our the top, and get like the user's friends list such things? Of course! Access is not like in the framework presented in the XFO site? the iframe is only capable of rendering HTML elements? Finally, the **completely no ** iframe site and what to do? I give you the assurance that we are even able to contact to compile the code. Sit down and explore yourselfto. Have a nice day! [Manuel](<https://twitter.com/magicmac2000>). |
| id | SSV:92801 |
| last seen | 2017-11-19 |
| modified | 2017-03-20 |
| published | 2017-03-20 |
| reporter | Root |
| title | Microsoft Edge allows remote attackers to bypass the Same Origin Policy(CVE-2017-0002) |
The Hacker News
| id | THN:D0463537F0A6A260170D27CB12689824 |
| last seen | 2018-01-27 |
| modified | 2017-01-11 |
| published | 2017-01-10 |
| reporter | Swati Khandelwal |
| source | https://thehackernews.com/2017/01/microsoft-security-patch.html |
| title | Microsoft Releases 4 Security Updates — Smallest Patch Tuesday Ever! |
References
- http://www.securityfocus.com/bid/95284
- http://www.securityfocus.com/bid/95284
- http://www.securitytracker.com/id/1037573
- http://www.securitytracker.com/id/1037573
- https://docs.microsoft.com/en-us/security-updates/securitybulletins/2017/ms17-001
- https://docs.microsoft.com/en-us/security-updates/securitybulletins/2017/ms17-001